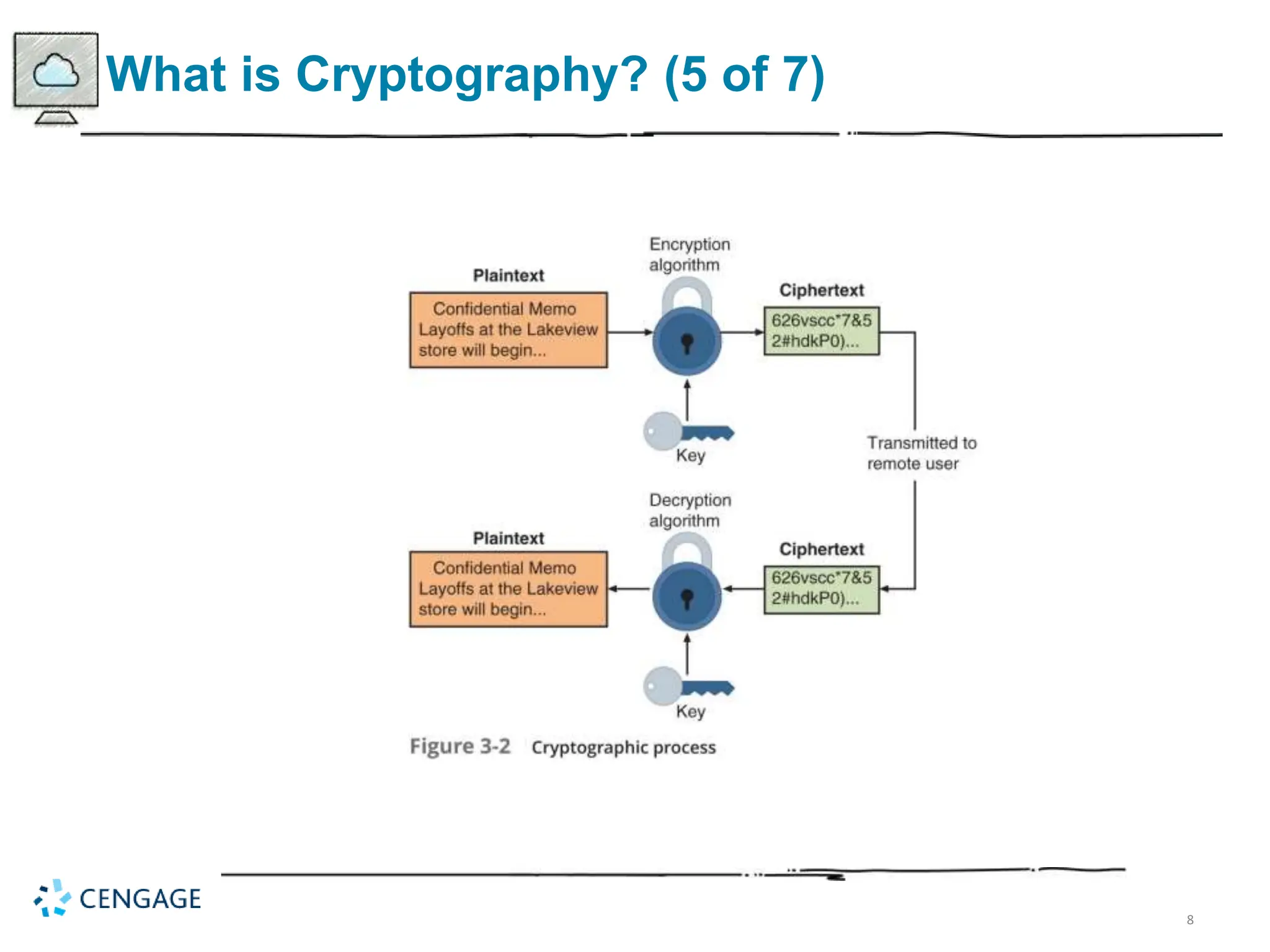
