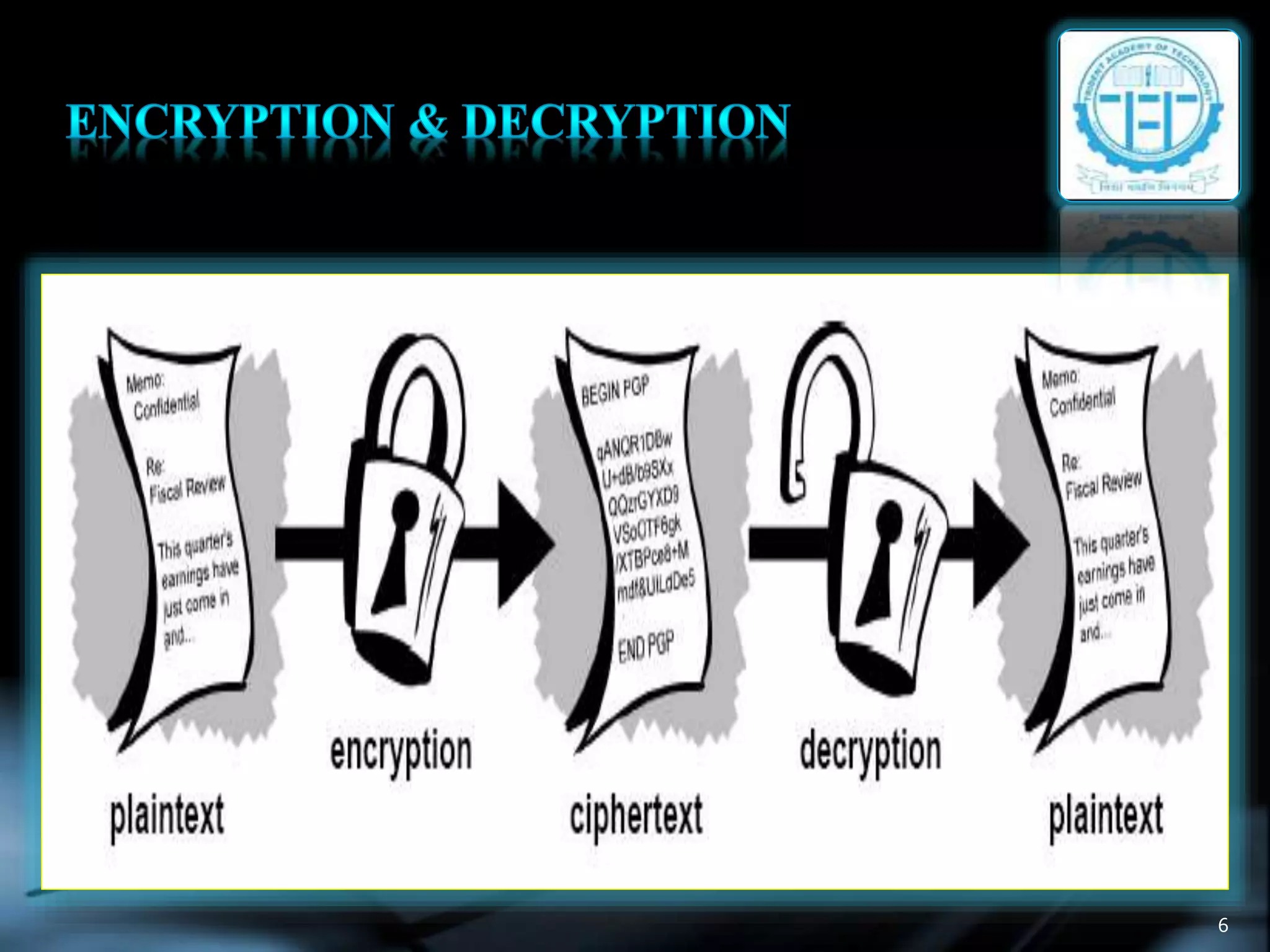
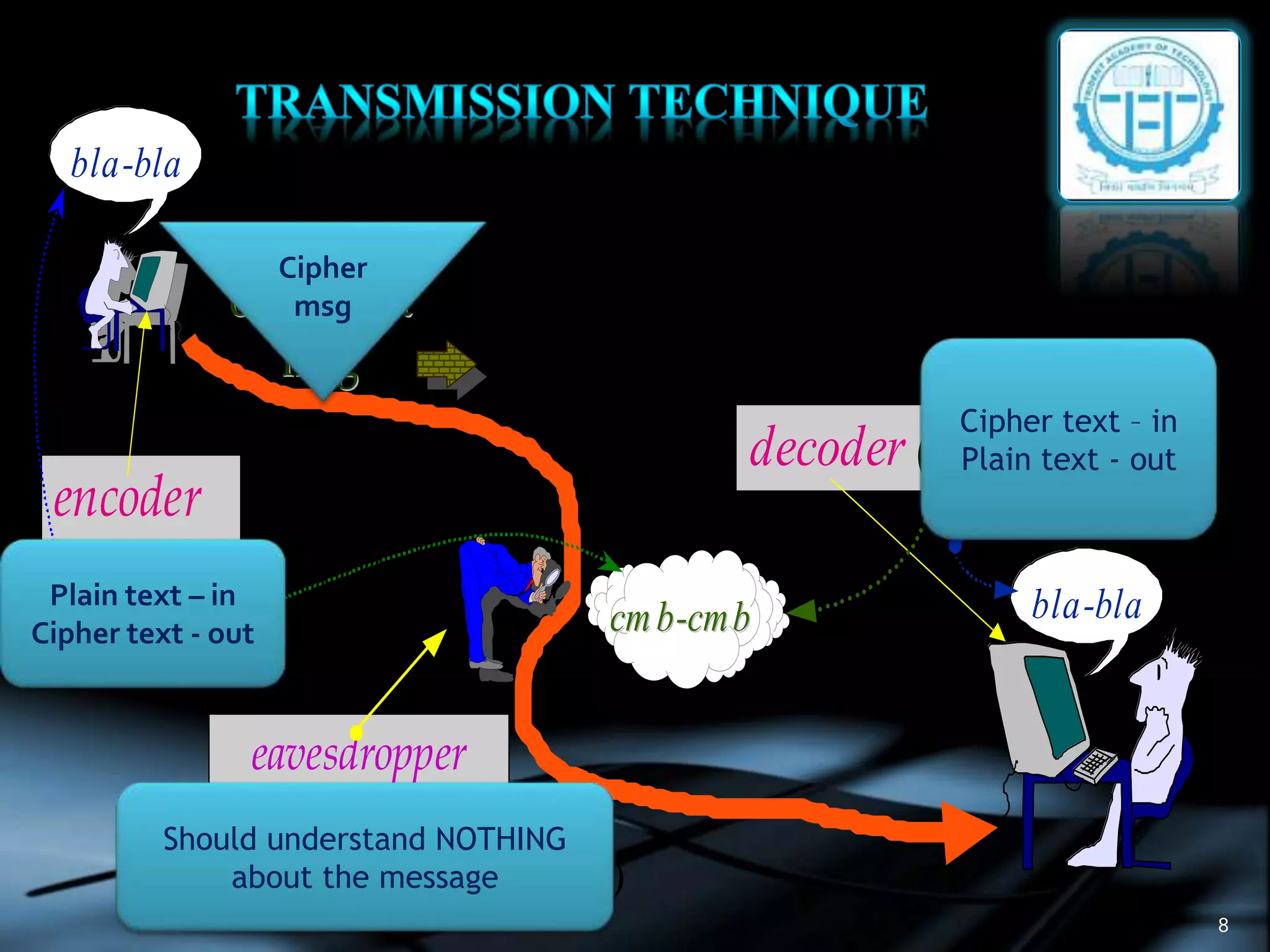
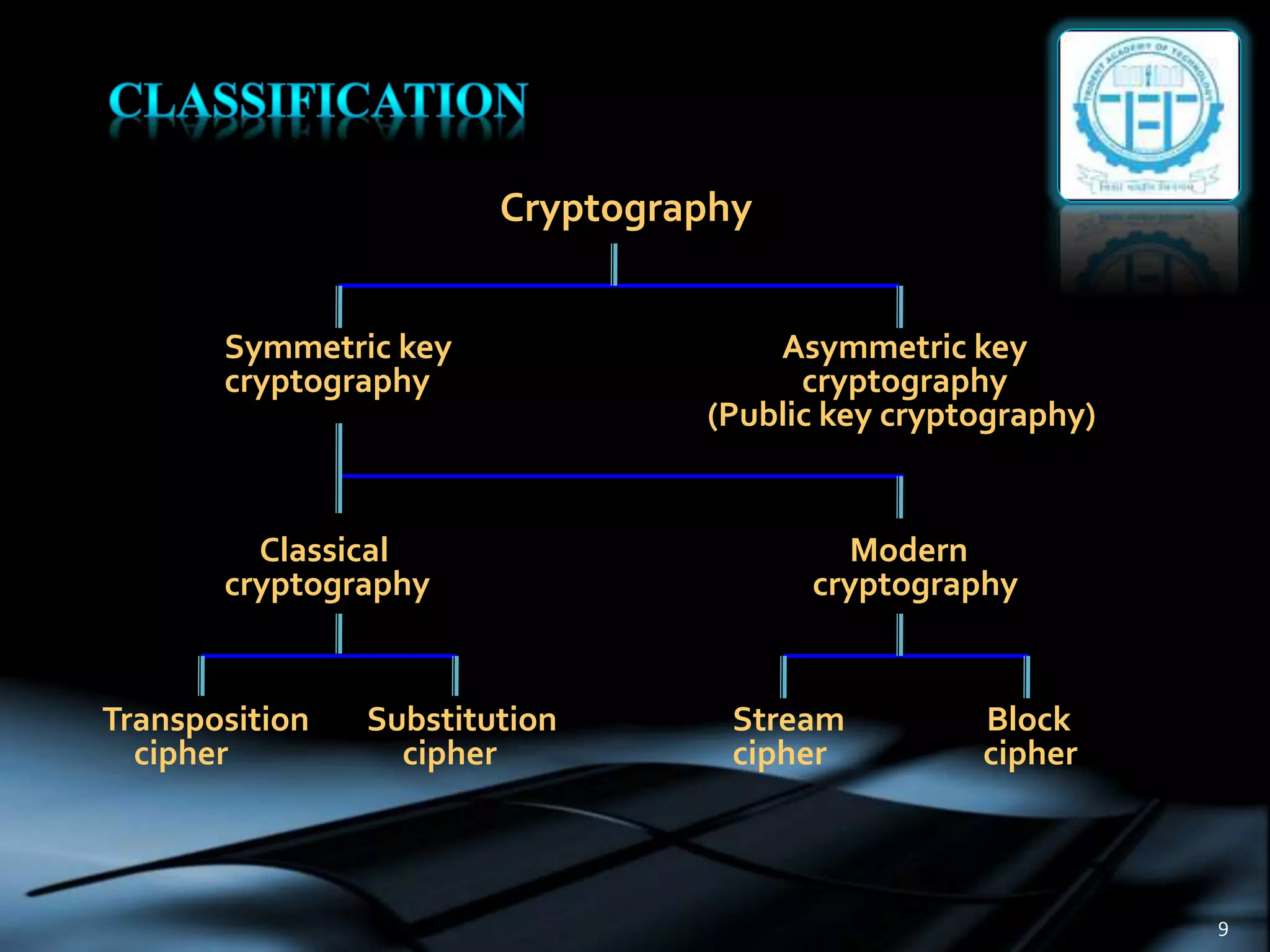
