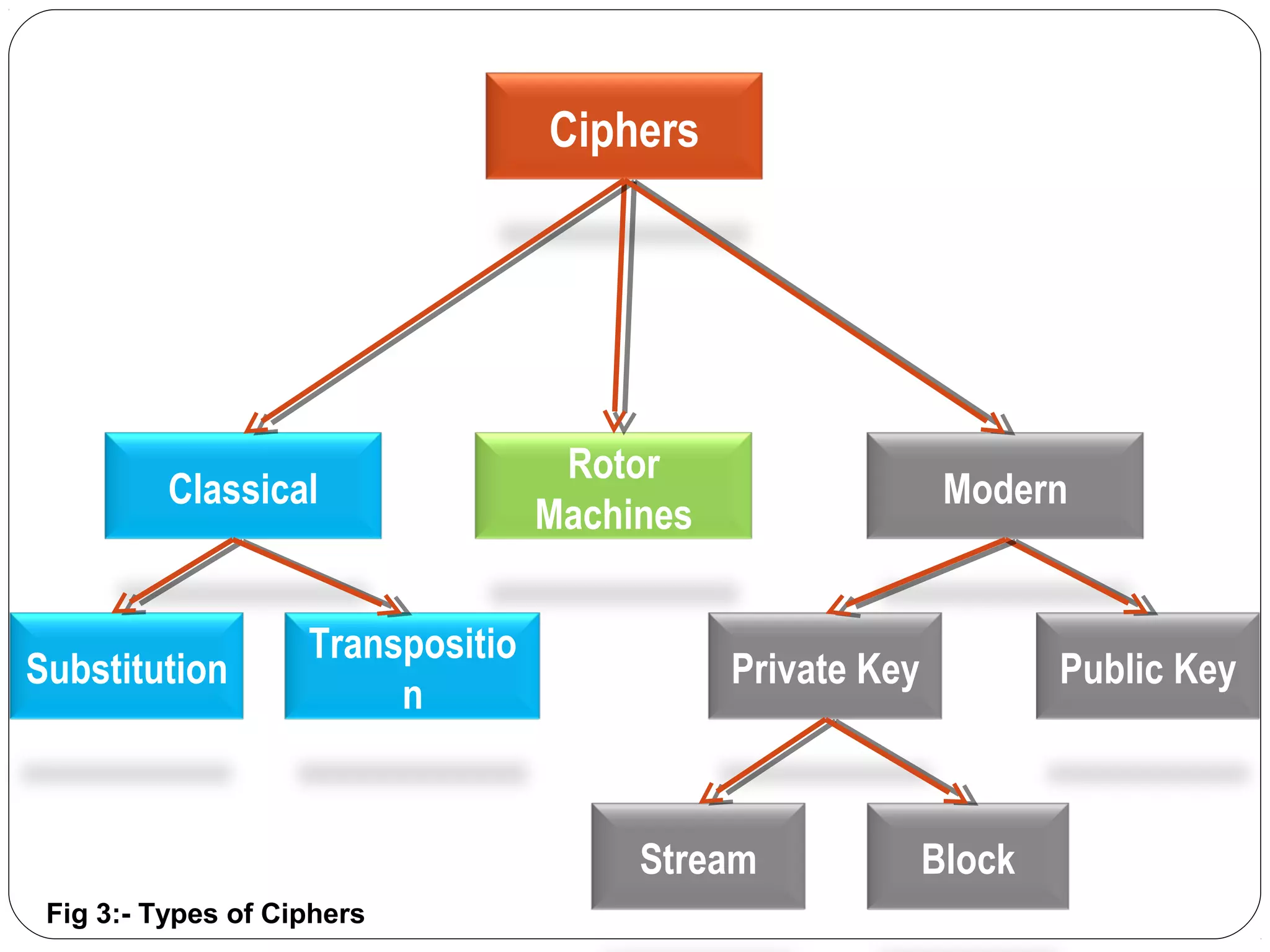
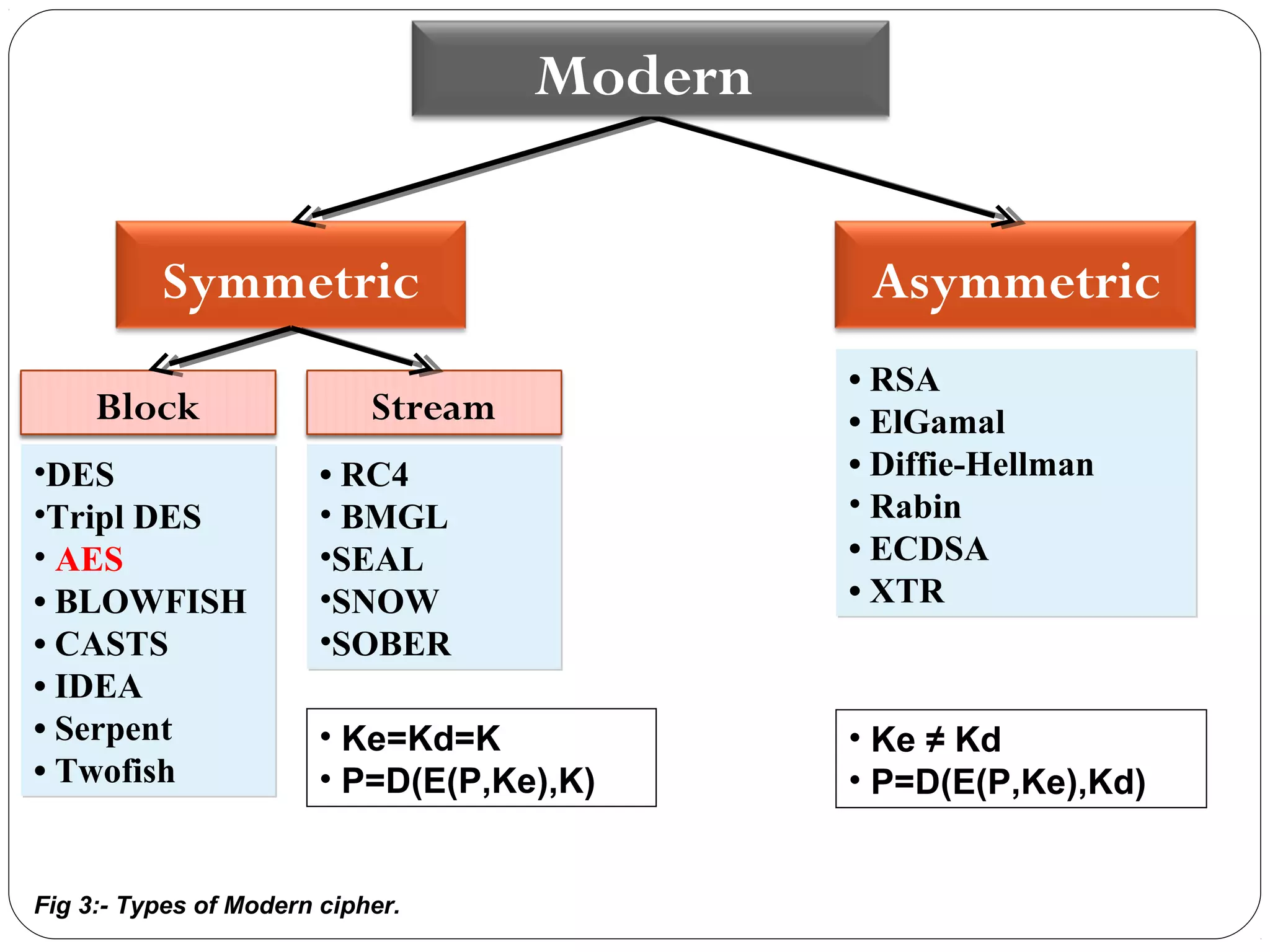
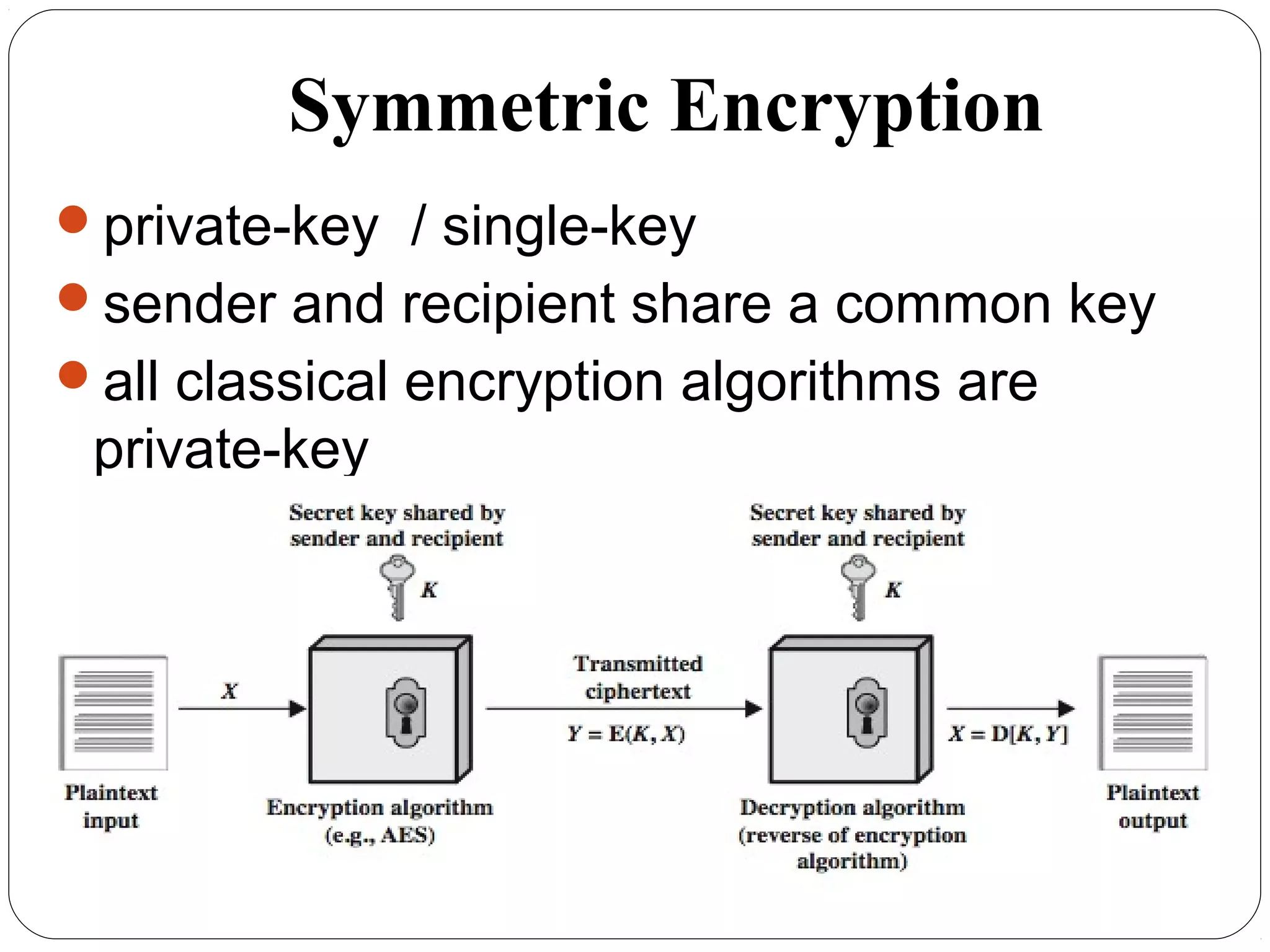
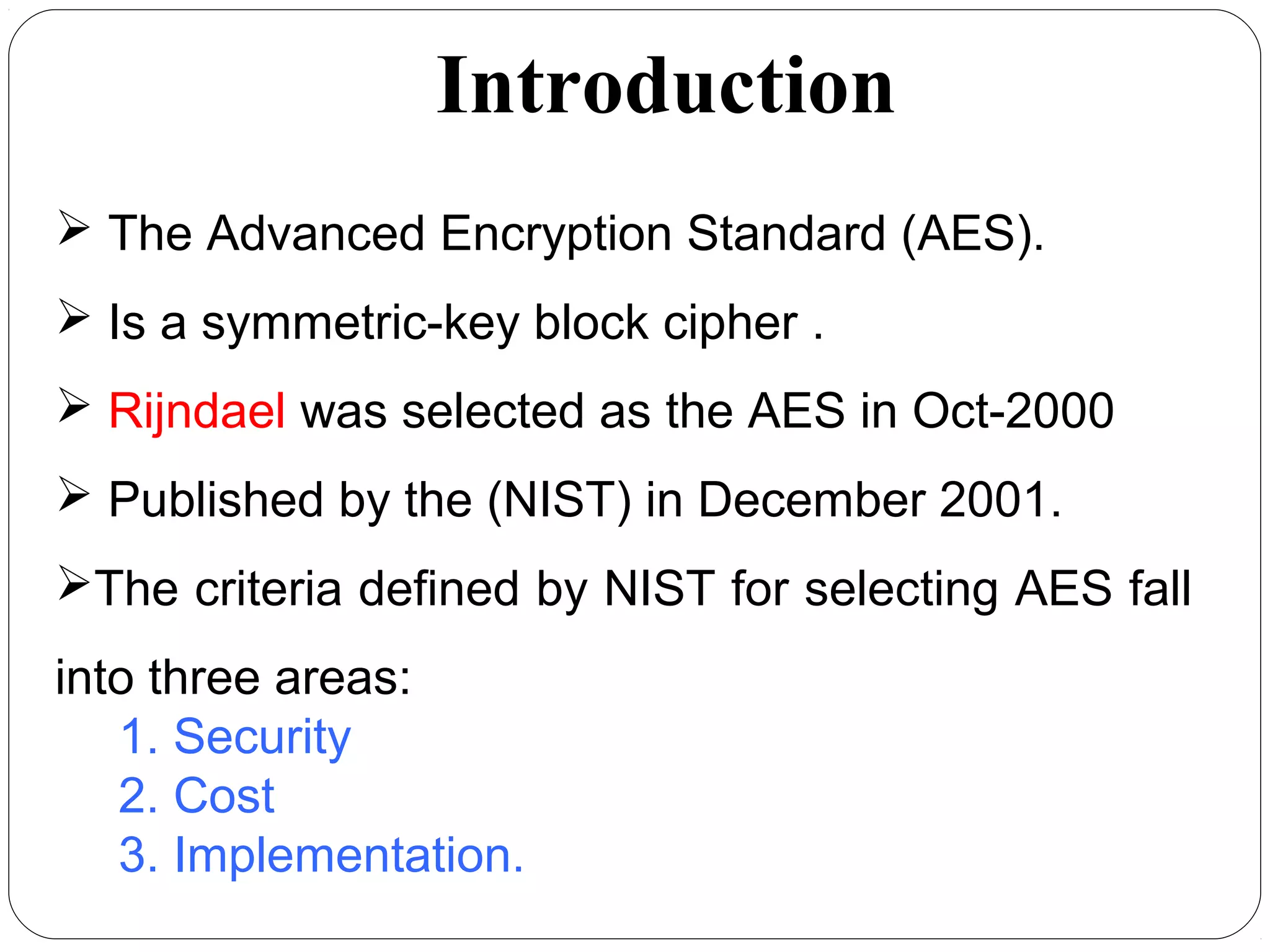
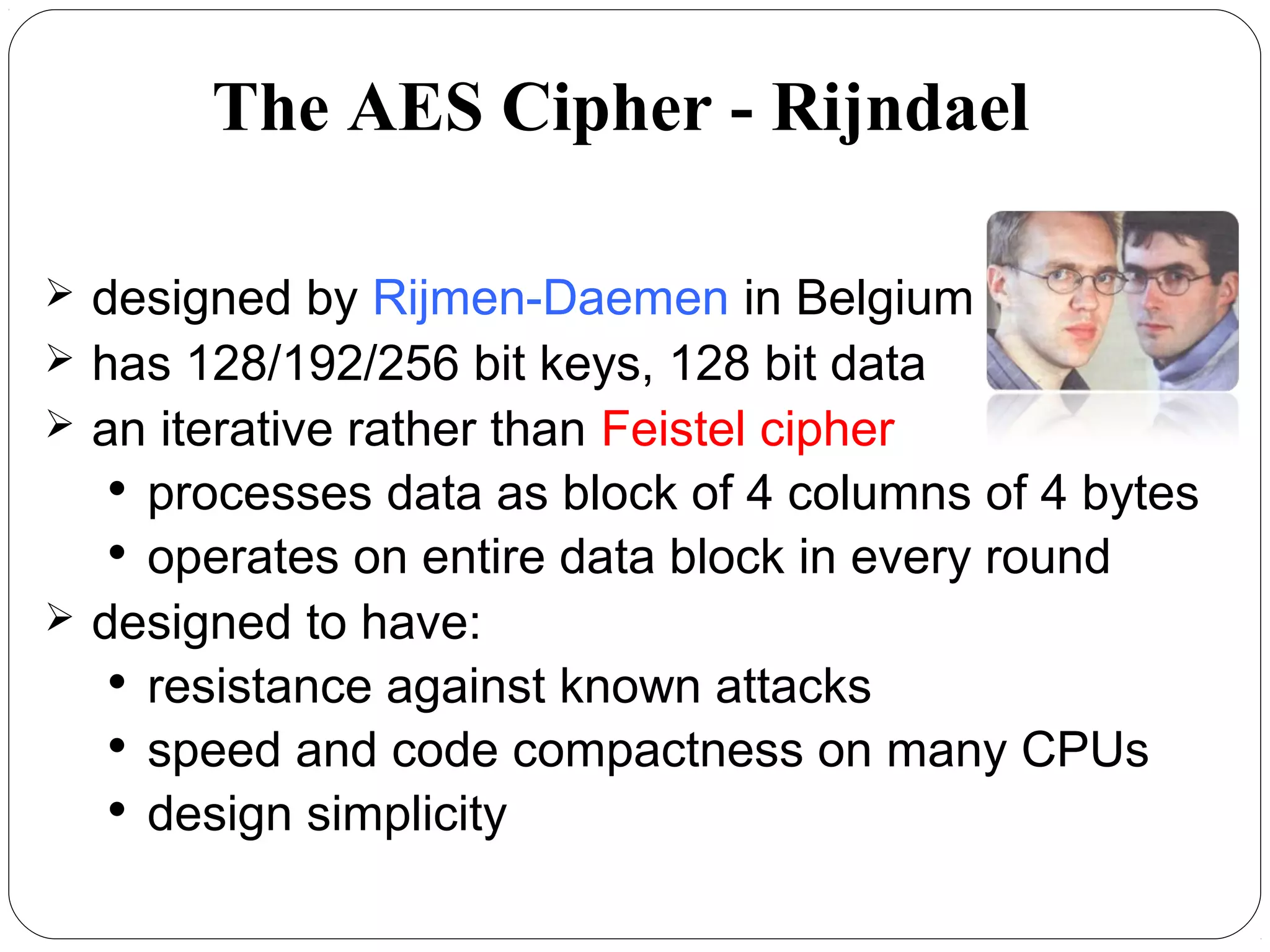
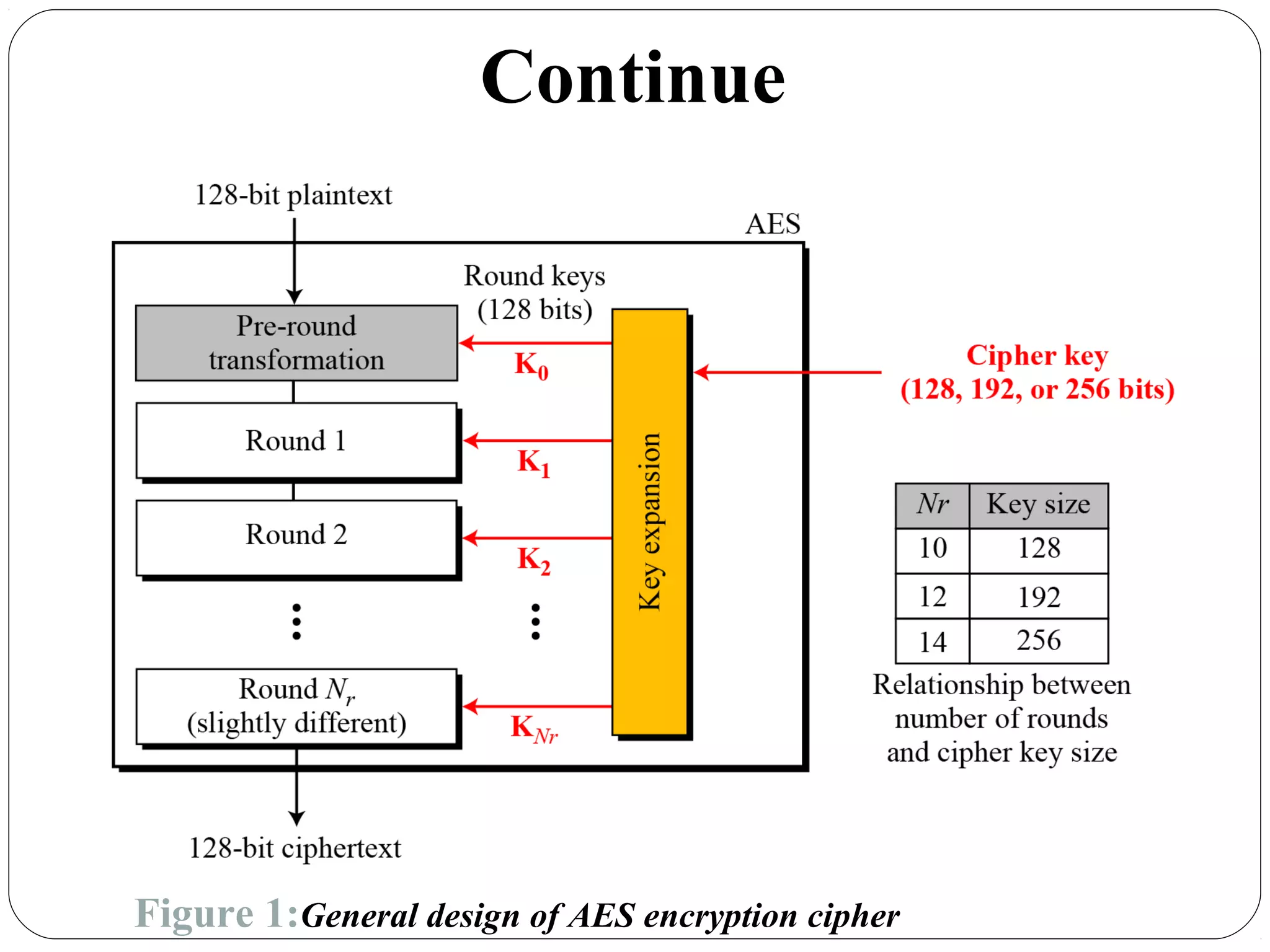
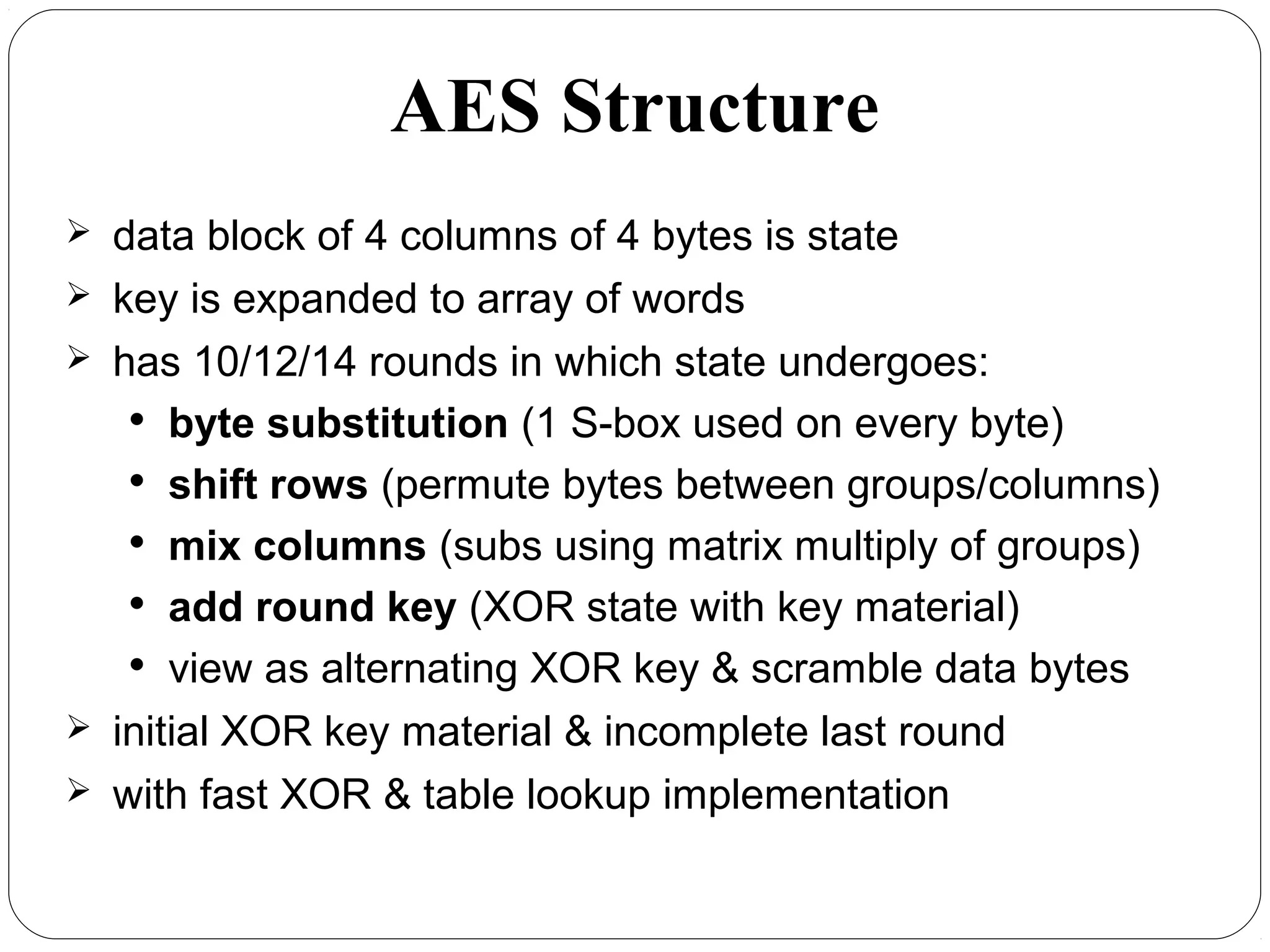
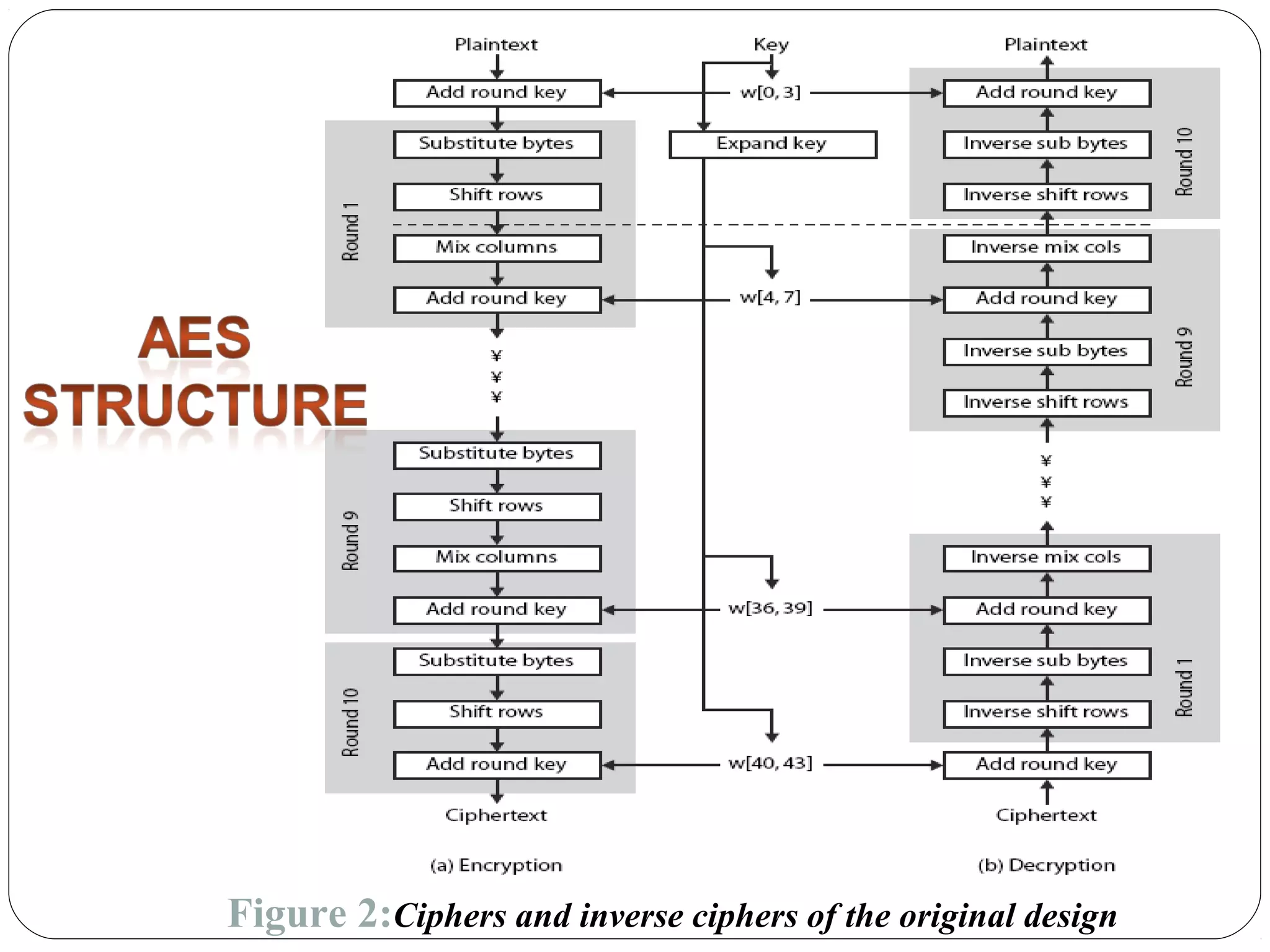
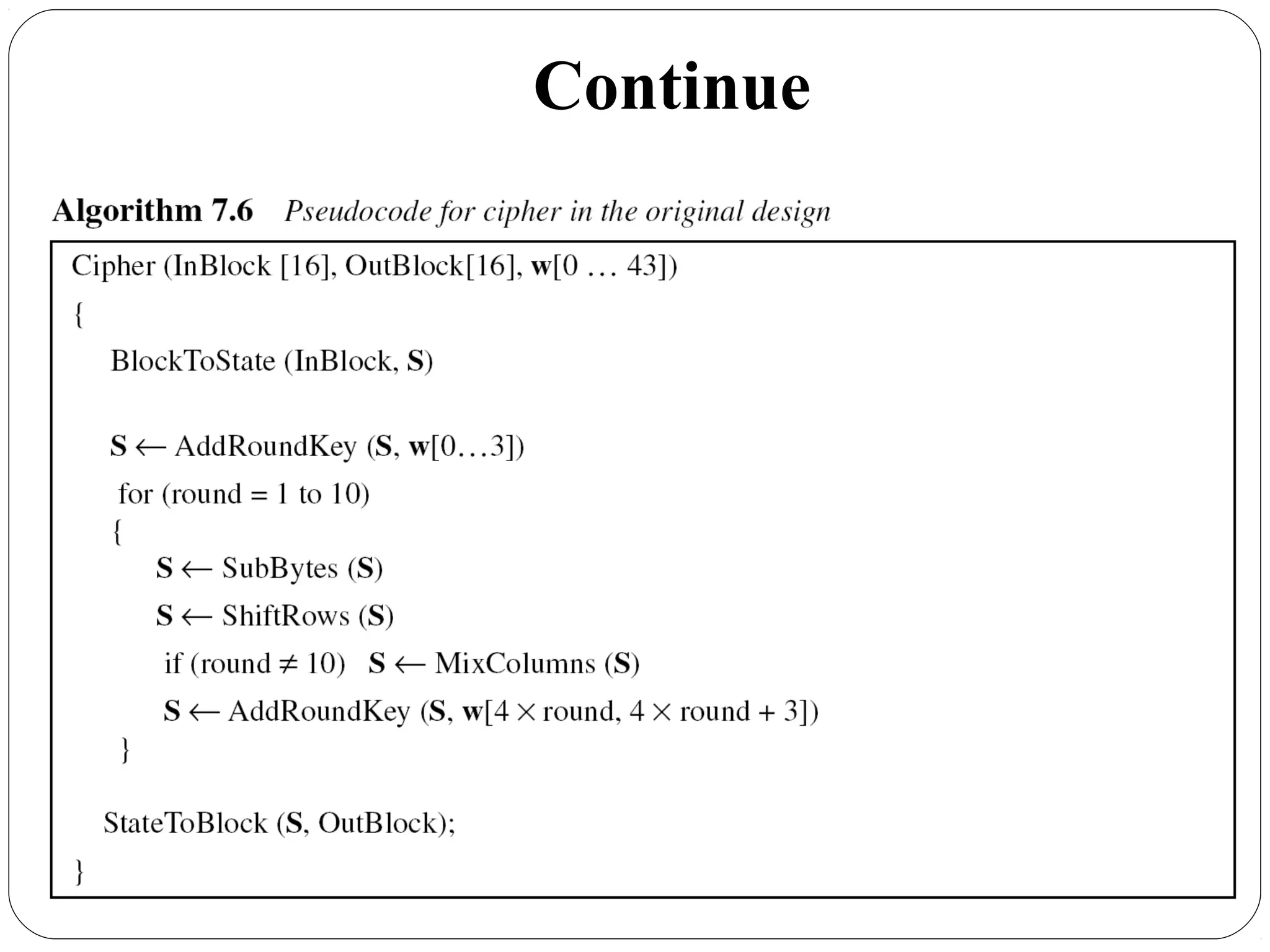
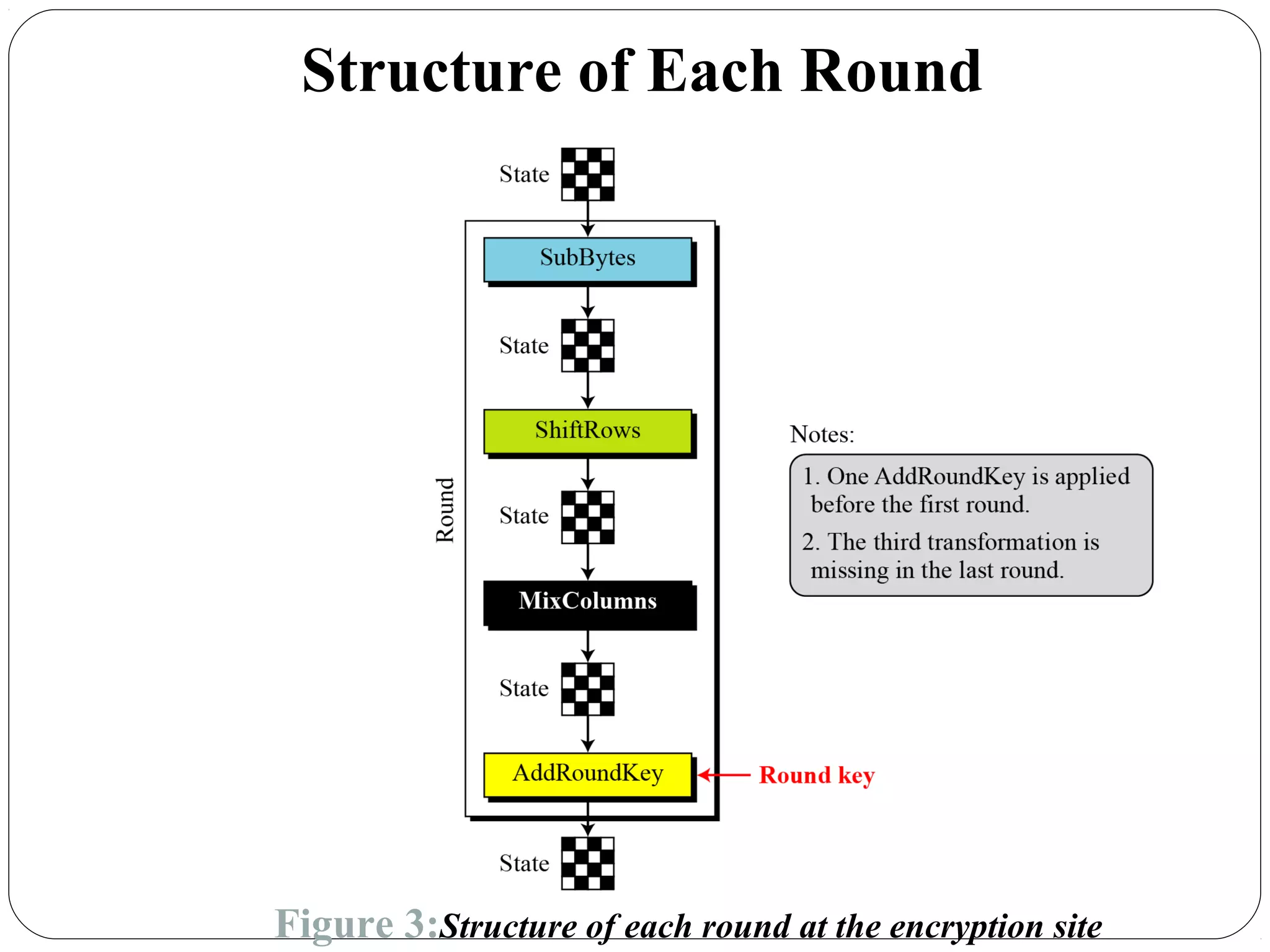
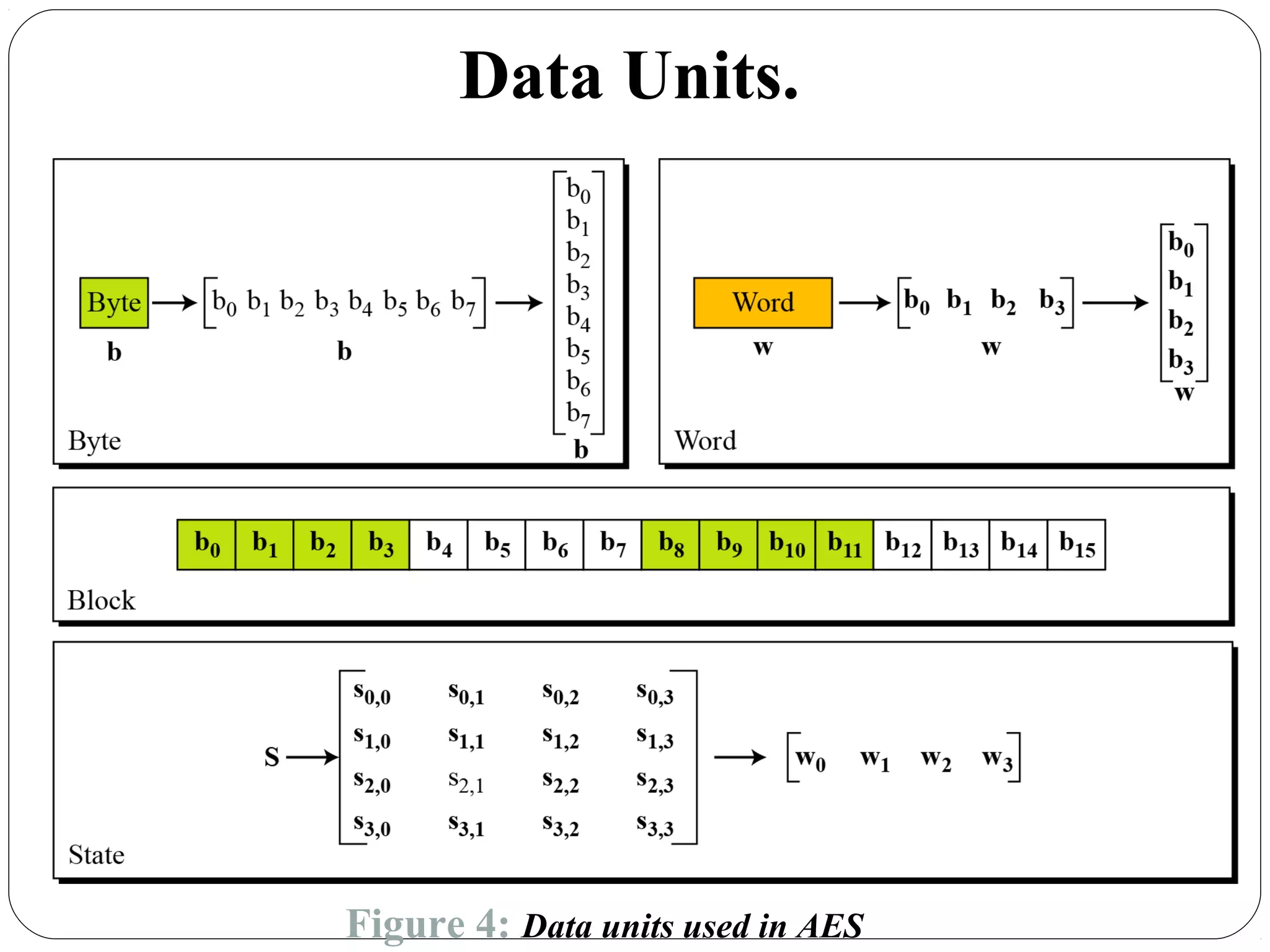
