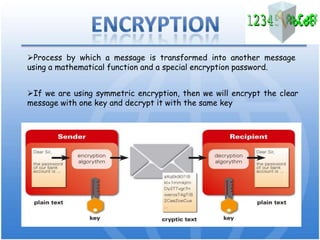
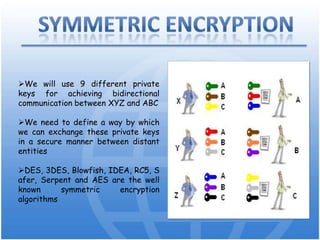
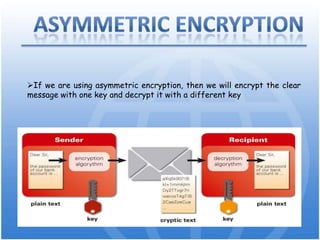
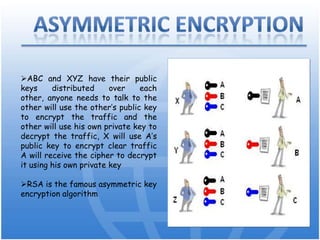
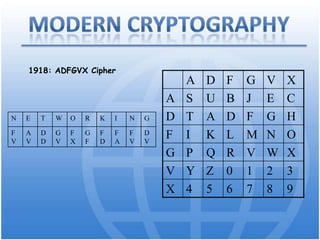
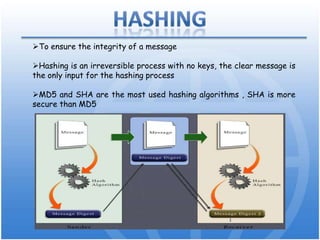
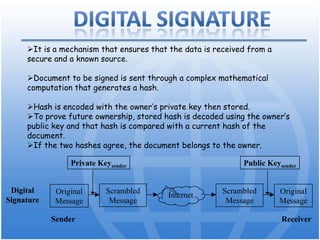
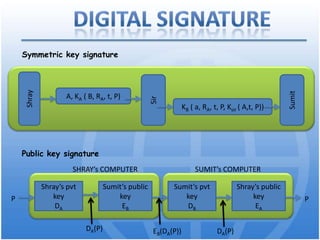
Cryptography is the science of secure communication. It uses techniques like encryption to provide confidentiality, integrity, and authentication of information. The main goals of cryptography are to ensure that information is hidden from unauthorized parties and to verify the identity of senders and the authenticity of messages. Modern cryptography uses both symmetric and asymmetric algorithms, with public key cryptography being widely used to securely exchange keys and for functions like digital signatures. Common cryptographic techniques include encryption, hashing, digital signatures, and digital certificates. Cryptography has many applications including e-commerce, network security, and communication security.