Quantum cryptography uses principles of quantum mechanics to securely distribute encryption keys between two parties. It allows Alice and Bob to detect if an eavesdropper (Eve) is trying to intercept the key during transmission. Eve's attempt to measure the quantum states used to transmit the key would introduce detectable errors. The document discusses the history and principles of quantum cryptography, including types like discrete and continuous variable QKD. It also covers desirable attributes like confidentiality and rapid key delivery, providing an example of how quantum key distribution works between Alice and Bob.





![logarithm problem. But since these problems typically are not provably hard, the corresponding
cryptosystems are potentially insecure. For example, the famous and widely used RSA public-key
cryptosystem [Rivest et al. 1978] could easily be broken if large integers were easy to factor. The
hardness of integer factoring, however, is not a proven fact but rather a hypothesis.1.We mention
in passing that computing the RSA secret key from the corresponding public key is polynomial-time
equivalent to integer factoring [May 2004].
Second, the theory of quantum computation has yielded new methods to tackle these
mathematical problems in a much more efficient way. Although there are still numerous
challenges to overcome before a working quantum computer of sufficient power can be built, in
theory many classical ciphers (in particular public-key cryptosystems such as RSA) might be broken
by such a powerful machine. However, while quantum computation seems to be a severe
challenge to classical cryptography in a possibly not so distant future, at the same time it offers
new possibilities to build encryption methods that are safe even against attacks performed by
means of a quantum computer. Quantum cryptography extends the power of classical
cryptography by protecting the secrecy of messages using the physical laws of quantum
mechanics.
The currently used public key encryption and signature schemes can be broken by quantum
adversaries. This led to the innovation of quantum cryptography.
Quantum Cryptography
It is the science of exploiting the quantum mechanical properties to perform cryptographic tasks.
The quantum key distribution offers an information- theoretically secure solution to the key
exchange problem. Its main advantage is that it allows the completion of various cryptographic
tasks that are proven or assume to be impossible using only classical communication. For example:](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-6-320.jpg)
![it is impossible to copy data encoded in a quantum state and the very act of reading data encoded
in quantum state changes the state. This is used to detect the eavesdropping in quantum key
distribution.
History:
Quantum cryptography is based on 2 major elements of quantum mechanics as the base of its
implementation.
The two principles are:
1) Heisenberg uncertainty principle: At the instant at which the position of the electron is
known, its momentum therefore can be known only up to magnitudes which correspond to that
discontinuous change; thus, the more precisely the position is determined, the less precisely the
momentum is known, and conversely. This simply means that observation of quanta changes its
behavior. By measuring the velocity of quanta we would affect it, and thereby change its position;
if we want to find a quant's position, we are forced to change its velocity. Therefore, we cannot
measure a quantum system's characteristics without changing it (Clark, n.d.) and we cannot record
all characteristics of a quantum system before those characteristics are measured.[1]
2)Principle of photon polarization: It is the quantum mechanical description of the classical
polarized sinusoidal plane electromagnetic wave. An individual photon can be described as having
right or left circular polarization or a superposition of two.
The concept of quantum cryptography was first proposed by Stephen Wiesner in his seminar paper
“Conjugate Coding”, which proposed how to store or transmit two messages by coding them in
two “conjugate observables”, such as circular or linear polarization of light, so that either (not
both) of which may be received and decoded. This study was further carried on by Charles H.](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-7-320.jpg)
![Bennett and Gilles Brassard who proposed a method of secure communication which is called
BB84. This method is at the basis of quantum key distribution methods.[2]
3. There is one more principle that forms the basis of Quantum cryptography i.e. The No Cloning
Theorem. It states that it is impossible to create a copy of an arbitrary unknown quantum state.
This makes it impossible to perform eavesdropping because it will quickly be detected and thus
guarantees that the communicated data remains private.