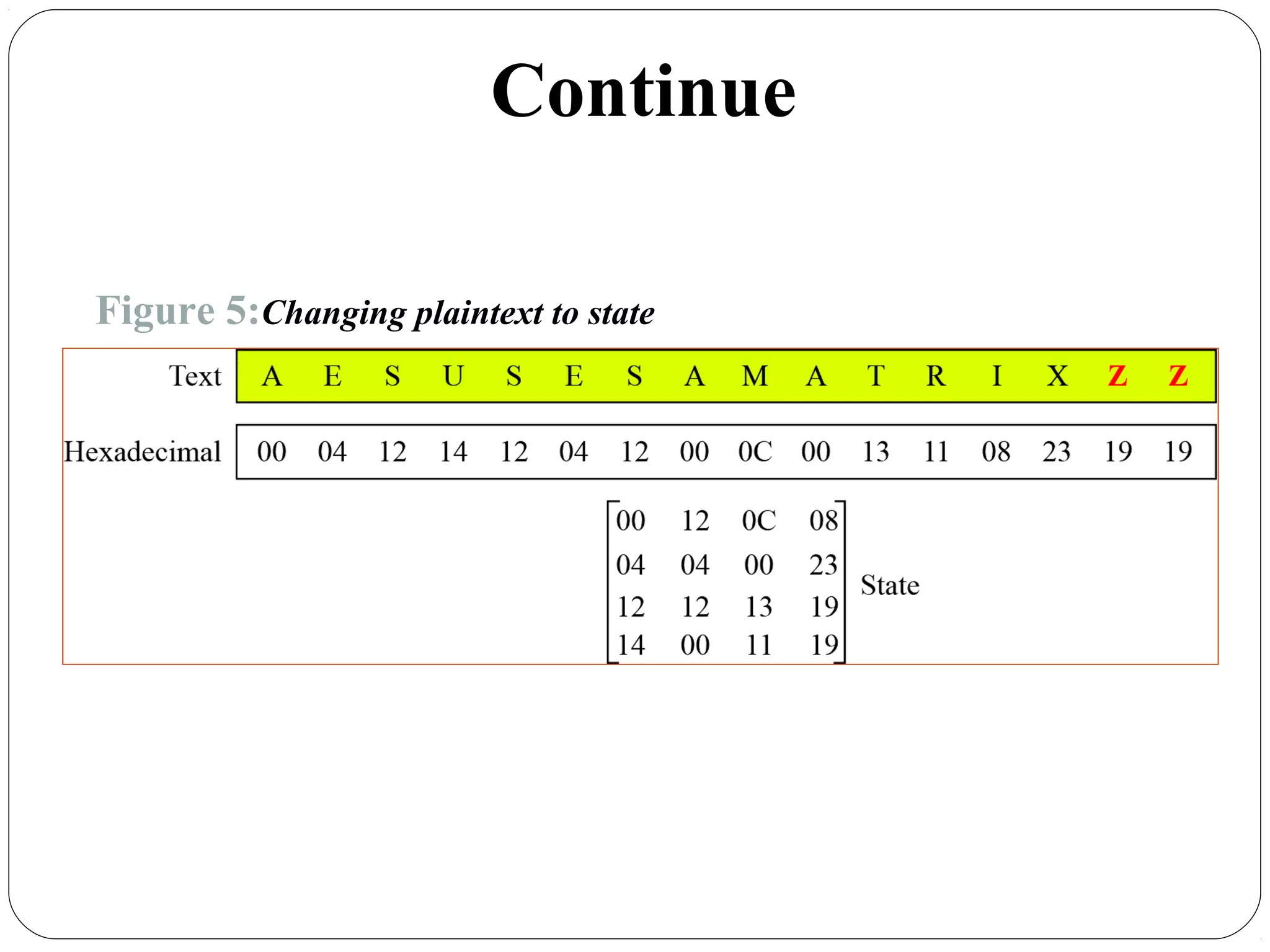
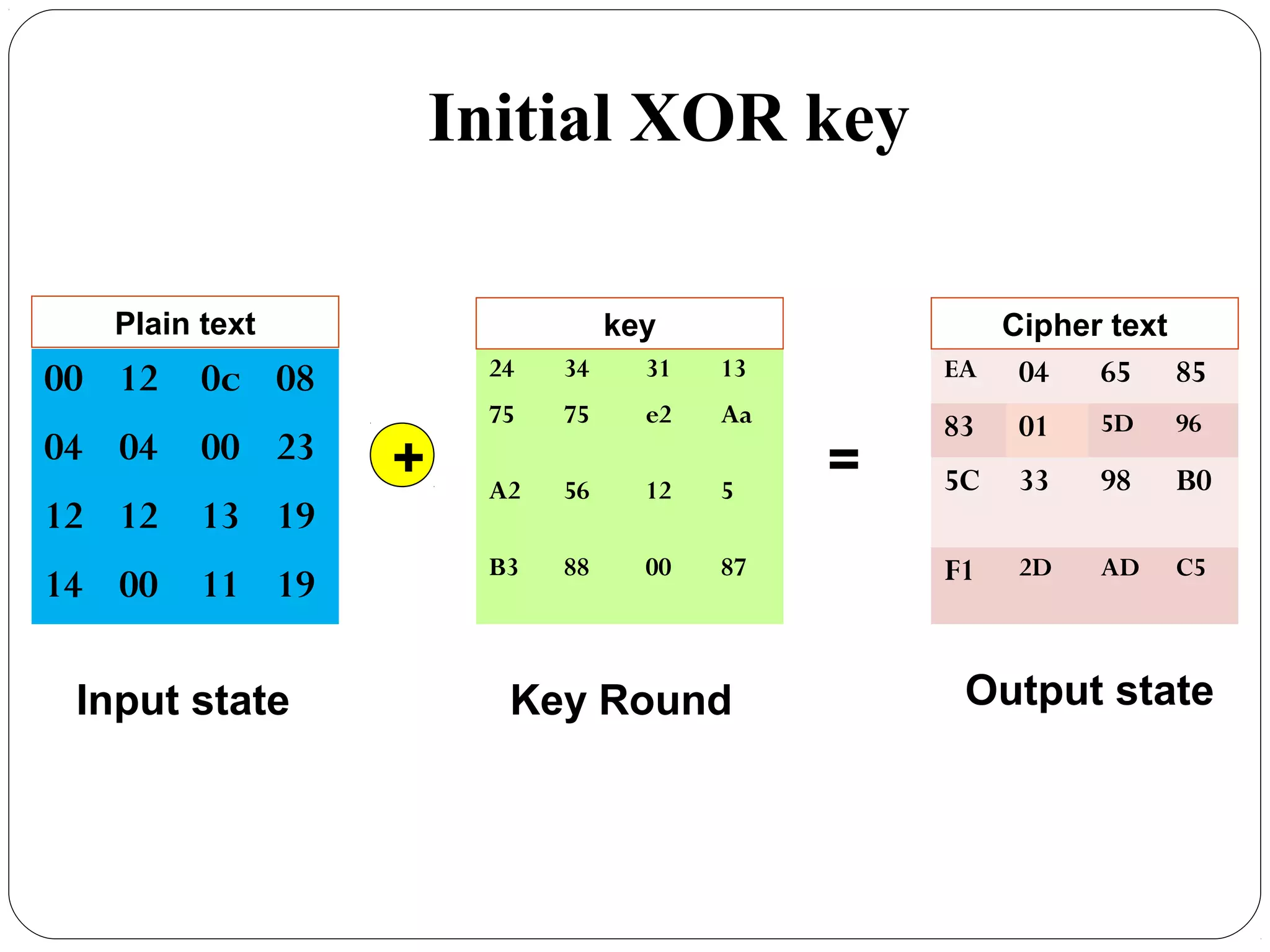
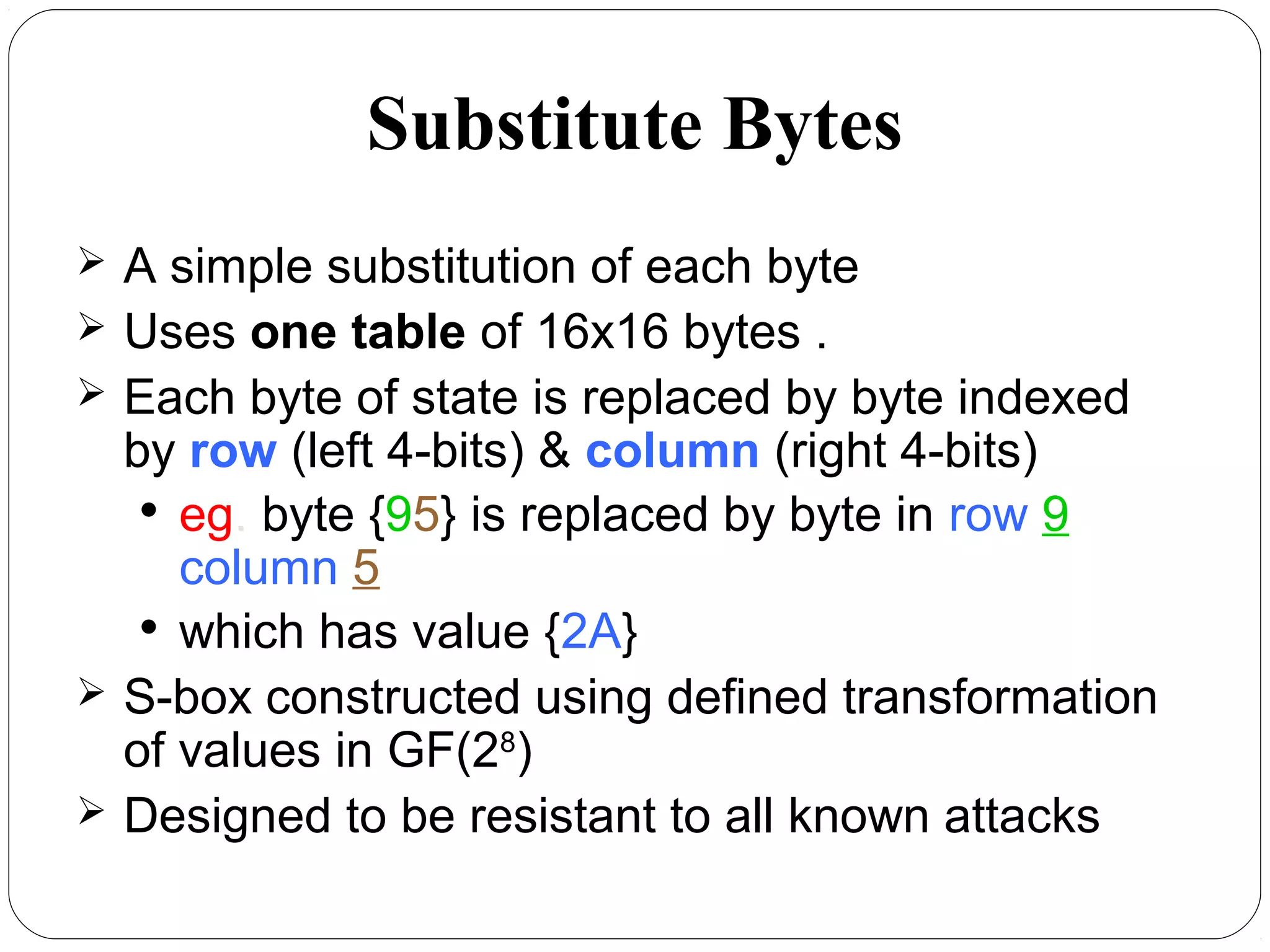
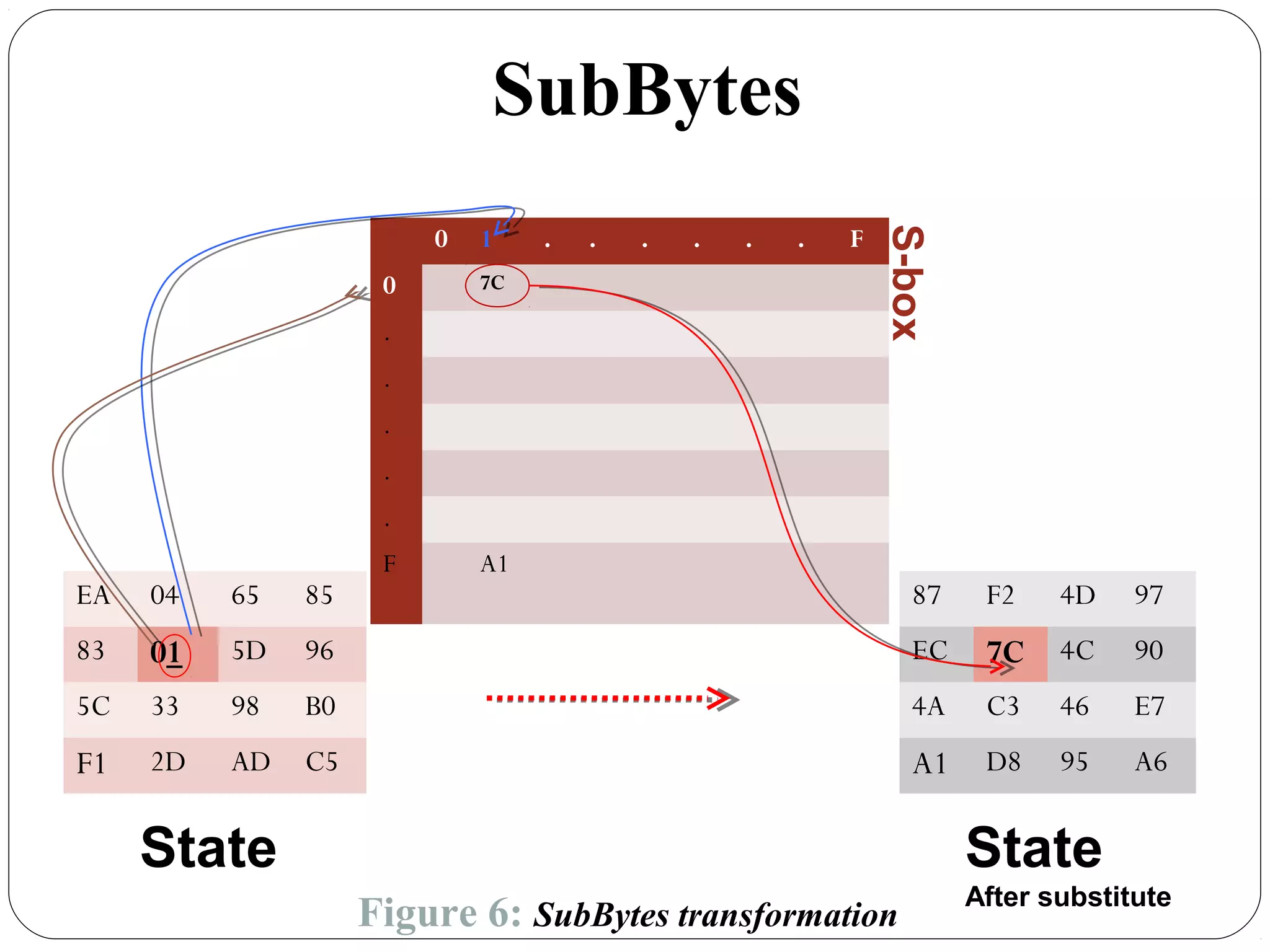
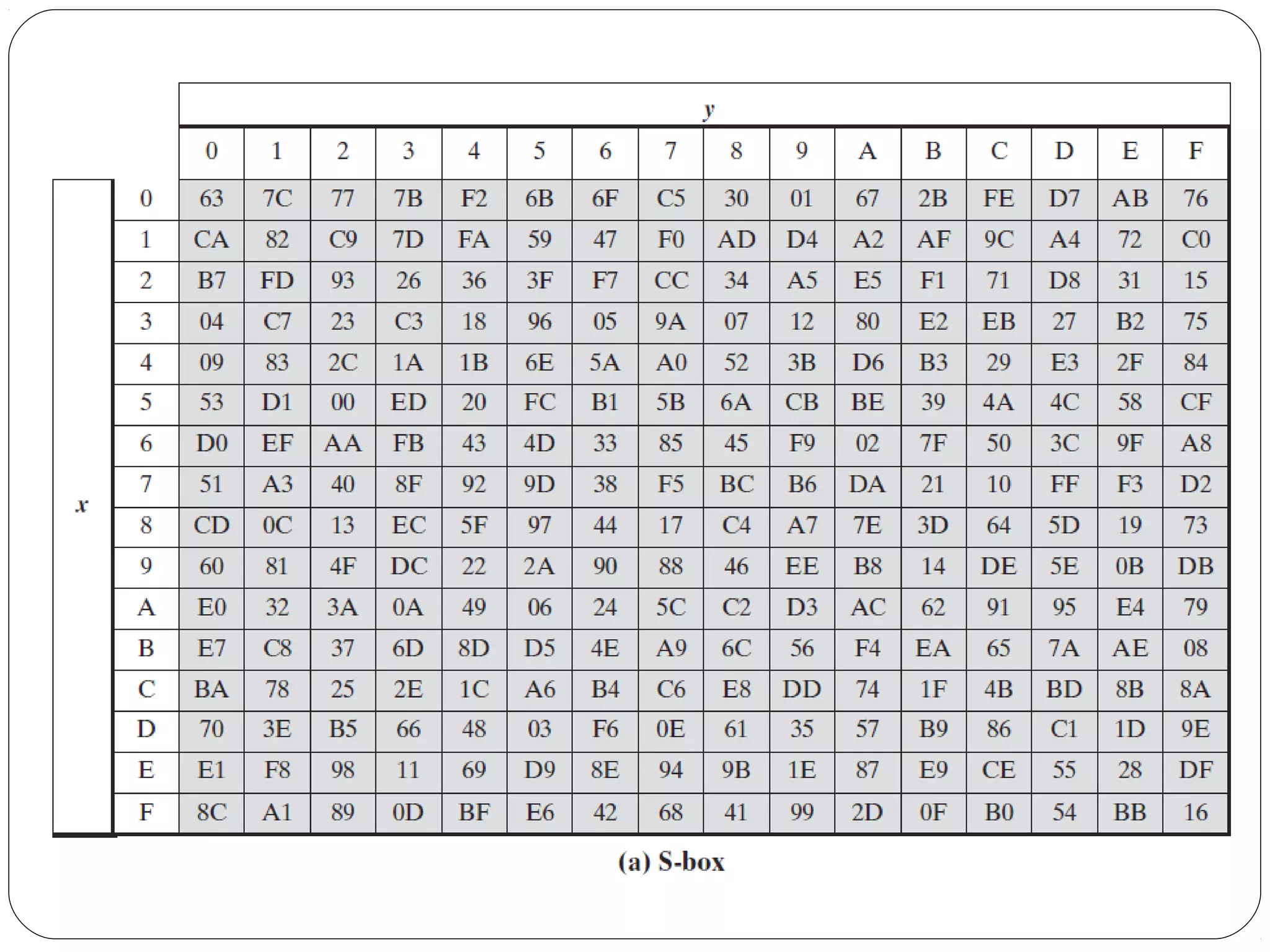
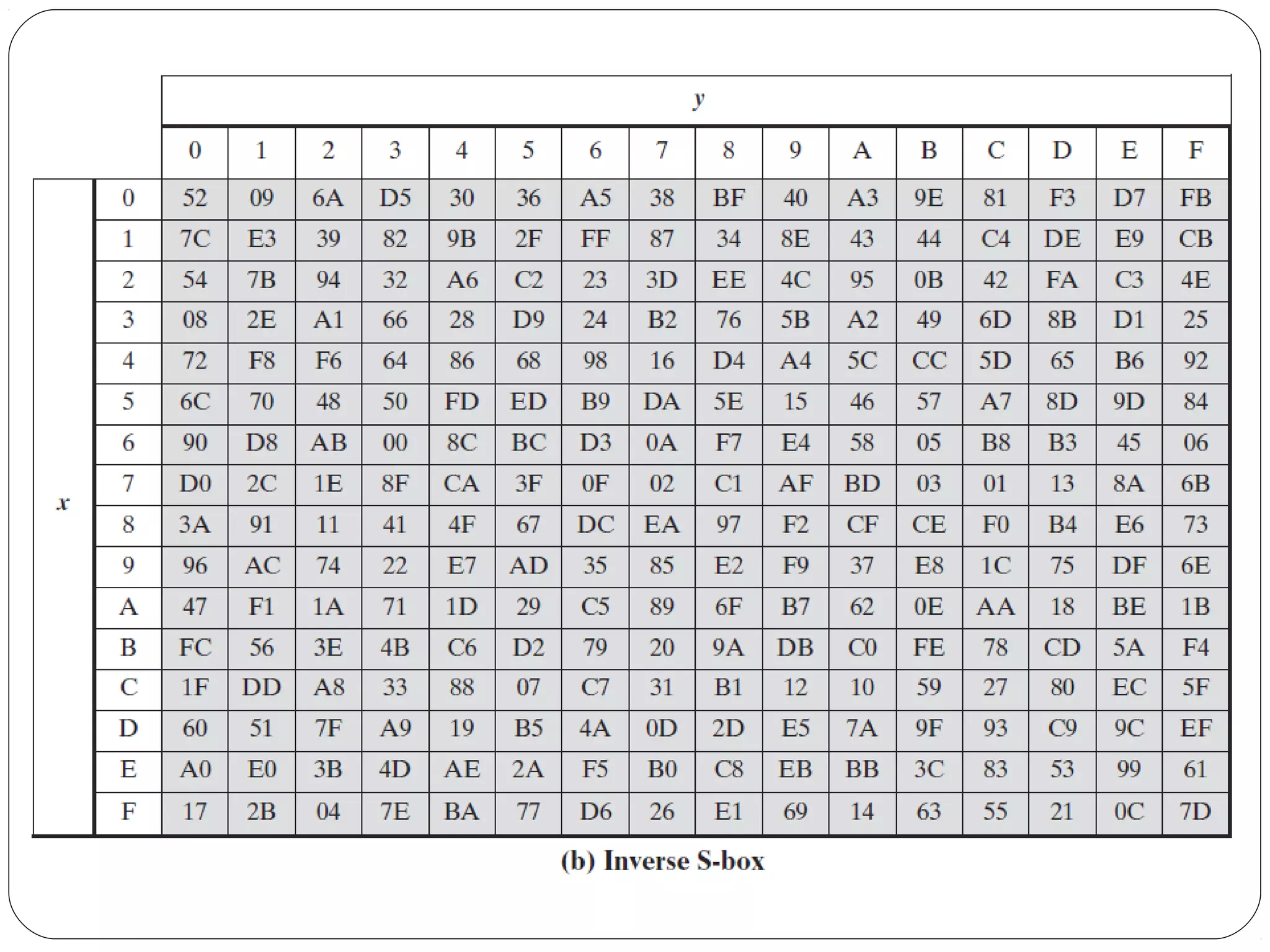
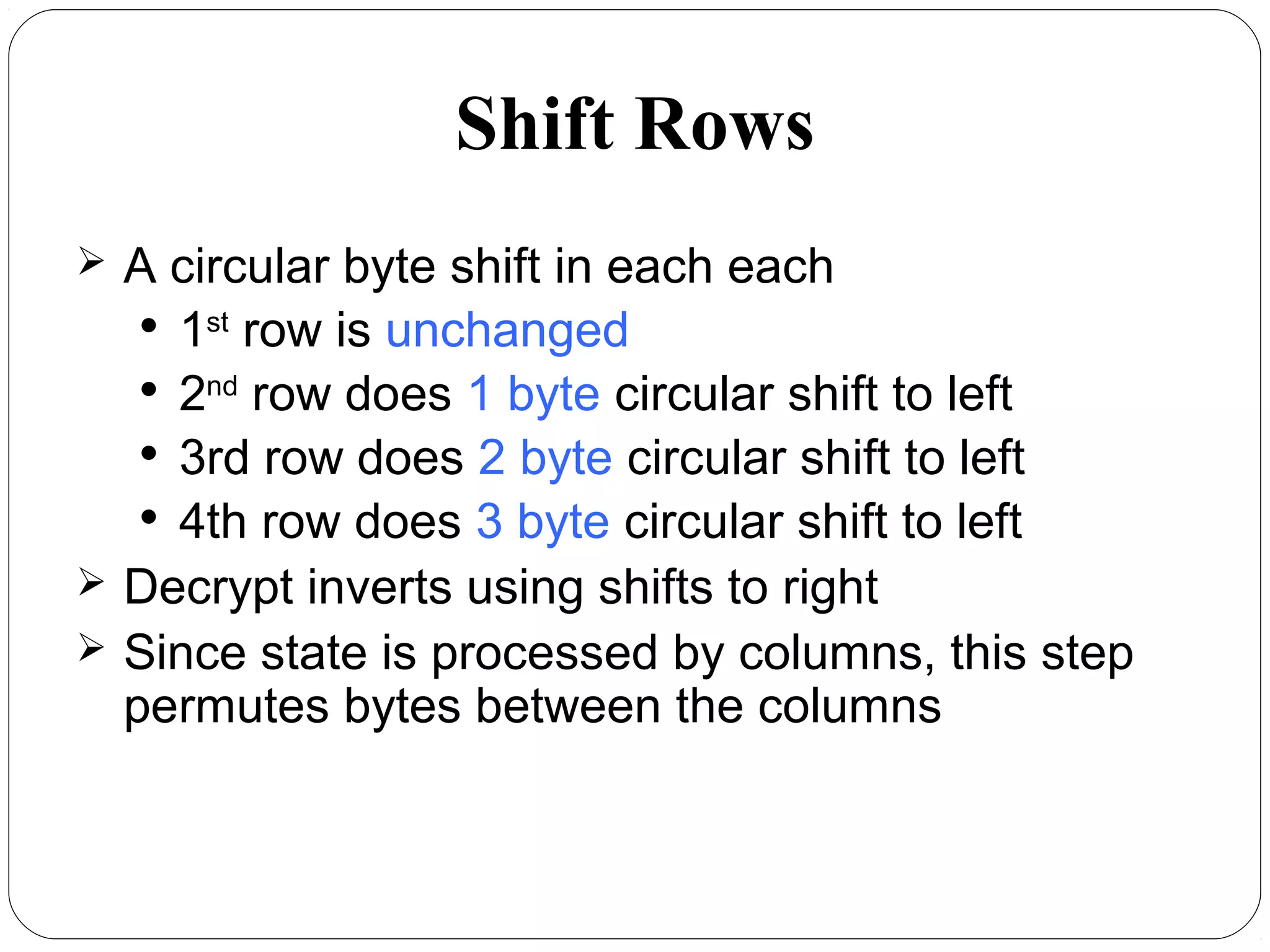
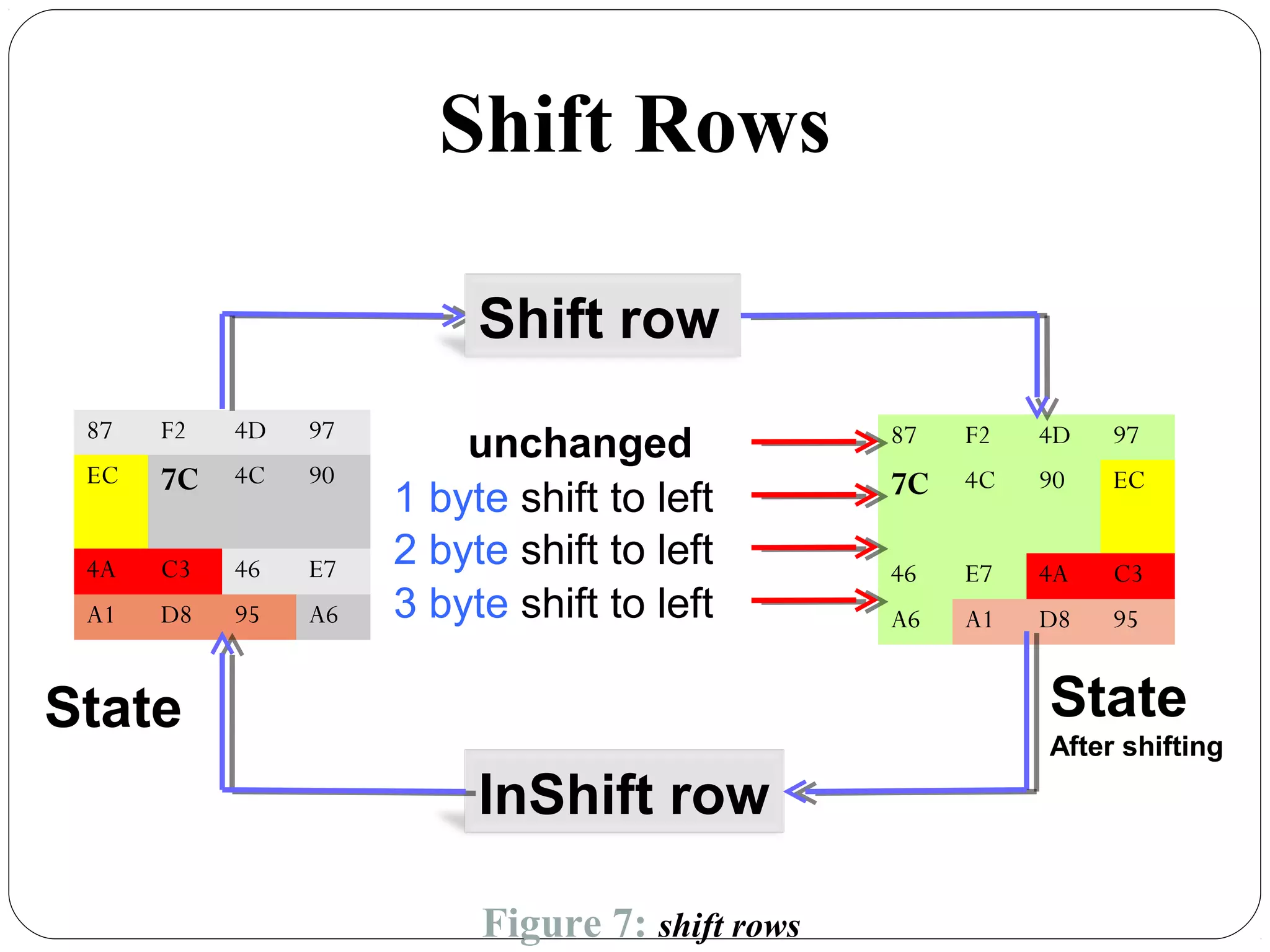
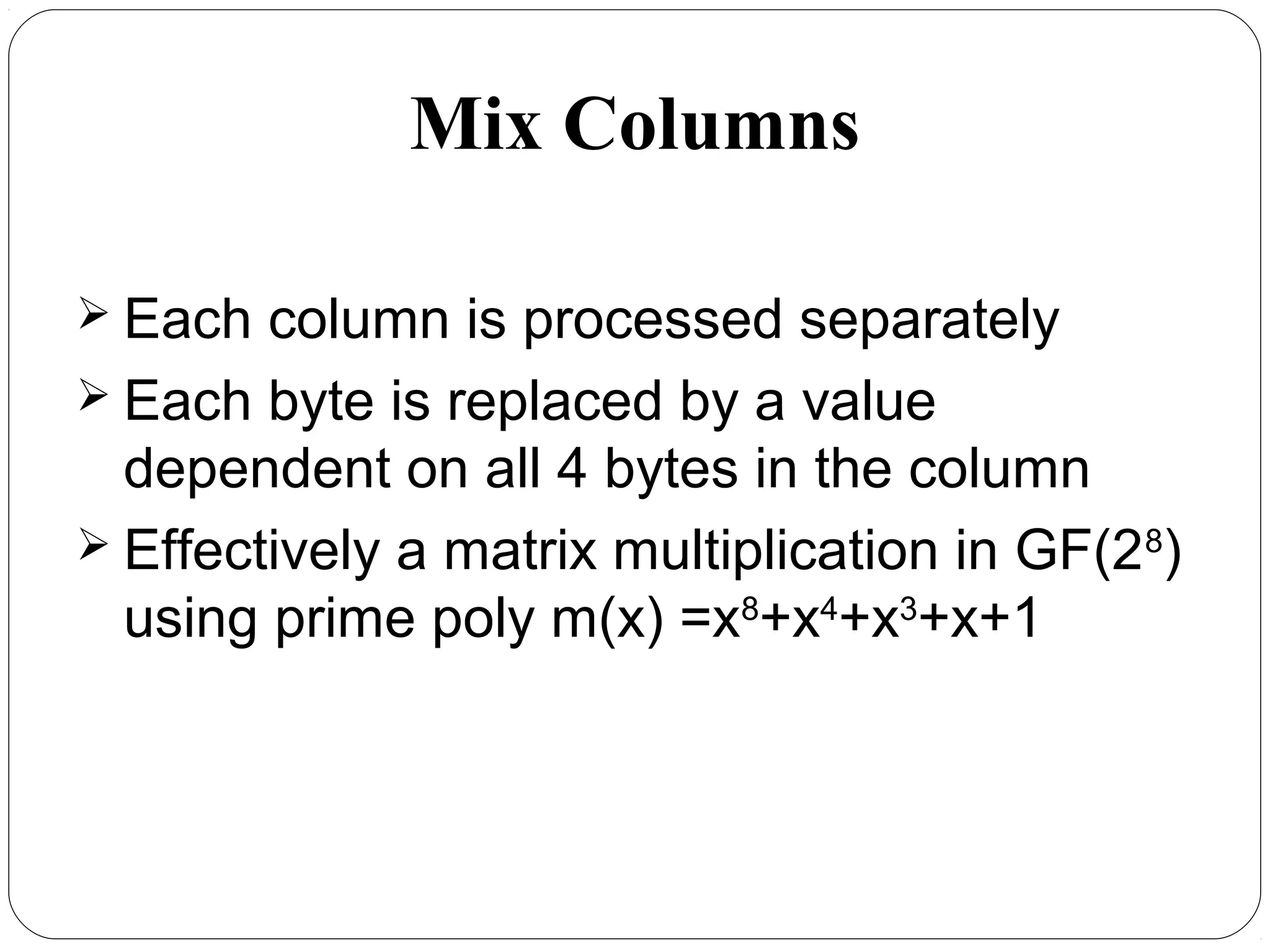
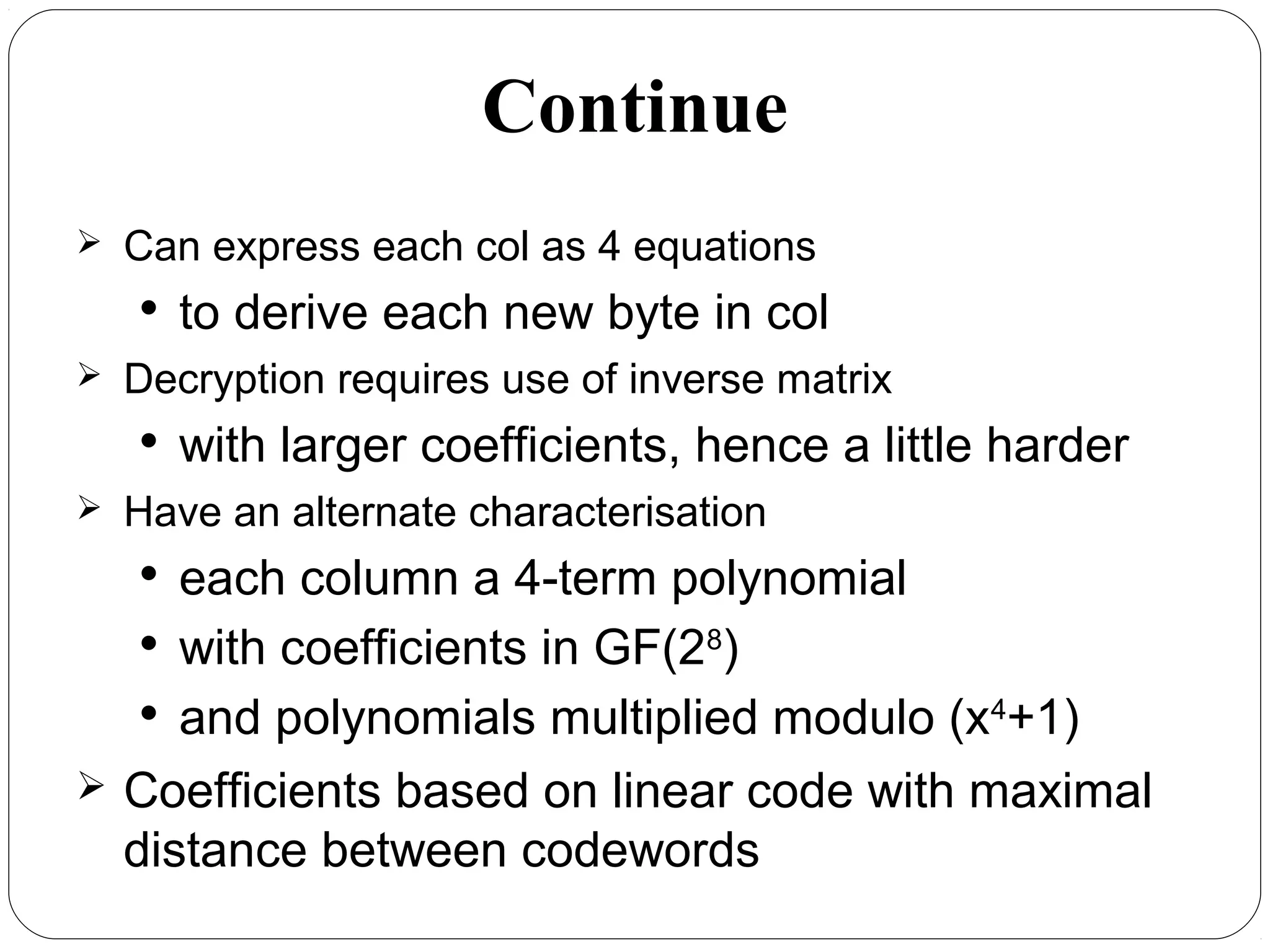
