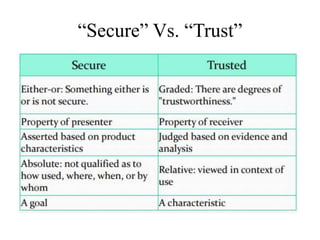
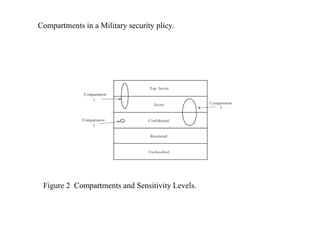
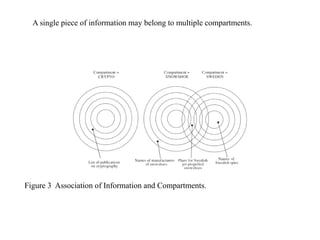
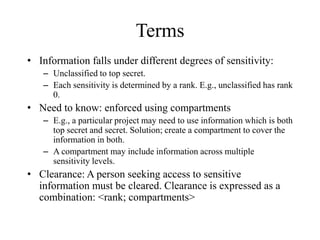
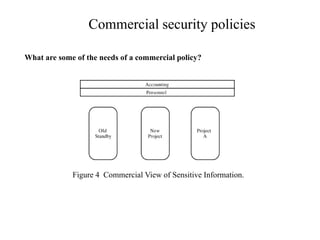
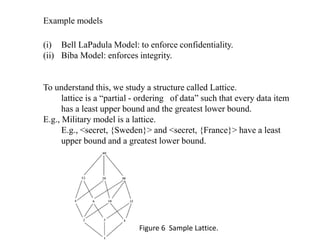
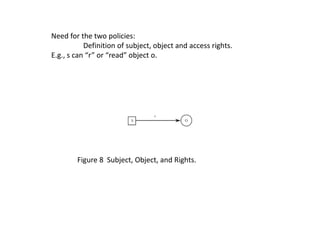
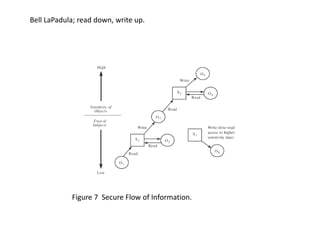
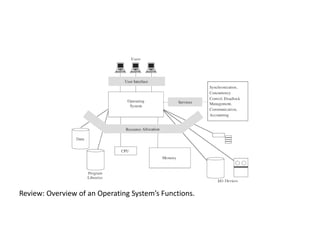
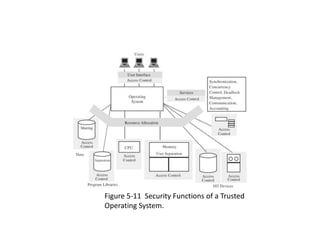
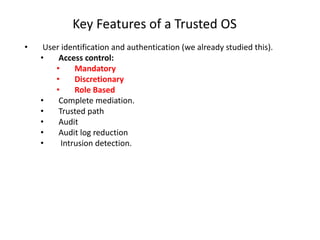
The document provides an overview of general purpose operating system protection. It discusses various file protection mechanisms including all-none protection, group protection, and individual permissions. It also covers user authentication methods such as passwords, biometrics, and one-time passwords. The document then examines security policies, models, and the design of trusted operating systems. It analyzes features like access control, identification, authentication, and auditing that are important for a trusted OS.