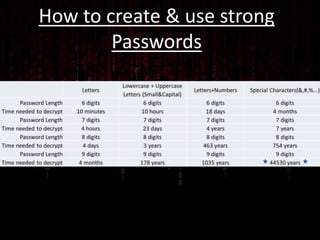
This document discusses the science of encryption through three main topics: the purpose and history of cryptography, modern cryptography techniques, and password security. It describes cryptography as the science of secure communications and its goals of authentication, privacy, integrity, and non-repudiation. The history of cryptography is divided into ancient uses and electro-mechanical machines of World War II. Modern techniques discussed are secret key cryptography, hash functions, and public key cryptography. It emphasizes the importance of strong, unique passwords for security.