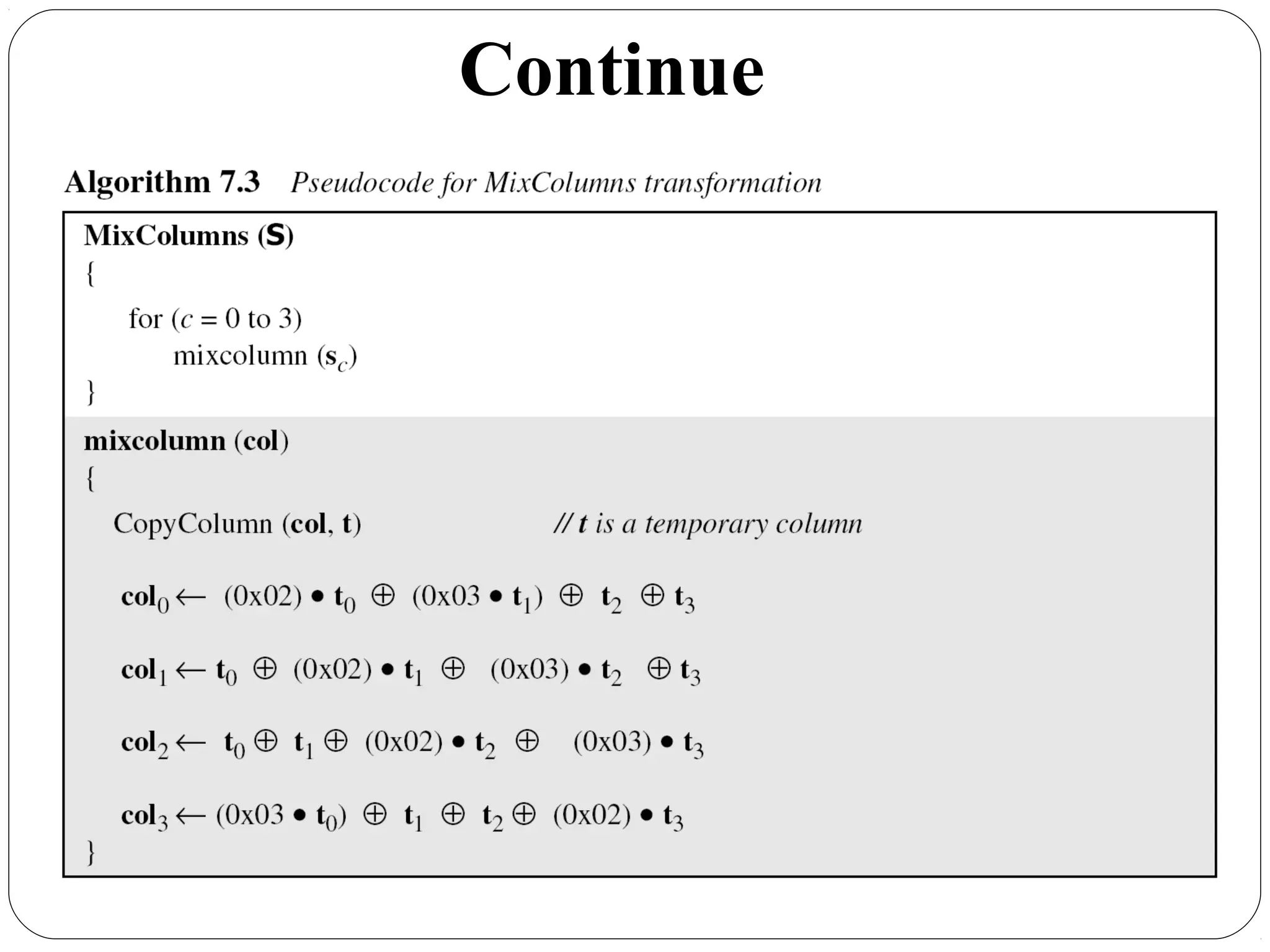
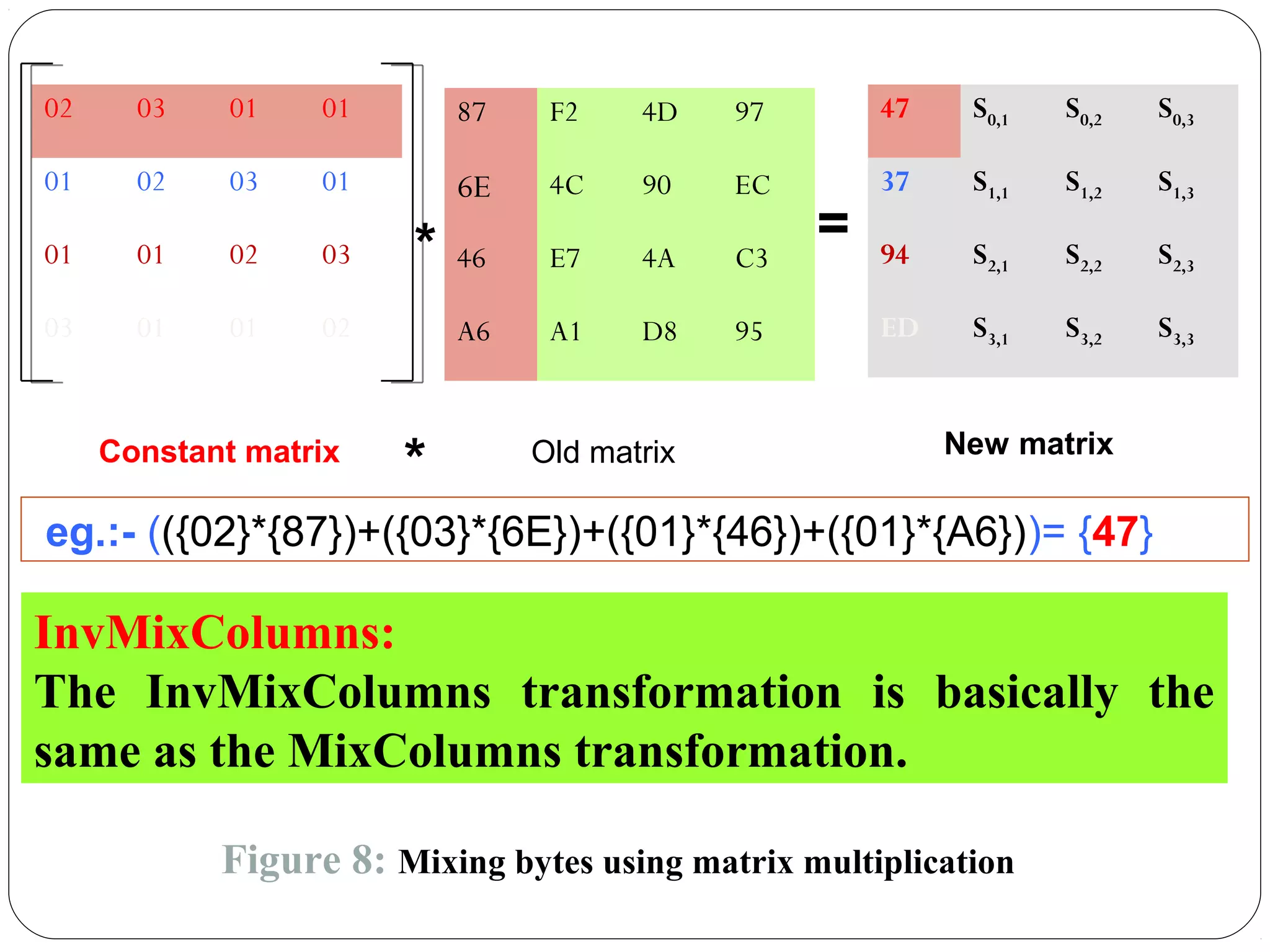
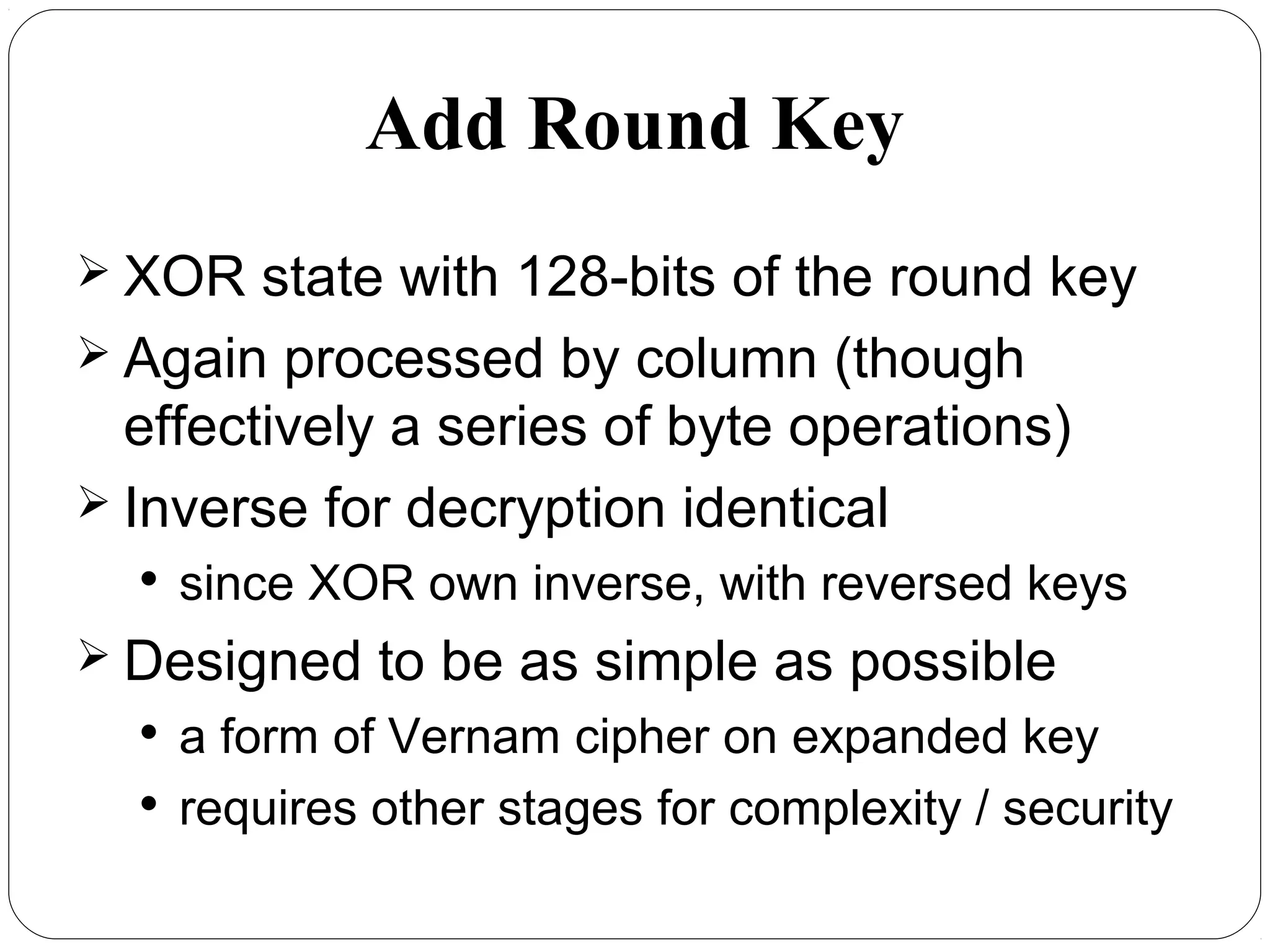
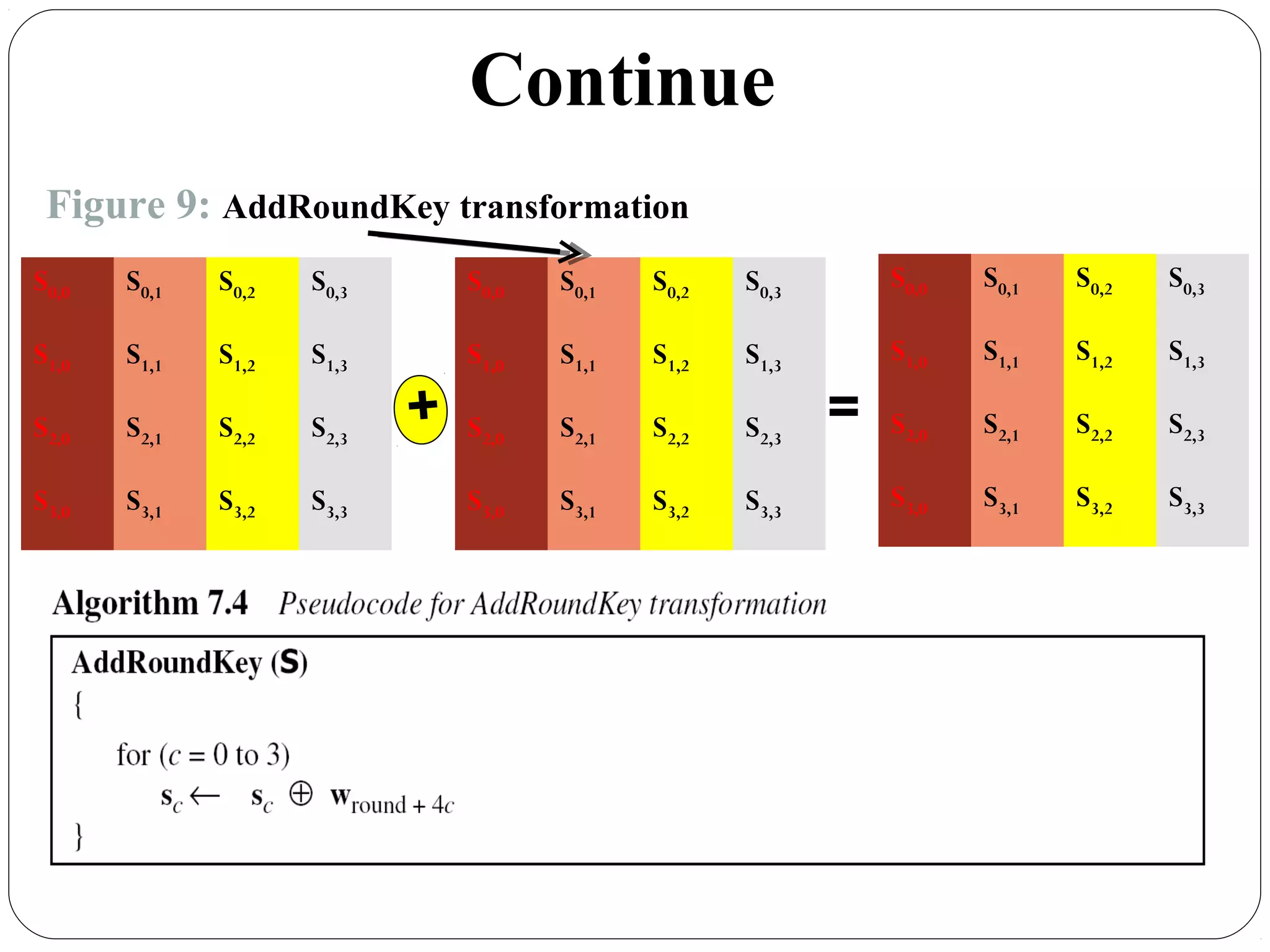
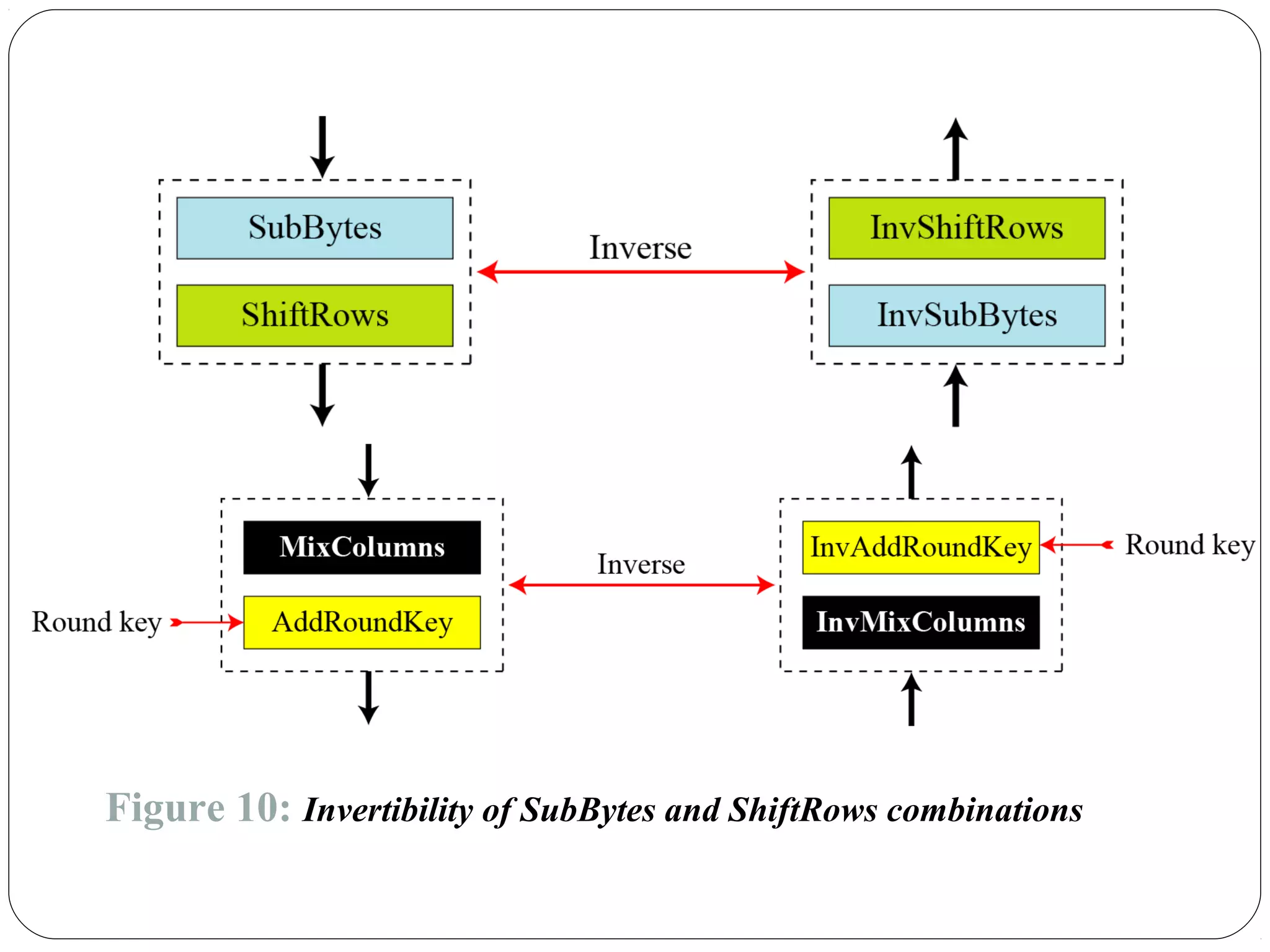
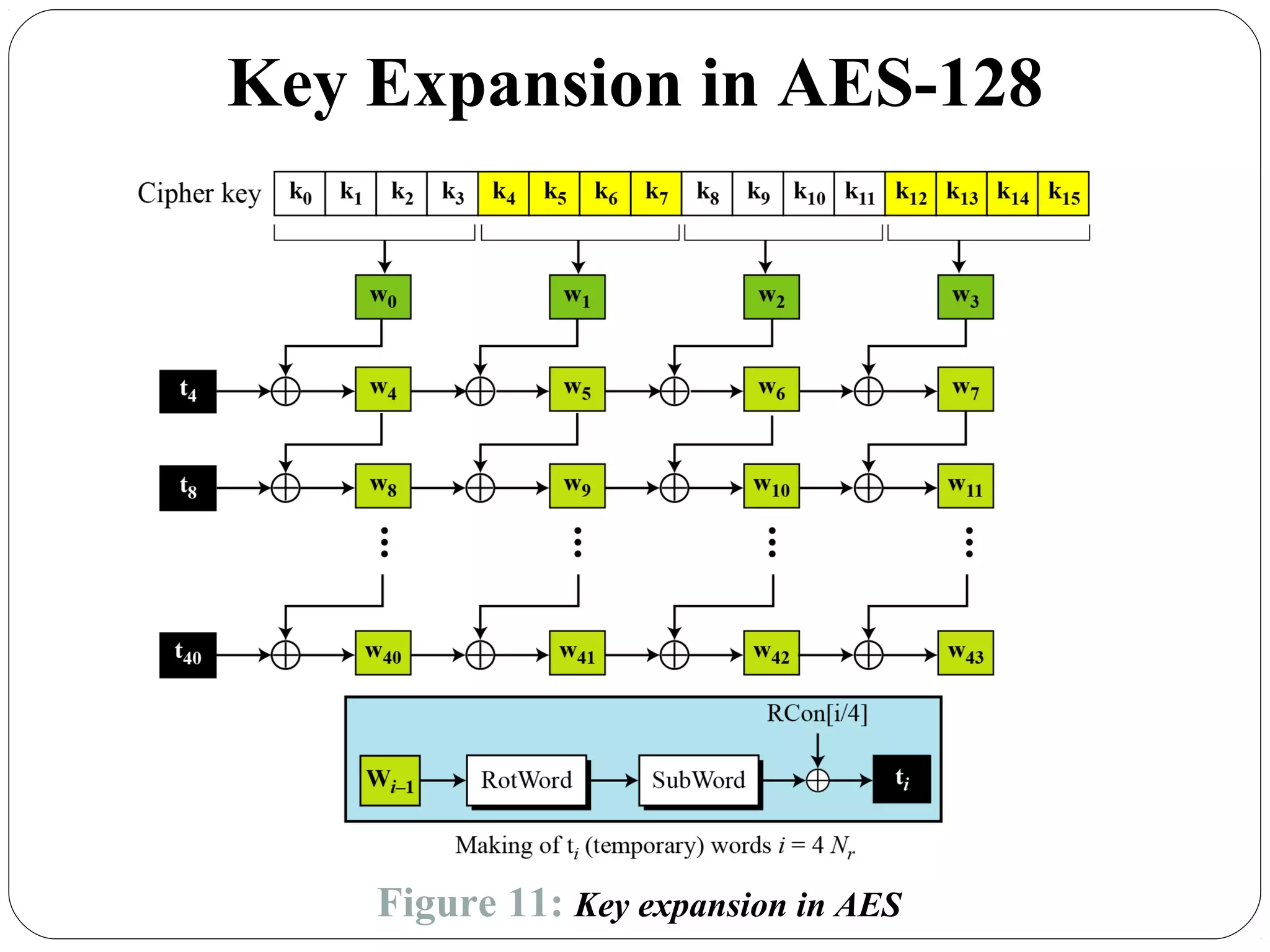
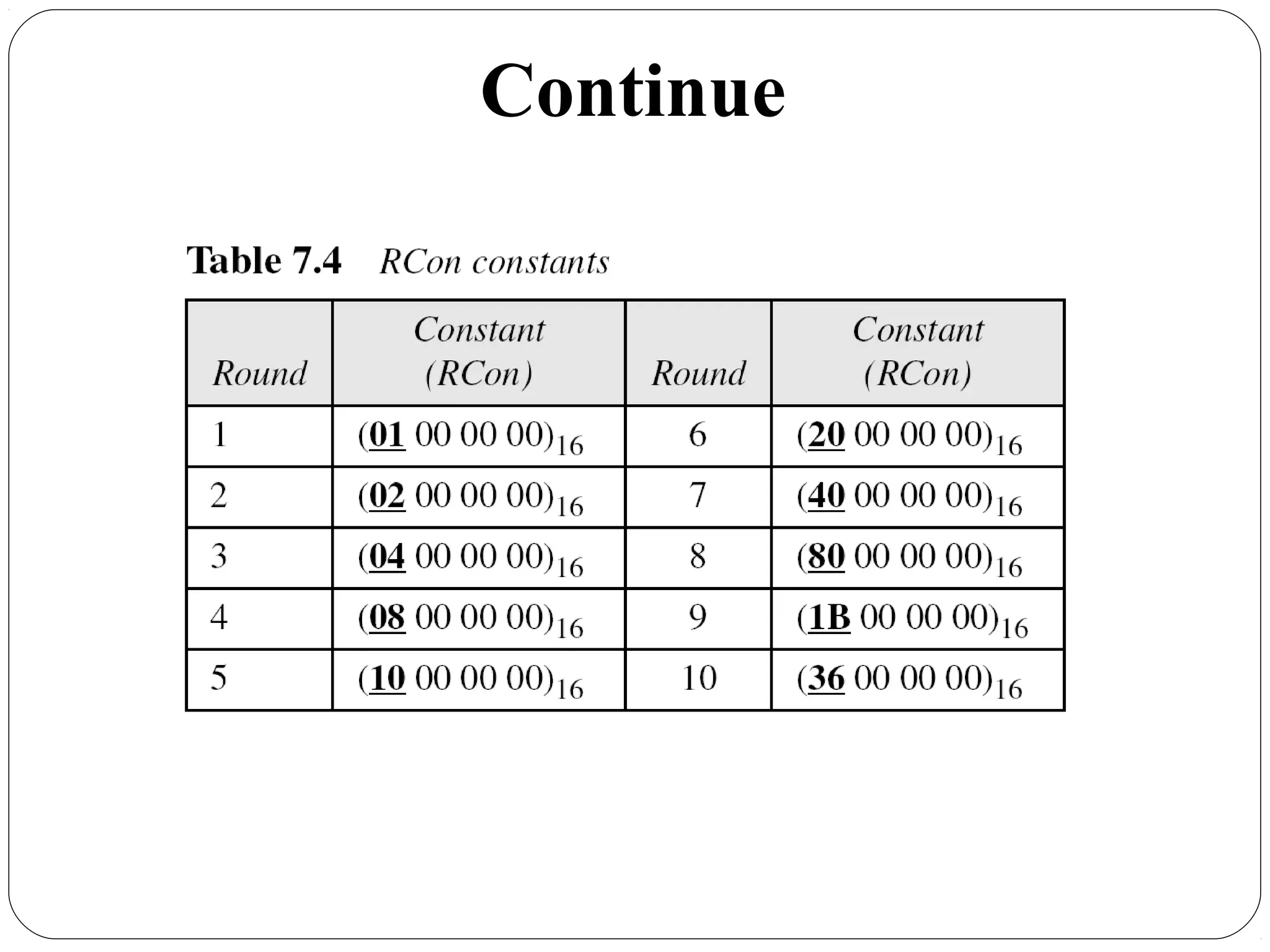
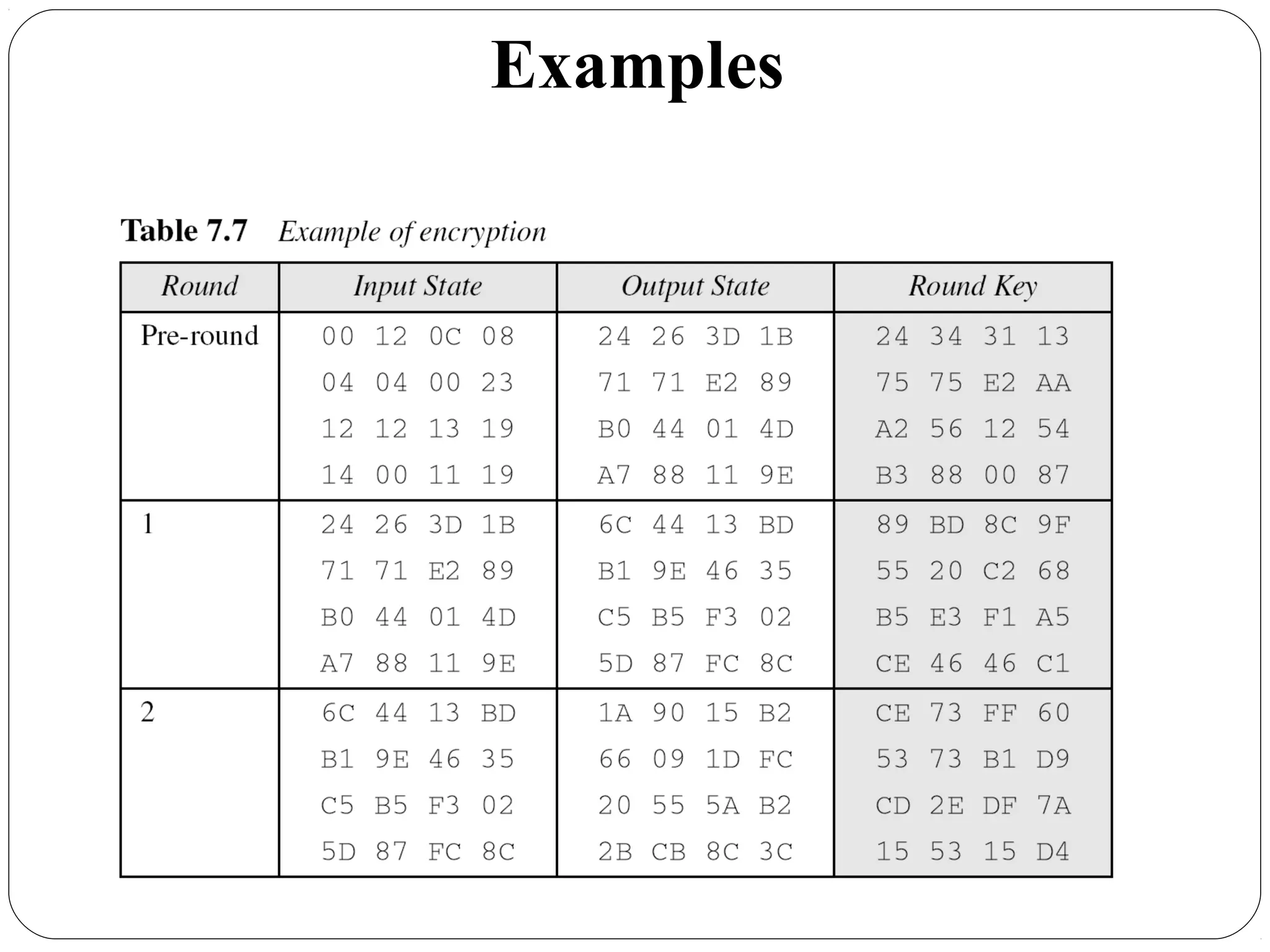
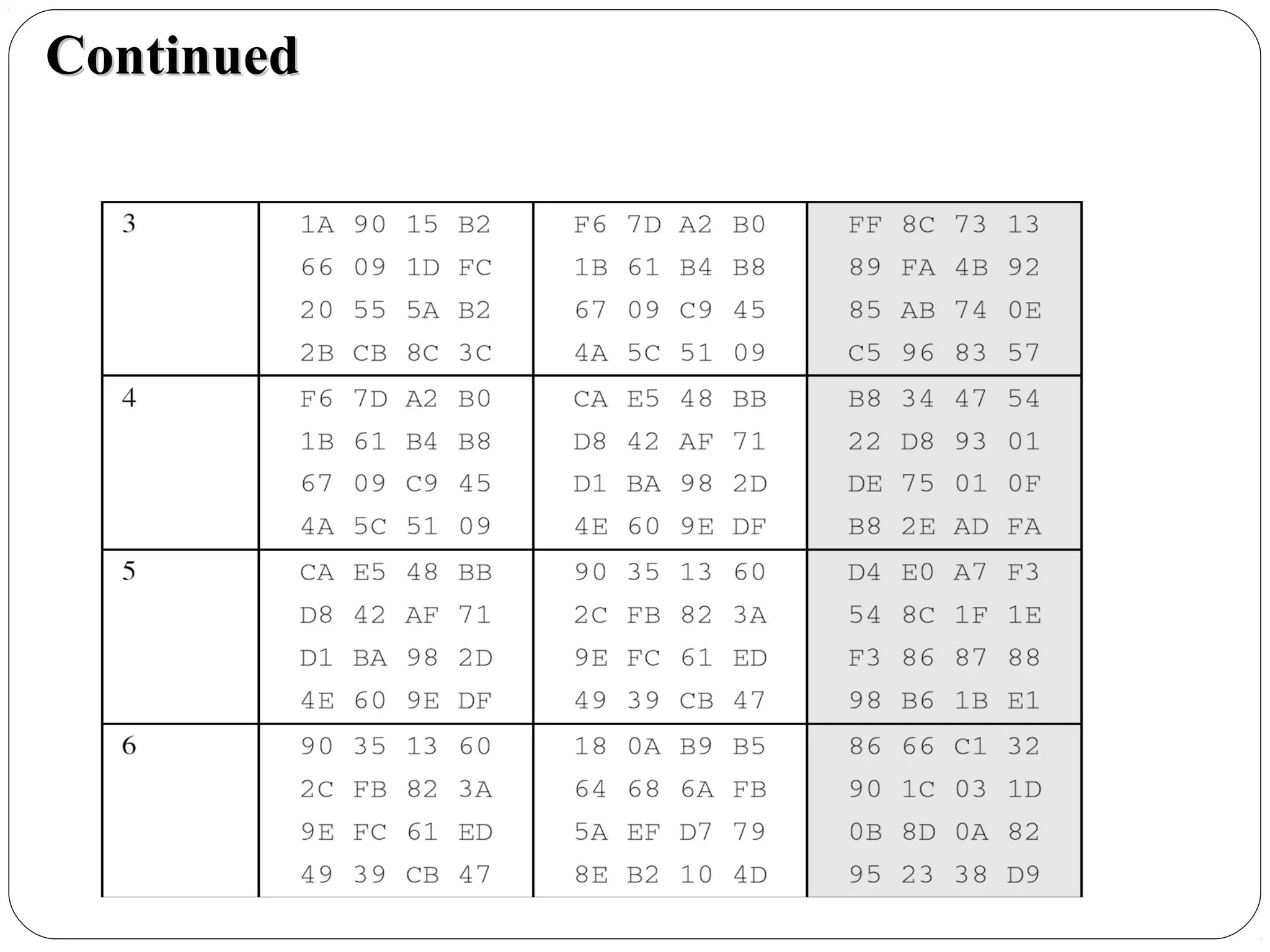
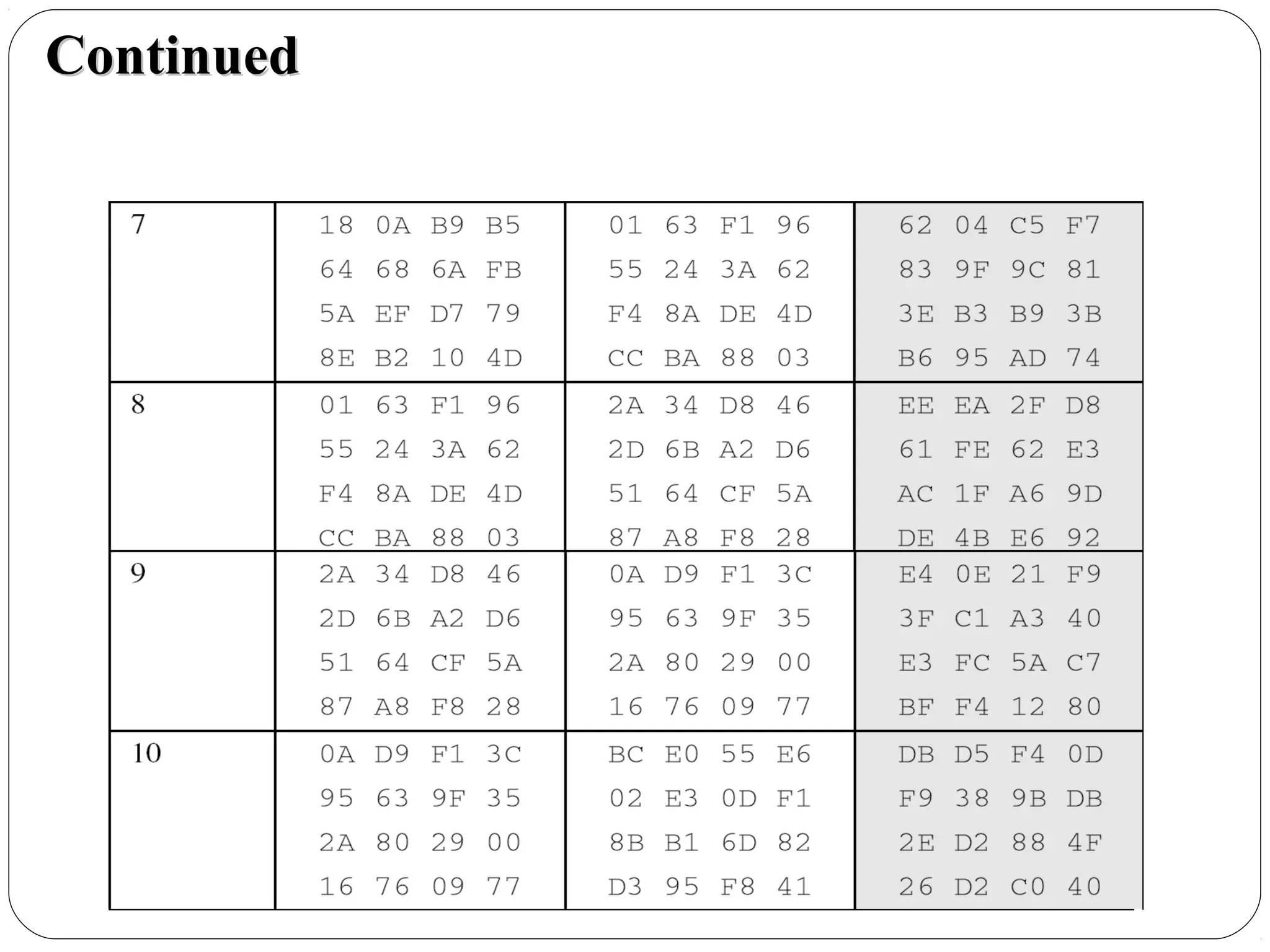
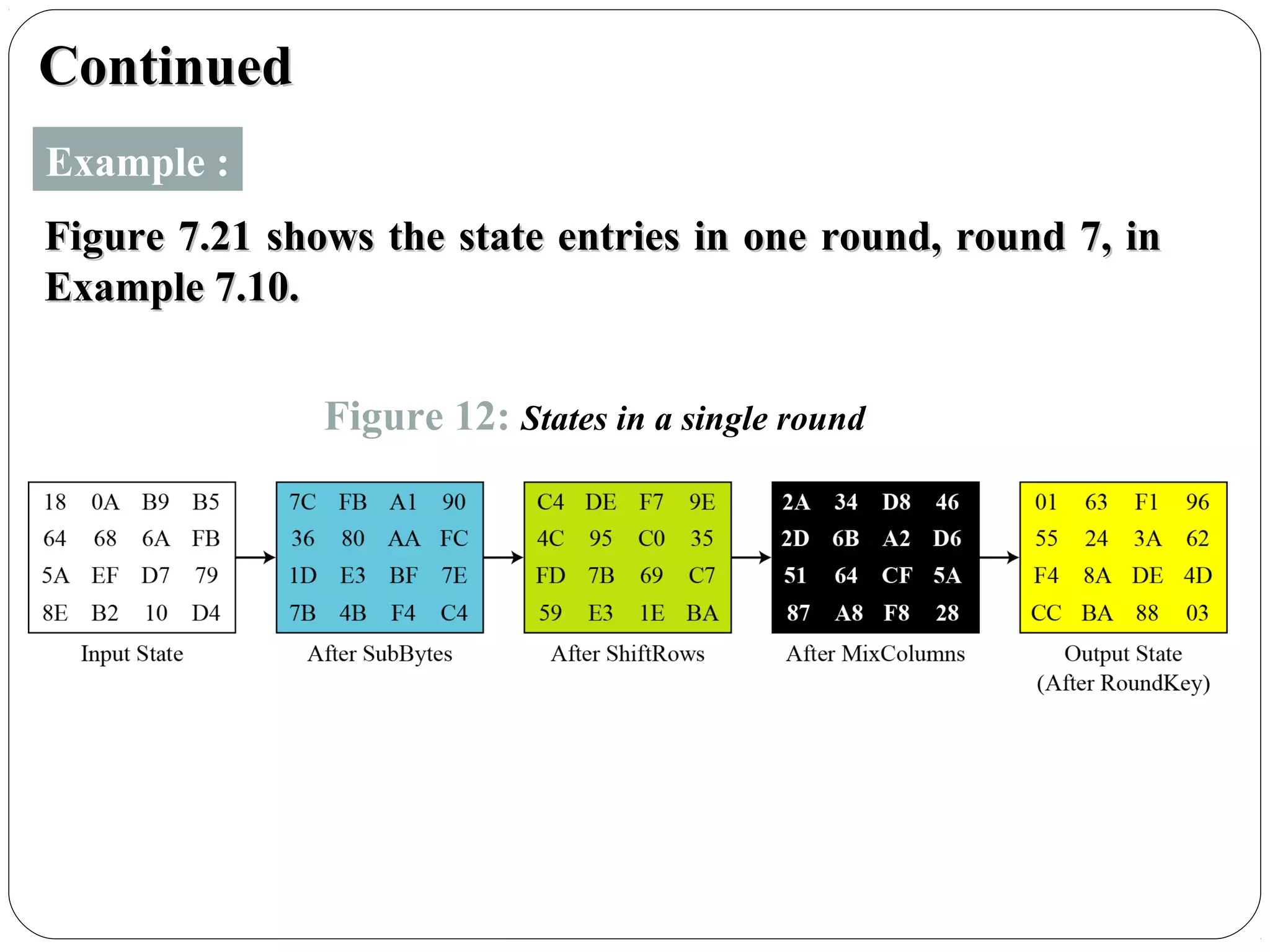
