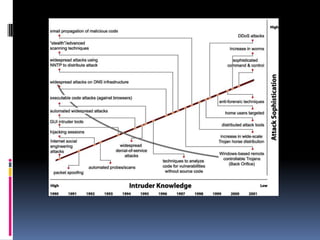
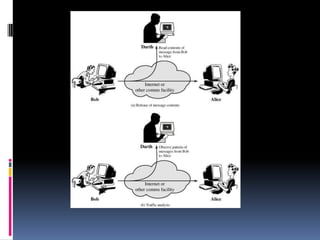
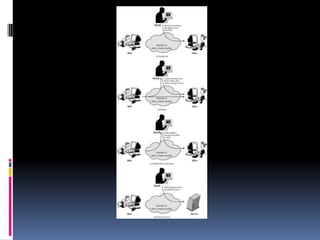
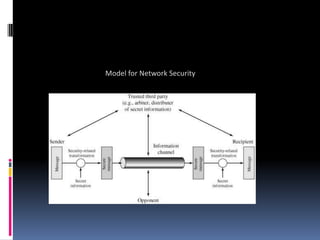
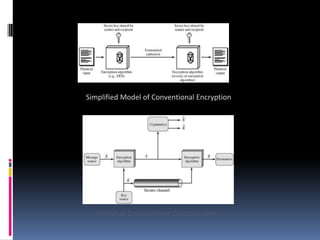
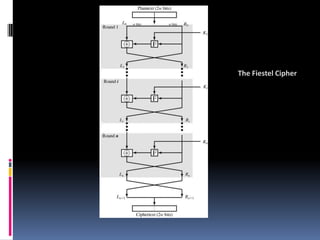
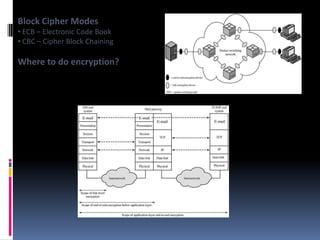
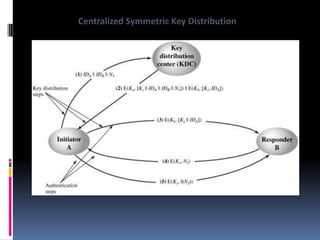
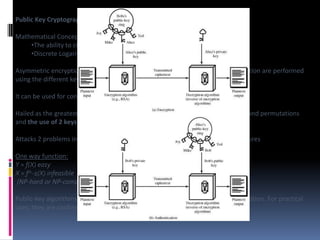
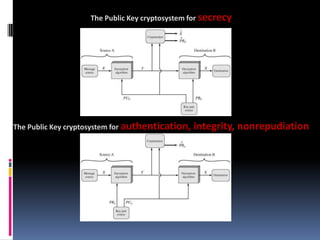
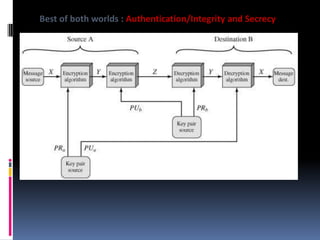
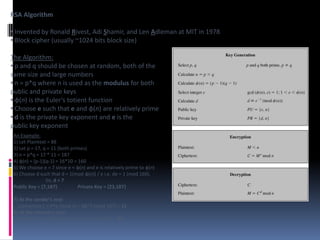
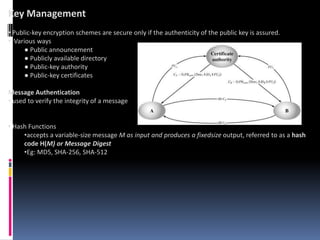
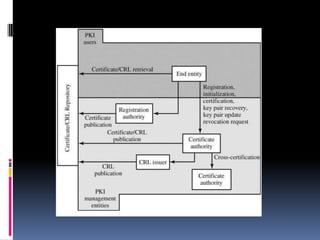
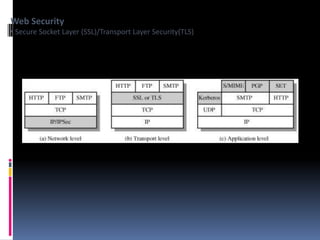
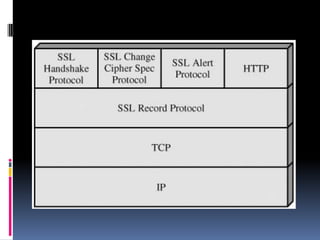
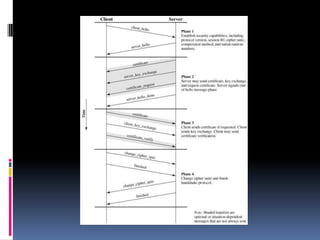
The document provides an overview of cryptography and network security, covering topics including symmetric and asymmetric cryptography, key management, hashing algorithms, and digital signatures. It discusses various encryption algorithms such as DES, AES, RSA, and the principles of secure communications and authentication protocols. Key security trends and challenges, including key distribution and digital signatures, as well as real-world applications like SSL/TLS and PKI are also addressed.