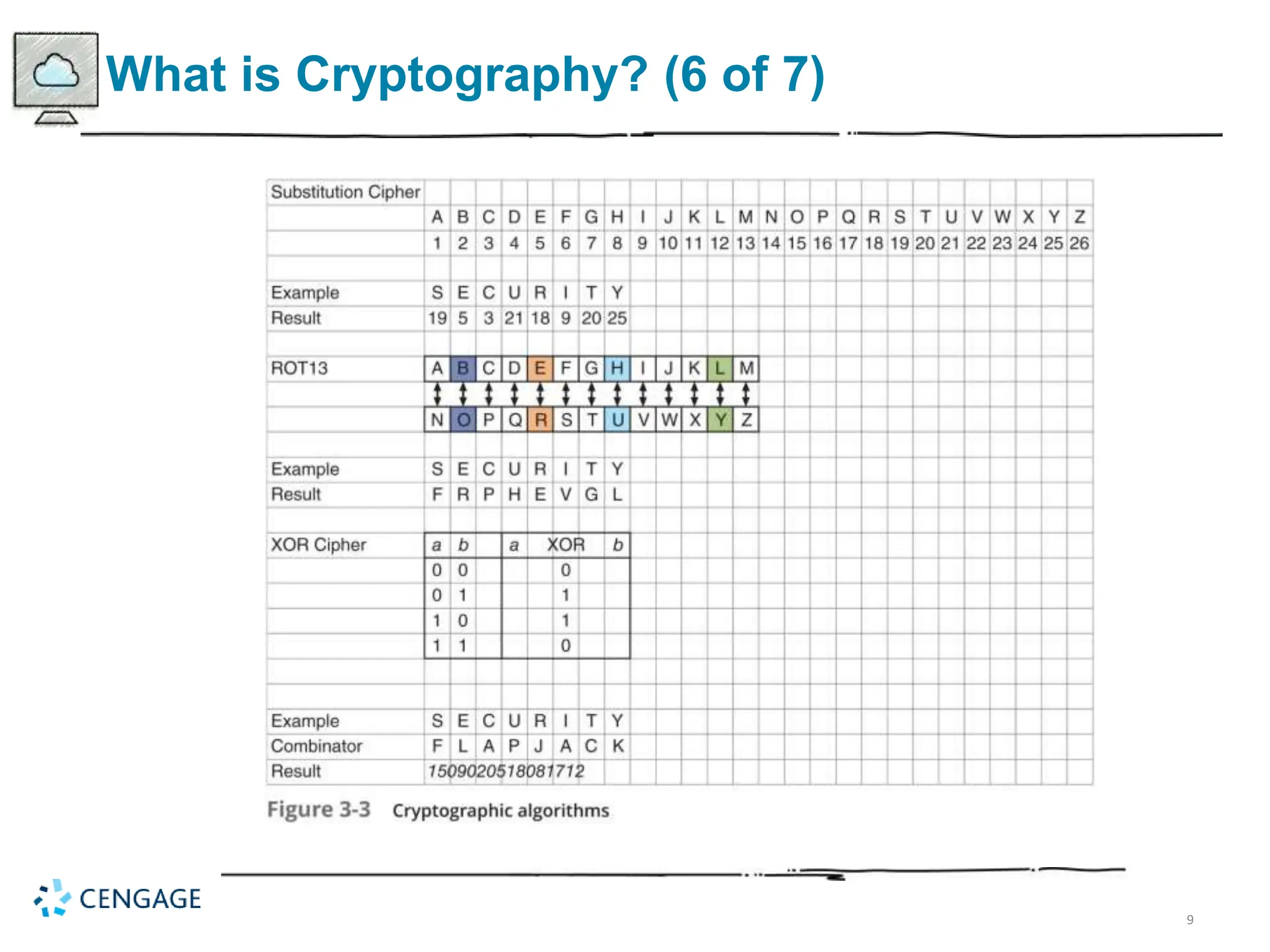