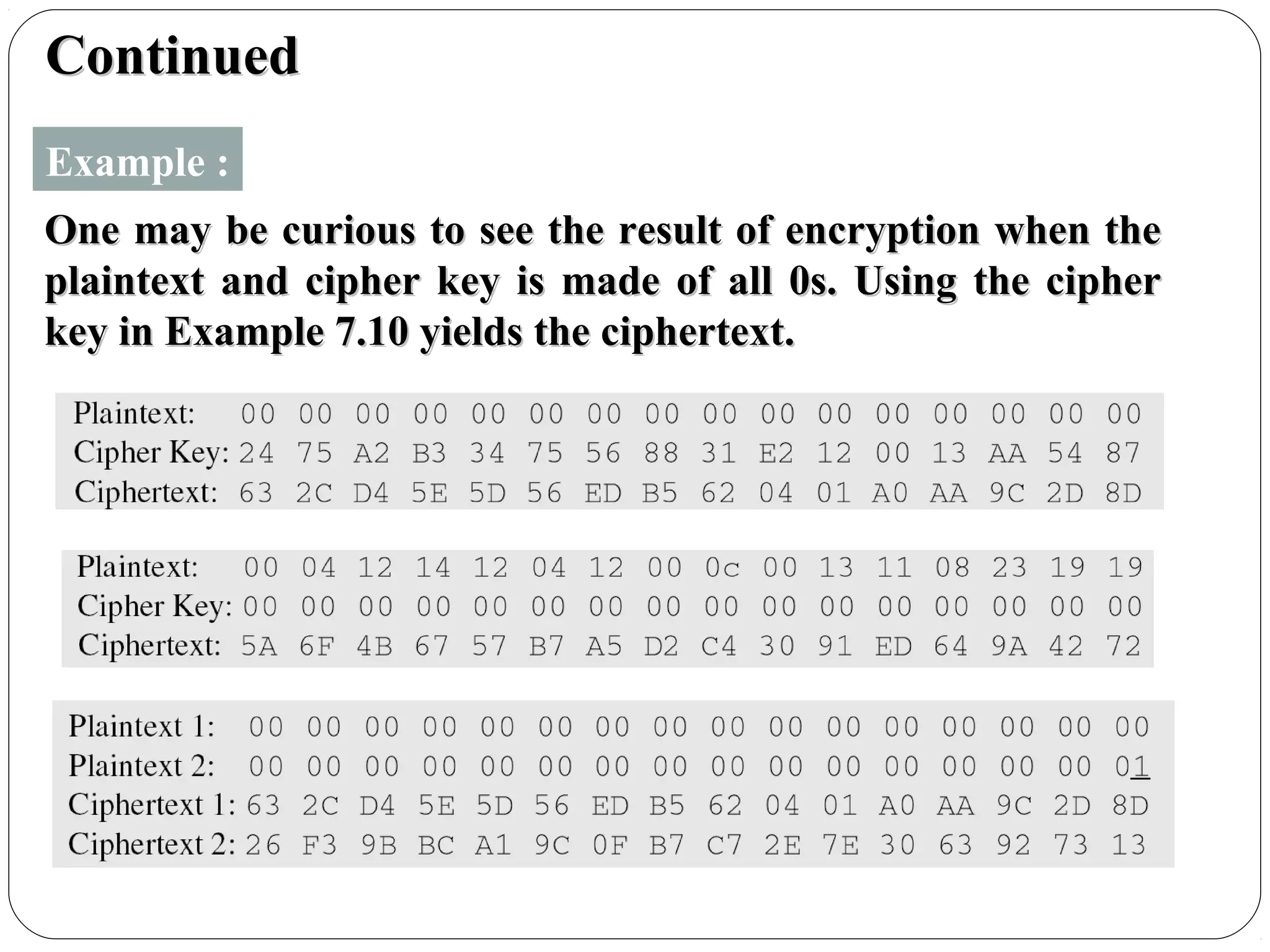
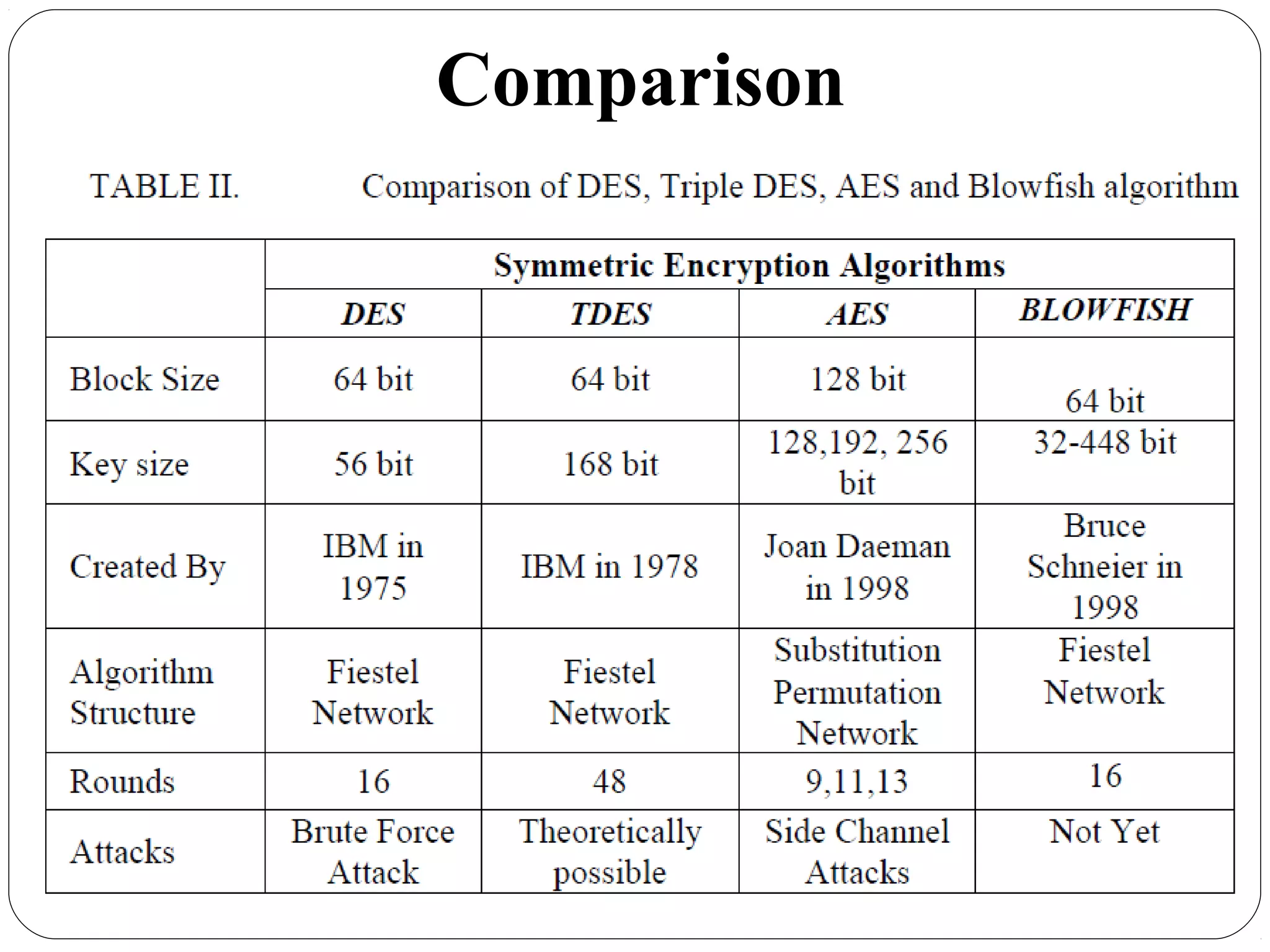
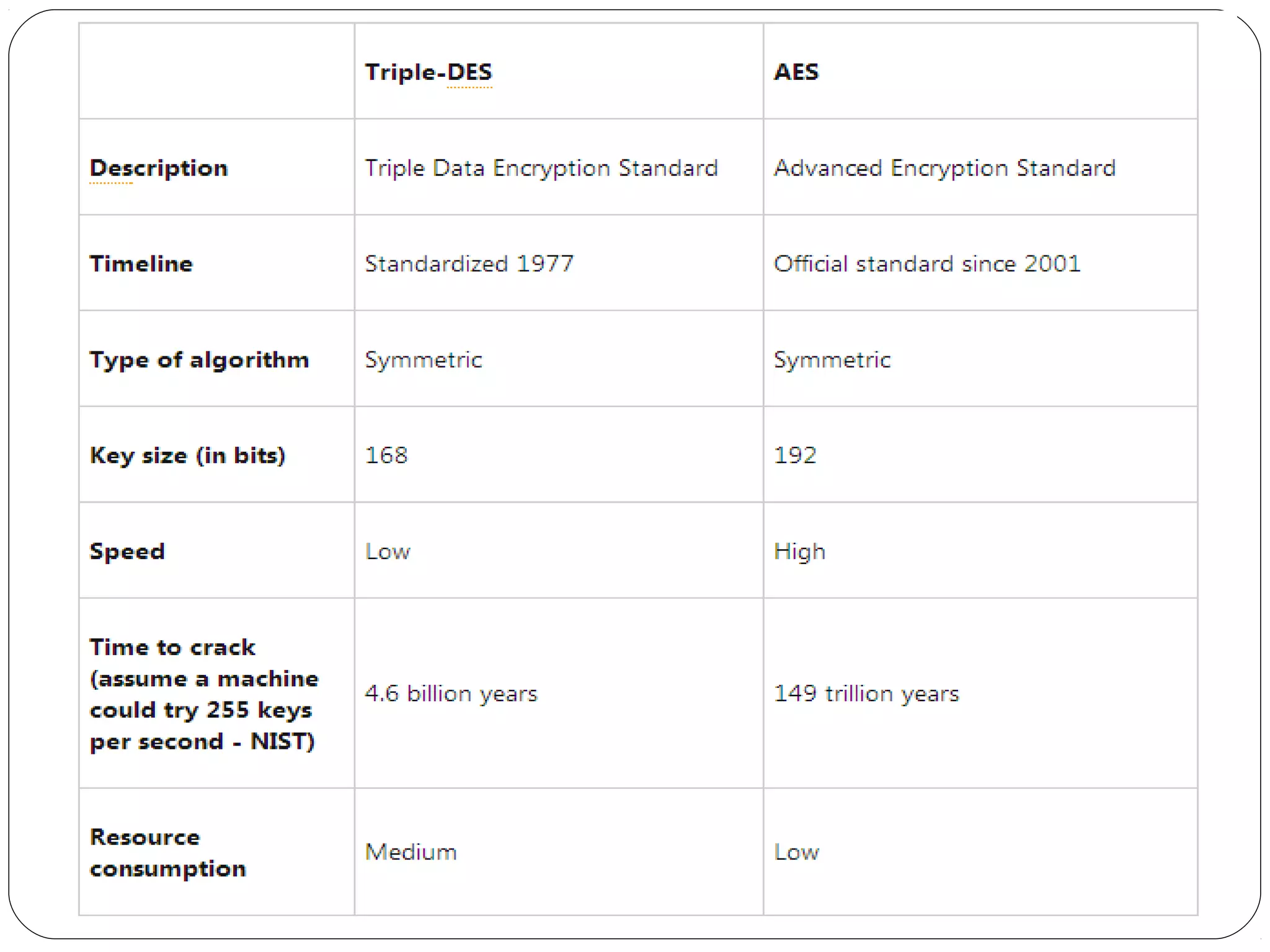
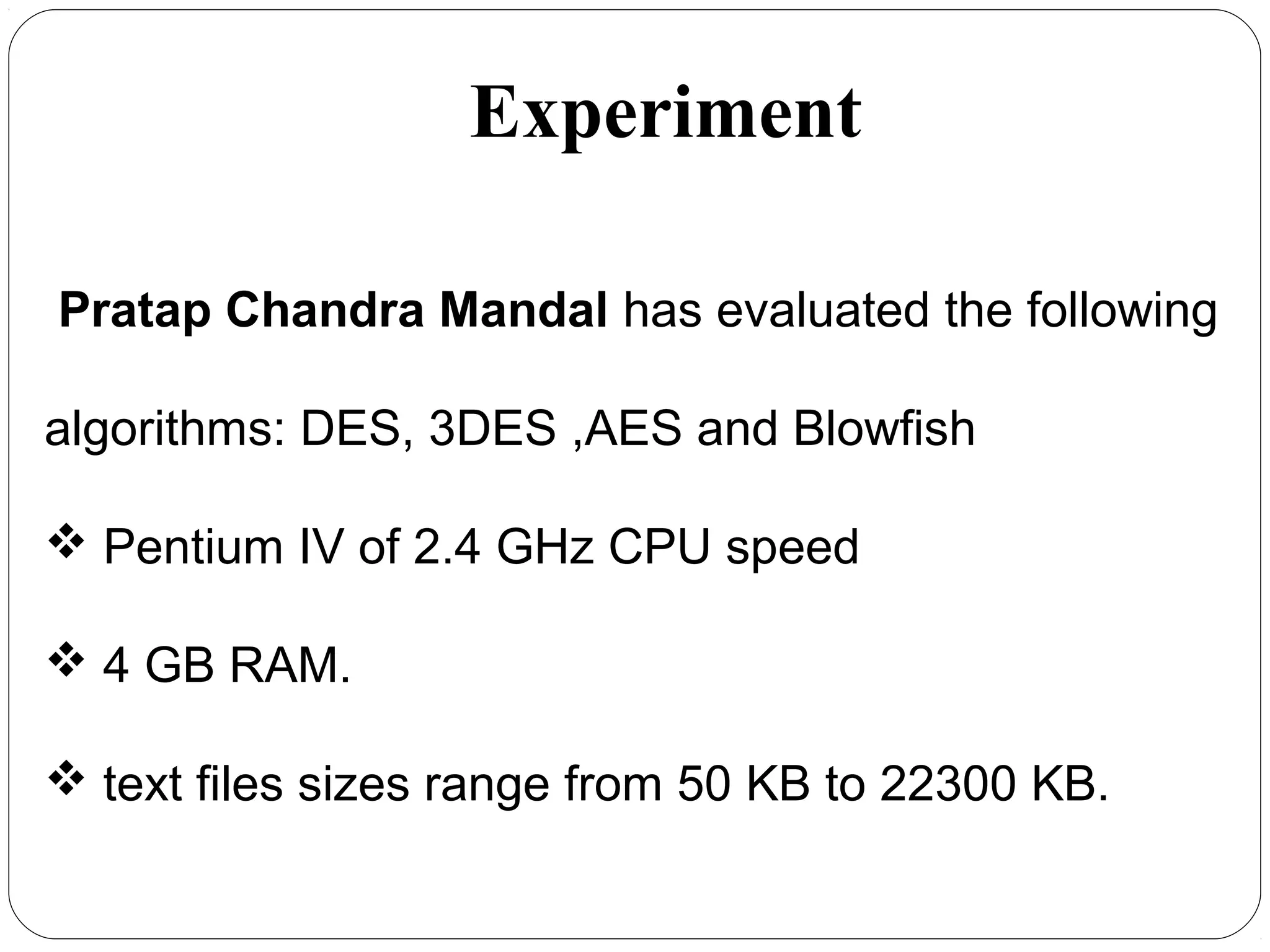
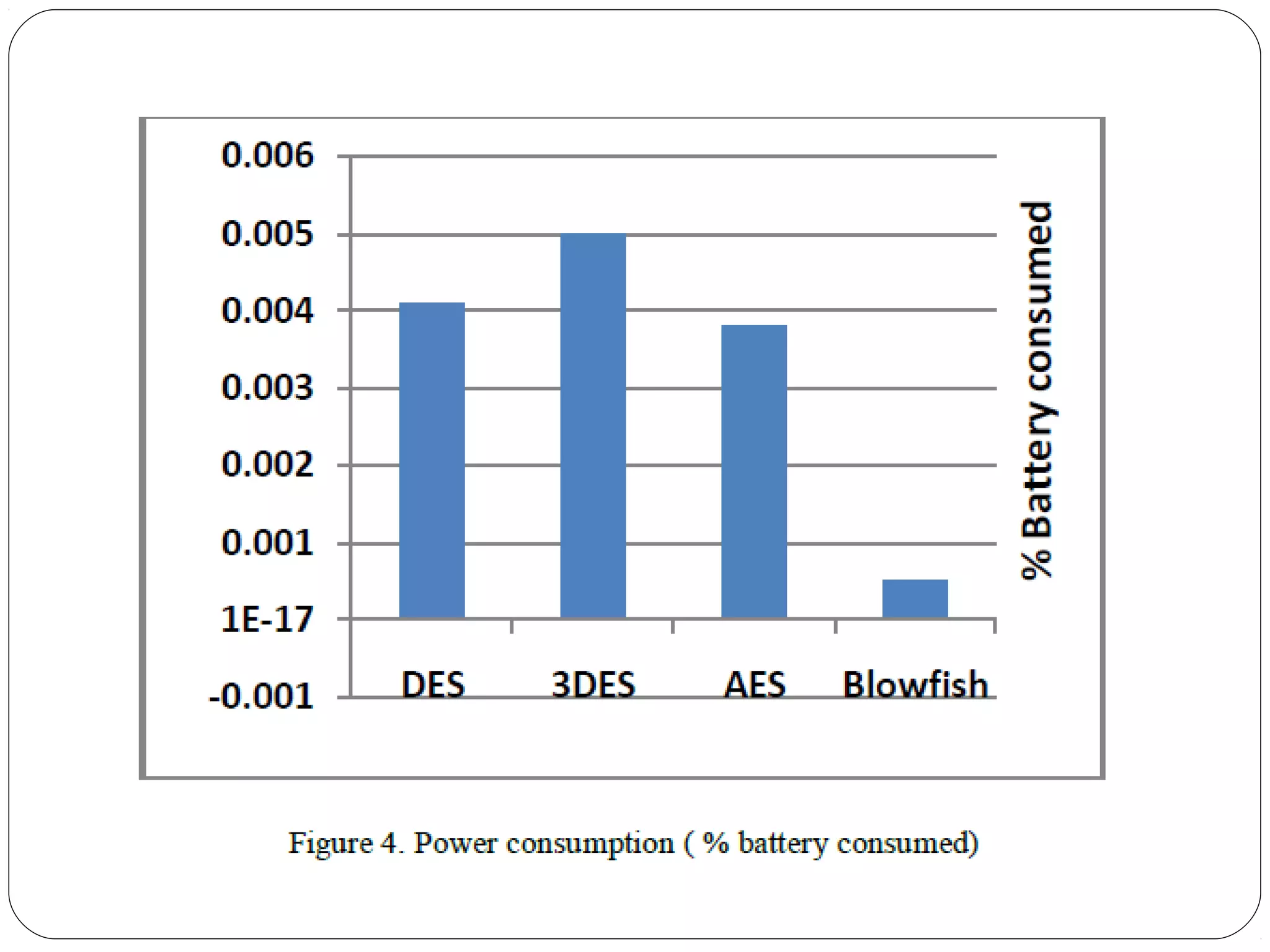
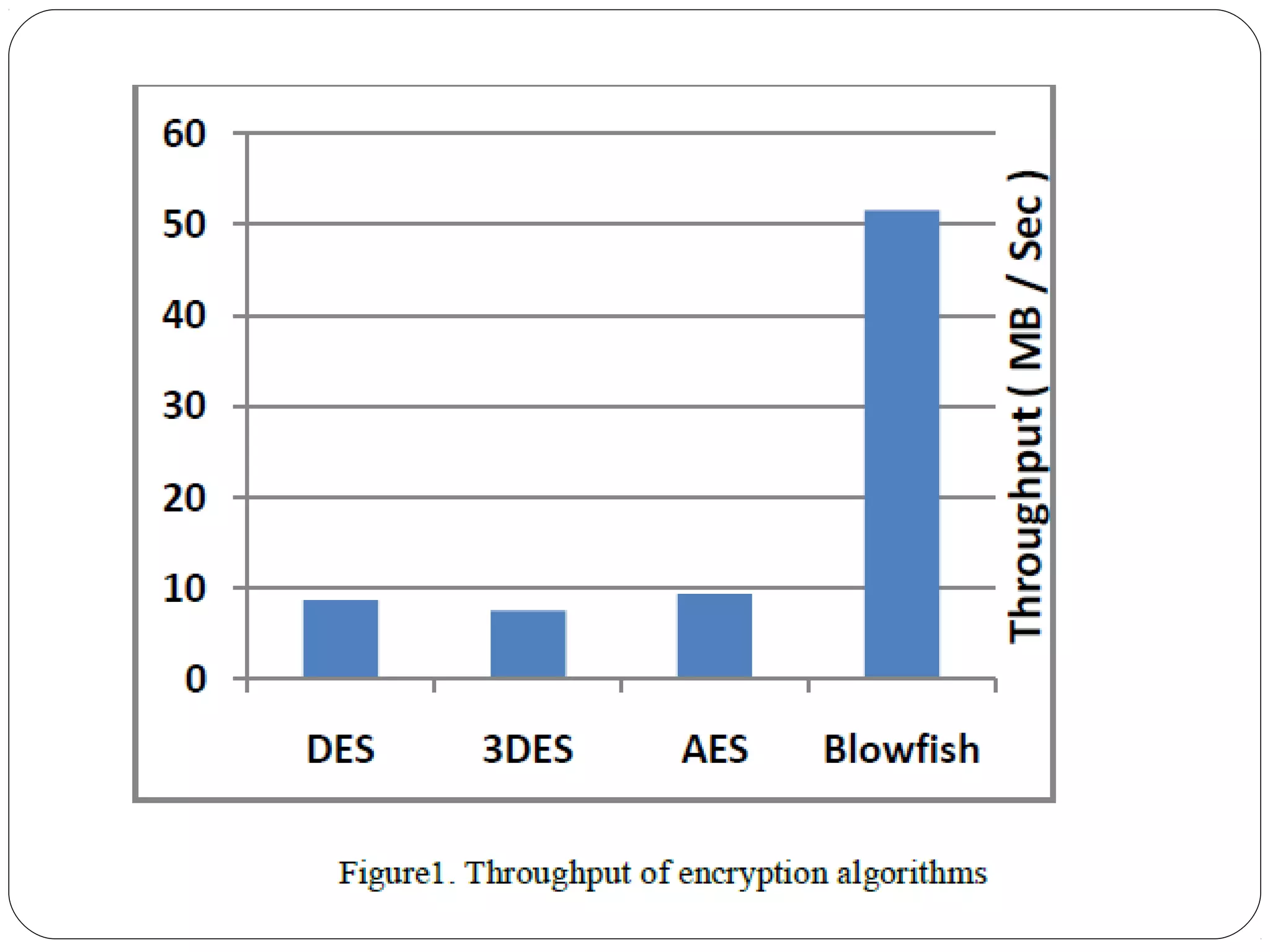
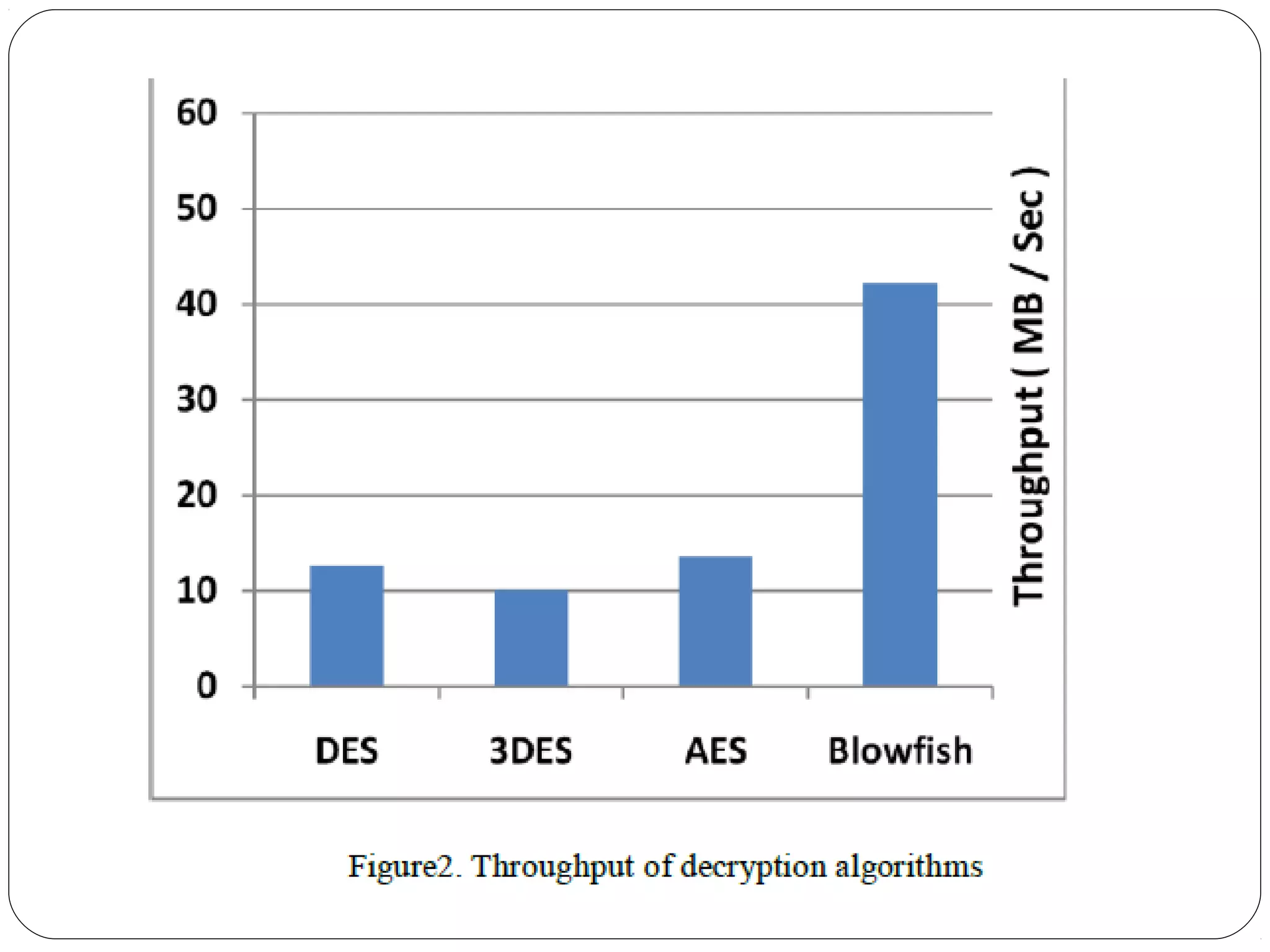
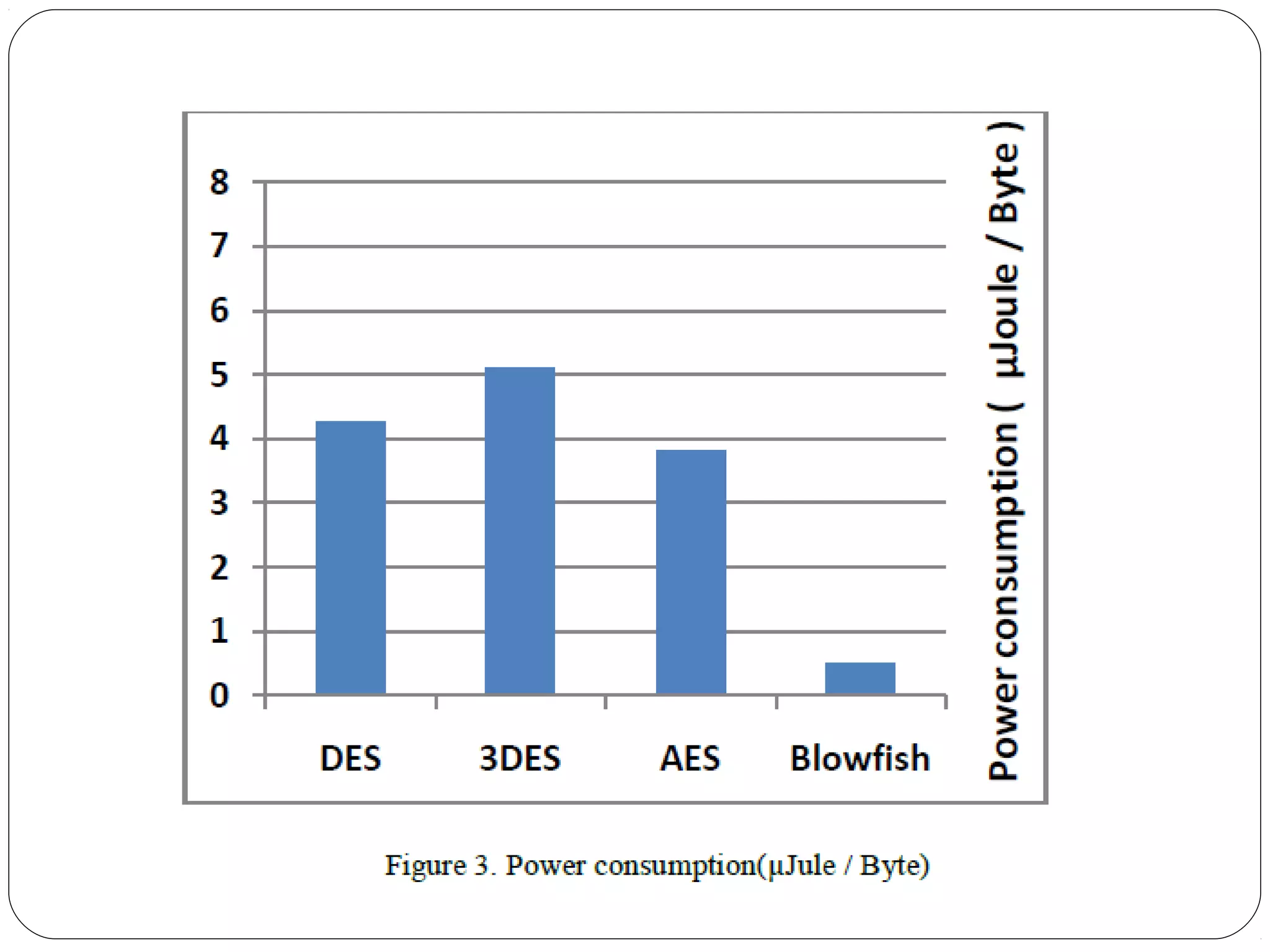
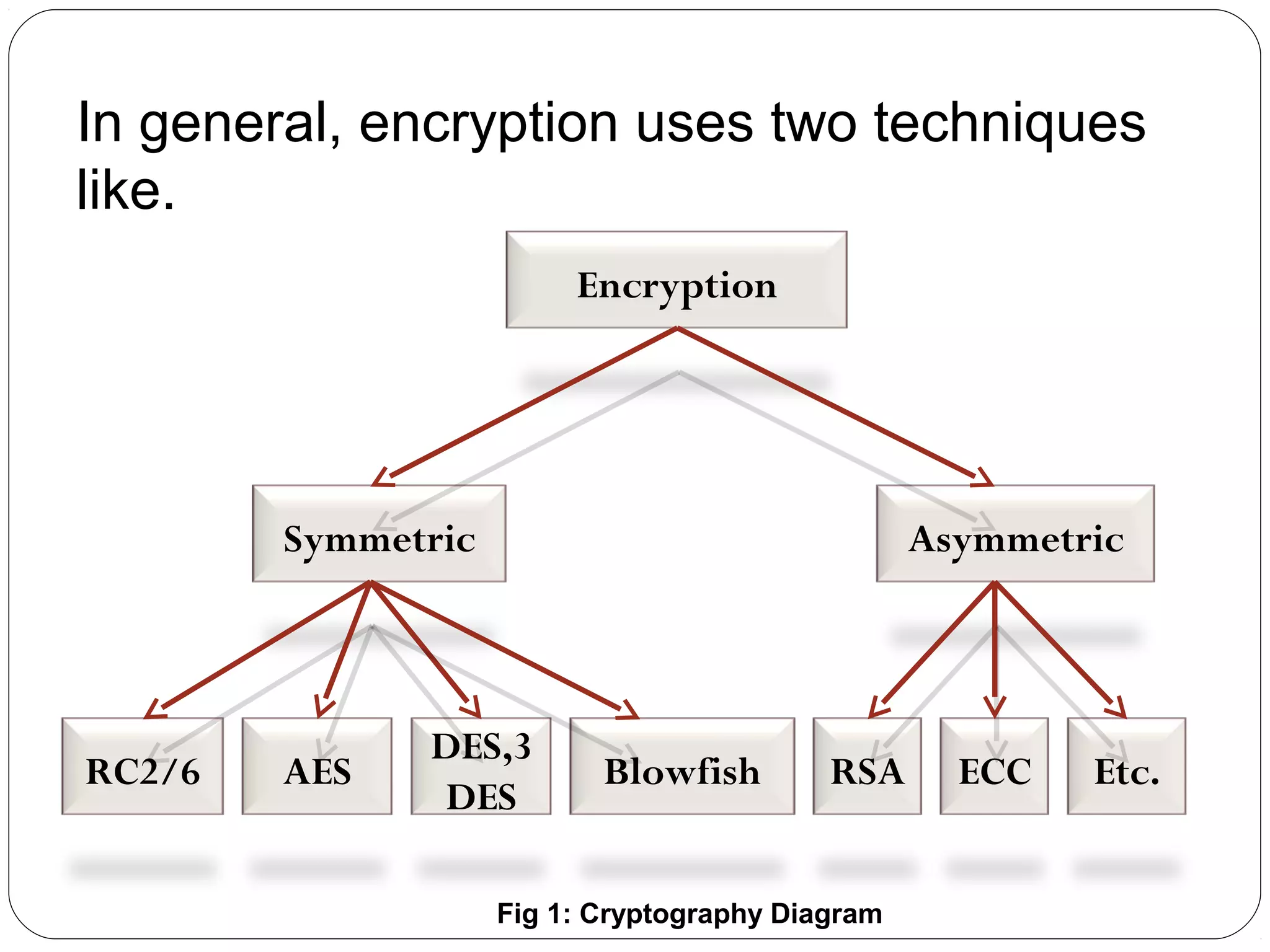
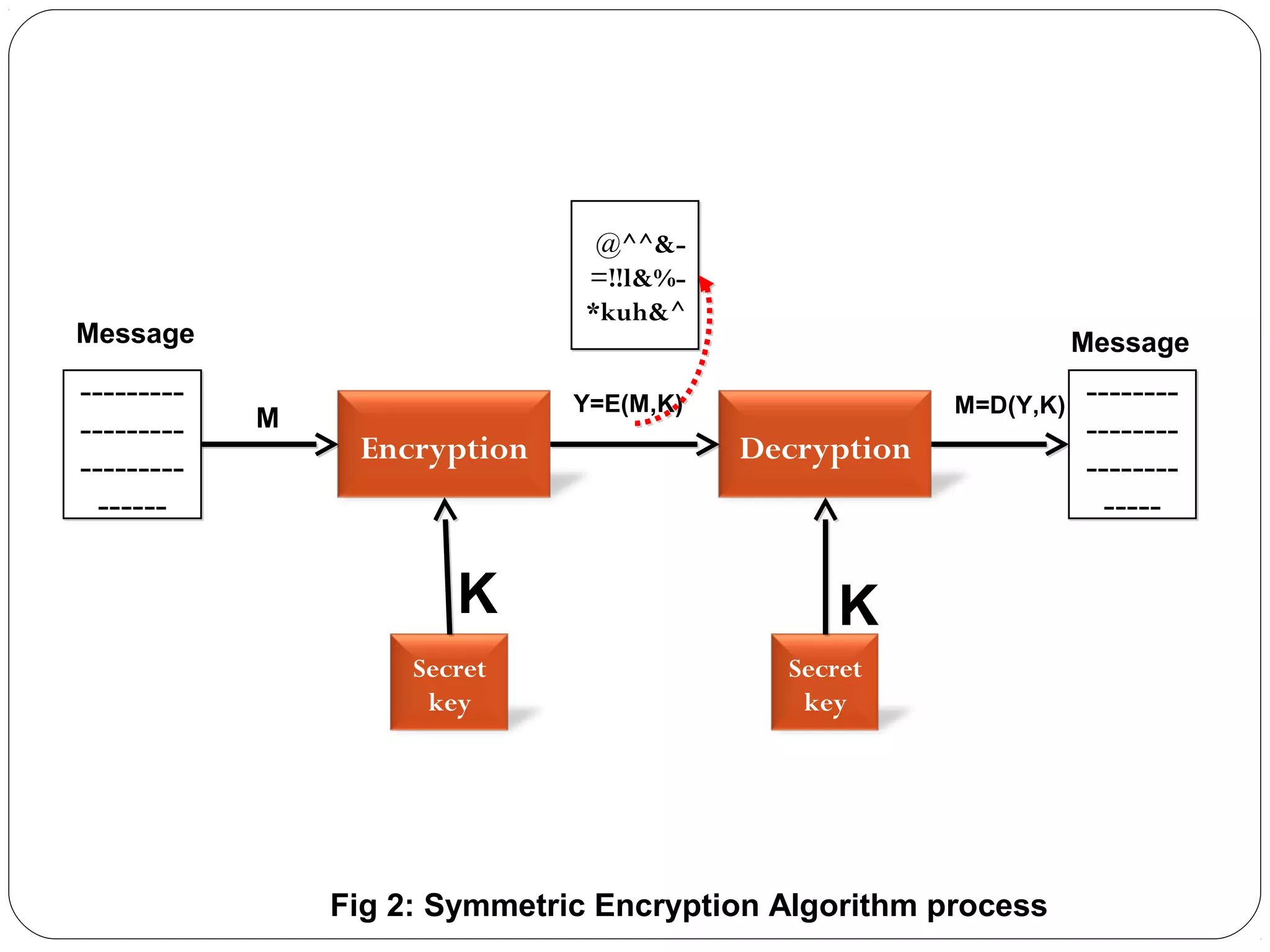
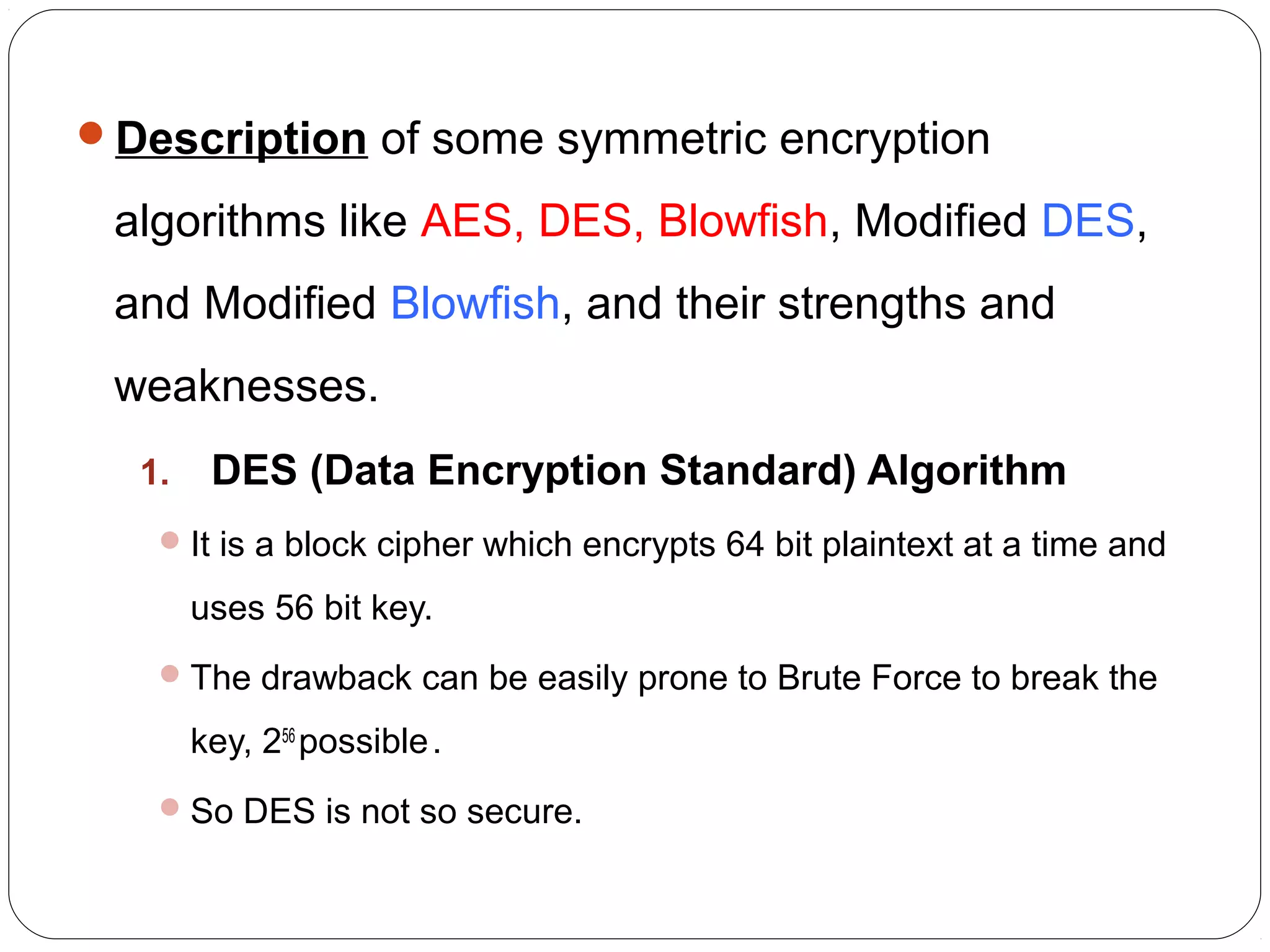