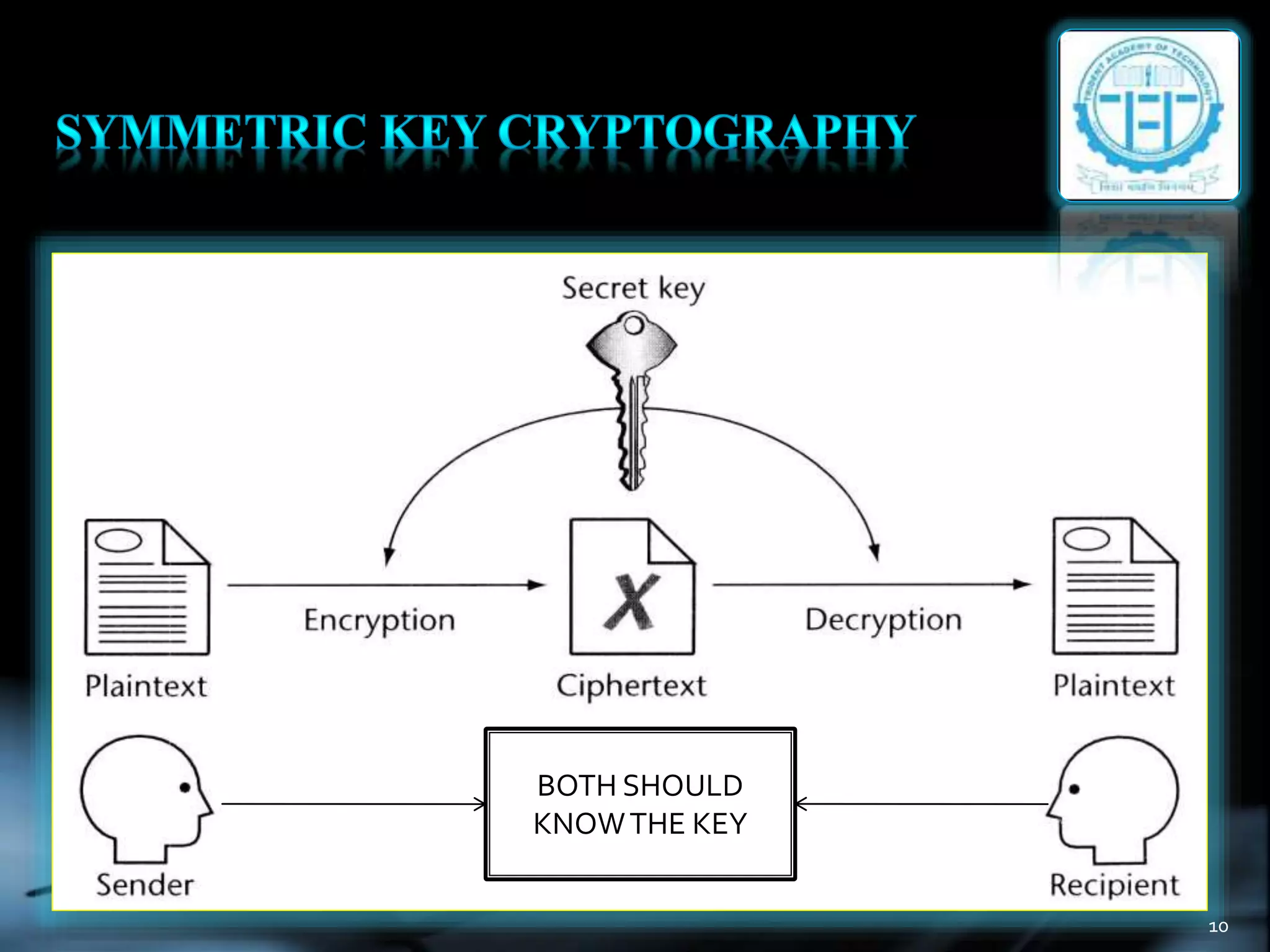
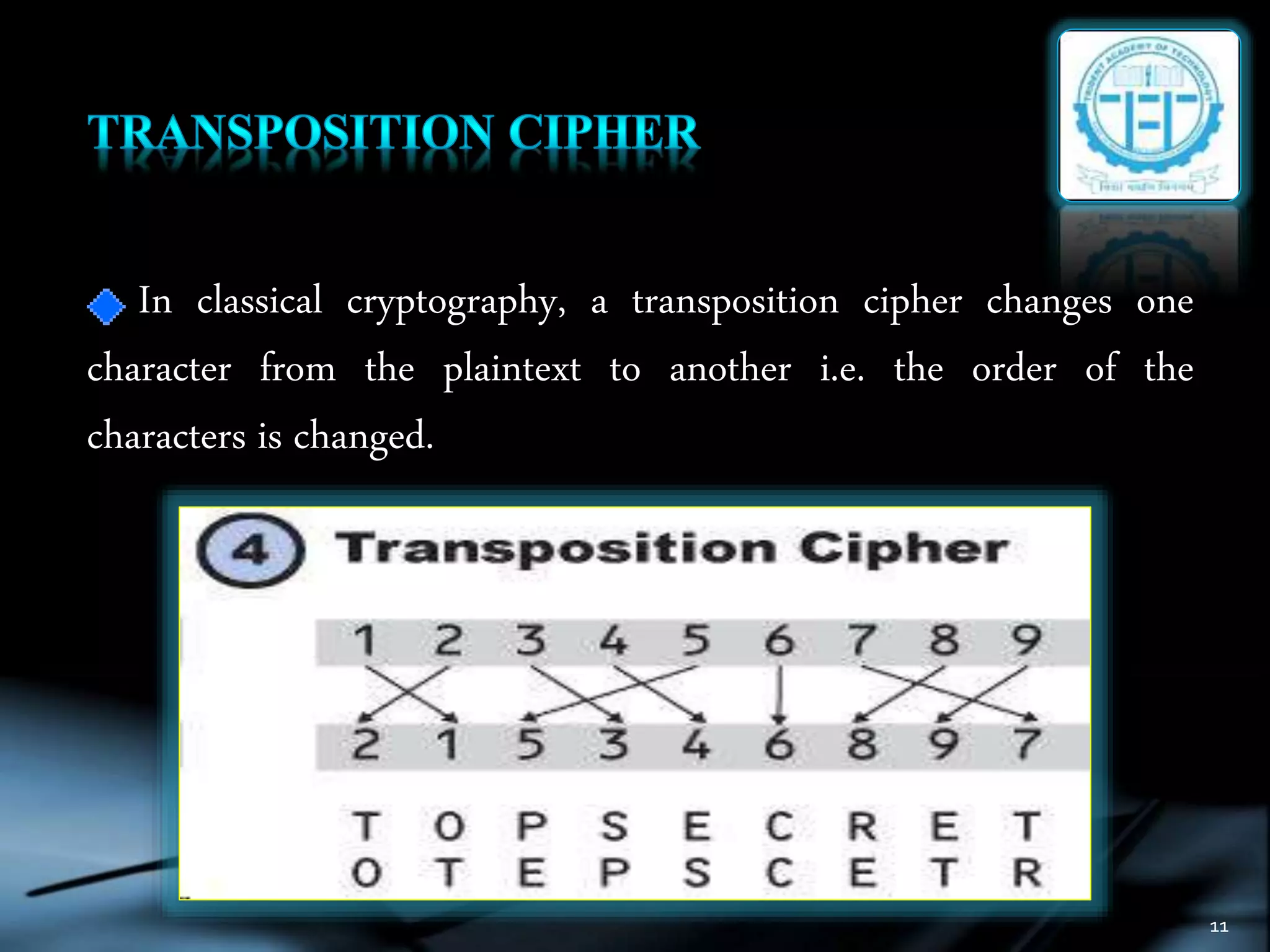
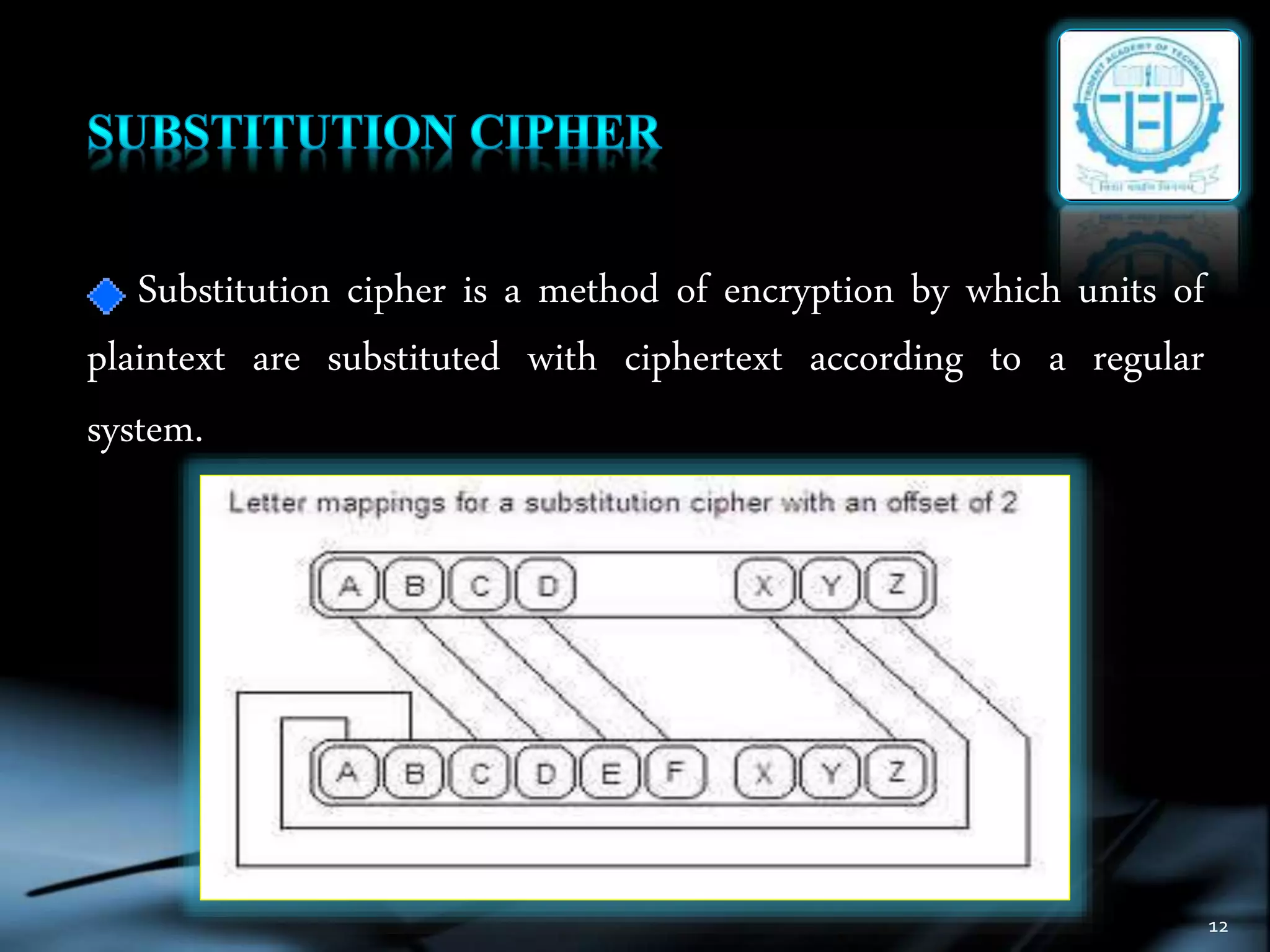
