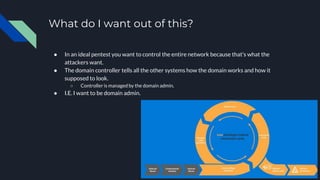
1. The document discusses various methods for gaining domain administrator privileges on a Windows domain, including exploiting the domain's architecture, abusing Active Directory services like Kerberos, and cracking Kerberos tickets.
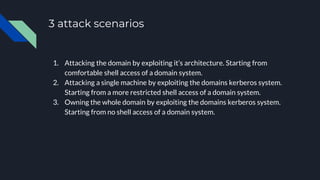
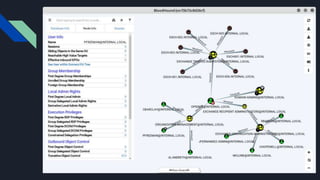
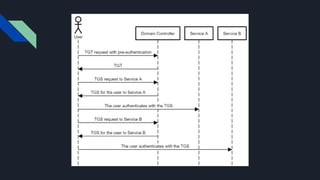
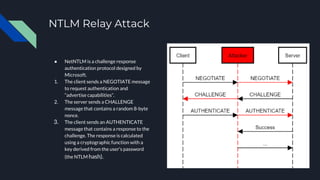
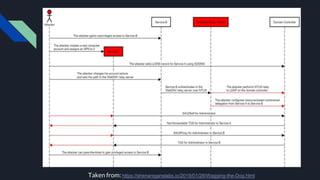
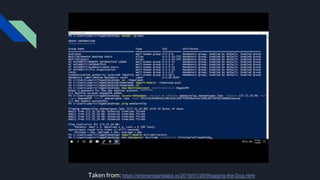
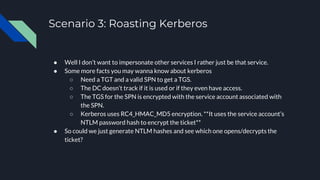
2. It provides three attack scenarios: leveraging internal access and the BloodHound tool, performing an NTLM relay attack against WebDAV to setup delegation, and directly cracking Kerberos tickets by requesting tickets for service principal names.
3. The document recommends demonstrating these attacks against a test environment to gain hands-on experience compromising a Windows domain from different starting points.