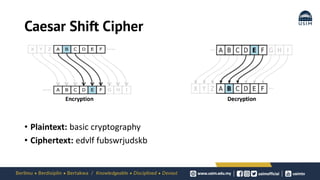
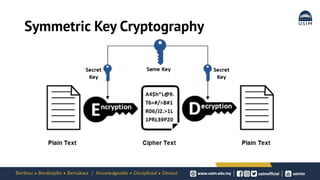
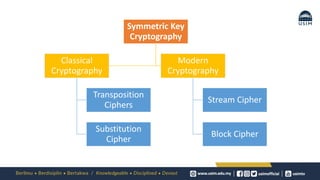
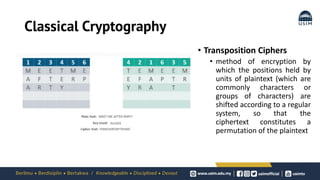
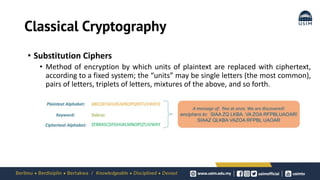
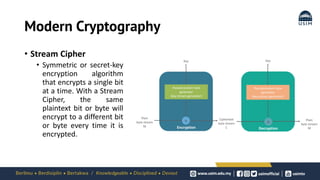
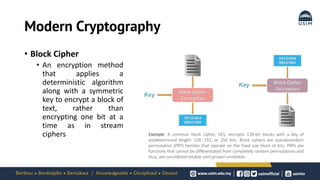
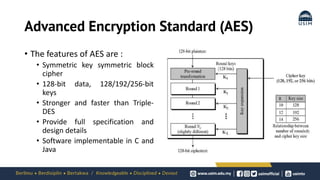
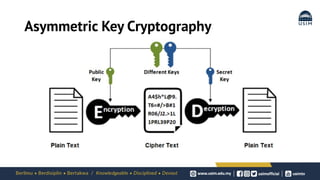
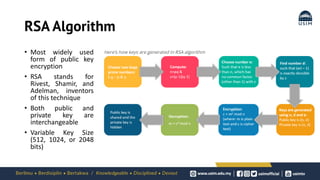
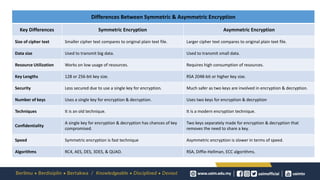
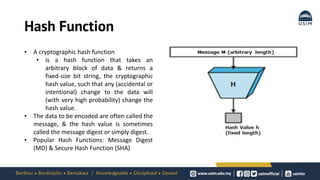
Cryptography is the study of secure communication techniques. The document provides a high-level overview of basic cryptography concepts including its history, objectives, terminology, and types (symmetric, asymmetric, hash functions). Symmetric cryptography uses a single secret key for encryption and decryption while asymmetric cryptography uses two keys: a public key for encryption and a private key for decryption. Popular symmetric algorithms include AES and RSA. Hash functions like MD5 and SHA are used to verify message integrity. Quantum computing may improve applications like cancer treatment, traffic optimization, and weather forecasting by solving complex optimization problems.