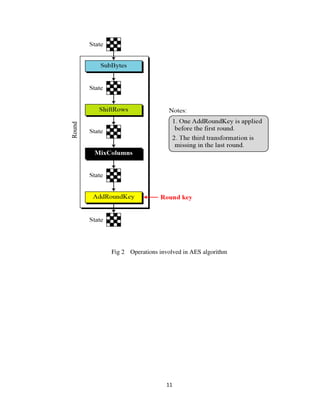
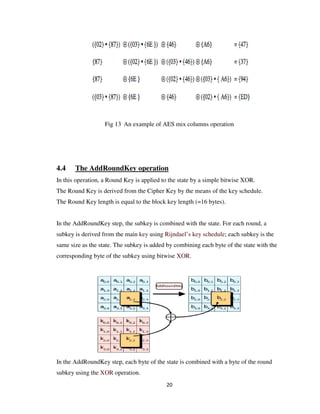
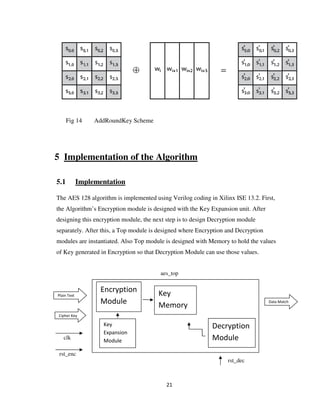
This document describes a student project to implement the Advanced Encryption Standard (AES) in Verilog. AES is a symmetric block cipher that uses 128-bit blocks and 128/192/256-bit keys. The project aims to develop optimized and synthesizable Verilog code to encrypt and decrypt 128-bit data using AES. The document provides background on cryptography, AES, and its algorithm which includes key expansion, substitution, transposition, and mixing operations. It also outlines the implementation, encryption, decryption, and performance estimation aspects of the project.












![14
b (i,j) = SBox[a(i,j)]
The inverse of SubBytes is the same operation, using the inversed S-Box, which is also
precalculated.
Fig 4 SubBytes step
In the SubBytes step, each byte in the state is replaced with
its entry in a fixed 8-bit lookup table, S; b(i,j) = S(i,j)
Fig 5 S-box implementation on the state matrix](https://image.slidesharecdn.com/aesreport-160405122804/85/Advanced-Encryption-Standard-AES-14-320.jpg)









![26
REFERENCES
[1] AES page available via http://www.nist.gov/CryptoToolkit.4
[2] Computer Security Objects Register (CSOR): http://csrc.nist.gov/csor/.
[3] J. Daemen and V. Rijmen, AES Proposal: Rijndael, AES Algorithm
Submission, September 3, 1999, available at [1].
[4] J. Daemen and V. Rijmen, The block cipher Rijndael, Smart Card research and
Applications, LNCS 1820, Springer-Verlag, pp. 288-296.
[5] B. Gladman’s AES related home page
http://fp.gladman.plus.com/cryptography_technology/.
[6] A. Lee, NIST Special Publication 800-21, Guideline for Implementing
Cryptography in the Federal Government, National Institute of Standards and
Technology, November 1999.
[7] A. Menezes, P. van Oorschot, and S. Vanstone, Handbook of Applied
Cryptography, CRC Press, New York, 1997, p. 81-83.
[8] J. Nechvatal, ET. al., Report on the Development of the Advanced Encryption
Standard (AES), National Institute of Standards and Technology, October 2, 2000,
[9] Understanding AES Inverse Mix-Columns Transformation Calculation.pdf
[10] http://www.ijsrd.com/articles/IJSRDV1I9071.pdf
[11] http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf
[12] http://www.jatit.org/volumes/Vol53No2/6Vol53No2.pdf](https://image.slidesharecdn.com/aesreport-160405122804/85/Advanced-Encryption-Standard-AES-26-320.jpg)