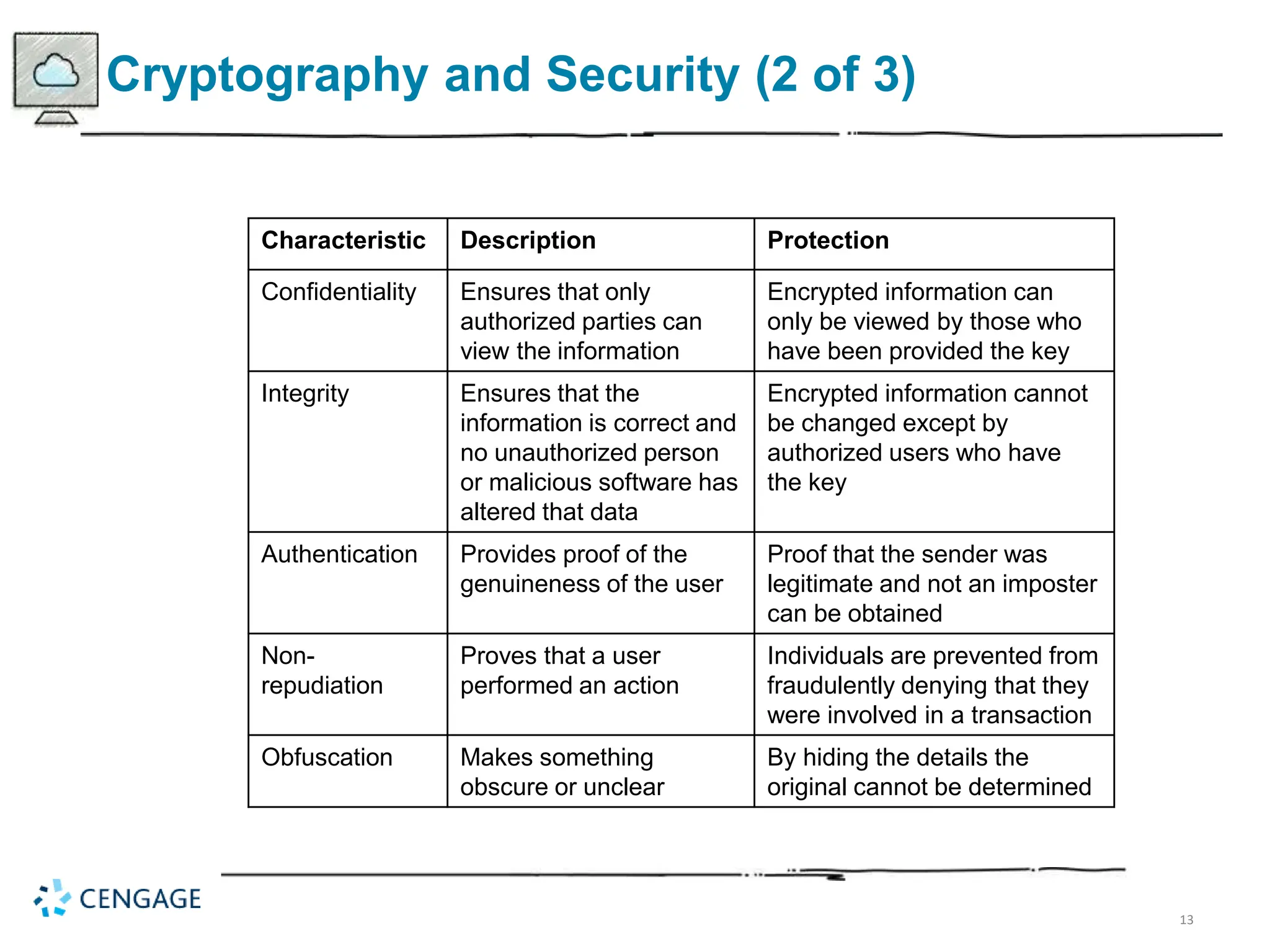
