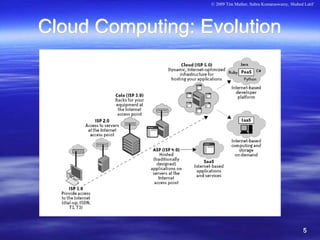
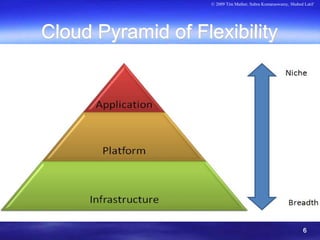
The document discusses the evolving landscape of cloud security and privacy, particularly from an enterprise perspective on risk and compliance. Key topics include infrastructure security, data security, identity and access management (IAM), and the need for improved audit and compliance frameworks in the context of cloud computing. It emphasizes that while cloud computing offers significant benefits such as cost and scalability, there are considerable challenges related to security responsibilities and data privacy that enterprises must navigate.


![© 2009 Tim Mather, Subra Kumaraswamy, Shahed Latif
What We Do Discuss
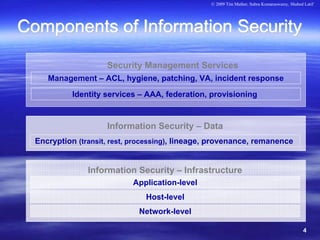
• Infrastructure Security
• Network-level
• Host-level
• Application-level
• Data Security
• Identity and Access Management (IAM)
• Privacy Considerations
• Audit & Compliance Considerations
• Security-as-a- [Cloud] Service (SaaS)
• Impact on the Role of Corporate IT
Where Risk Has Changed: ± 3](https://image.slidesharecdn.com/cloudsecurityandprivacy-12520085183843-phpapp01/85/Cloud-Security-And-Privacy-3-320.jpg)