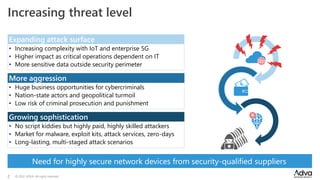
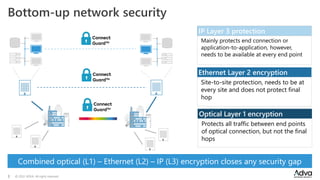
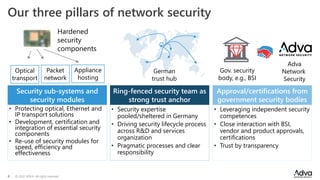
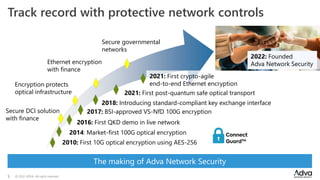
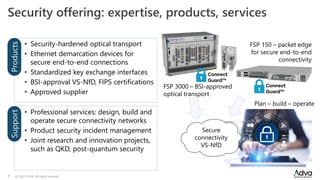
ADVA Network Security, established in September 2022, addresses rising cybersecurity threats through specialized solutions for optical, Ethernet, and IP transport. The company emphasizes a bottom-up approach to security, including hardened devices and a strong focus on certifications and independent security expertise based in Germany. With a history of innovation in encryption and secure network transport, ADVA aims to protect sensitive data across critical infrastructure and governmental networks.