Quantum Key Distribution(QKD):
The current key distribution approach presents many challenges. Its security is threatened by weak
random number generators, advances to CPU power, new attack strategies and emergence of
quantum computers.
Quantum key distribution addresses these challenges by using quantum properties to exchange
secret information such as a cryptographic key which can then be used over an insecure channel.
The security of this relies on fundamental laws of nature, which are not vulnerable to increasing
computational power, new attack techniques and quantum computers. For the highest security
requirements, QKD enables the contiguous generation and sharing of truly random one time pad
keys. If there is an eavesdropper trying to intercept a quantum exchange, will inevitably leave
detectable traces. The legitimate exchanging parties can decide either to discard the corrupt
information or reduce the information available to the eavesdropper to nought by distilling a
shorter key.
A QKD implementation typically includes the following components:
i) A fiber or free-space quantum channel to send quantum states of light between the
transmitter (Alice) and receiver (Bob). This channel does not need to be secured.](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-8-320.jpg)
![ii) A public but authenticated communication link between the two parties to perform
post-processing steps and distill a correct and secret key.
iii) A key exchange protocol that exploits quantum properties to ensure security by detecting
eavesdropping or errors, and by calculating the amount of information that has been intercepted
or lost. Both errors and potential information leakage are removed during subsequent error
correction and privacy amplification post-processing steps, leaving Bob and Alice with a shared key
known only to them.[3]
Types of Quantum Key Distribution:
1. Discrete variable QKD: It encodes quantum information in discrete variables and uses single
photon detectors to measure the received quantum states. Example: BB84 and E91 protocols.
2. Contiguous variable QKD: IN this the quantum information is encoded onto the amplitude and
phase quadratures of a coherent laser and then can be measured by the receiver using homodyne
detectors.
Both these approaches have been proven to be information theoretically secure even in the
presence of an attacker or eavesdropper.](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-9-320.jpg)

![material, in realistic settings and often run at much lower rates. This is unacceptably low if one
uses these keys in certain ways, e.g., as one-time pads for high speed traffic flows. However it may
well be acceptable if the keying material is used as input for less secure (but often secure enough)
algorithms such as the Advanced Encryption Standard. Nonetheless, it is both desirable and
possible to greatly improve upon the rates provided by today’s QKD technology.[4][5].
QKD Example:
The following is an example of how quantum cryptography can be used to securely distribute keys.
Alice begins by sending a message to Bob using a photon gun to send a stream of photons
randomly chosen in one of four polarizations that correspond to vertical, horizontal or diagonal in
opposing directions (0,45,90 or 135 degrees). For each individual photon, Bob will randomly
choose a filter and use a photon receiver to count and measure the polarization which is either
rectilinear (0 or 90 degrees) or diagonal (45 or 135 degrees), and keep a log of the results based on
which measurements were correct vis-à-vis the polarizations that Alice selected. While a portion of
the stream of photons will disintegrate over the distance of the link, only a predetermined portion
is required to build a key sequence for a onetime pad. Next, using an out- of-band communication
system, Bob will inform Alice to the type of measurement made and which measurements were of
the correct type without mentioning the actual results. The photons that were incorrectly
measured will be discarded, while the correctly measured photons are translated into bits based
on their polarization. These photons are used to form the basis of a onetime pad for sending
encrypted information. It is important to point out that neither Alice nor Bob are able to determine
what the key will be in advance because the key is the product of both their random choices. Thus,
quantum cryptography enables the distribution of a one-time key exchanged securely. Now let us
suppose that a malicious attacker attempts to infiltrate the cryptosystem and defeat the quantum](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-11-320.jpg)



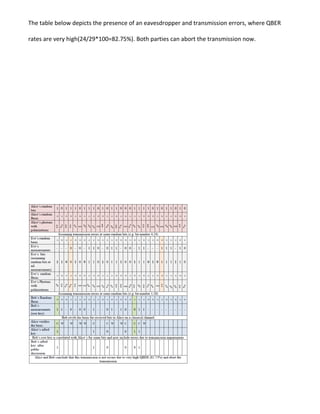
![BB84 uses quantum properties so well that it has become the base for quantum cryptography. Its
disadvantage is its assumption for ideal quantum sources and detectors, which makes it vulnerable
to PNS and detector noise attacks.[6]
B92 PROTOCOL
It is similar to BB84 coding scheme but uses only for 2 out of 4 BB84 states, which makes it easier
to implement. It encodes classical bits in two non orthogonal BB84 states. Since no measurement
can distinguish two non orthogonal quantum states, it makes it impossible to identify the bit with
certainty. If there is any attempt to learn the bit, it will modify the state in a noticeable way. B92
allows the receiver to learn whenever he gets the bit sent without further discussion with Alice.