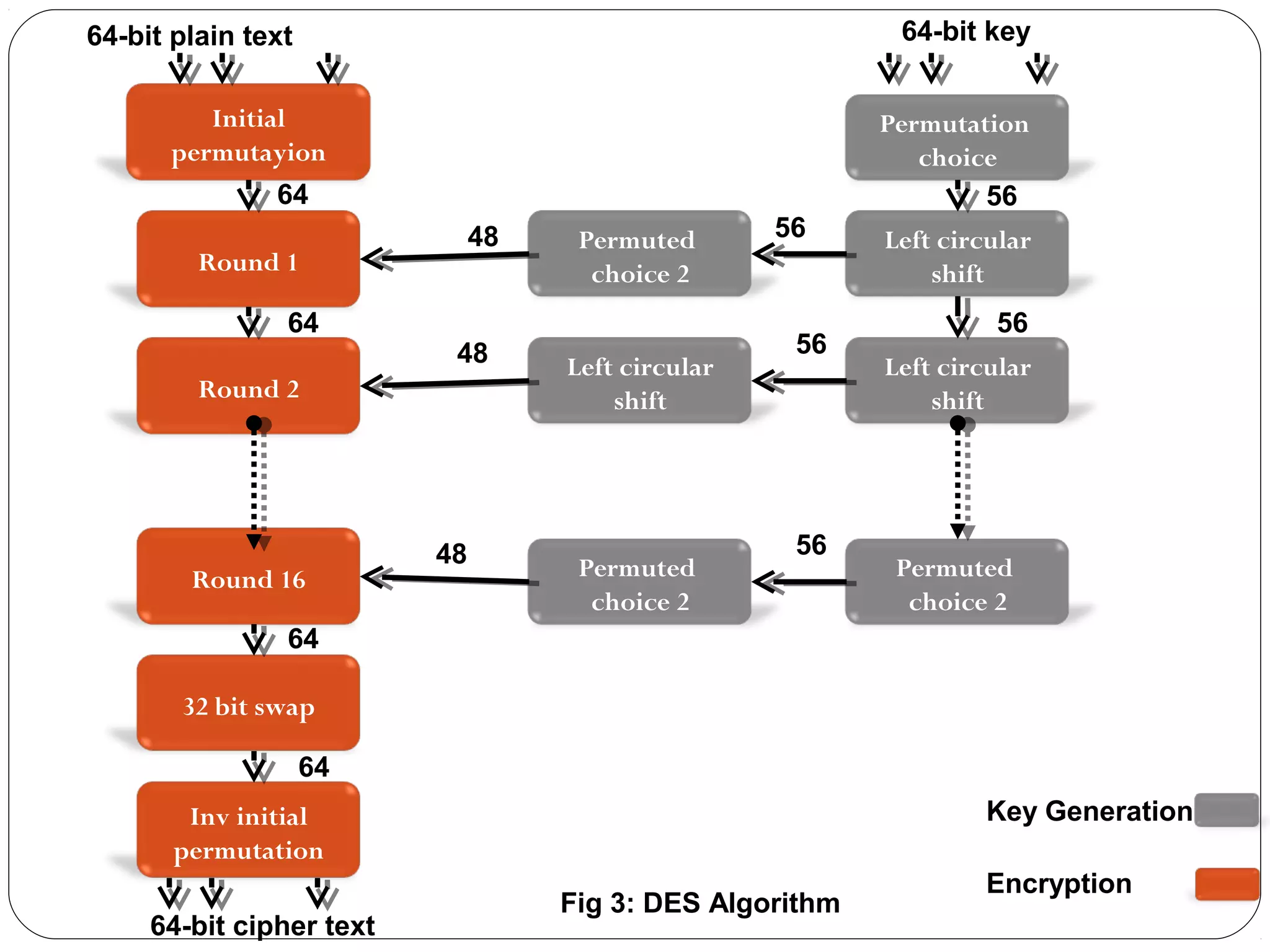
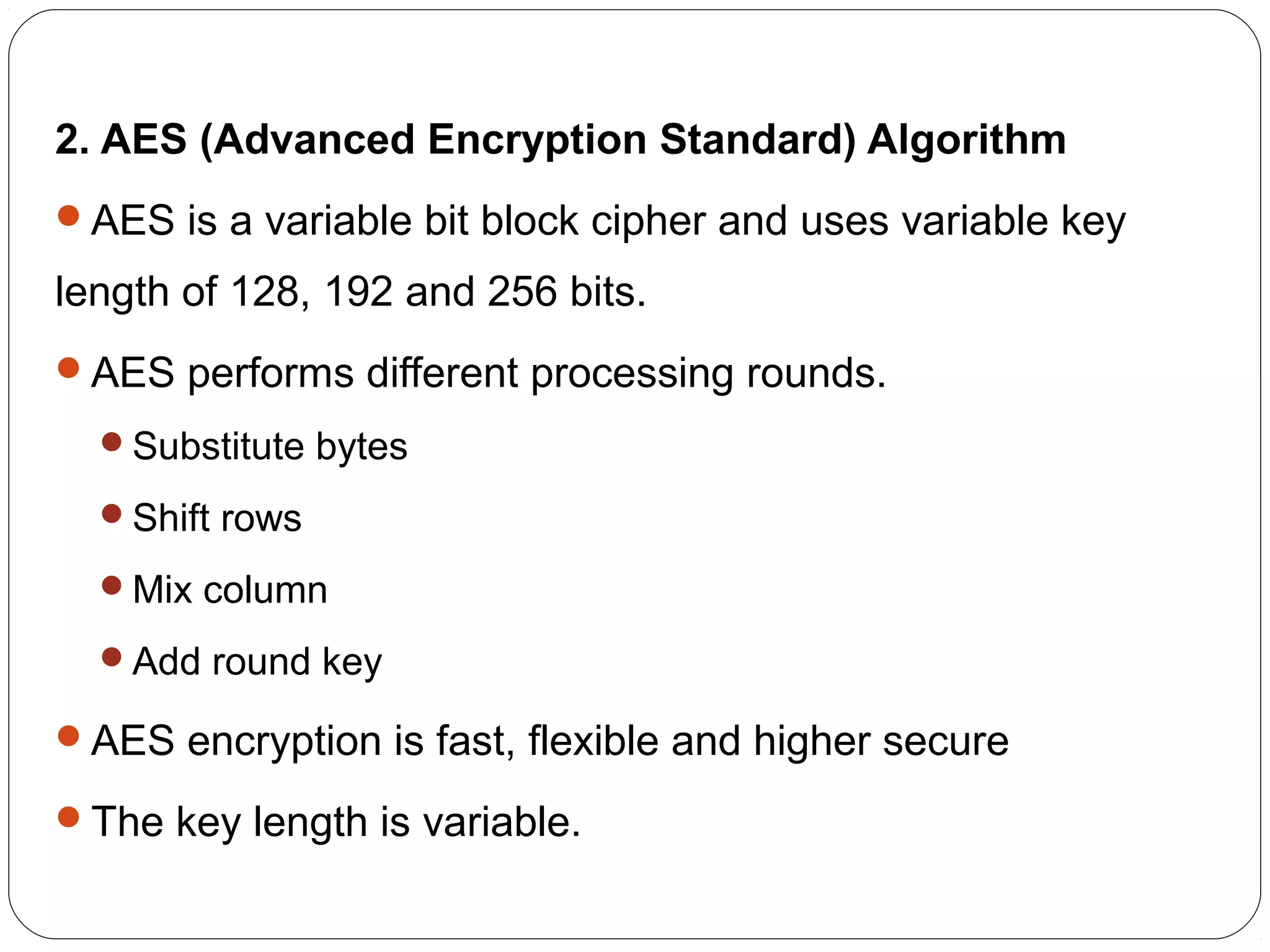
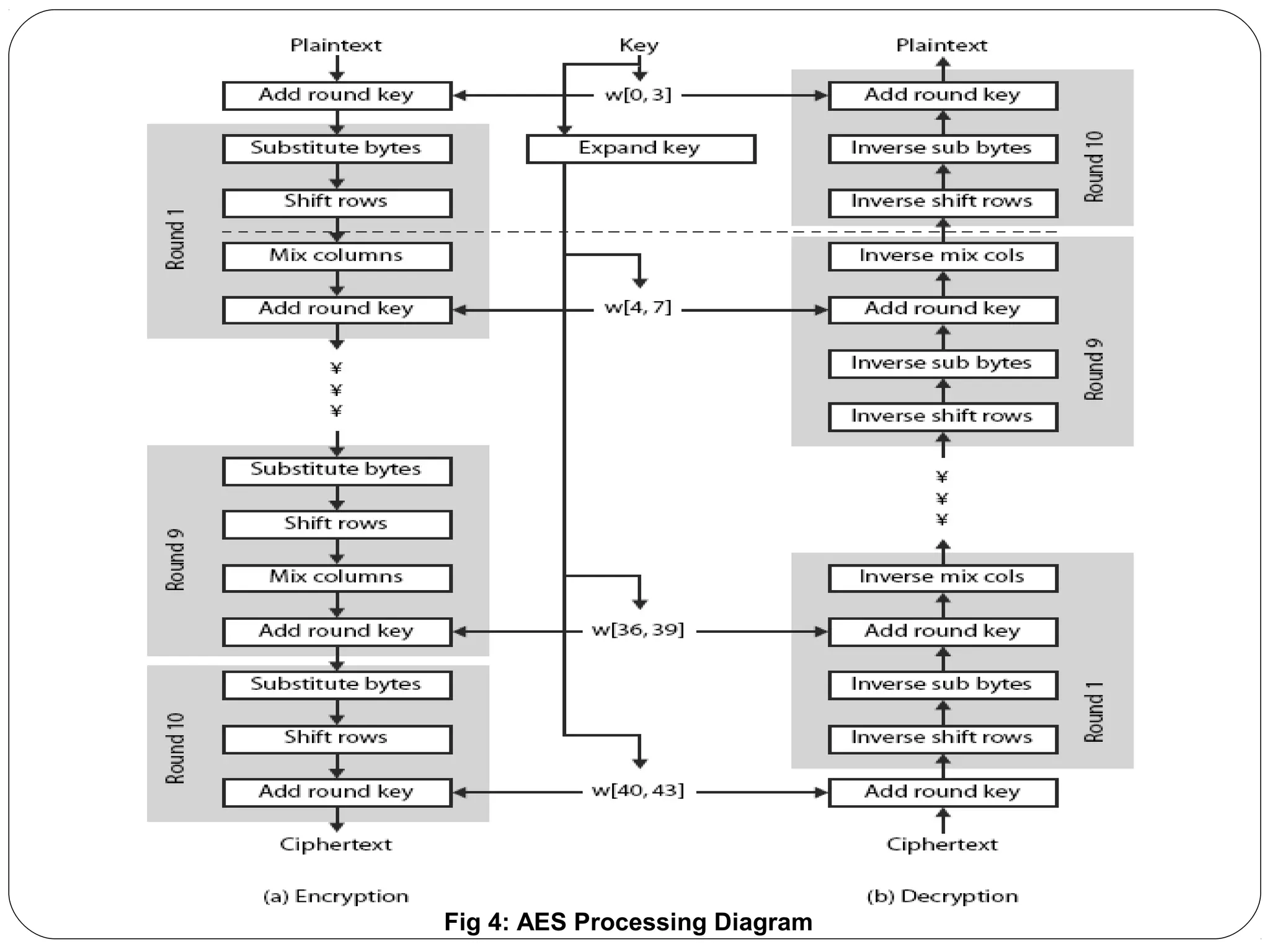
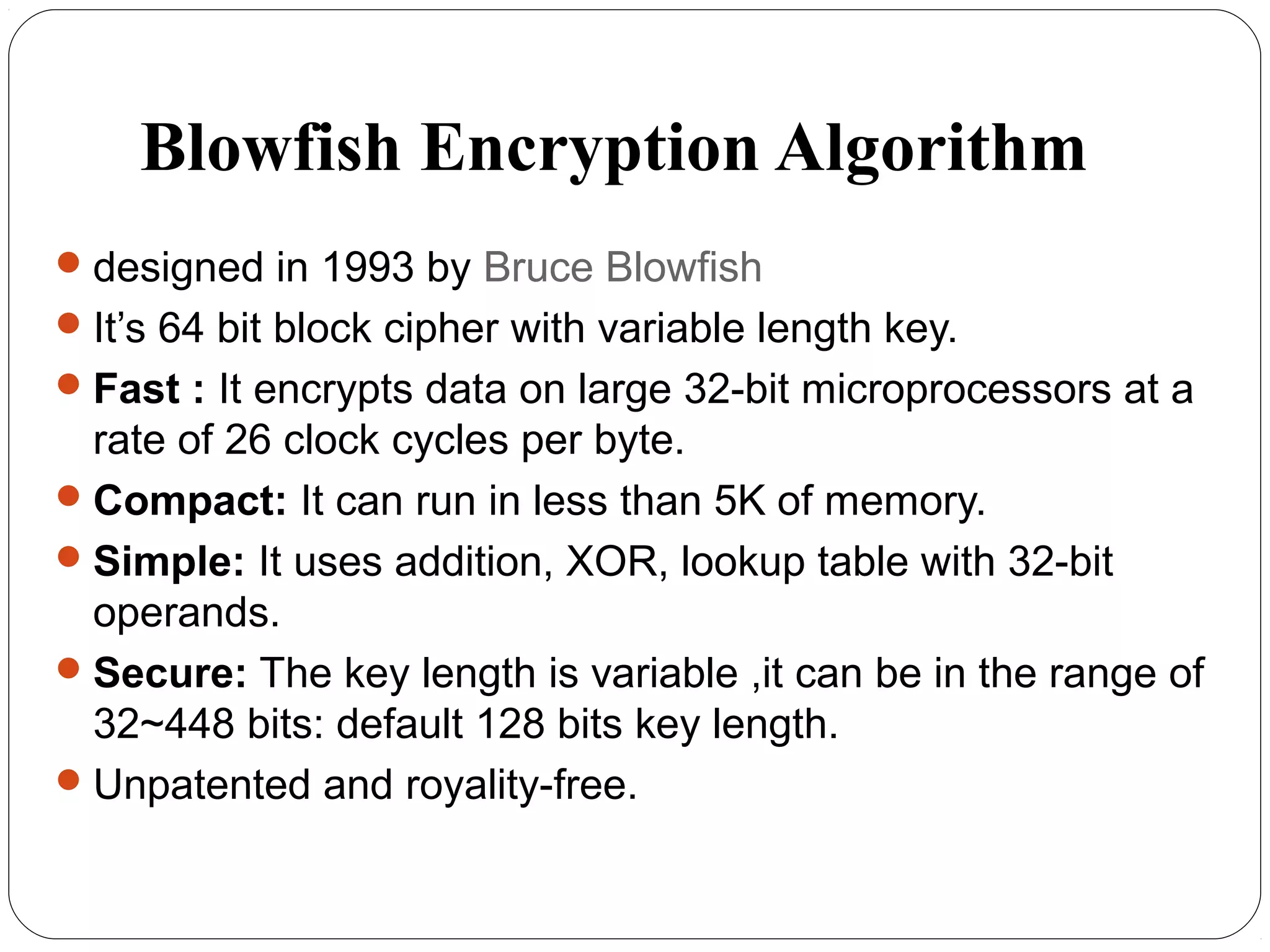
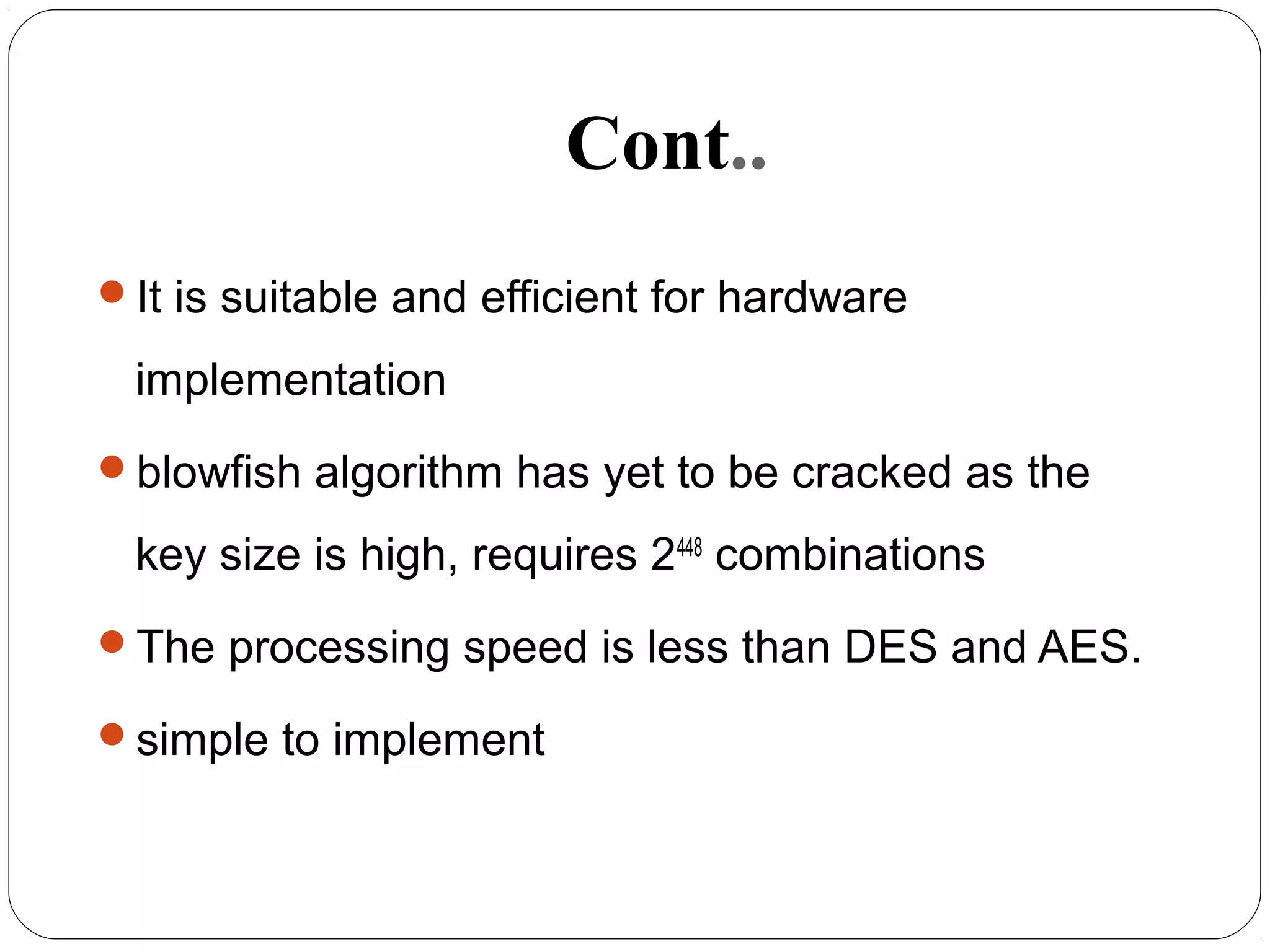
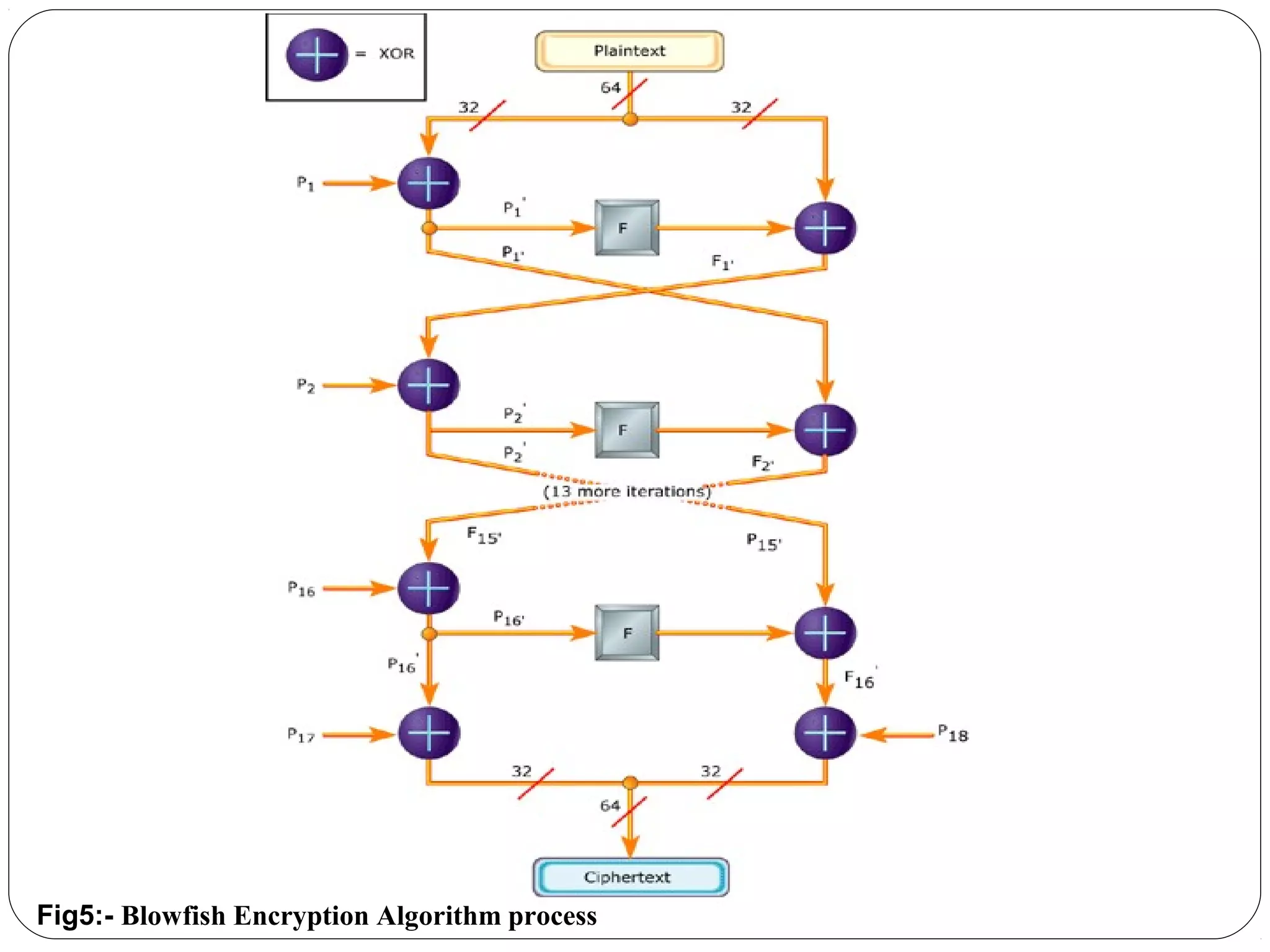
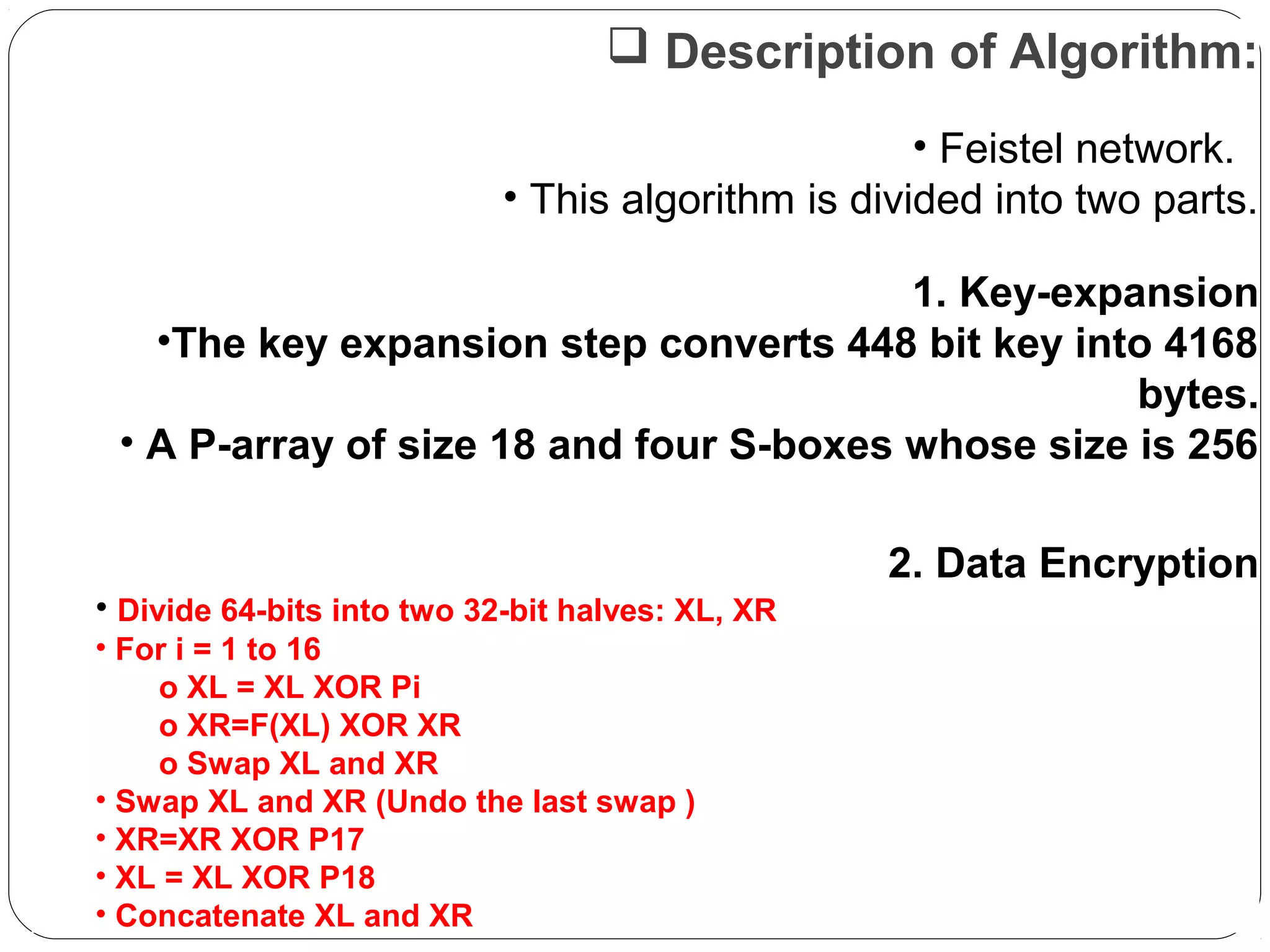
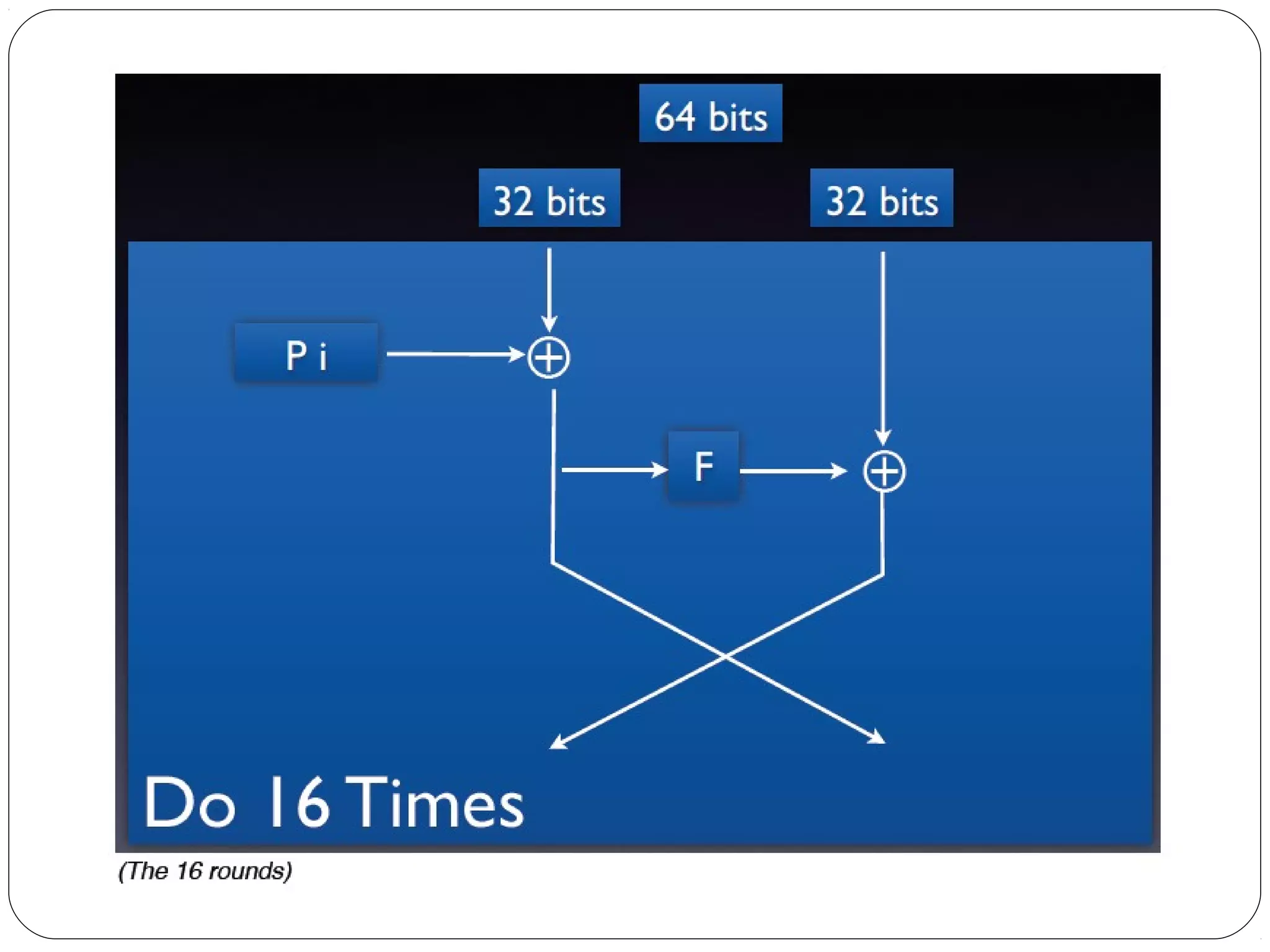
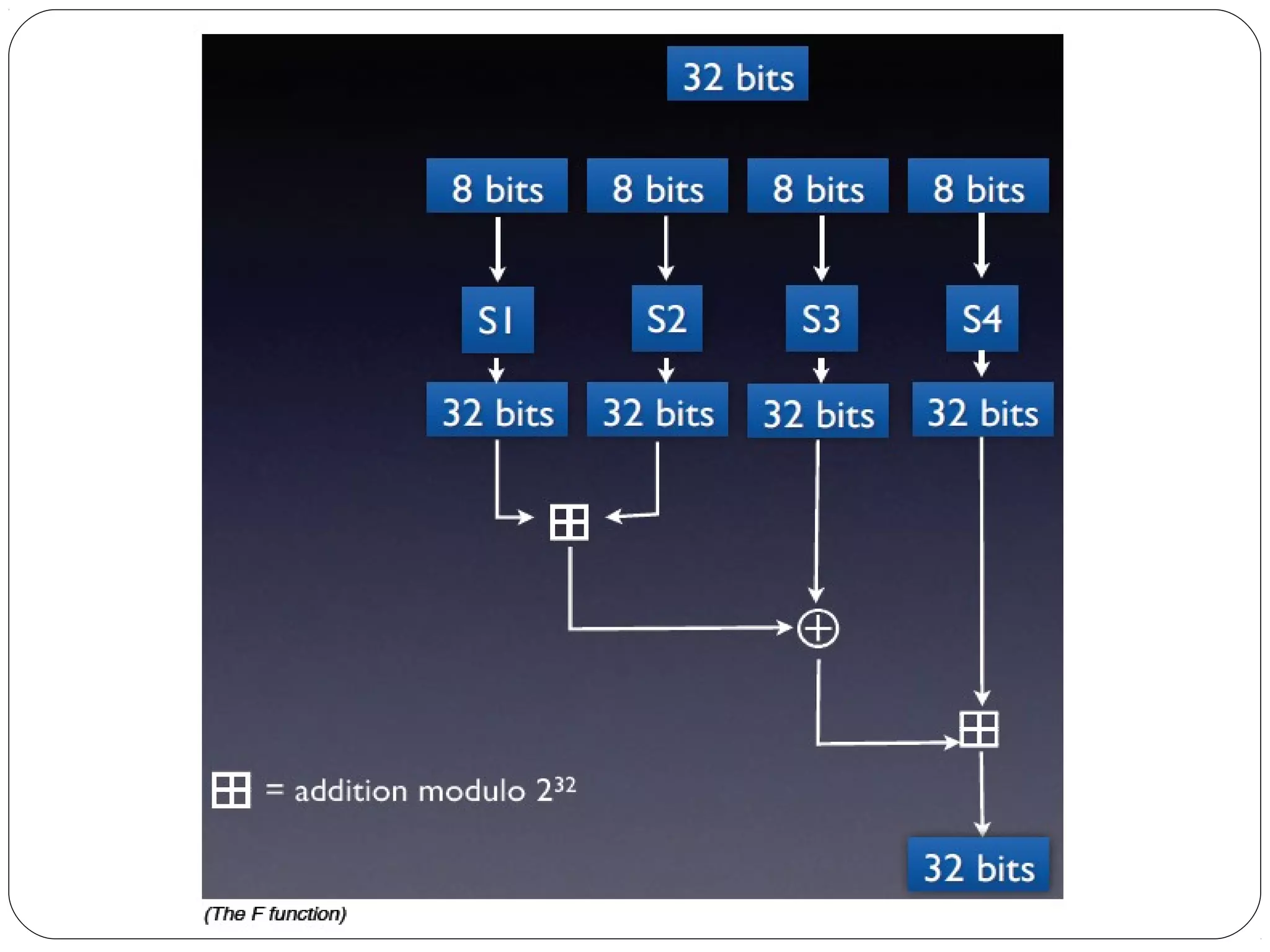
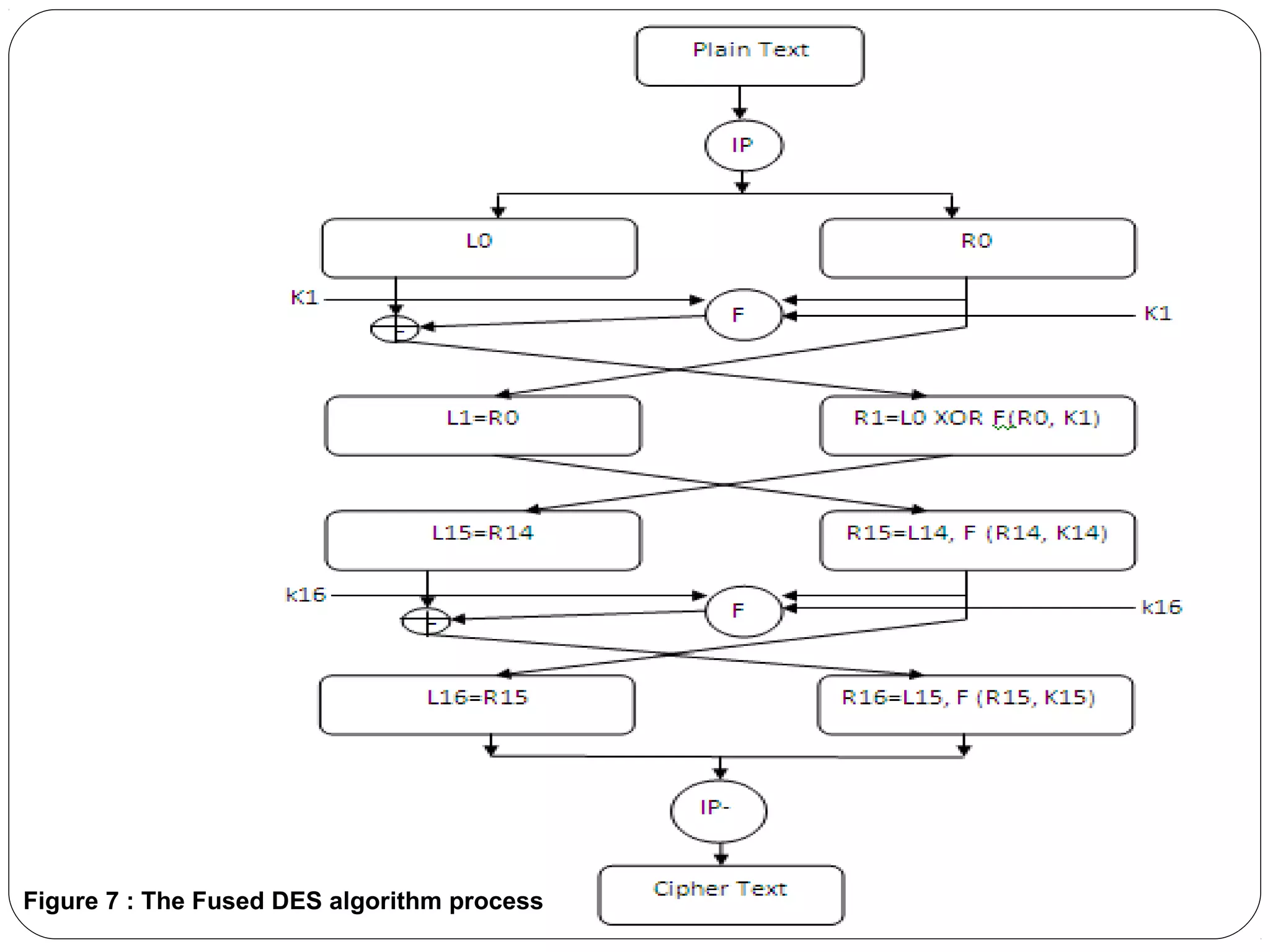
