This document provides an overview of cryptography concepts including:
- Cryptography is the study of encrypted information and involves encryption to convert plaintext to ciphertext and decryption to convert ciphertext back to plaintext.
- Ciphers use algorithms and keys to encrypt and decrypt messages, with symmetric encryption using the same key and asymmetric encryption using different keys.
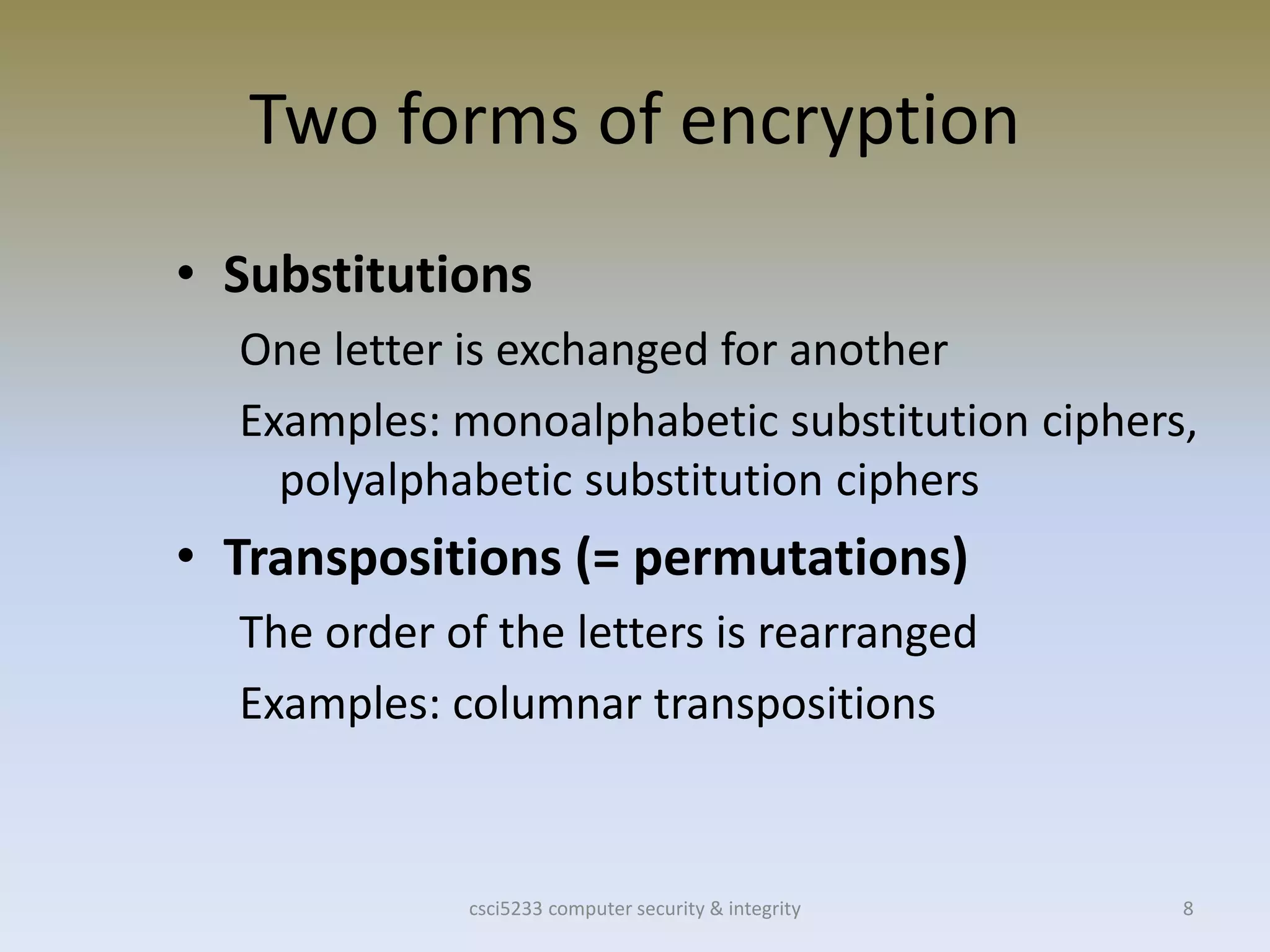
- Common encryption methods include substitution ciphers that swap letters and transposition ciphers that rearrange letters.
- Cryptanalysis involves decrypting messages without the key by analyzing patterns and weaknesses in encryption algorithms.