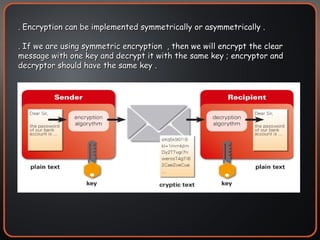
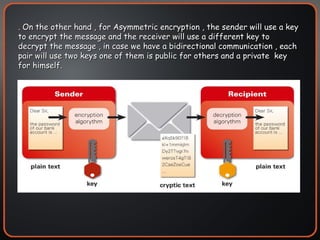
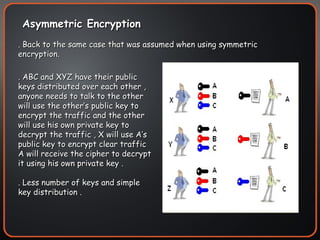
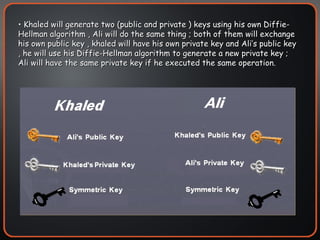
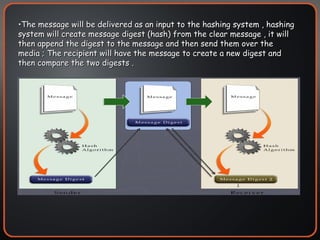
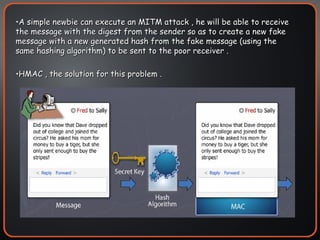
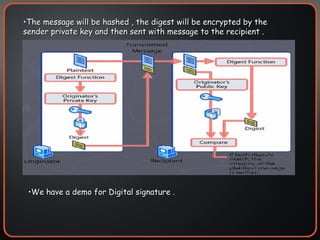
The document provides an overview of cryptography concepts including encryption, hashing, digital signatures, authentication protocols, public key infrastructure (PKI), cryptosystems, and cryptanalysis. Symmetric encryption uses the same key to encrypt and decrypt, while asymmetric encryption uses different public/private keys. Hashing ensures integrity by generating a message digest. Digital signatures combine hashing and encryption to provide authenticity. PKI establishes trust to authenticate users. Cryptosystems implement the cryptographic framework using algorithms, protocols, and keys. Cryptanalysis aims to break ciphers through weaknesses rather than brute force attacks.