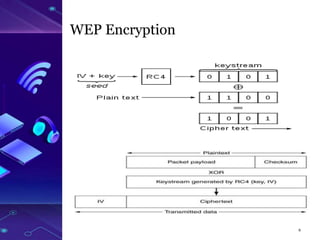
The document discusses the WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) protocols, detailing their authentication, encryption methods, and vulnerabilities. It highlights weak points in WEP, such as poor key management and predictable initialization vectors, alongside various attacks like FMS, PTW, and ARP replay. WPA was introduced as a more secure replacement with enhancements like TKIP and AES, but also has known vulnerabilities exploited by attacks such as the Beck-Tews and Michael attacks.