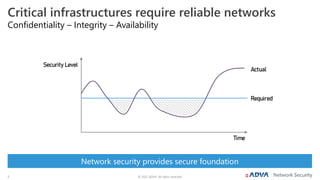
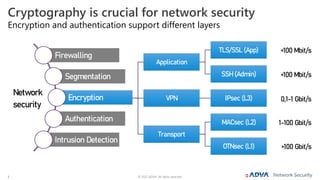
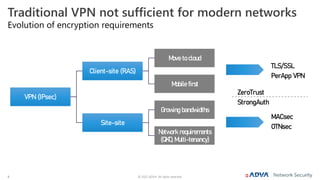
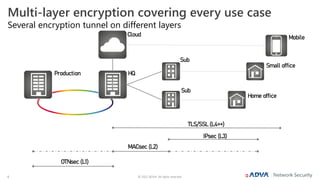
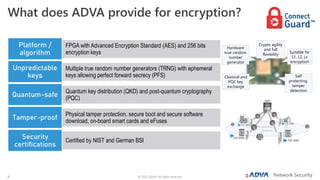
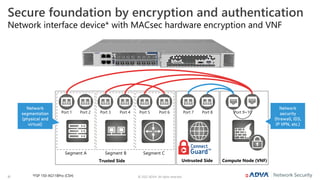
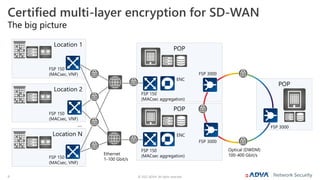
The document outlines the importance of multi-layer encryption for enhancing network security, especially for critical infrastructures, by integrating various encryption protocols across multiple layers. It emphasizes the evolution of encryption needs in modern networks and discusses the advancements provided by ADVA, including quantum-safe technologies and secure management solutions. The summary highlights the necessity of robust encryption mechanisms and the assurance of security certifications in creating a safe networking environment.