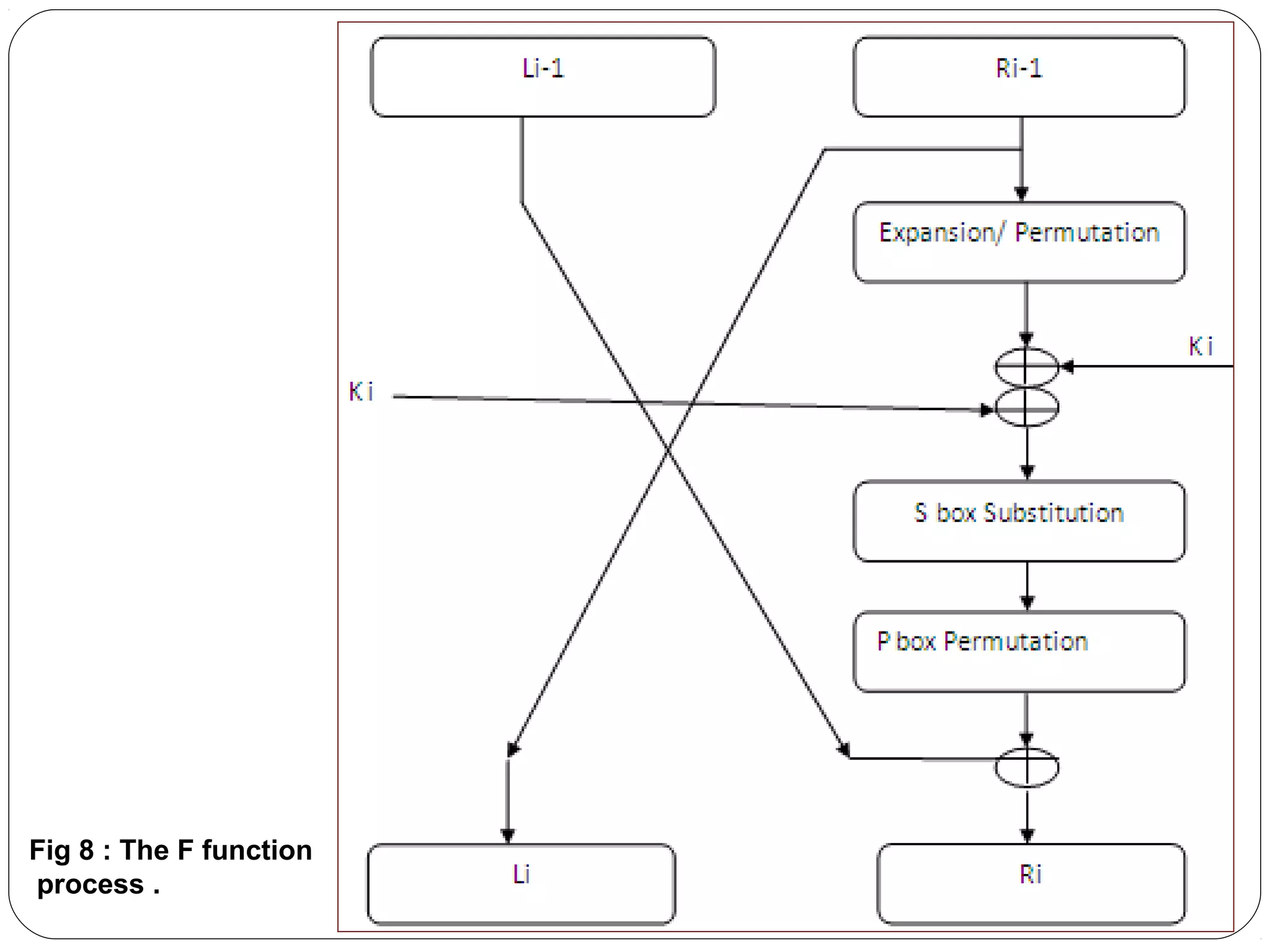
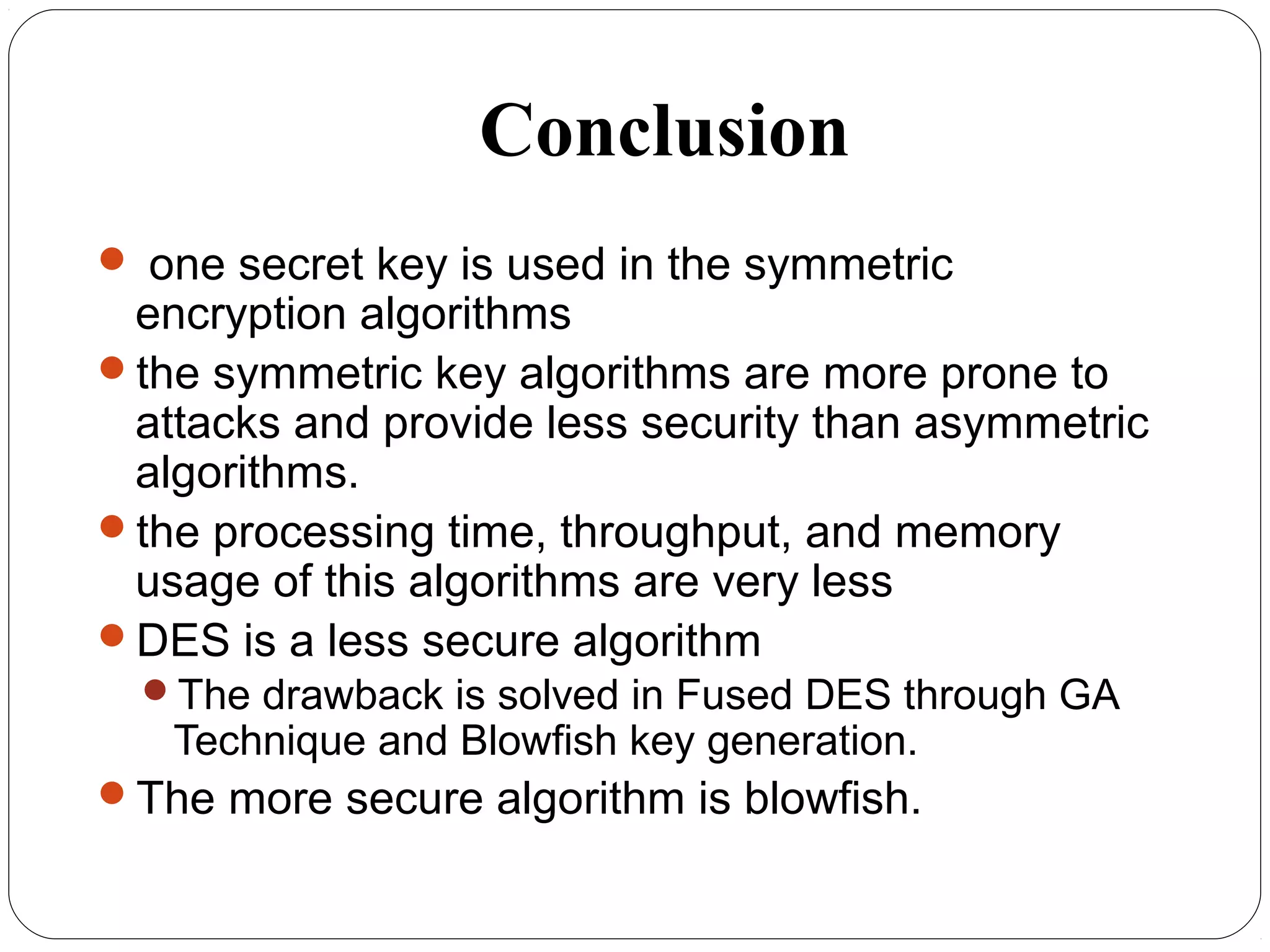
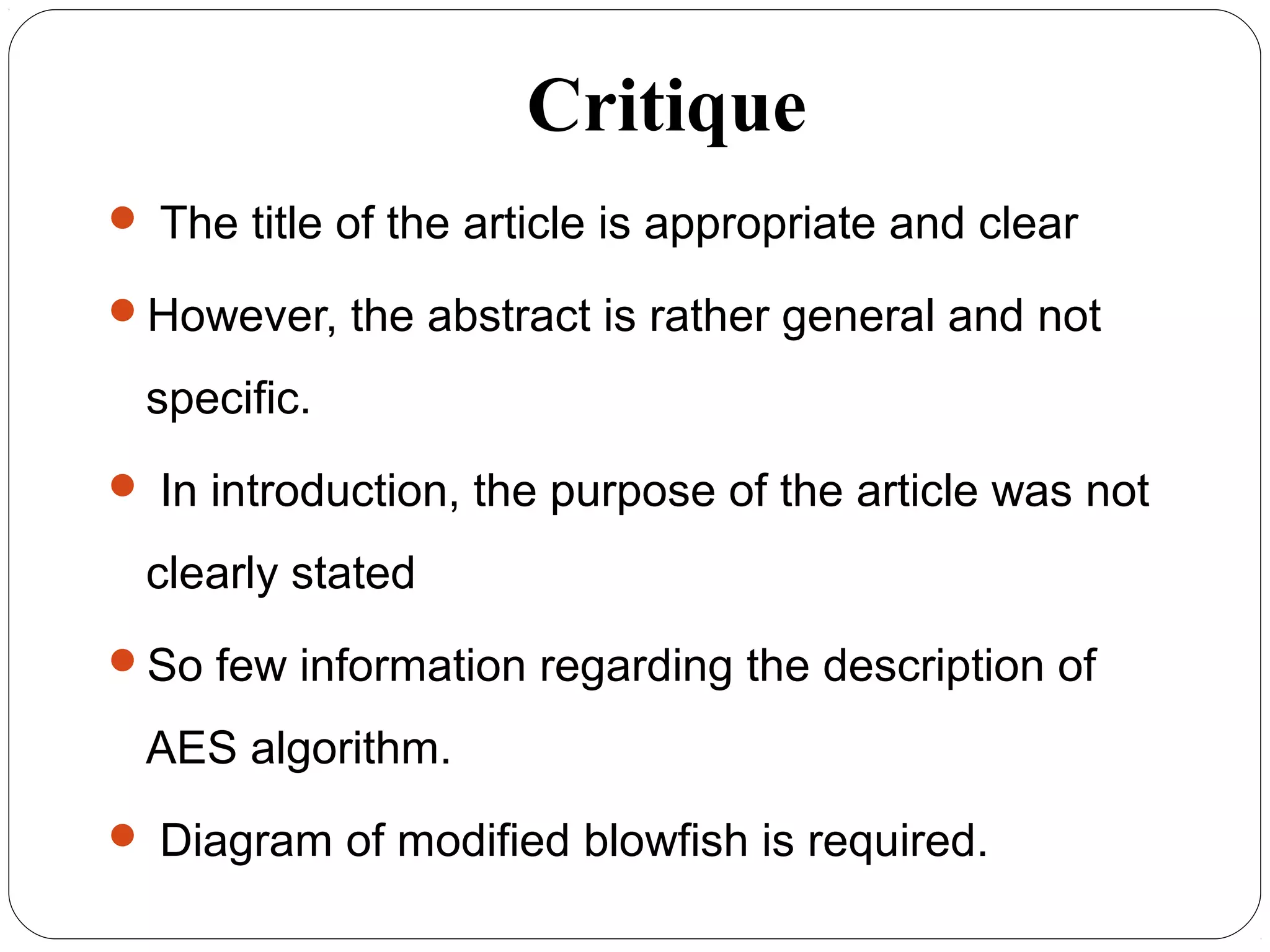
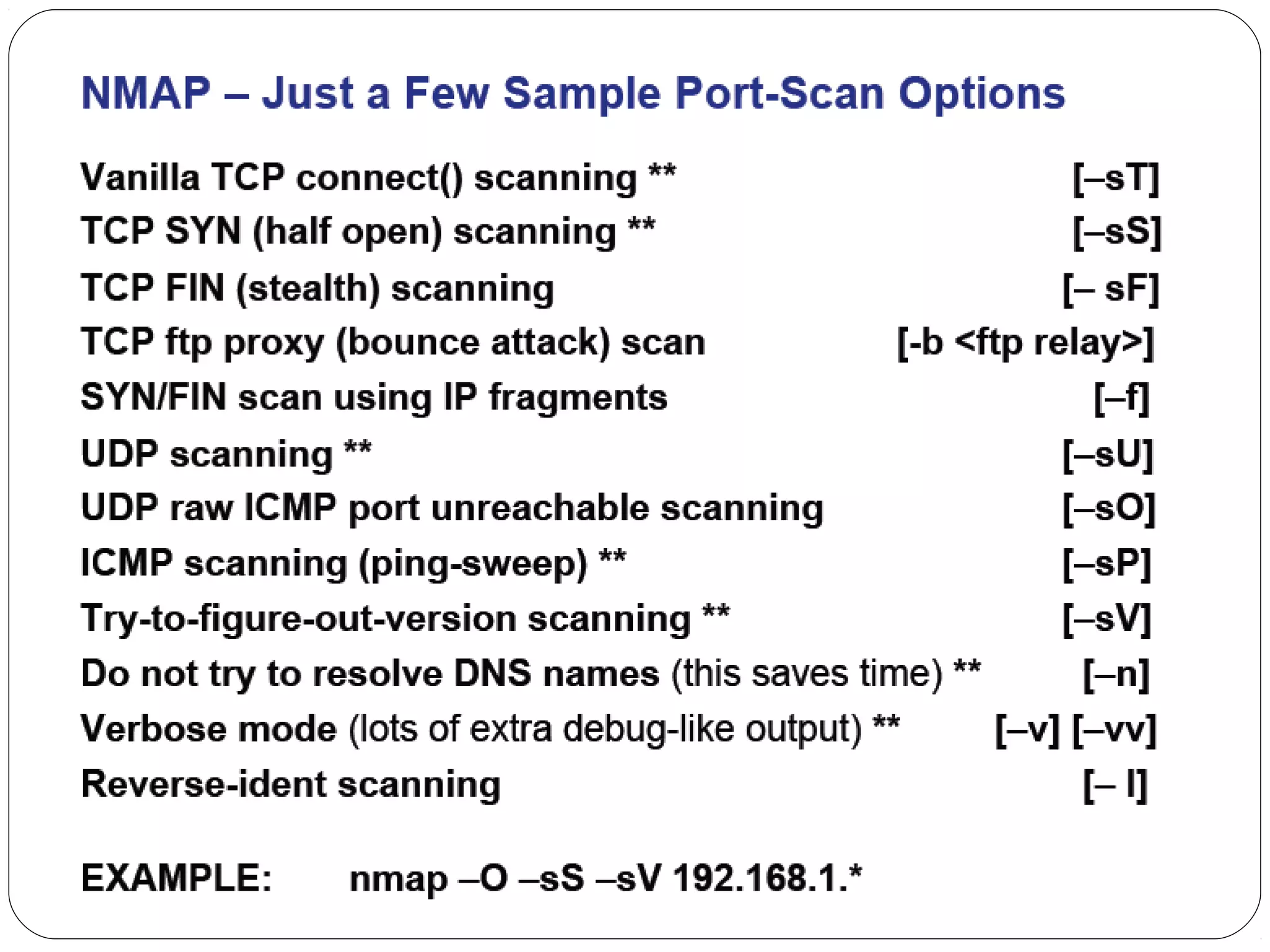
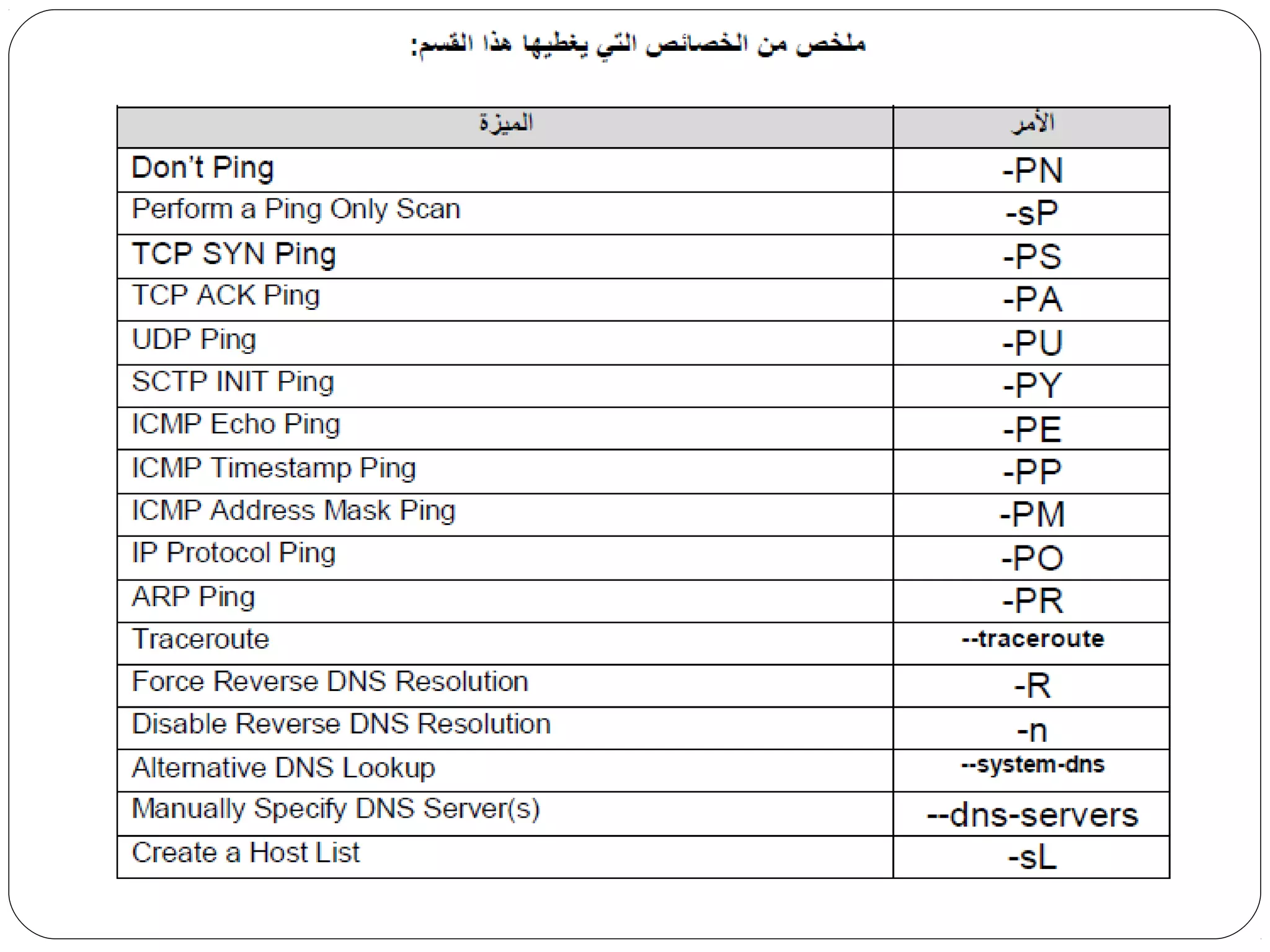
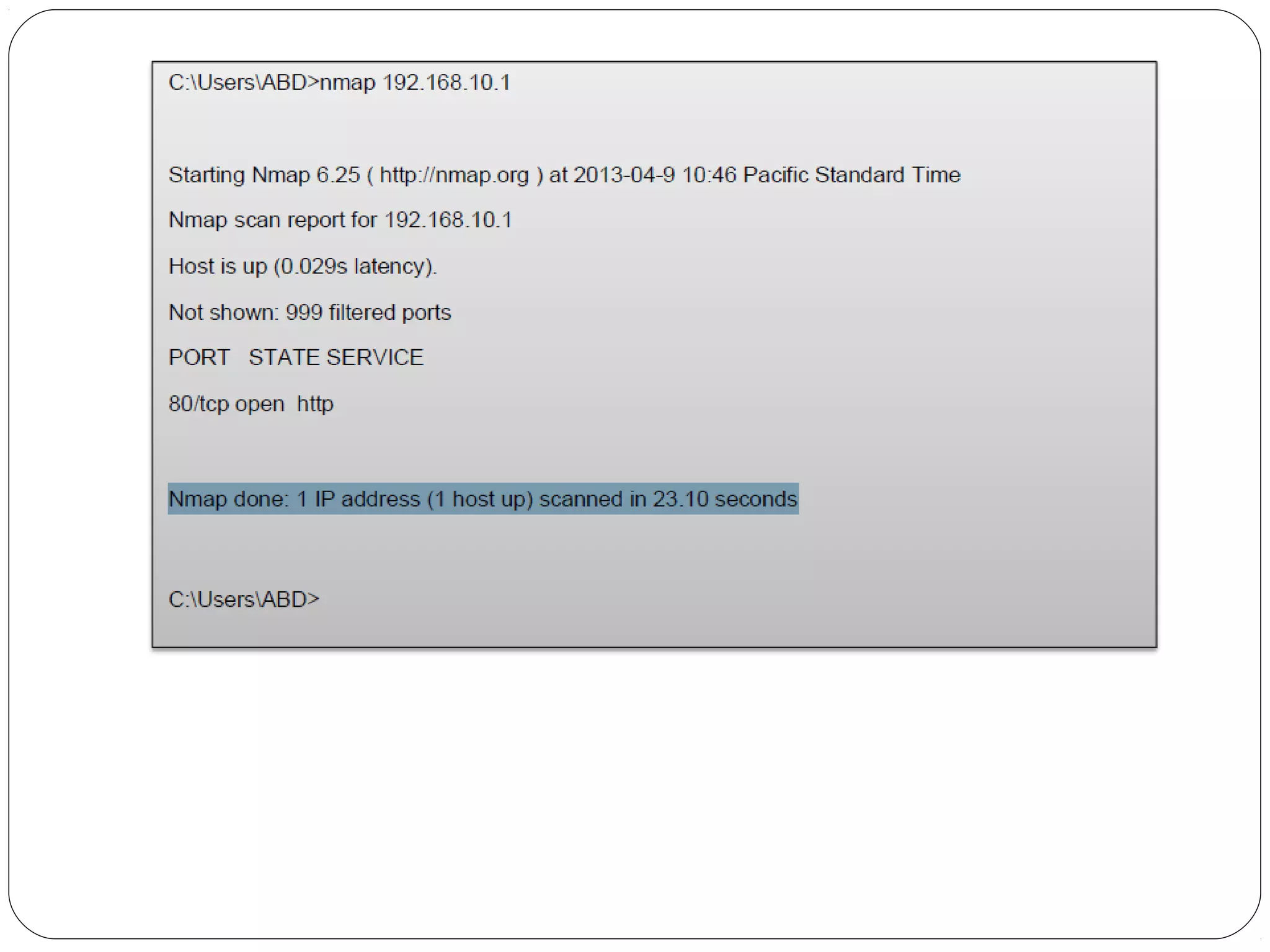
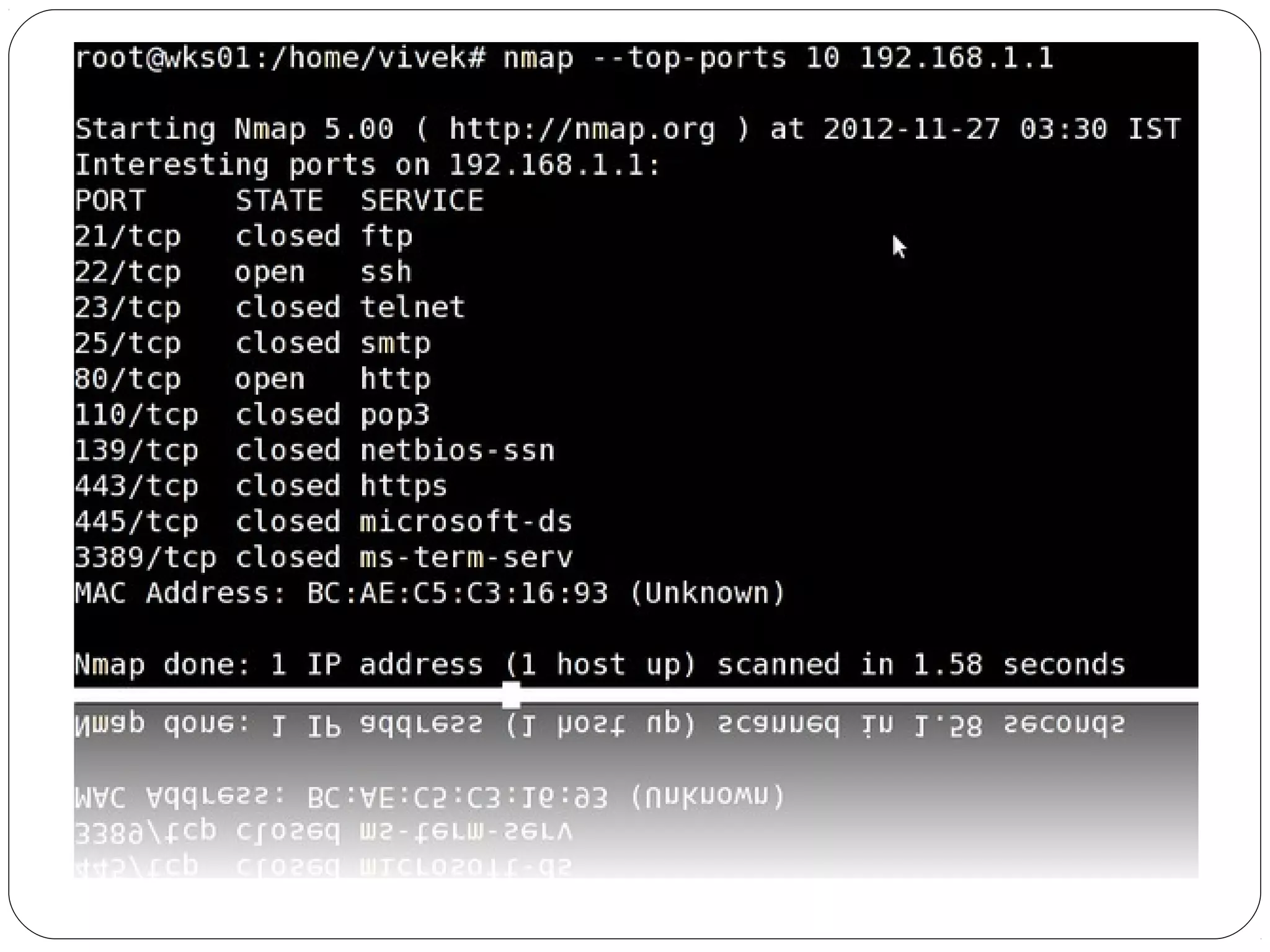
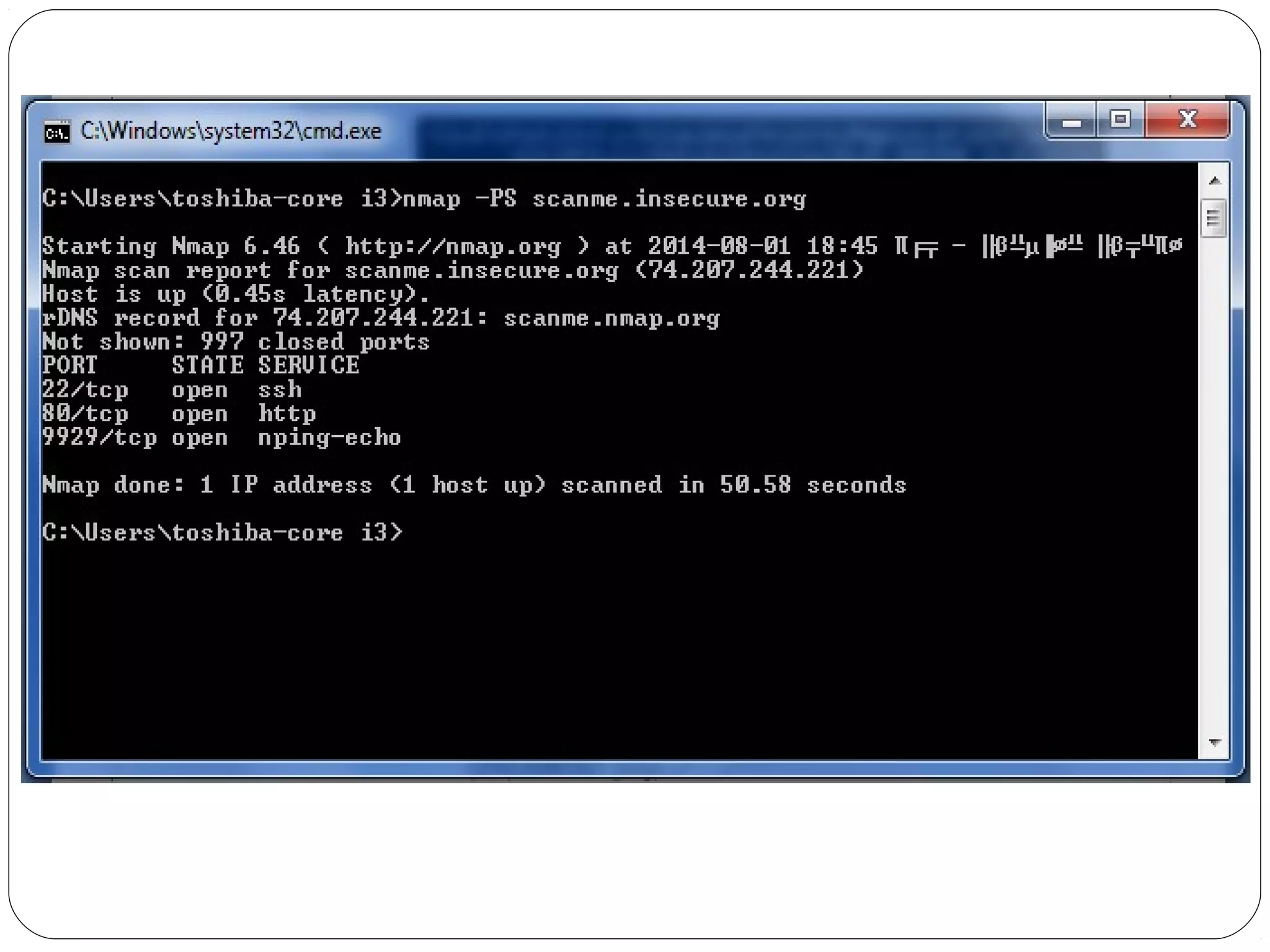
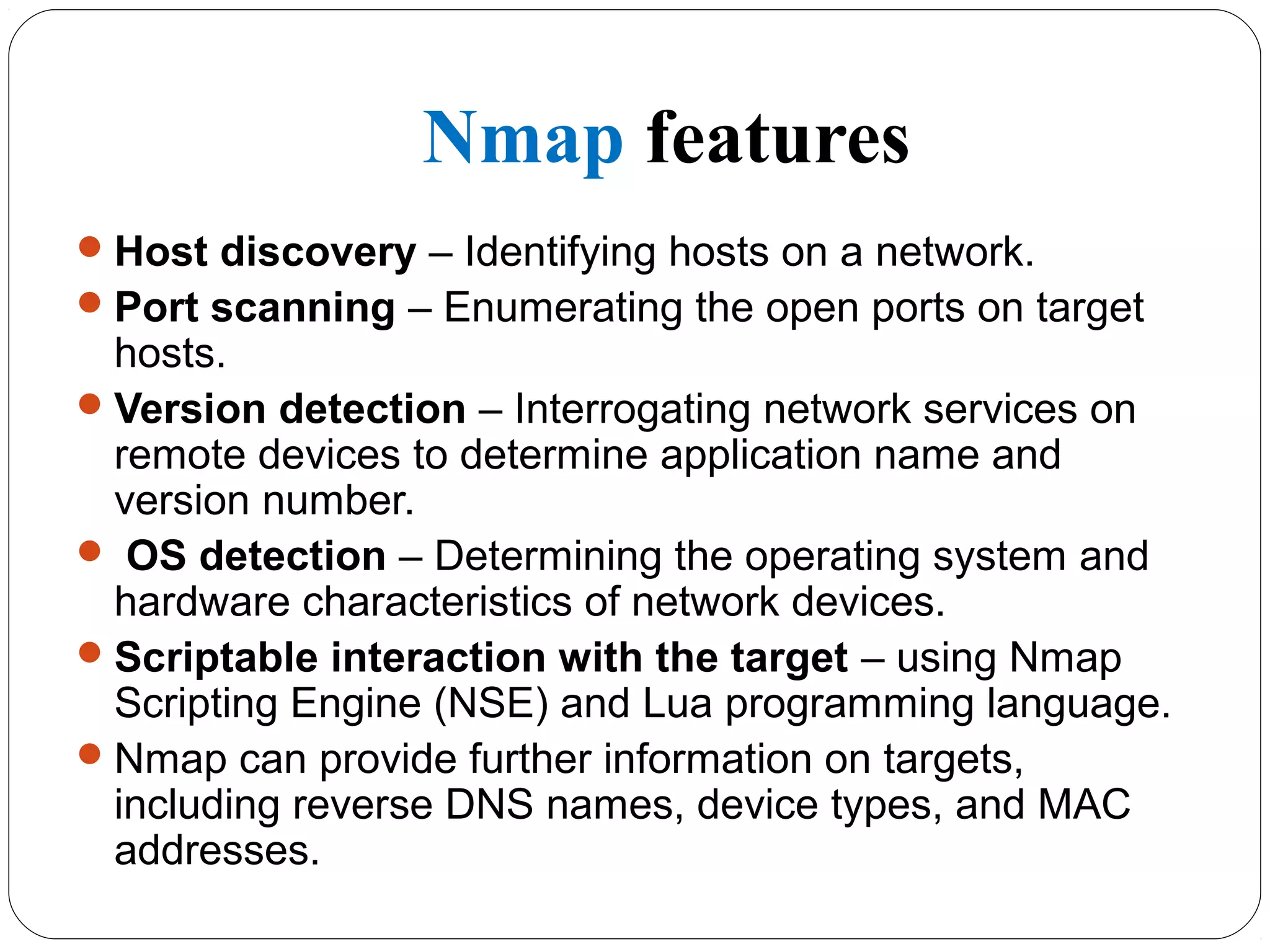
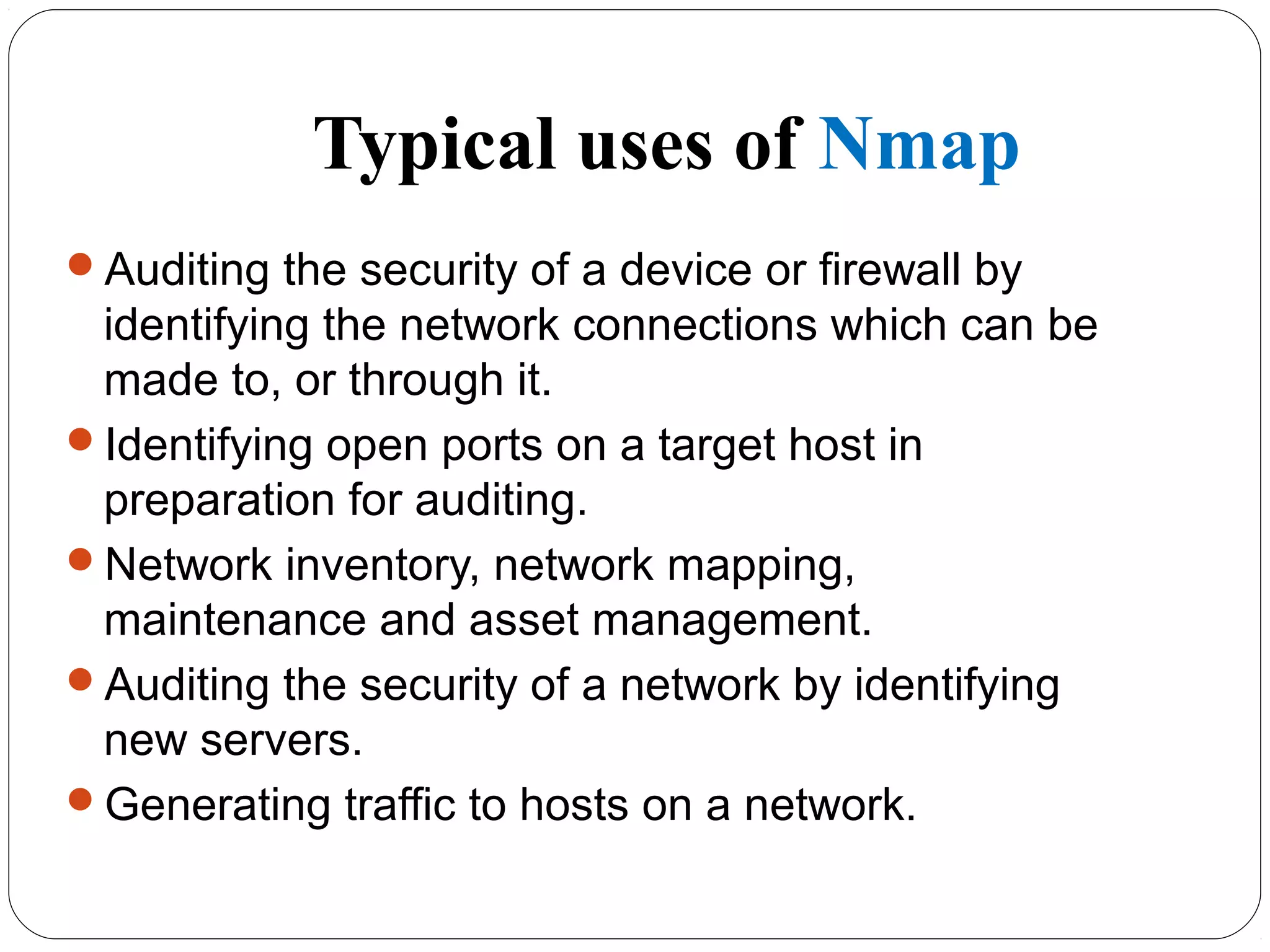
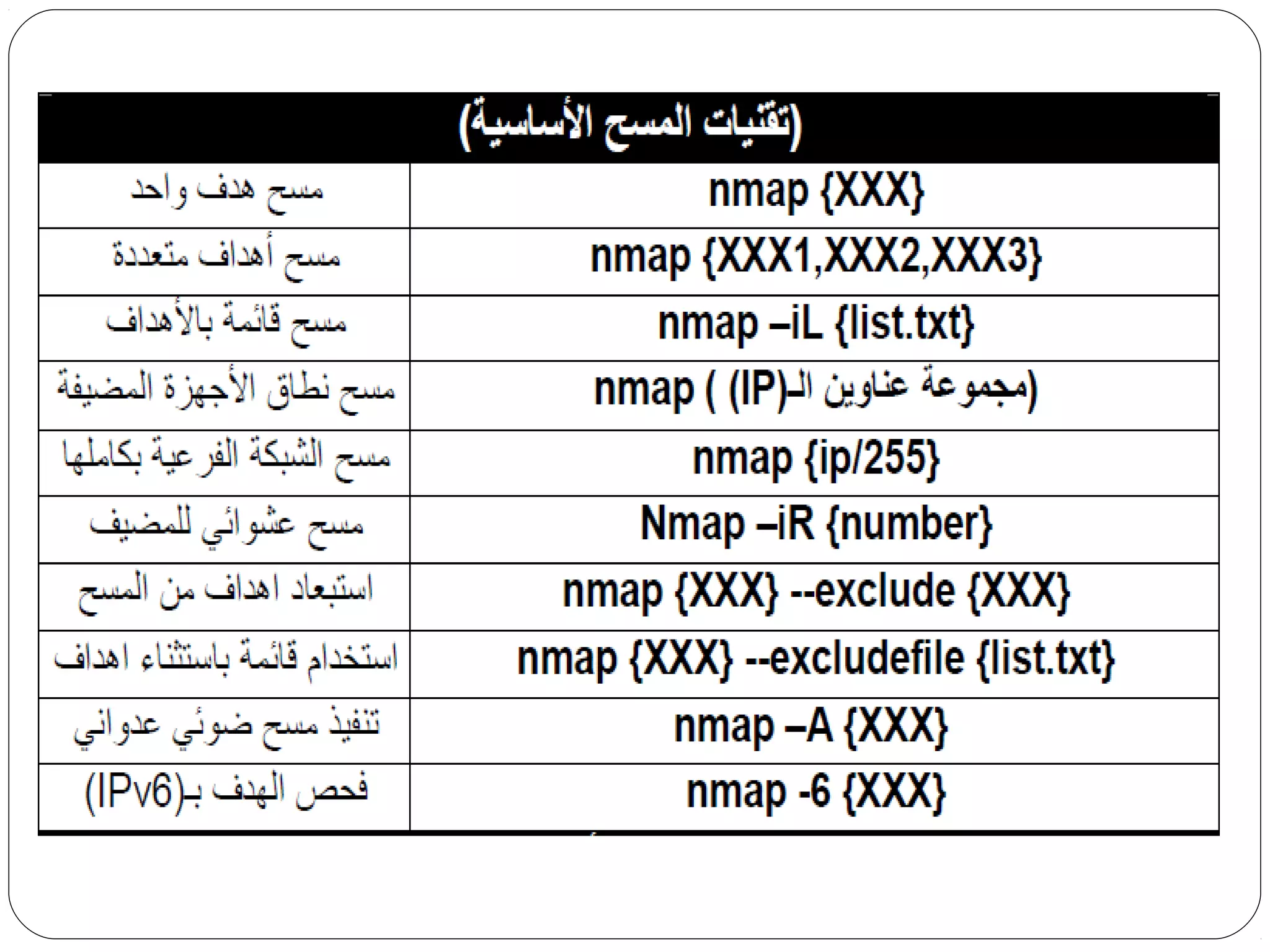
