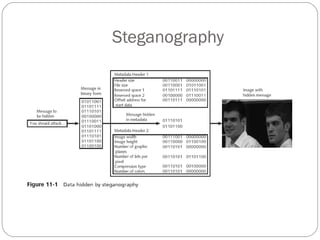
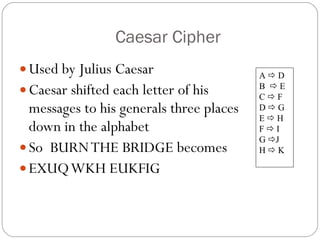
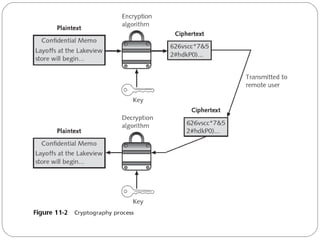
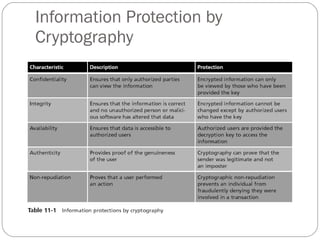
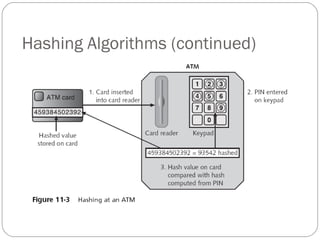
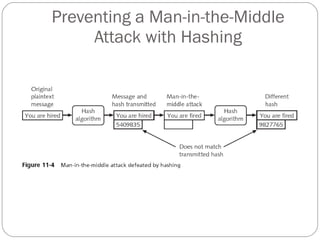
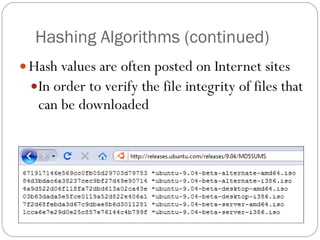
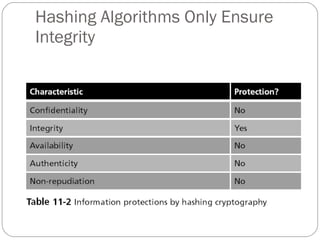
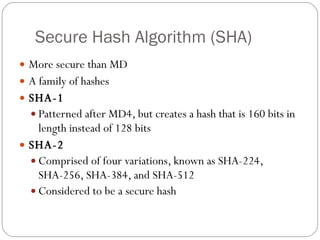
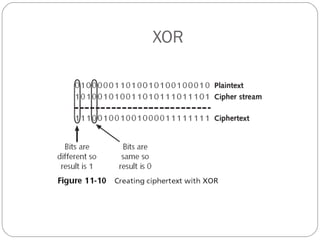
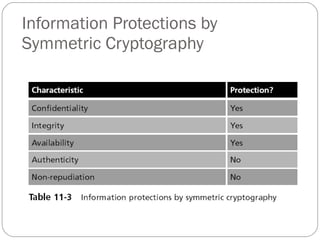
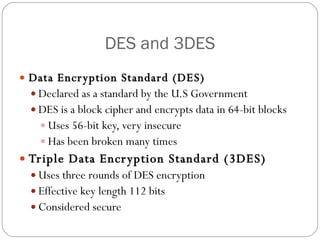
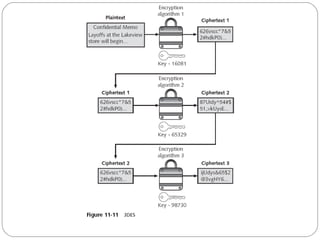
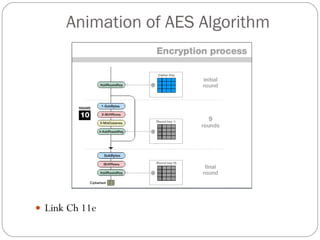
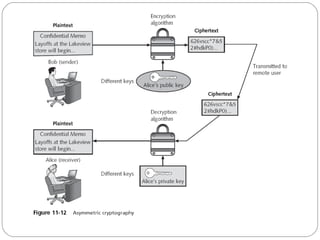
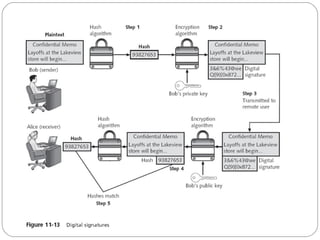
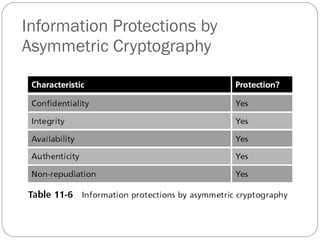
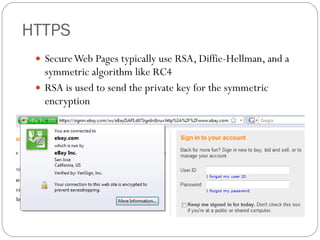
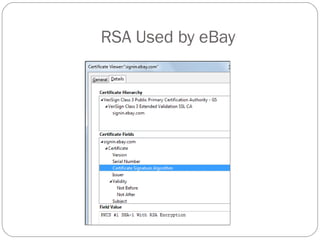
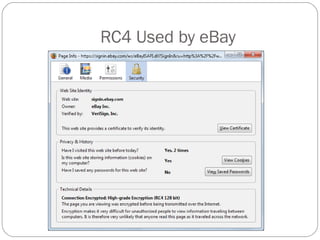
Chapter 11 of the Security+ guide covers basic cryptography, detailing its objectives, types, and operations. It explains cryptographic concepts such as encryption, decryption, hashing algorithms, and the distinction between symmetric and asymmetric cryptography. Additionally, it discusses various algorithms used in cryptography and practical applications for file and disk encryption.