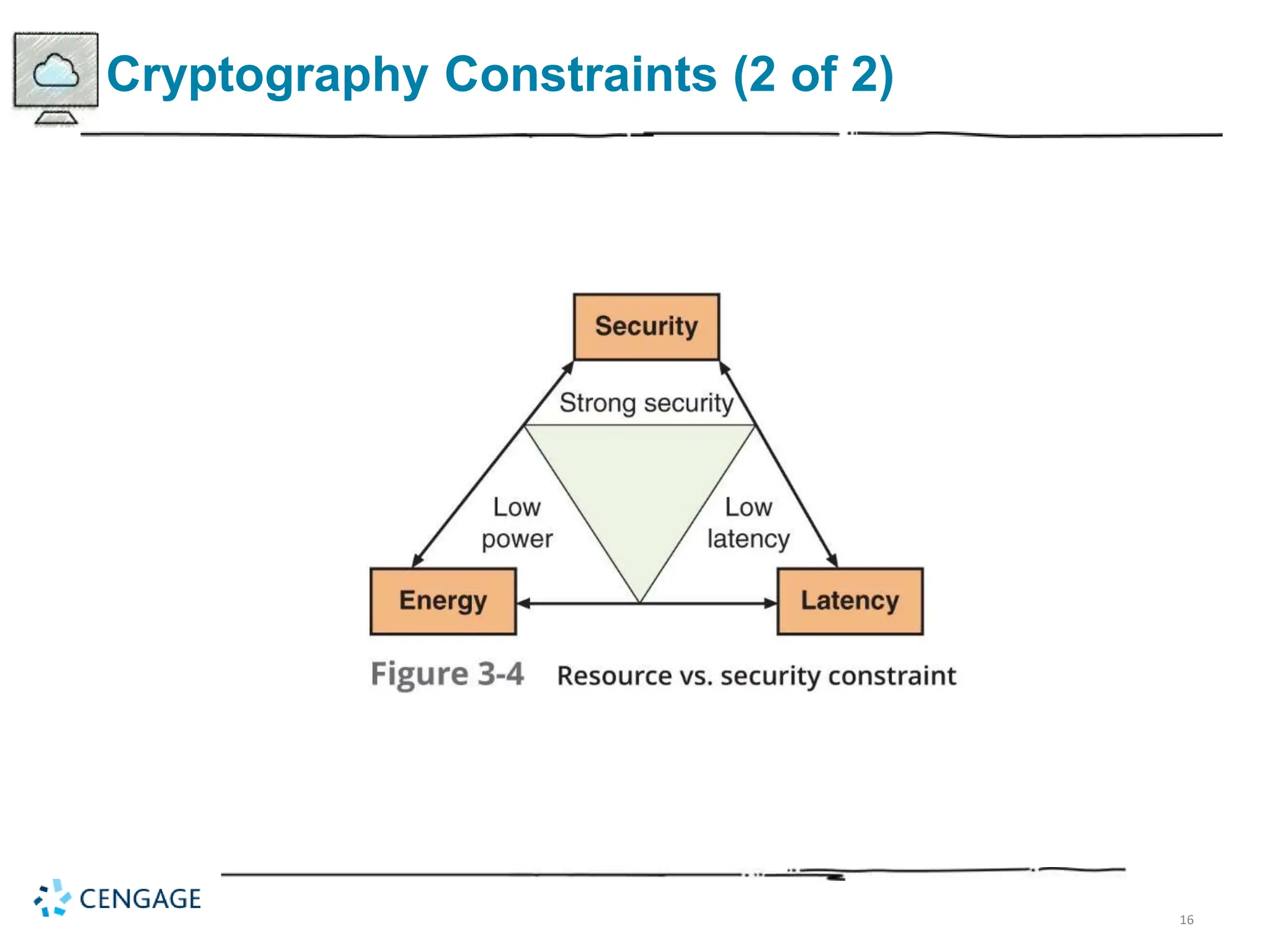