But it is difficult to establish in certain experimental settings and very often turns to be insecure. In
B92, the classical bit b=0 is encoded by a photon with horizontal polarization and b=1 is encoded
by photon with polarization angle 45 degrees.[7]
IS QUANTUM CRYPTOGRAPHY HACKABLE?
A hacker can blind a detector with a strong pulse, rendering it unable to see the secret keeping
photons. Another weakness to the system is, photons are often generated using a laser tuned to
such a low intensity that its producing one single photon at a time. There is a certain probability
that the laser will make a photon encoded with your secret information and then a second photon
with that same information. All an intruder has to do is to steal that second photon and could gain
access to the data. The problems mentioned are just in theories given by Renner. To put them into
action will take a lot of technological advancements.[8]](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-16-320.jpg)
![CITATIONS AND REFERNCES
[1] https://en.wikipedia.org/wiki/Quantum_cryptography
[2] [https://en.wikipedia.org/wiki/Photon_polarization]
[3] [https://www.quintessencelabs.com/wp-content/uploads/2016/09/CSA_What-is-
[4] https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0ahUKEwiqyp-
O0OLXAhWi5oMKHZY5Ag4QFggsMAA&url=http%3A%2F%2Fblog.protogenist.com%2F%3Fp
%3D702&usg=AOvVaw1_7CvJg9qdKR0mzL8igaBC
[5]C. Elliott, “Building the quantum network,” New J. Phys. 4 (July 2002) 46.
[6] [https://arxiv.org/ftp/arxiv/papers/1407/1407.2357.pdf]
[7] [http://gva.noekeon.org/QCandSKD/QCandSKD-introduction.html]
[8] https://www.wired.com/2013/06/quantum-cryptography-hack
[9] https://www.quora.com/What-are-the-pros-and-cons-of-quantum-cryptography
[10] http://ieeexplore.ieee.org/document/5383498](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-17-320.jpg)
![[12] https://arxiv.org/abs/1504.05628
[13]https://www.google.com/search?
q=principle+of+photon+polarization+quantum+cryptography&oq=principle+of+photon+polarizatio
n+quantum+cryptography&aqs=chrome..69i57.17347j0j7&sourceid=chrome&ie=UTF-8
[14]https://www.google.com/search?
q=principle+of+photon+polarization+quantum+cryptography&oq=principle+of+photon+polarizatio
n+quantum+cryptography&aqs=chrome..69i57.17347j0j7&sourceid=chrome&ie=UTF-8
[15]http://nvlpubs.nist.gov/nistpubs/ir/2016/NIST.IR.8105.pdf
[16]https://www.google.com/url?
sa=t&rct=j&q=&esrc=s&source=web&cd=4&ved=0ahUKEwiw7ajQgsXXAhVE64MKHTc2A2oQFghA
MAM&url=https%3A%2F%2Fwww.wired.com%2F2013%2F06%2Fquantum-cryptography-hack
%2F&usg=AOvVaw2U5ObWp79goagNGIWdPhzV](https://image.slidesharecdn.com/quantumcryptography-180425230505/85/Quantum-cryptography-18-320.jpg)