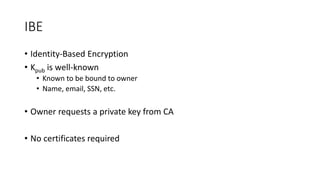
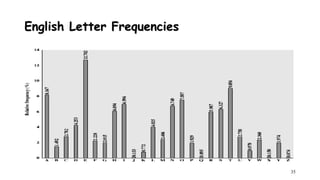
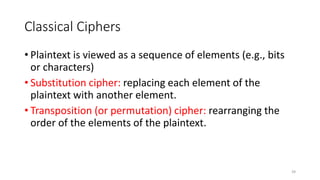
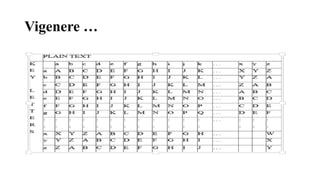
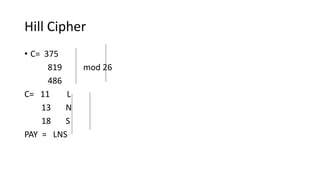
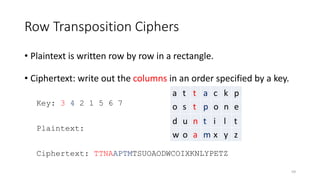
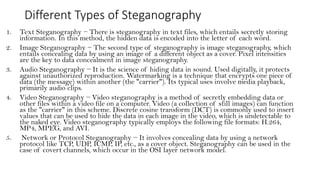
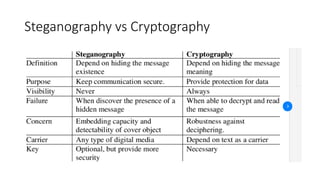
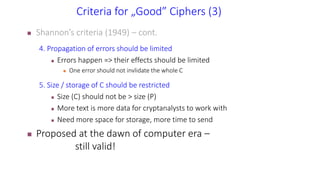
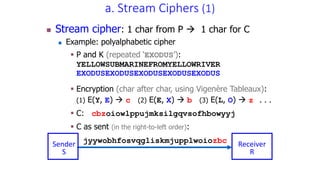
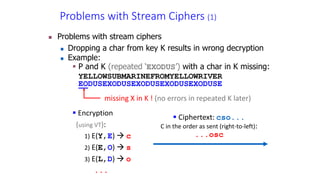
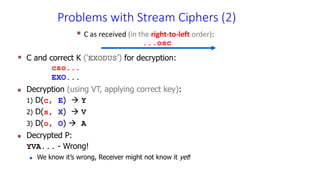
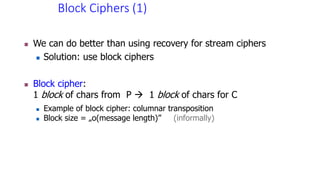
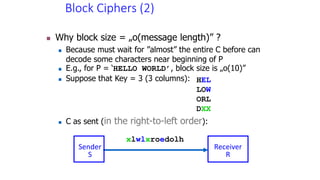
The document discusses classical encryption techniques such as the Caesar cipher, monoalphabetic substitution cipher, and Playfair cipher. The Caesar cipher replaces each letter with the letter three positions down the alphabet. The monoalphabetic substitution cipher randomly maps each plaintext letter to a ciphertext letter. The Playfair cipher encrypts pairs of letters based on their positions in a 5x5 grid generated from the key. Cryptanalysis techniques like frequency analysis that exploit patterns in letter frequencies are also covered.


















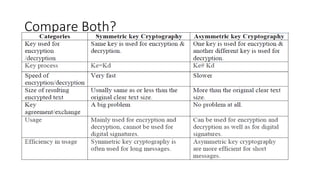





























































![Comparison of DES & AES (1)
DES AES
Date 1976 1999
Block size [bits] 64 128
Key length [bits] 56 (effect.) 128, 192, 256, or more
Encryption substitution, substitution, shift, bit
Primitives permutation mixing
Cryptographic confusion, confusion,
Primitives diffusion diffusion
Design open open
Design closed open
Rationale
Selection secret secret, but accepted
process public comments
Source IBM, enhan- independent Dutch
ced by NSA cryptographers](https://image.slidesharecdn.com/chapter1-4-231106124731-9f23691e/85/chapter-1-4-pdf-105-320.jpg)