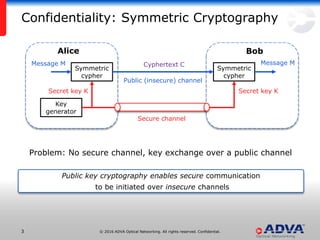
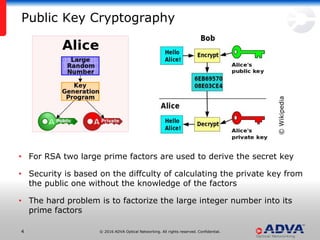
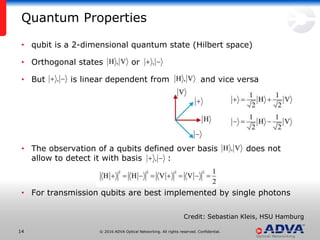
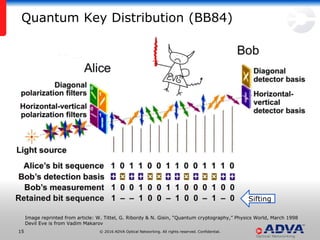
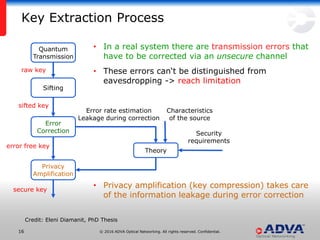
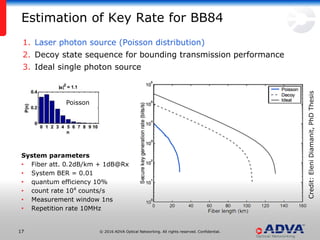
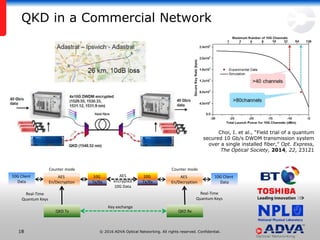
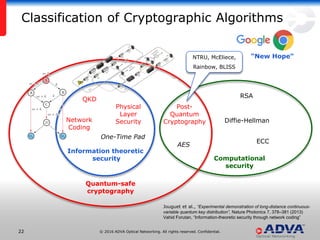
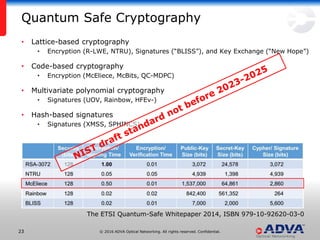
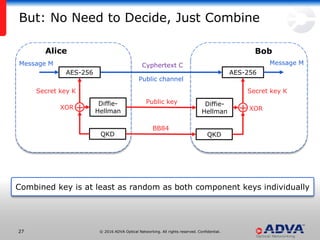
Helmut Griesser from ADVA Optical Networking discusses quantum-safe cryptography and quantum key distribution. He explains that quantum computers pose a threat to current public key encryption algorithms. Quantum key distribution provides absolute security by using quantum properties, but has limitations such as decreasing key rates with distance. Post-quantum or quantum-safe cryptography relies on unproven computational assumptions rather than physical properties. The best approach may be to combine diverse key exchange mechanisms like post-quantum, quantum key distribution, and classic public key encryption to strengthen security.