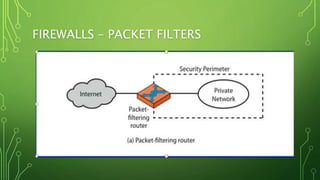
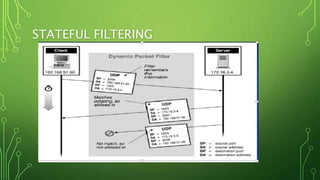
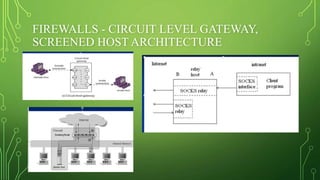
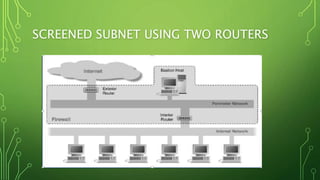
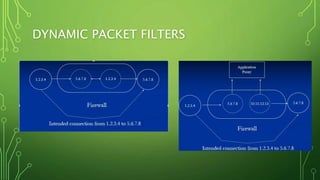
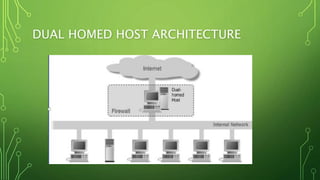
This document discusses different types of firewalls and how they work. It begins by explaining that firewalls come in many shapes and sizes, and sometimes a firewall is a collection of computers. All communication must pass through the firewall. It then discusses packet filters, stateful packet inspection engines, application gateways, and circuit-level gateways. Packet filters use transport layer information like IP addresses and port numbers to filter traffic. Stateful packet filters track client-server sessions to match return packets. Application gateways run proxy programs that filter traffic at the application layer. Circuit-level gateways filter traffic at the circuit level. A combination of these is known as a dynamic packet filter. The document also discusses additional firewall functions like network address