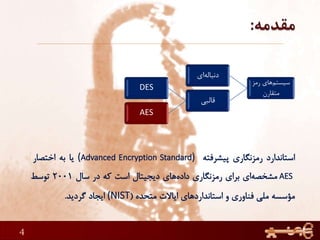
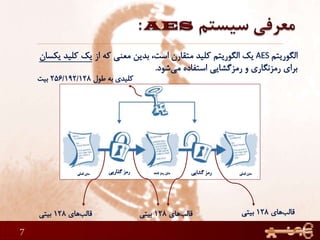
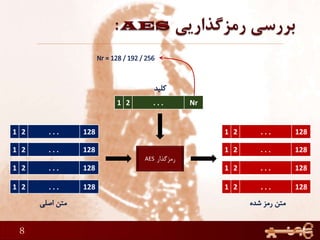
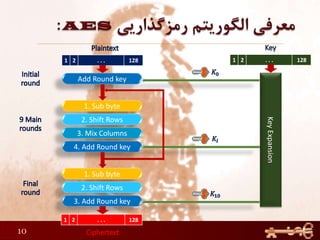
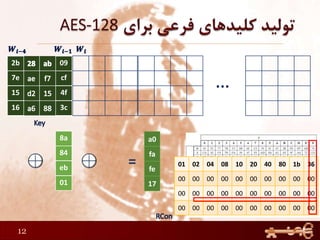
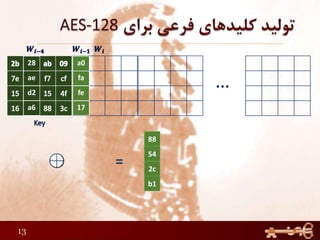
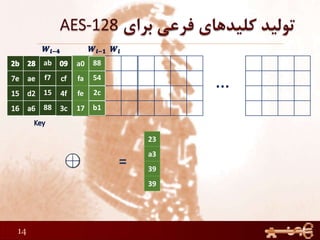
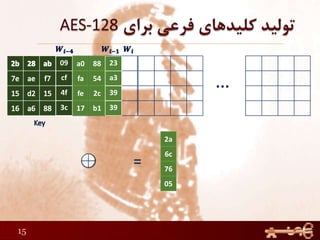
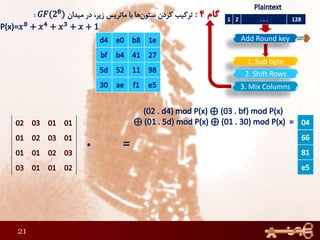
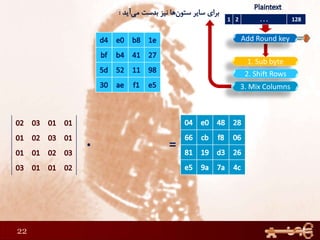
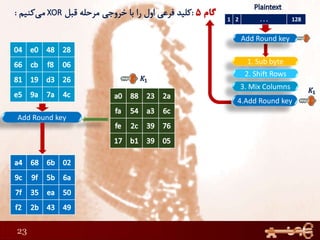
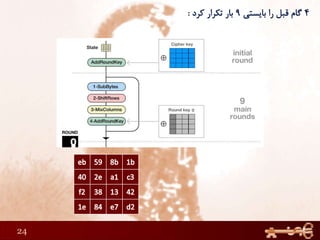
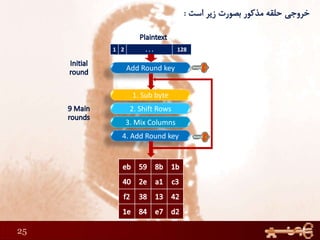
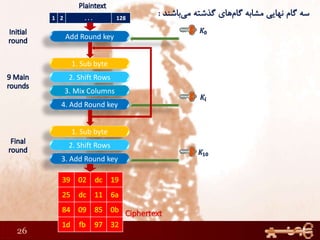
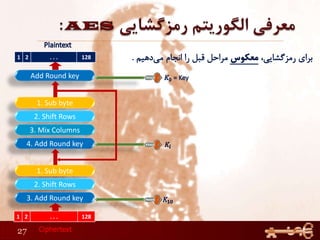
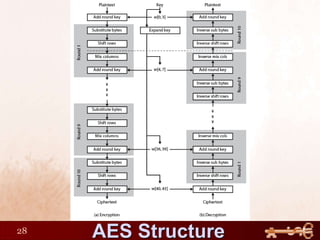
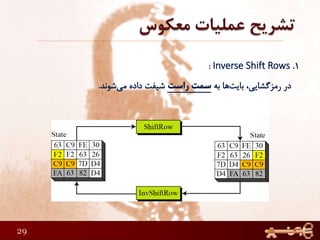
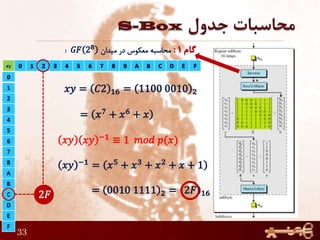
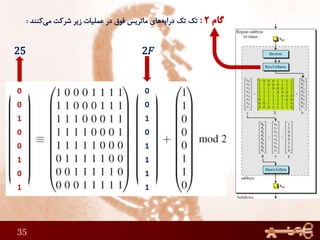
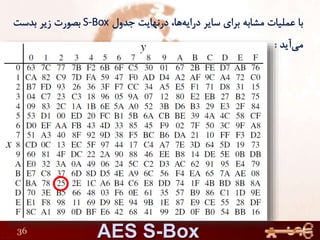
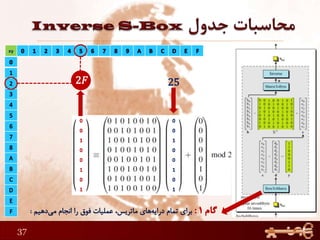
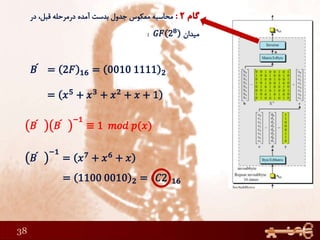
This document discusses AES (Advanced Encryption Standard), a symmetric encryption algorithm. It explains the AES encryption process which involves:
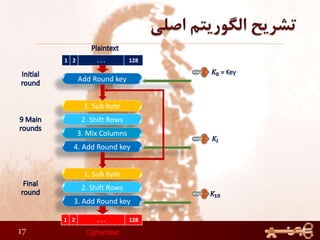
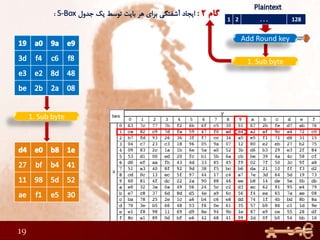
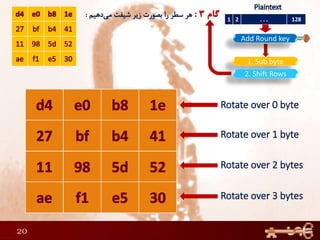
1) Performing rounds of substitution, shifting rows, mixing columns and adding a round key on the plaintext
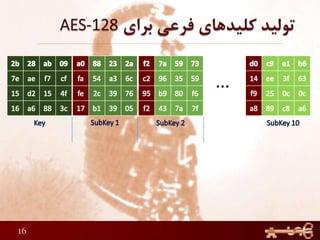
2) The number of rounds depends on the key size (10 rounds for 128-bit keys)
3) The round keys are derived from the original key through an expansion process