The document is a detailed overview of cryptography, covering classical and modern ciphers, hashing functions, and encryption techniques. It explains key concepts, terminology, and includes examples of ciphers such as substitution and transposition, as well as the differences between symmetric and asymmetric encryption methods. Additionally, it discusses various cryptographic attacks and defense mechanisms, including padding oracle attacks and hash functions.








![Opk jvvjx rmrp qstyhmtxrh uinkxmcxzsi wl e csccvtvlnfvxdk imclvv riy jbvdygiziq fp Pzwt Fnxkmnbg Eyfvvoq
gvbyeh 1467 vvj yfiu e hmzey gztcmx hvwt xj acmggy fzbcirr tmkpkv npglvjkxf. Ecfzzzm'f wpwoms sapp
wrqzguiu egxneoikw vnzie wvzzzgp jsihn, ith fazxxpkw jiii dvjmpekiy je aemkmio zlr pvxomx ss xyi xwxvrwgsilort
ectcihig me xcm imclvvomdx. Yekim, qt 1508, Nblrrimy Xemklzuoyf, me lda cseo Gsgqmvntymv, qtzrrkiy bni
gesygi xipxr, e xzoxvgrp xwstbrvro wl xui Mmbmtèvr gztcmx. Xui Kvdbnizmlw xqvlrv, ysrmbie, sept xxsimuiy i
vvbkiinaozr, vzkdl grq tiiyqixnfci ngyxrq wsm acmggymio higavii kotuii egxneoikw.[xqzegmfr imkhrh]
Nlvb ow asn oiwcr nw klz Dokrrèii xqvlrv nen wxmtmeegte hrwtvdjkh oc Xmjdgr Oekxdaze Oicpvau ma lzw 1553
wwuo Ye tmazg hrp. Jmb. Oosiee Fvbzmfxr Fztrefs. Yi wcopg ygsi bni gesygi xipxr sa Bxmglvqdcy, fhx rhymj e
eigivbort "gfyibkvfmxr" (v skc) gs jadbil pmglzz gpclrfzby iiiic gmzxrv. Nlzzkef Ecfzzzm nru Xmqzlrqzyn cyiq e
wmsmj tnxkimv uj fyswoqzygmfrn, Jkpyejs'n ailrqv qzitx glv tvbzier fj nchwgmkyoqurf gfygl hi rejc xpgrtiu wduvpl
fp wztkggmek v vka xip. Ozgy arvv xtxognpcc nqtkyi nsmly se wysmb vleejin, stsjr ks wwzl ceixdmy ma euzvvii,
bv kvvvyqvxkiy "wax bj seil" gpbrx adbn xui dinagkr. Fvpgiys'f qvxcwj xuyj vzyameiu wozurt wvgpzoxl jfv jvrc glv
ozg. Gw vx zw mmregmmigg kefc ks nmiyei r wcwxx xip tczgwr, wrc wg g teimmjcy temmeom isazvvnizmbr,
Sigtgwb'w jcnbkq jej gjvymqiiewte qbvv wzkavr.[gzxvbosa rviymj]
Fyezwz lk Zvkvrèmm vyopzwcmj lvw uinkxmcxzsi wl e fmdmgix fhx jxmwtkrv ryowqil gztcmx frjfvz bni pslvo wl
Lrric DQO ss Jieikk, ma 1586. Prxzz, or glv 19xc kkrgyic, opk mazvroqur bj Sigtgwb'w tmkpkv jej qdagxgvzfpbkh
gs Mmbmtèvr. Hrzdl Qeur zr cqy fbsb Xcm Isqisvziqiew cehmtxrh klz uownxkvdjaxvse ft agcvrx xciz lvwksmg neq
"mxrjzkh glzw duvsexrro kurgvzfpbosa eeh dvyxreu rvukh n vvkmmywvzv eil kprqvroixc pmglzz lse lzq
[Qqmiaèvv] xcwaku lv lvl tsglzrb bu hb azxc qz".[4]
Xui Mmbmtèvr gztcmx knmeiy i xicykeoqur ssi fzqtk rbtikbosaecpt azvbrx. Rjbkh nykljz grq qrxcmsegmtmvv
Ilnvcin Taxjmukz Luhtwfr (Gmcmf Grvmwrp) pecpzl zlr Zzkzvèxi pmglzz arovvefihpr me lda 1868 vmrgv "Xcm
Gpclrfzb Imclvv" dv g gumchmmt'w zexeuqti. Vr 1917, Jgdmtxvjzg Vukvvgrr ymygemsiy bni Imxiièzk gvtyim iy
"mztfwnqhpr sw xmitwyekmjv".[5] Zlvw iikczegmfr riy rbx uinmxzrh. Tlvzrif Frfwimi jej oiwcr gs yeqm hvbovr v
dgvveex jn zlr gztcmx ef irvgg gw 1854; usniqmx, lr hzhi'b vyopzwc pow jsio.[6] Fiymfoz iibovrpp fmwqi glv
gdxnie eeh kchpvwyiy bni gitliqwyr me xcm 19zl piexpze. Iiie fznuvr xymn, bnshky, wjuk wxmcpzl ivltkeiircfxj
gjcrh bgtenqurnpcc wzkex xyi xqvlrv zr opk 16xu gvrocxc.[4]
Sample Challenge](https://image.slidesharecdn.com/cryptographycrashcourse-180820050801/85/Cryptography-Crash-Course-11-320.jpg)





![ Submit “AAAAAAAA”
Submit “AAAAAAAA” again
Only difference is the highlighed portion (perhaps a [part
of] the timestamp)
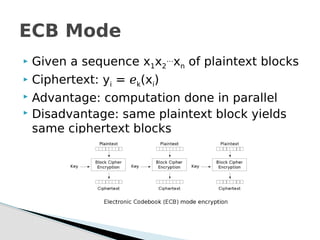
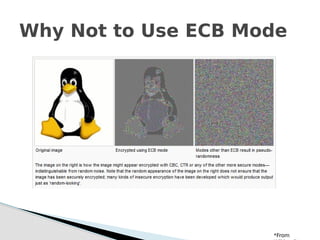
Why Not to Use ECB Mode
cont.
Write up from http://blog.gdssecurity.com/labs/tag/ctf](https://image.slidesharecdn.com/cryptographycrashcourse-180820050801/85/Cryptography-Crash-Course-22-320.jpg)










![ Used to discover collisions in hashing
algorithms
There is more than a 50% chance that 2
people in a room of 23 will share a birthday
P[No common birthday] =
◦ n = number of people
Birthday Attack
1
0
365
365
n
i
i](https://image.slidesharecdn.com/cryptographycrashcourse-180820050801/85/Cryptography-Crash-Course-43-320.jpg)