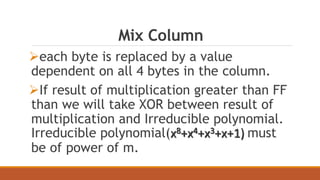
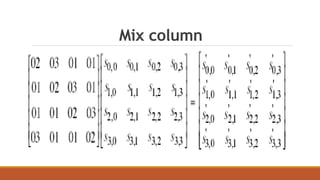
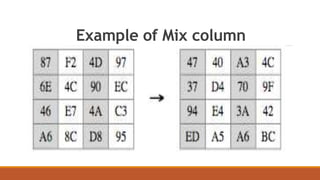
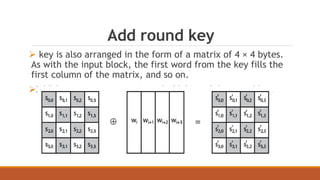
The document discusses the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that encrypts data in blocks of 128 bits using cipher keys of 128, 192, or 256 bits. It operates on a 4x4 column-major order state matrix through 10-14 rounds depending on the key size. Each round consists of four steps: byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into a key schedule to derive a different round key for each round.











![from a 4-Word
Round Key to the Next 4-Word
Round Key
The round constant for the ith round is denoted Rcon[i].
Since, by specification, the three rightmost bytes of the
round constant are zero, we can write it as shown below. The
left hand side of the equation below stands for the round
constant to be used in the ith round. The right hand side of
the equation says that the rightmost three bytes of the round
constant are zero.
Rcon[i] = (RC[i], 0x00, 0x00, 0x00)
The addition of the round constants is for the purpose of
destroying any symmetries that may have been introduced by
the other steps in the key expansion algorithm.](https://image.slidesharecdn.com/aes-141108014118-conversion-gate02/85/Aes-19-320.jpg)