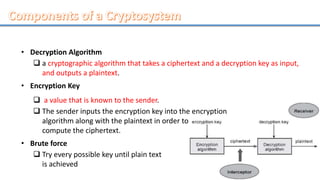
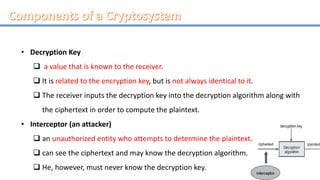
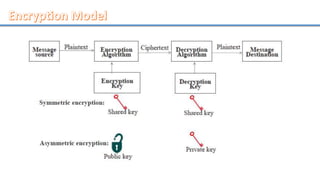
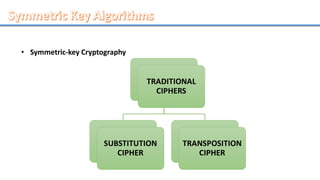
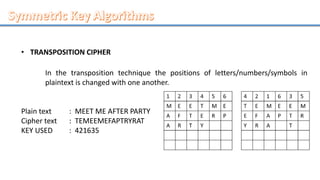
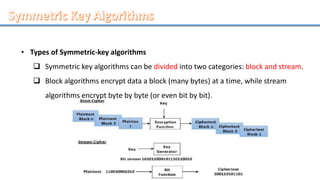
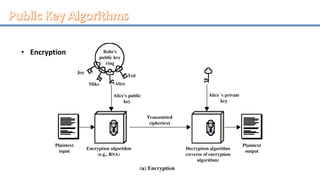
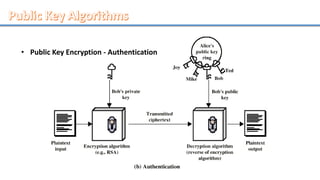
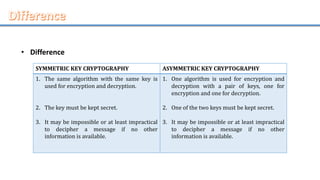
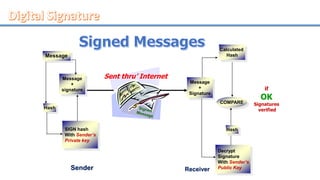
Network security involves securing computer networks and systems. It is handled by network administrators who implement security policies, software, and hardware to protect networks from unauthorized access, misuse, or denial of resources. Network security aims to authenticate users, control access to resources, and ensure confidentiality, integrity, non-repudiation and availability of networks and resources. Common methods include authentication, access control, encryption, digital signatures, and monitoring systems for security audits.