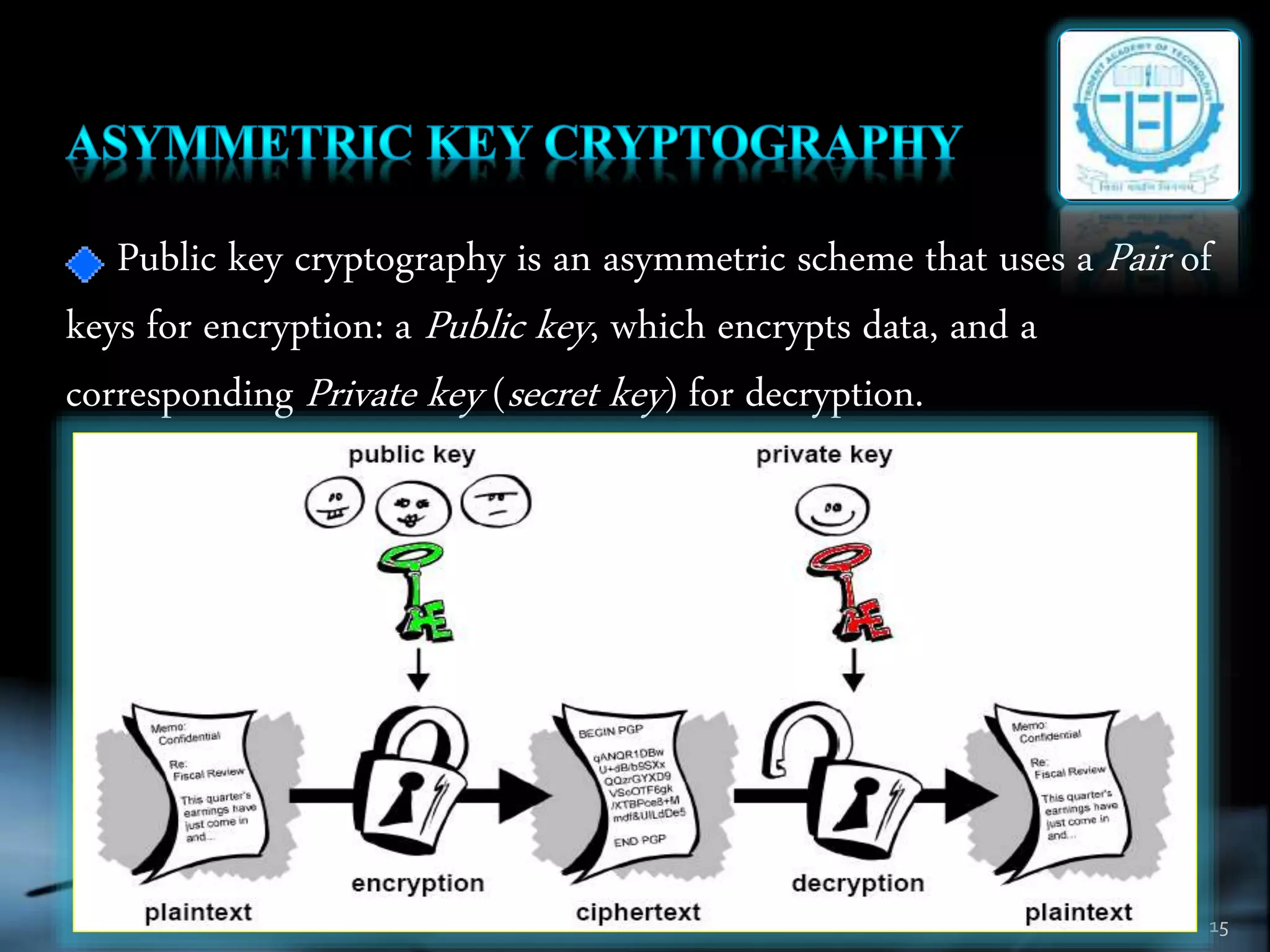
The document discusses various topics in cryptography including encryption, decryption, symmetric and asymmetric cryptography. It defines common cryptography terms like plaintext, ciphertext, encryption, decryption. It explains different encryption techniques like transposition cipher, substitution cipher, stream cipher and block cipher. It also discusses public key cryptography and cryptanalysis. The document concludes by mentioning some techniques to implement network security using cryptography and potential constructive and destructive uses of acoustic cryptanalysis.