The document discusses various topics related to public key cryptography including:
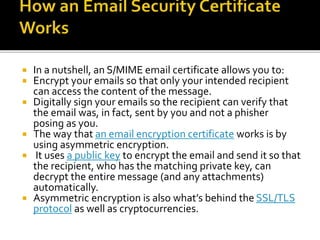
1) Public key cryptography uses key pairs (public/private keys) to encrypt and decrypt messages securely. Private keys are kept secret while public keys can be openly distributed.
2) RSA is a commonly used public key cryptosystem that uses large prime numbers to encrypt data. It is considered secure if a large enough key is used.
3) Digital signatures authenticate messages by encrypting a hash of the message with the sender's private key, allowing verification with their public key.