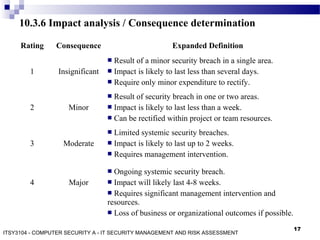
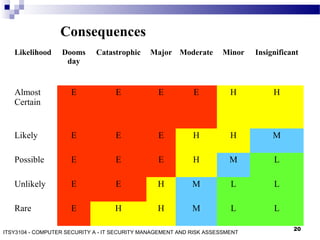
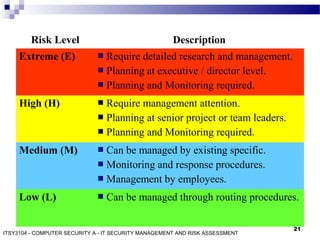
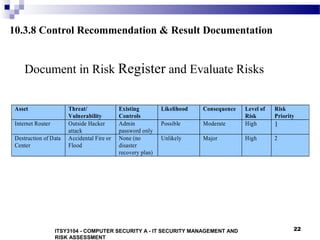
The document discusses IT security management and risk assessment, outlining key terminology such as assets, threats, vulnerabilities, and risks. It details various approaches to security risk assessment, including baseline, informal, formal, and combined methods, and describes a structured process for detailed risk analysis involving asset identification, threat identification, vulnerability assessment, risk analysis, and control recommendations. The content emphasizes the importance of tailored assessments based on organizational needs and resources to effectively manage risks.