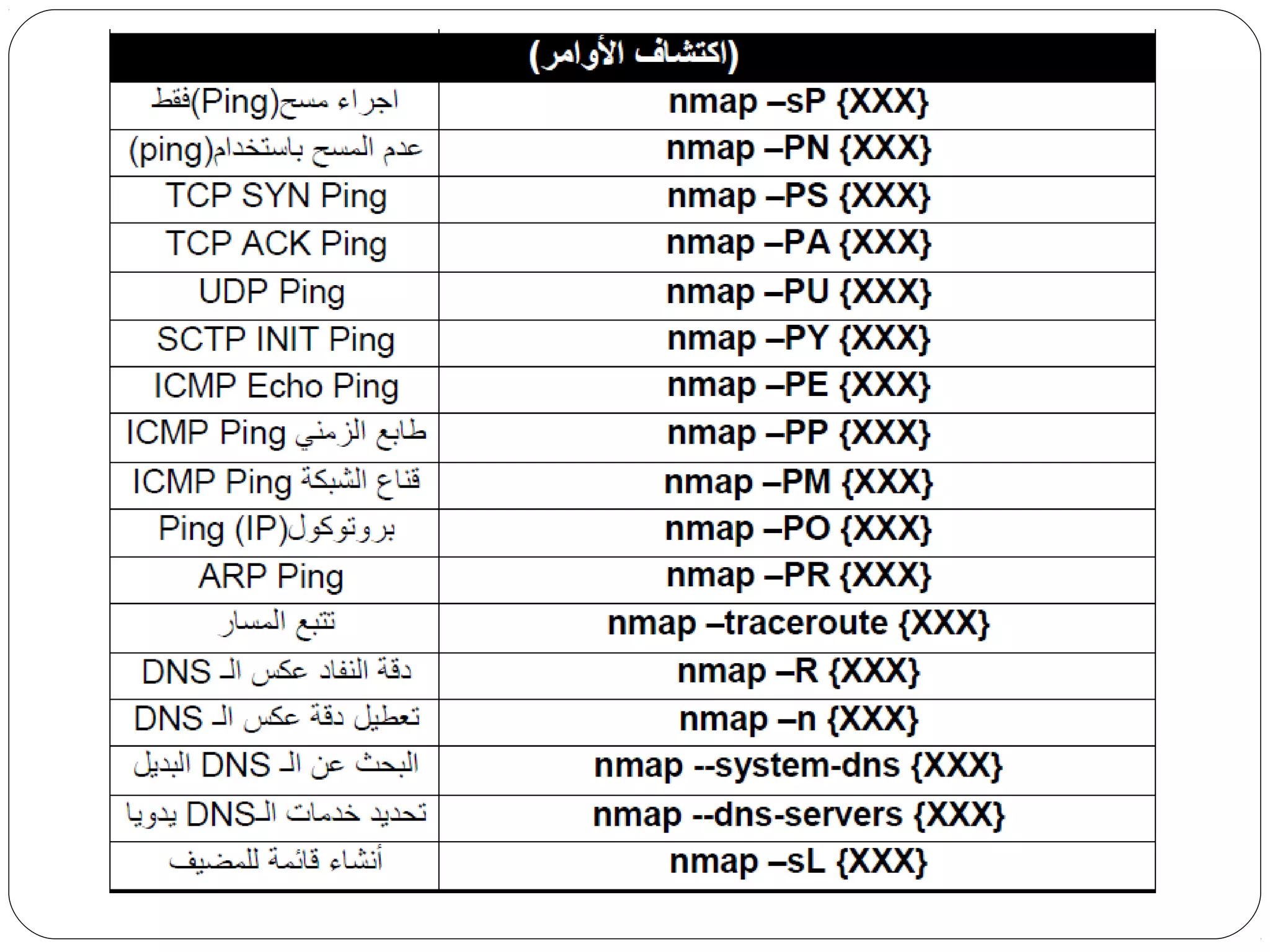
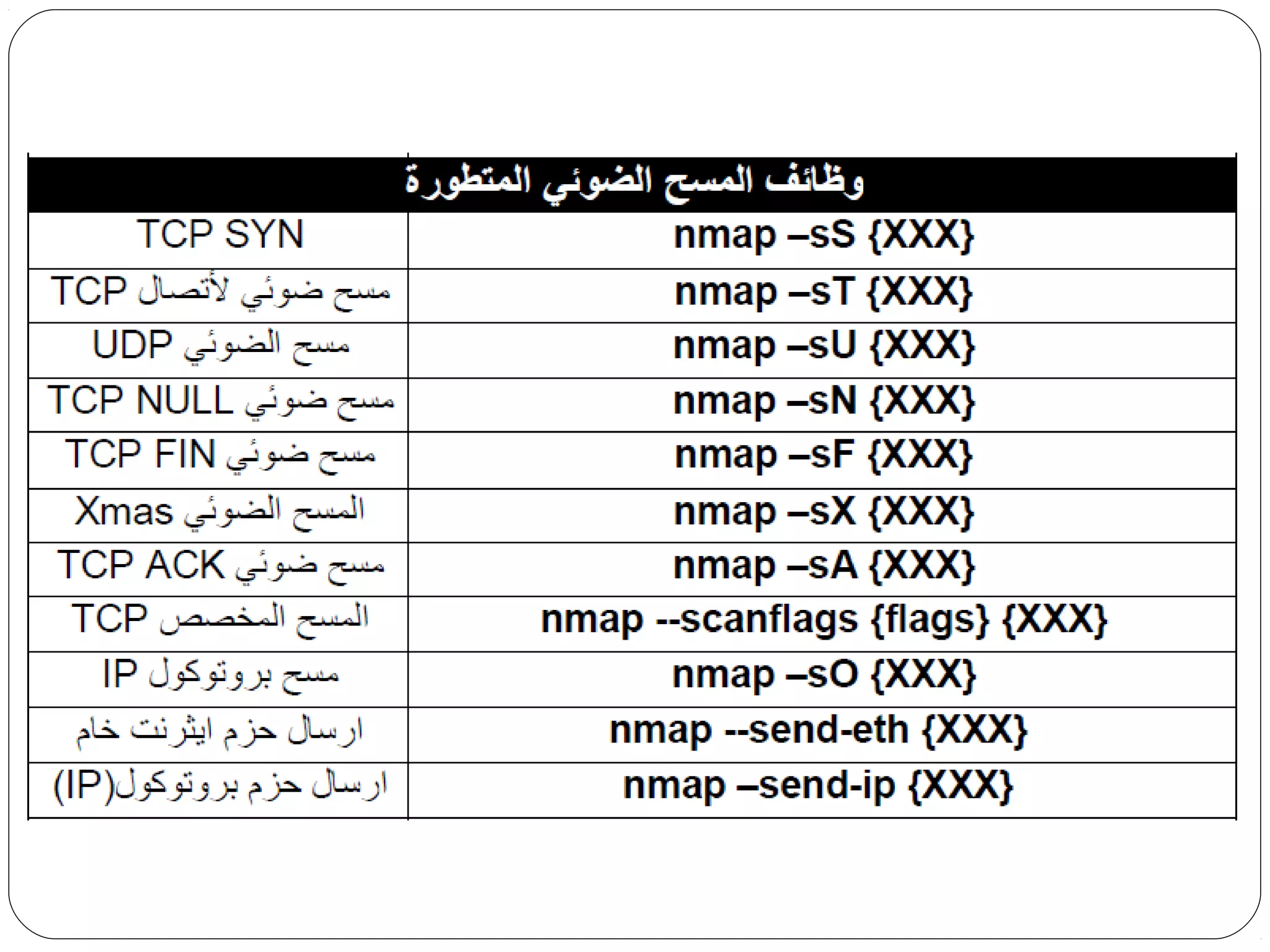
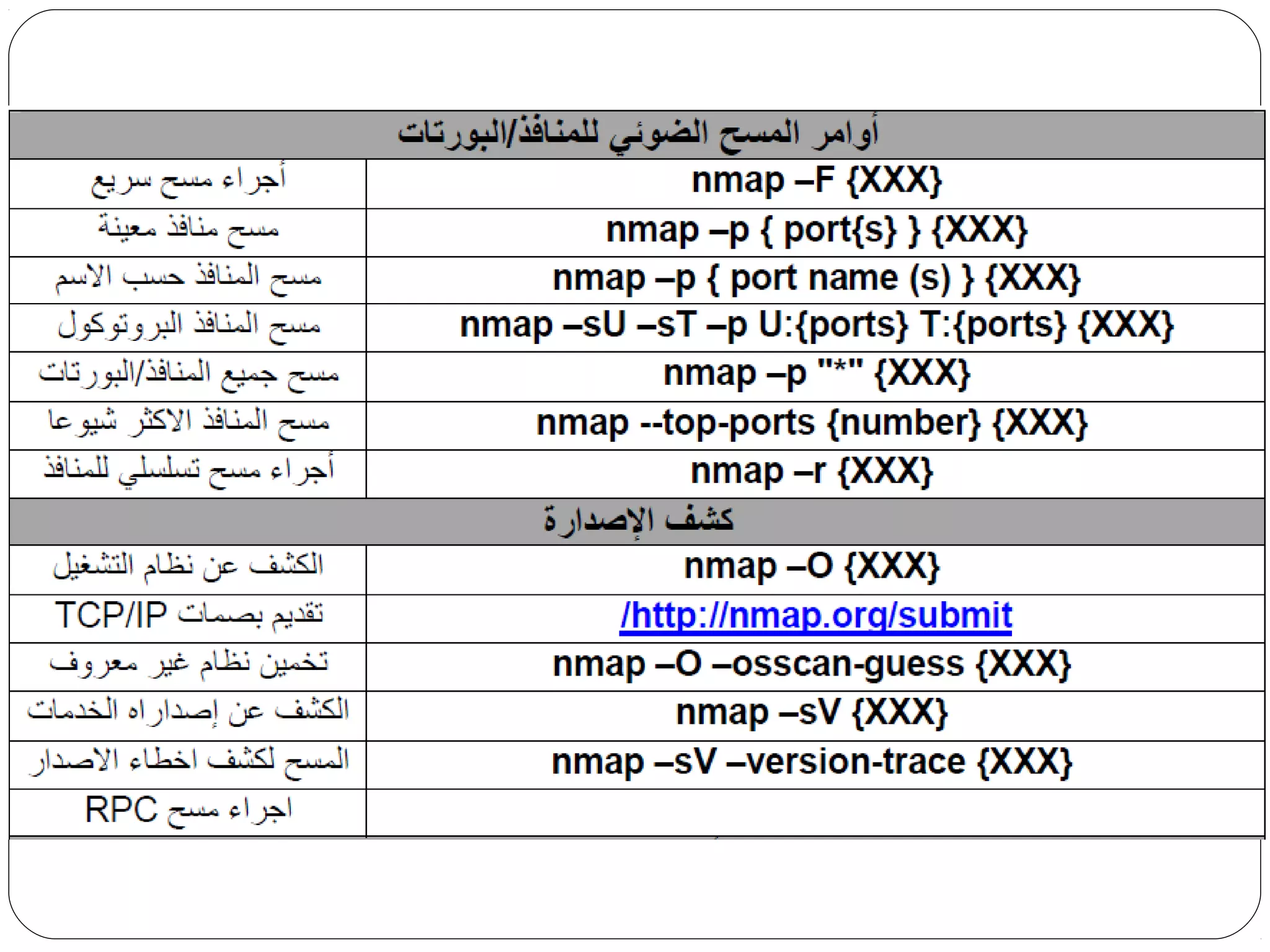
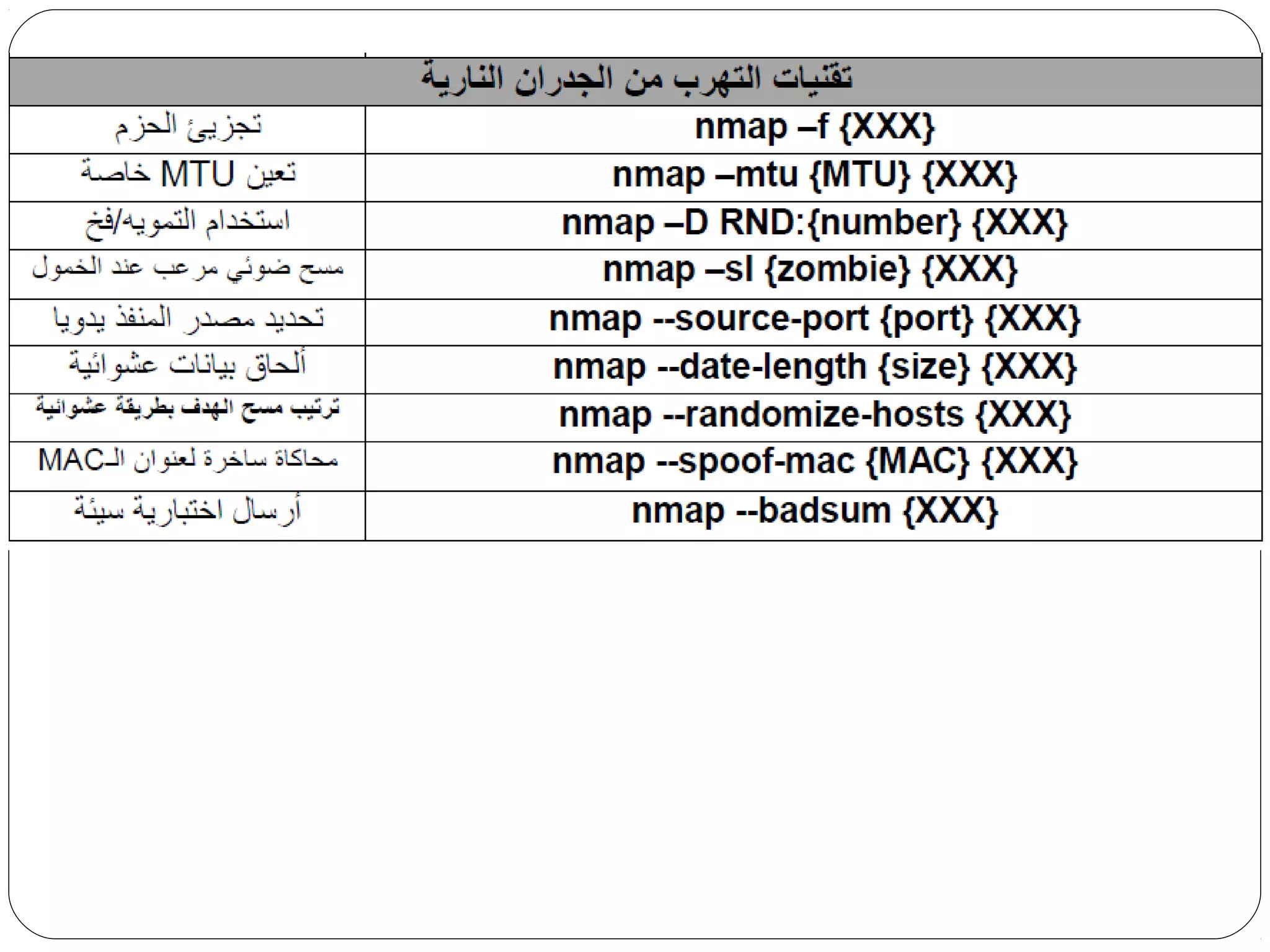
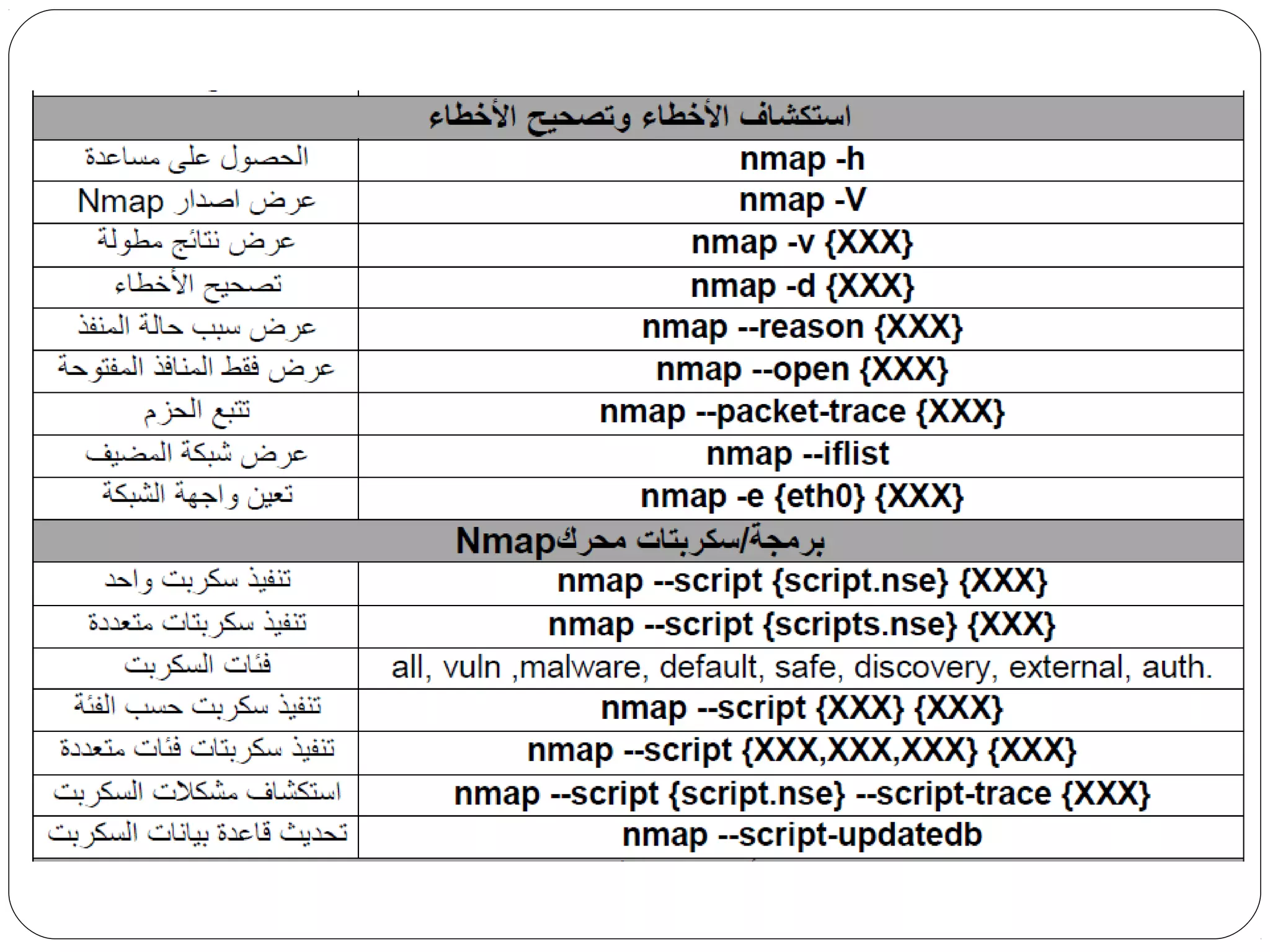
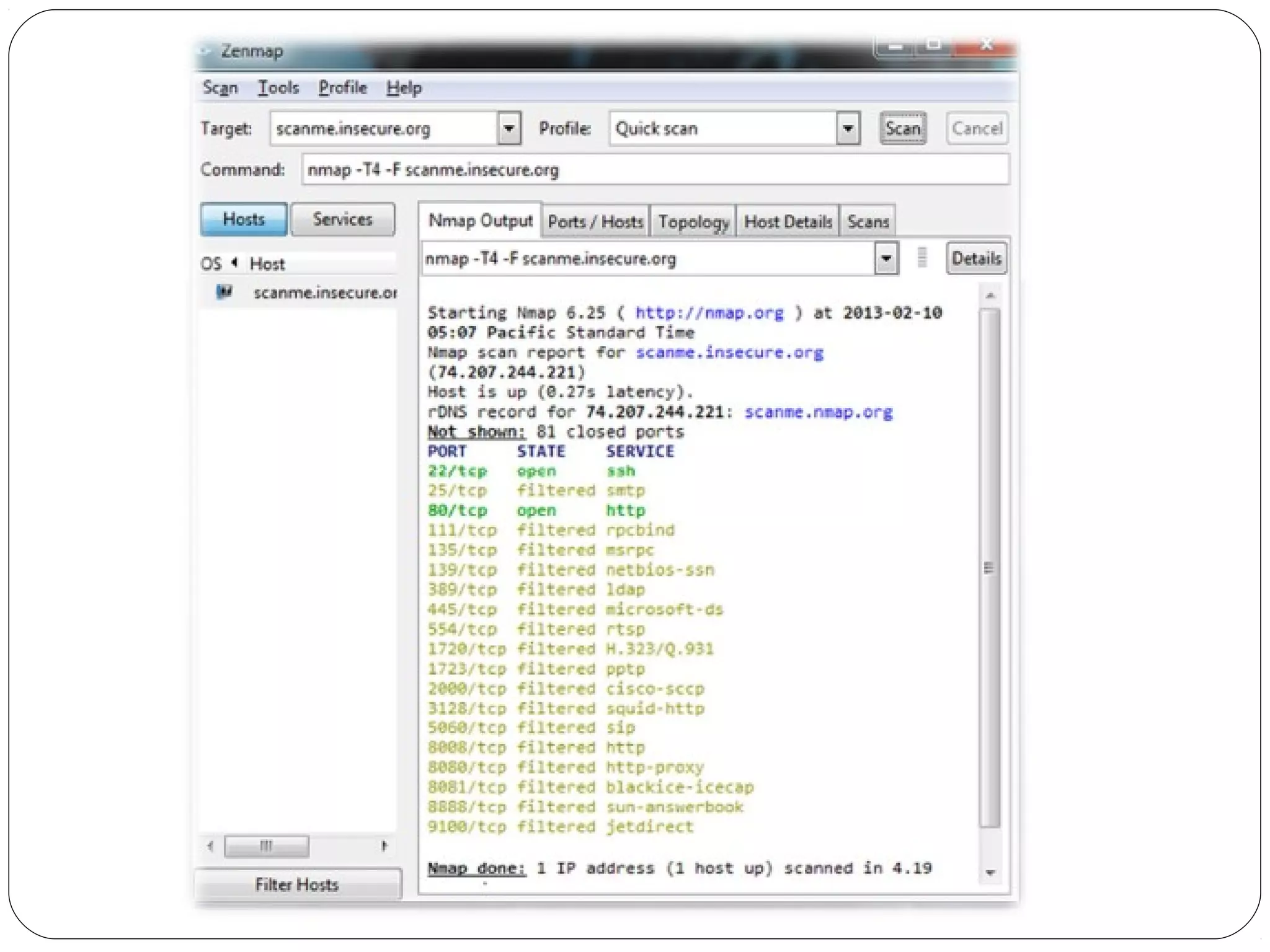
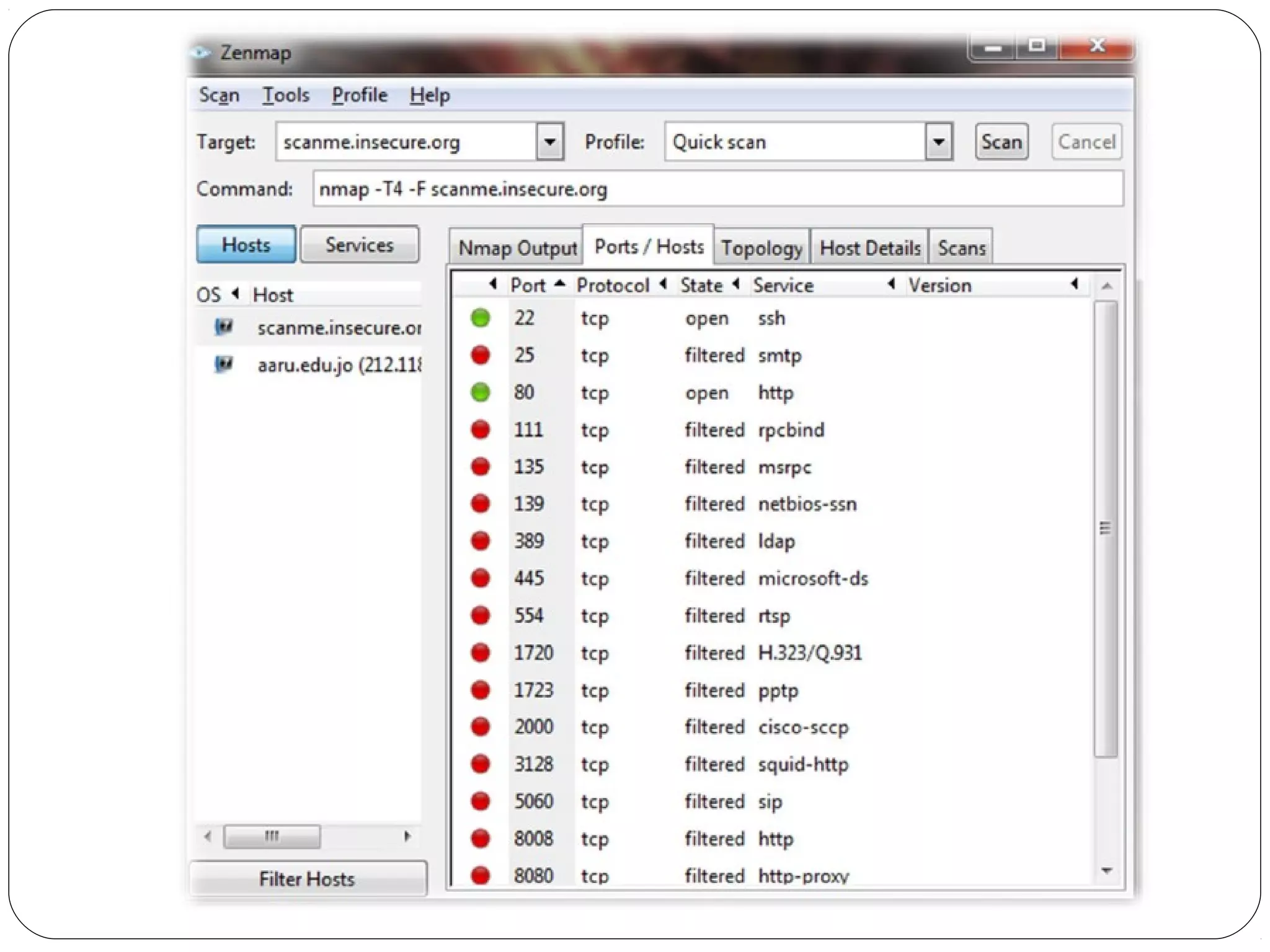
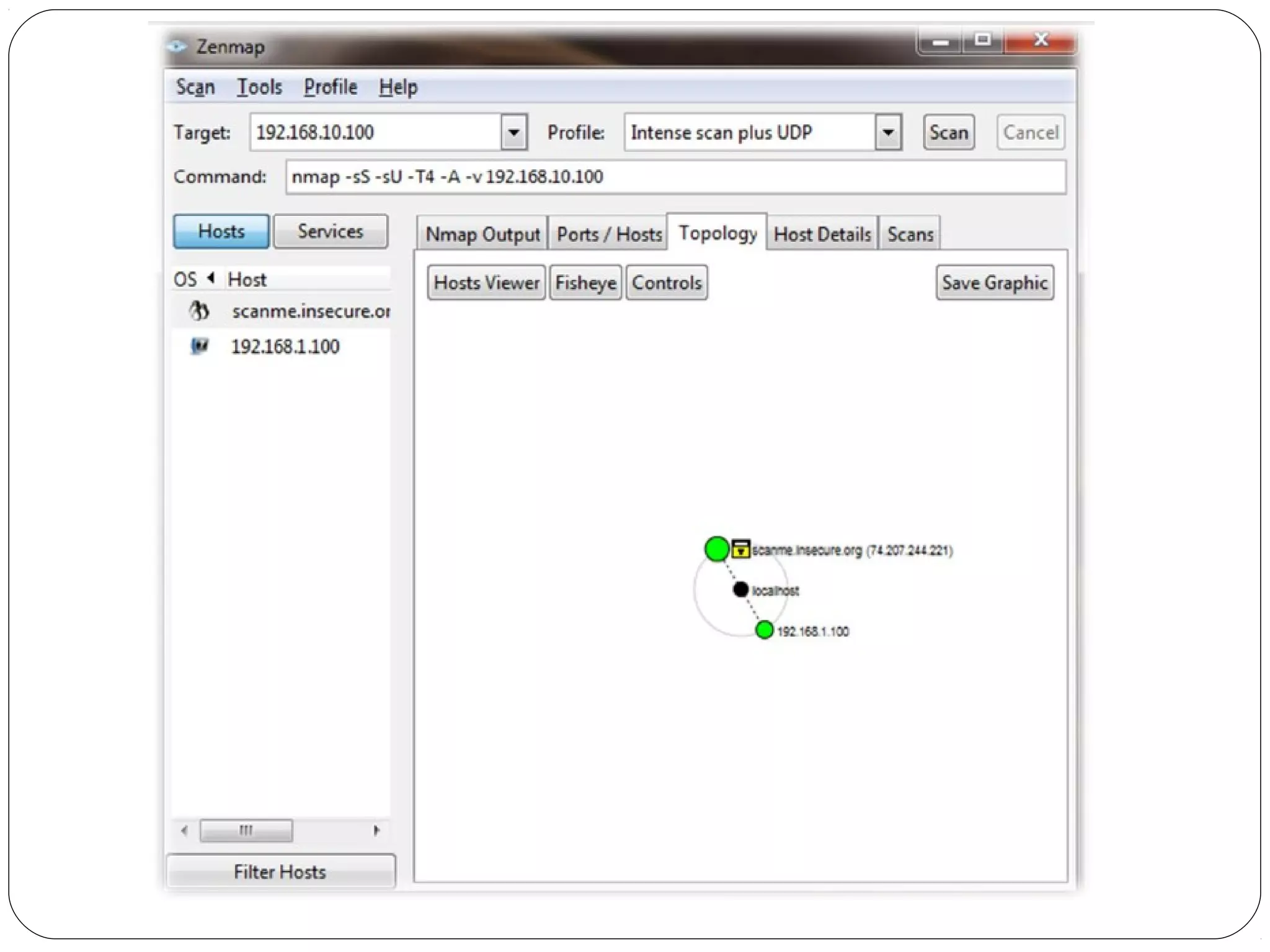
The document provides a comprehensive overview of cryptography, specifically focusing on cryptographic systems such as the AES (Advanced Encryption Standard) and its structure, implementation, and security features. It discusses different types of ciphers and their applications in ensuring confidentiality, integrity, and authentication in digital communications. Additionally, it reviews various symmetric encryption algorithms, evaluating their strengths and weaknesses, emphasizing the importance of key length and processing efficiency.