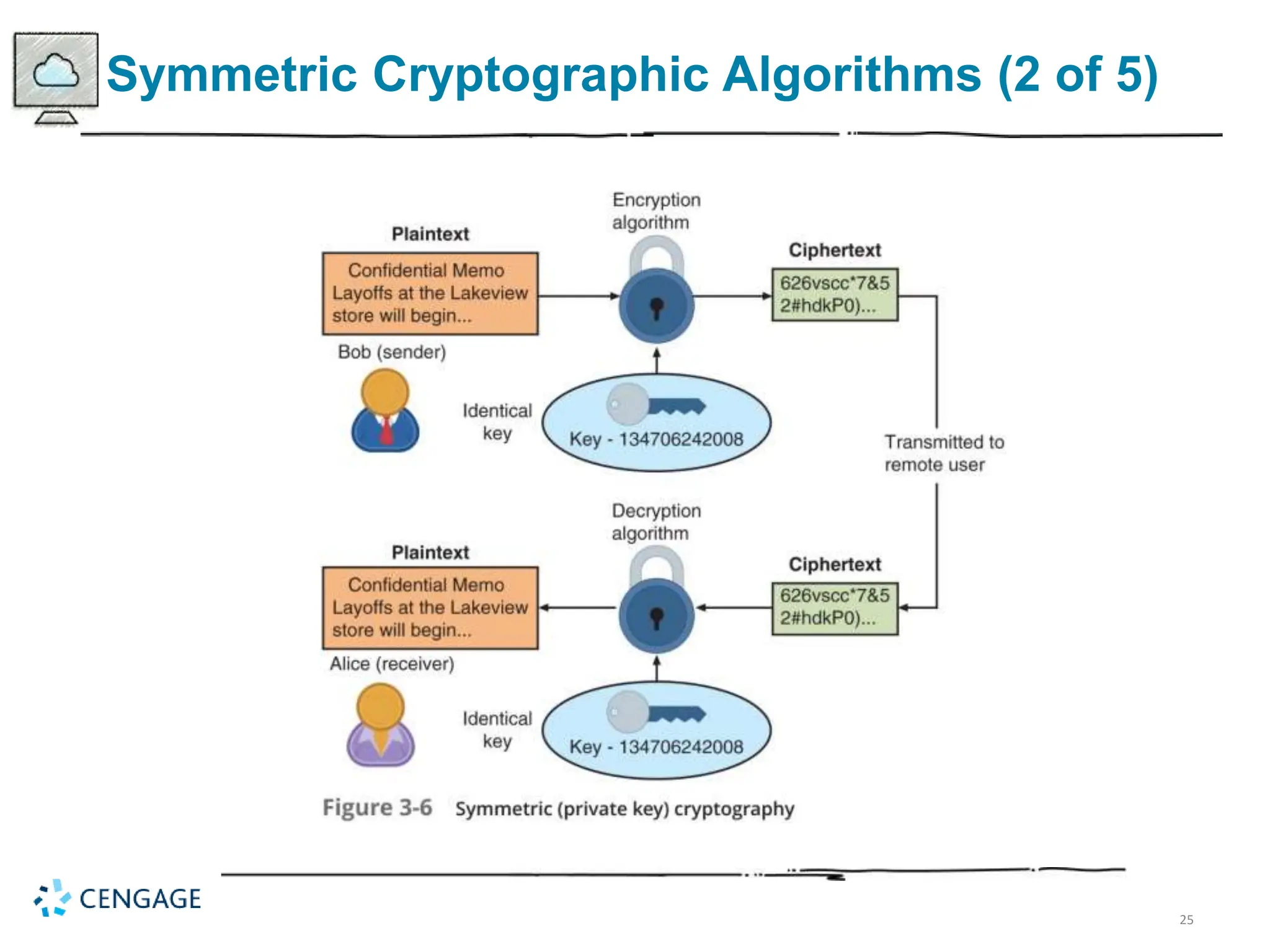
