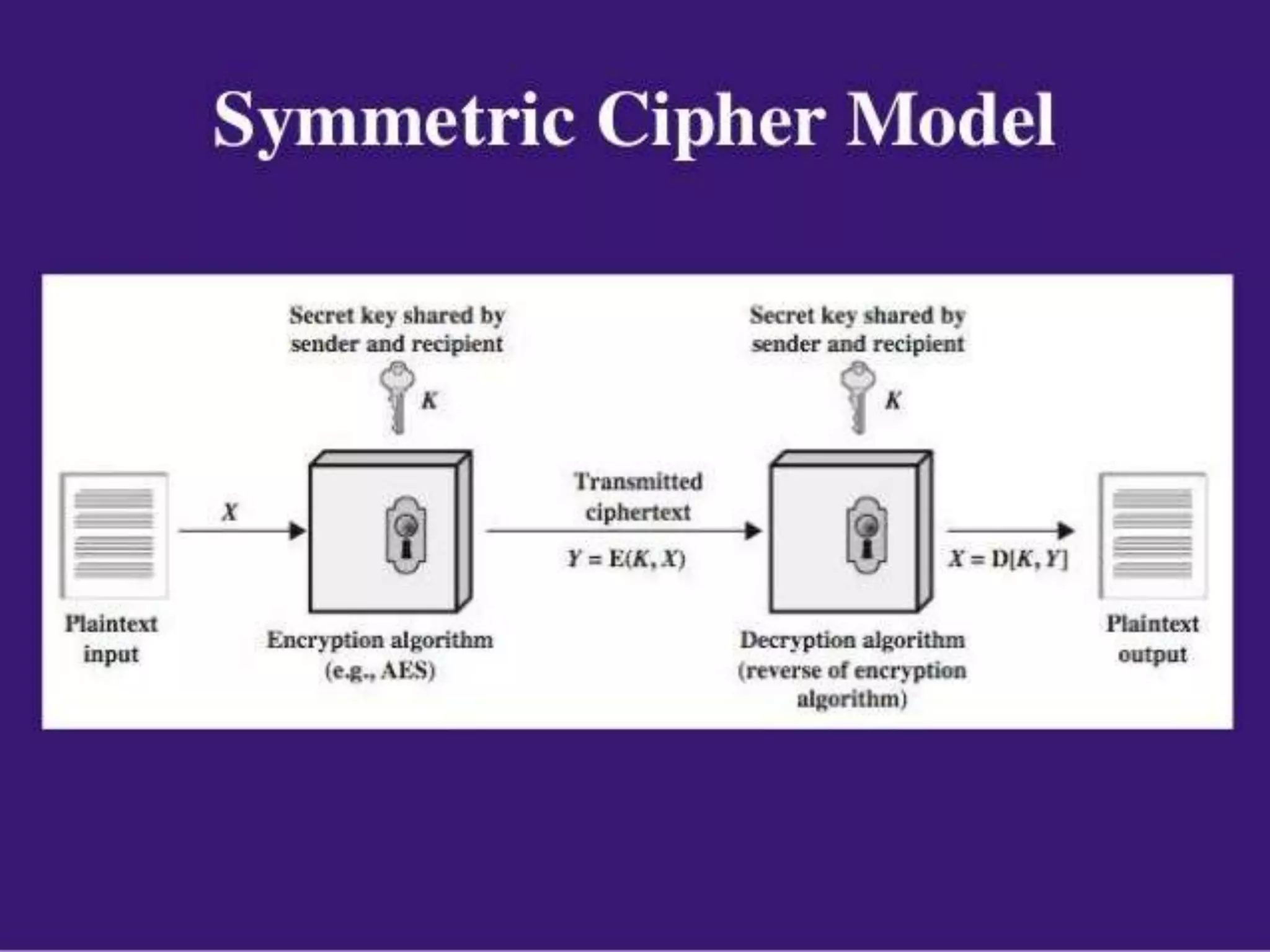
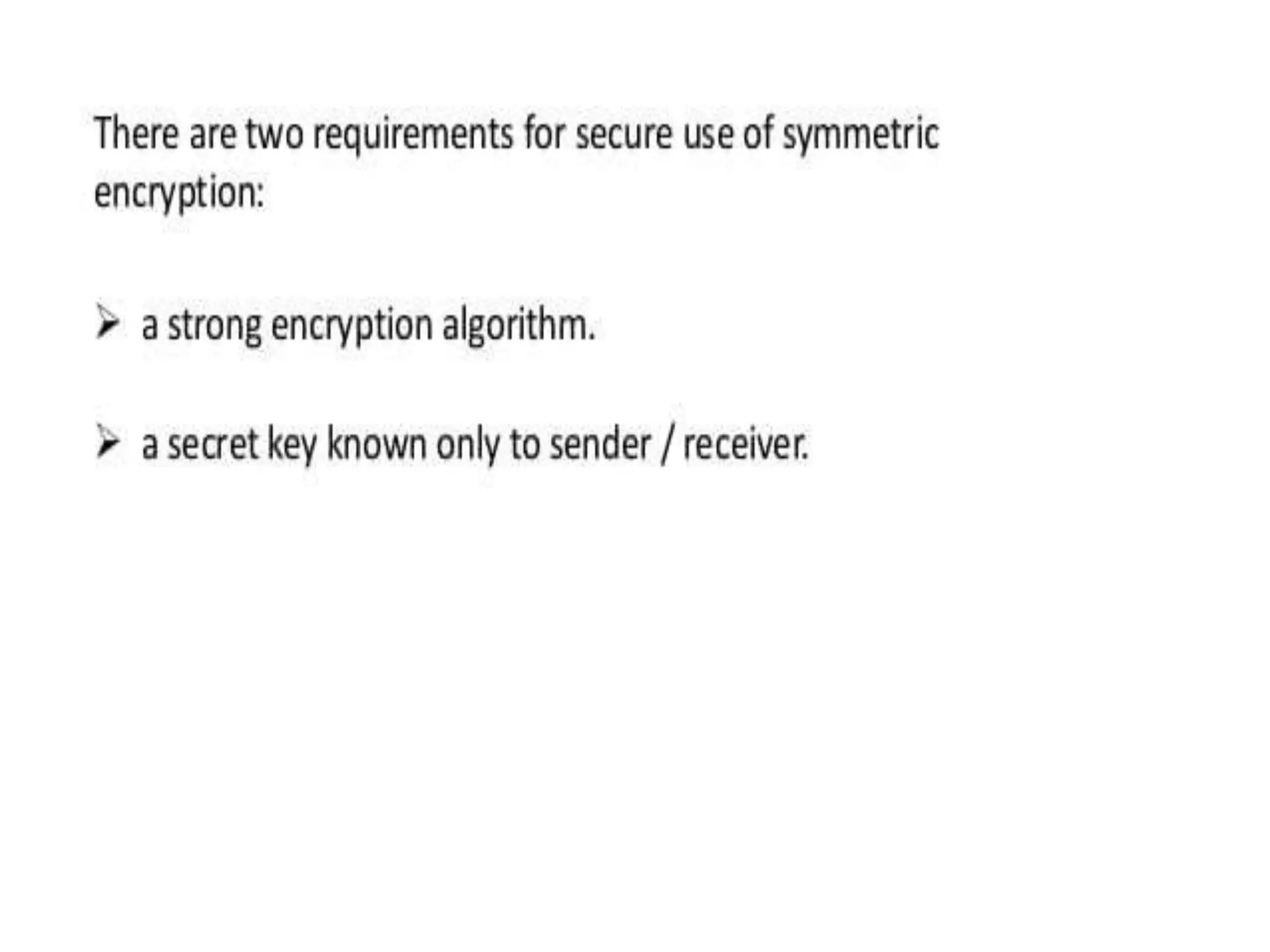
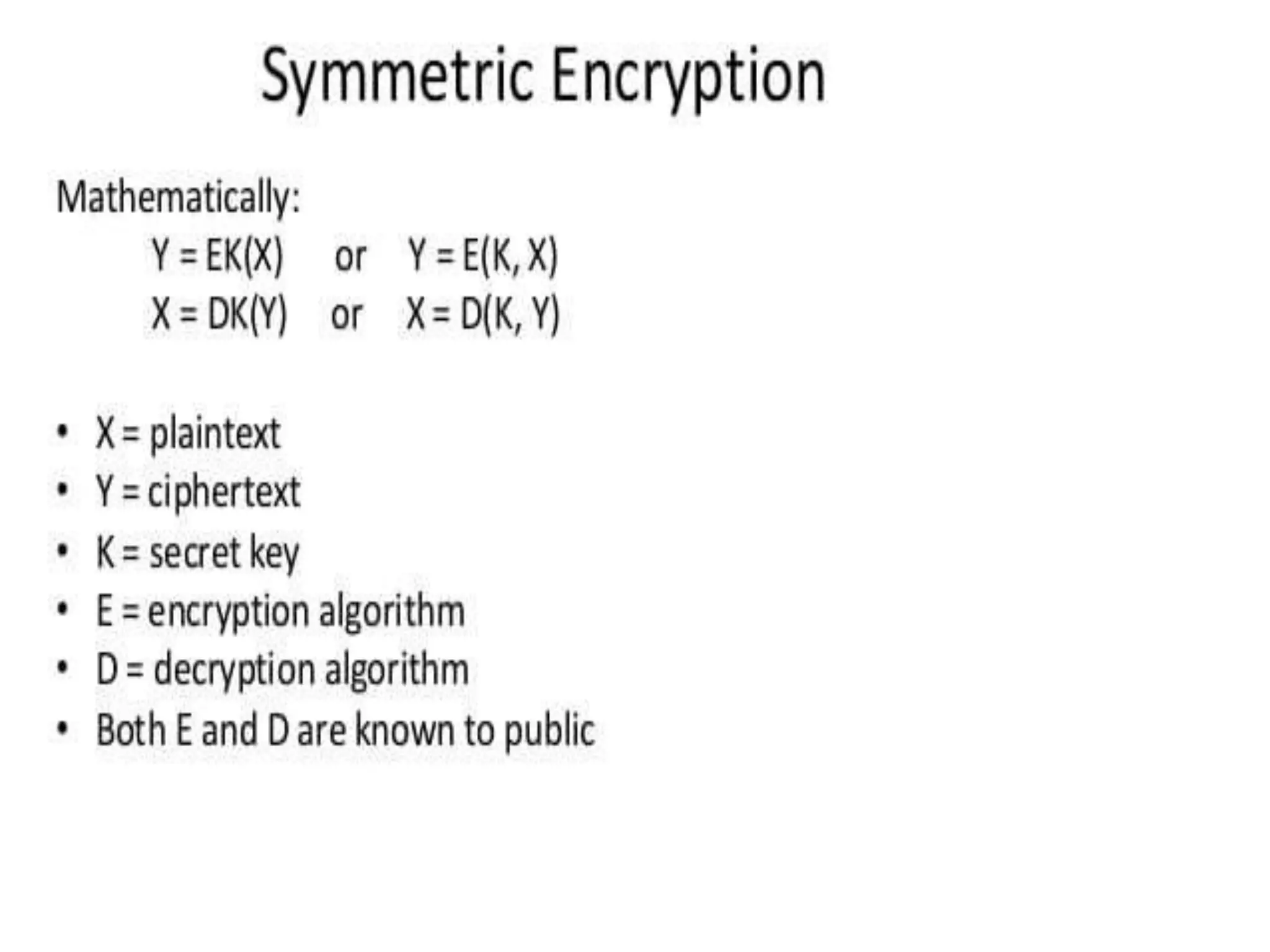
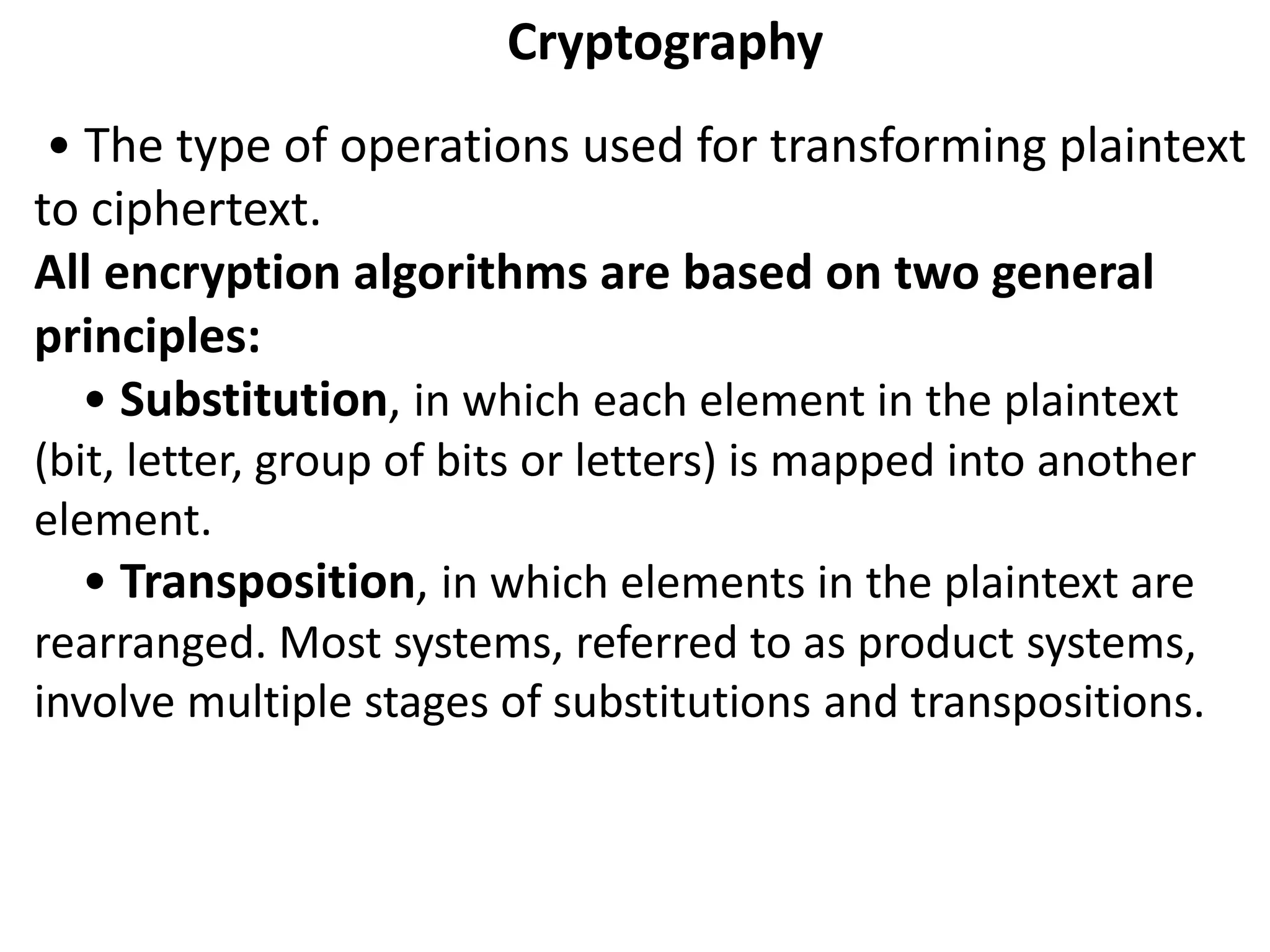
This document discusses symmetric encryption, also known as conventional or single-key encryption. Symmetric encryption uses a single key that is known to both the sender and receiver to encrypt plaintext into ciphertext and decrypt ciphertext back to plaintext. The document defines basic terminology related to symmetric encryption like plaintext, ciphertext, cipher, key, encryption, and decryption. It also discusses the principles of cryptography used in symmetric encryption like substitution and transposition ciphers. The document outlines advantages of symmetric encryption like speed but also disadvantages related to securely distributing the shared secret key between communicating parties.