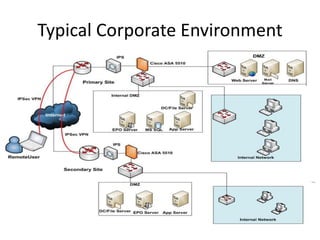
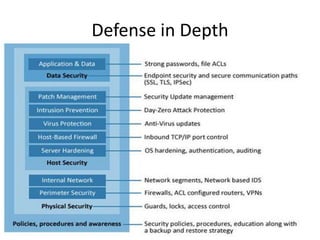
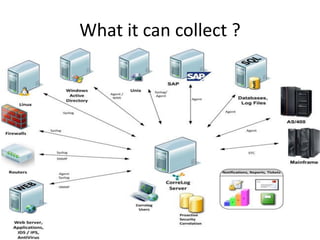
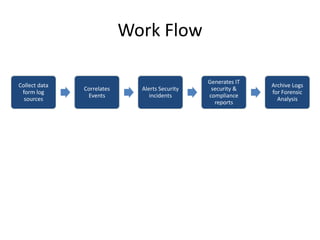
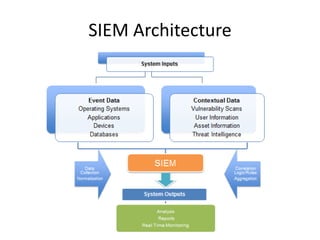
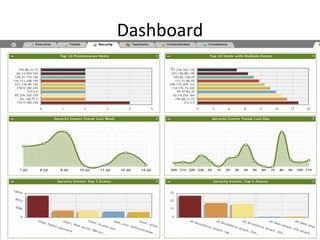
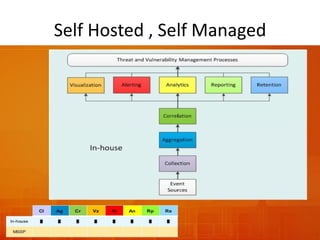
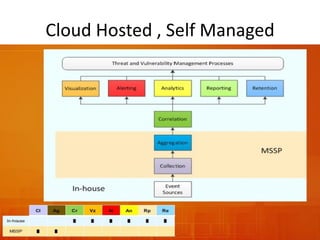
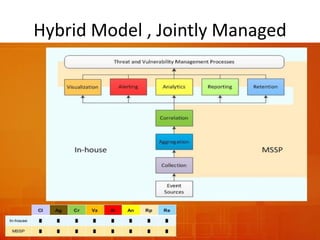
The document outlines the architecture and functionality of Security Incident Event Management (SIEM) systems, highlighting the importance of event collection, correlation, and reporting in security management. It discusses common challenges in SIEM implementation, such as inadequate planning and deployment strategies. The document also emphasizes the need for effective log management and compliance with security regulations.