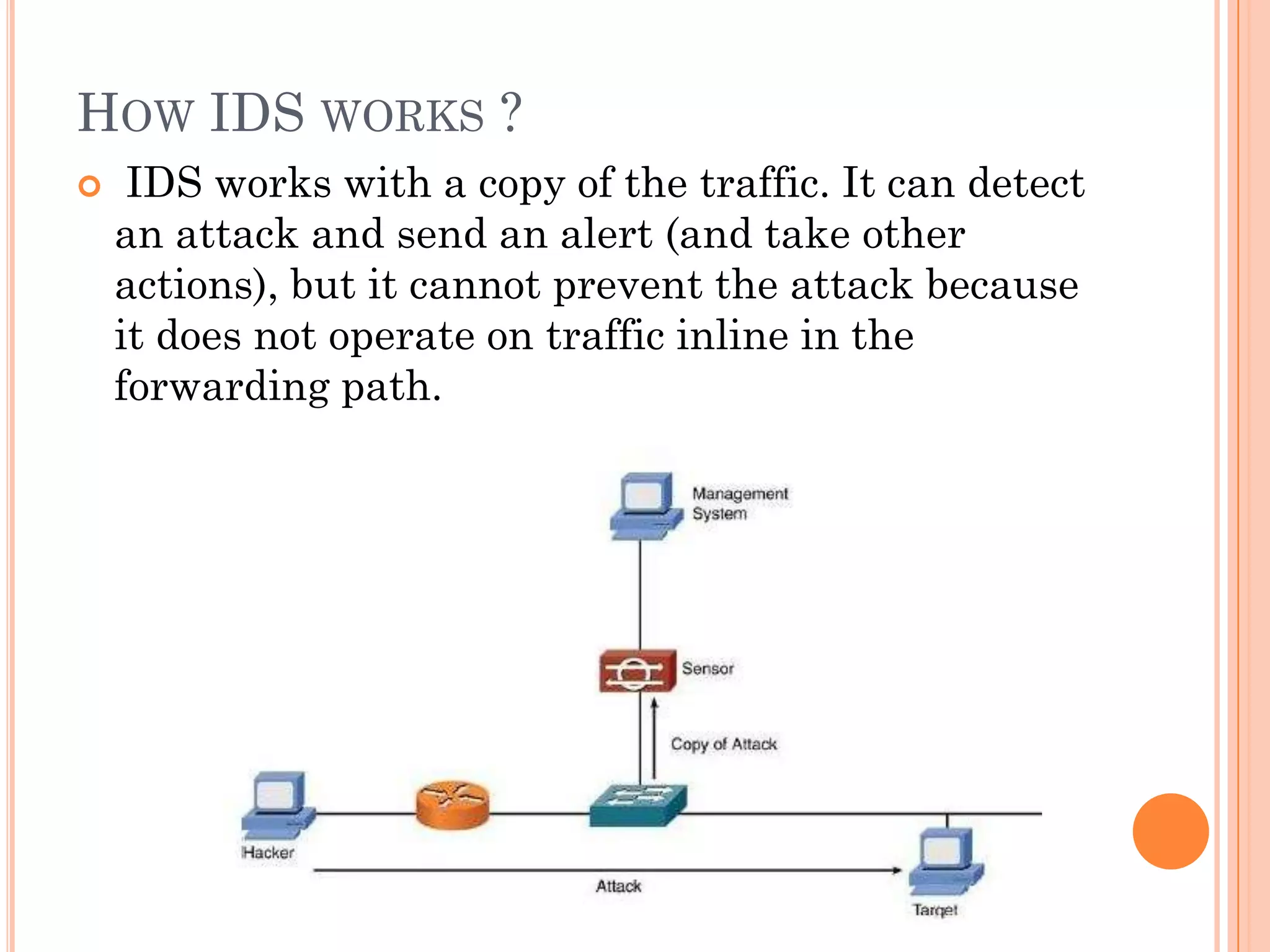
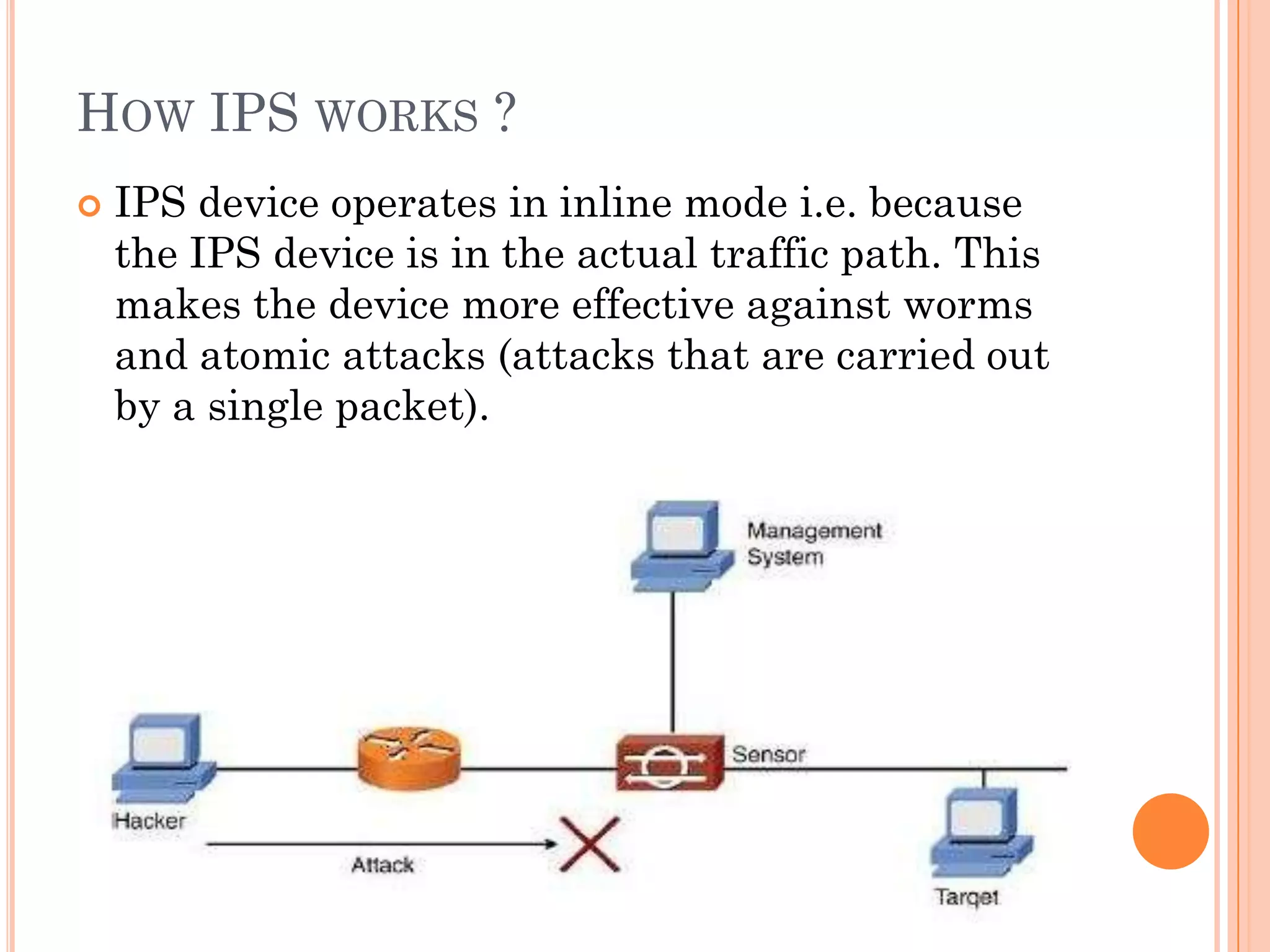
The document discusses intrusion prevention systems (IPS), which monitor network and system activity to identify and block malicious activity. It describes how IPS uses signature-based or anomaly-based detection methods to identify intrusions. IPS can be network-based, host-based, wireless, or focus on network behavior analysis. The document contrasts IPS with intrusion detection systems (IDS), which can only detect and report intrusions, while IPS can actively prevent them. It also compares IPS to firewalls, noting that IPS monitors for unwanted entries while firewalls regulate activity based on set rules.