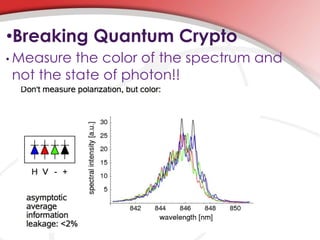
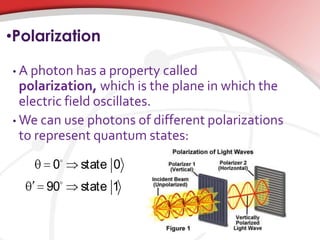
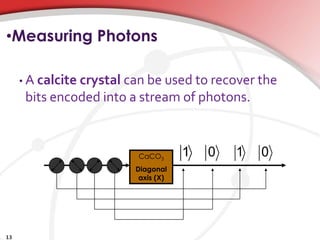
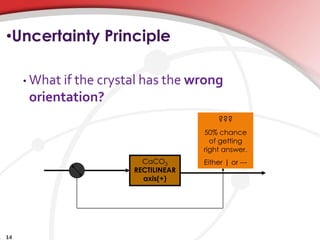
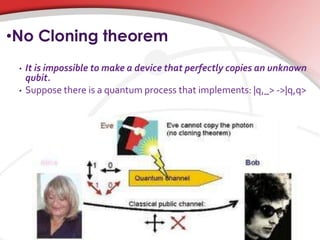
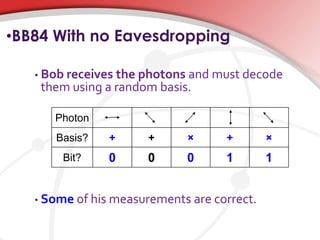
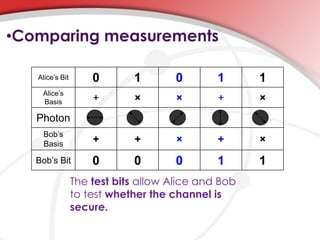
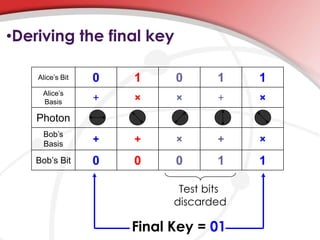
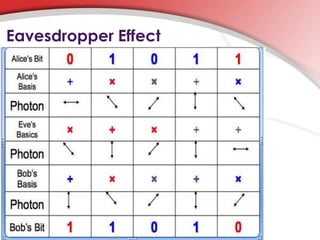
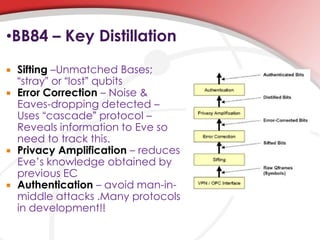
Quantum cryptography utilizes quantum mechanics to enable perfectly secure cryptosystems, safeguarding against potential threats from future quantum computers that could break classical encryption methods. Key concepts include quantum key distribution (QKD) techniques such as BB84, which encodes information in photon polarization and detects eavesdropping through measurement alterations. The technology is being developed for practical applications, including mobile phone security, despite challenges such as high costs and range limitations.


![•Basic Ideas of Cryptography
• Cryptography: “the coding and decoding of secret
messages.”
• The basic idea is to modify a message so as to make
it unintelligible to anyone but the intended
recipient.
• For message (plaintext) M,
e(M, K) encryption - ciphertext
d[e(M, K), K] = M decryption](https://image.slidesharecdn.com/cryptopresentationfinal-140409152958-phpapp02/85/Cryptopresentationfinal-5-320.jpg)














![•Making use of twisting and turning
• Makes use of the Reference
independent frame QKD[RfiQKD]
• Polarization or phase is measured in
context with a reference frame
• They select a specific threshold value
and drop below this value signals there
is an eavesdropper .](https://image.slidesharecdn.com/cryptopresentationfinal-140409152958-phpapp02/85/Cryptopresentationfinal-31-320.jpg)