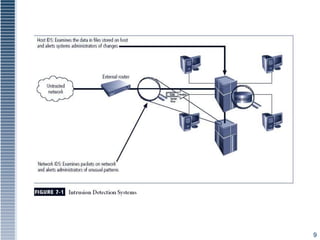
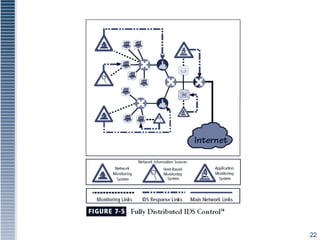
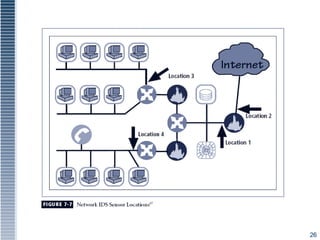
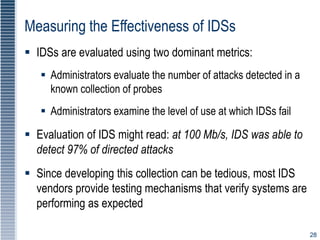
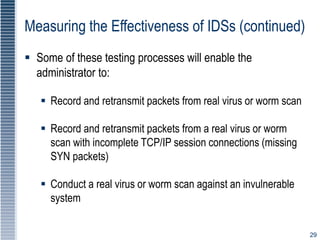
This document discusses various intrusion detection and security tools. It describes intrusion detection systems (IDS), including signature-based and statistical anomaly-based IDS. It also covers network-based IDS, host-based IDS, and application-based IDS. The document discusses deploying IDS, measuring IDS effectiveness, and tools like honey pots, honey nets, and padded cell systems which are used to study attackers.