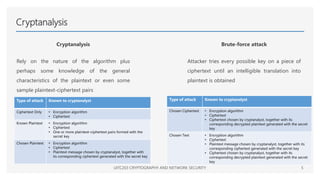
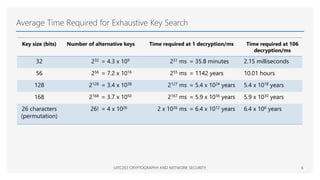
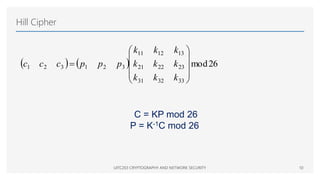
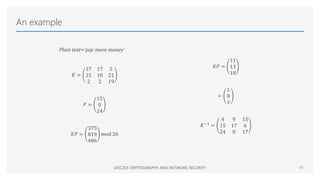
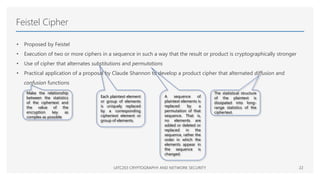
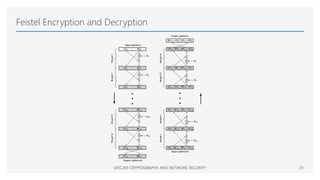
This document provides an overview of classical cryptographic techniques, focusing on concepts such as symmetric ciphers, encryption and decryption algorithms, and various ciphers including the Caesar, Playfair, Hill, and Vigenère ciphers. It also discusses the principles of cryptanalysis, types of attacks, and the Feistel cipher structure, emphasizing the importance of key selection and size for securing cryptographic systems. Additionally, the document highlights practical challenges in implementing secure encryption methods and references significant works in the field of cryptography.