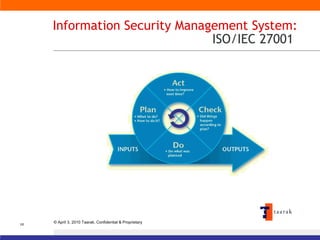
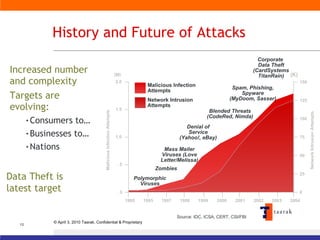
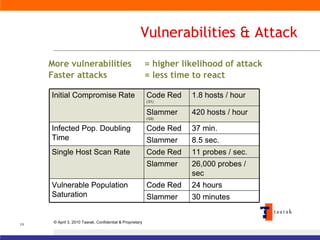
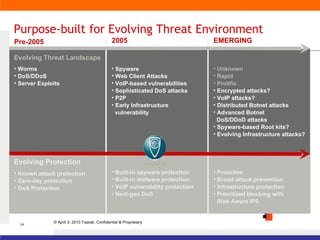
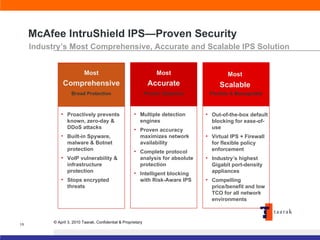
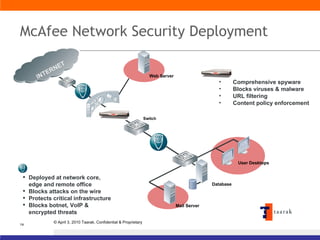
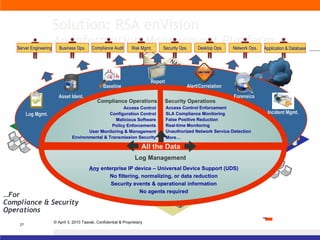
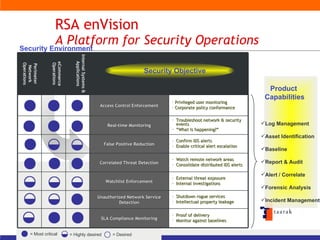
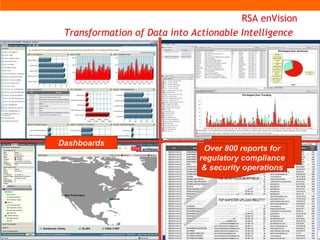
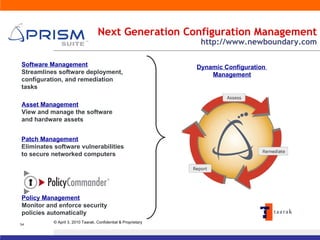
The document discusses information security solutions provided by Taarak India Private Limited. It covers their team size and certifications, solutions addressing confidentiality, integrity and availability, and agenda items around risk to information, information security management, technology challenges of bandwidth availability/optimization, data security, log management and system management.
![Information Security Taarak India Private Limited By Mohit Shukla – [email_address] Harsh Bhasin – harsh@taarak.com](https://image.slidesharecdn.com/itsecurity-12702914057826-phpapp02/75/Information-Security-1-2048.jpg)