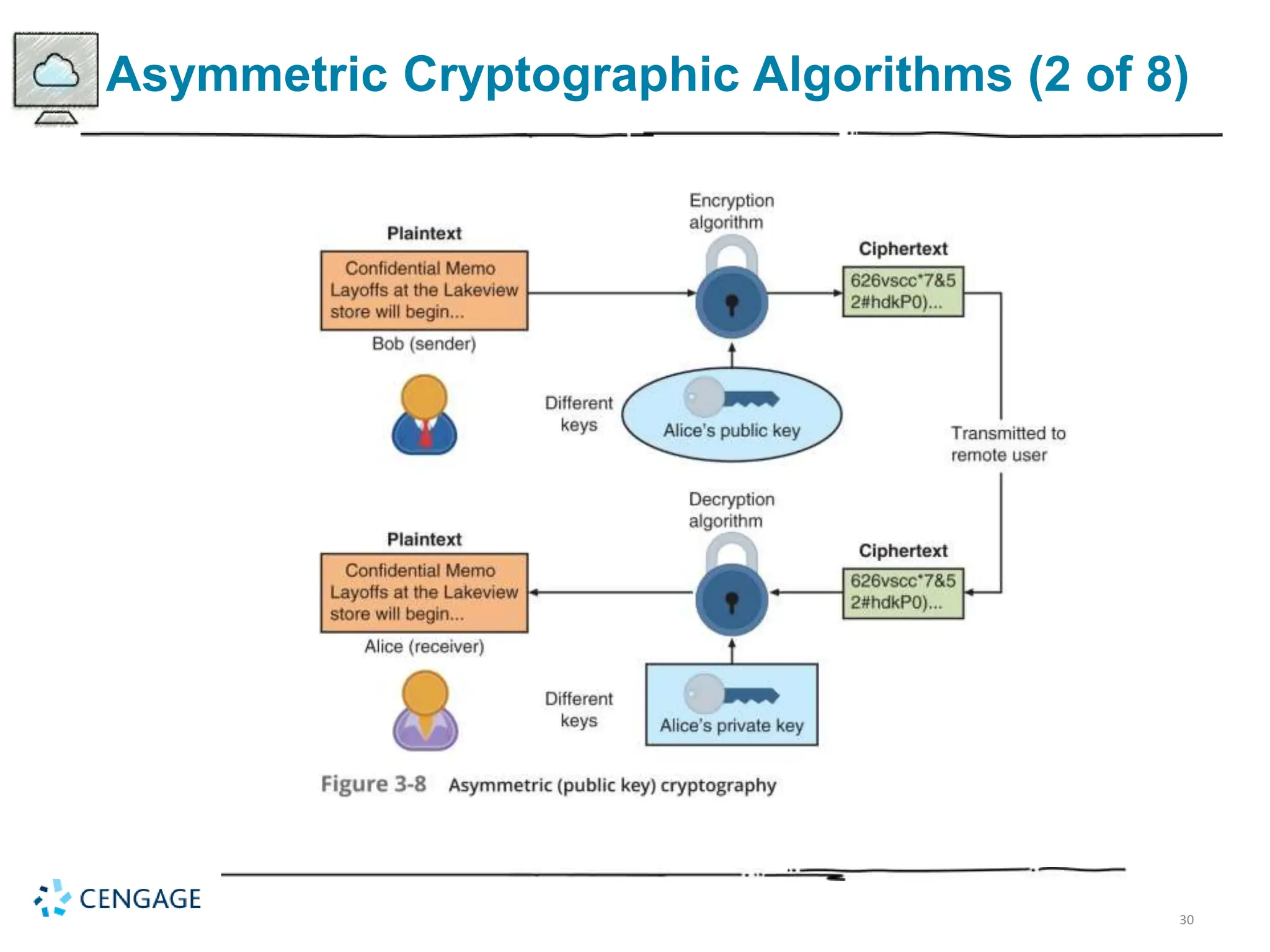
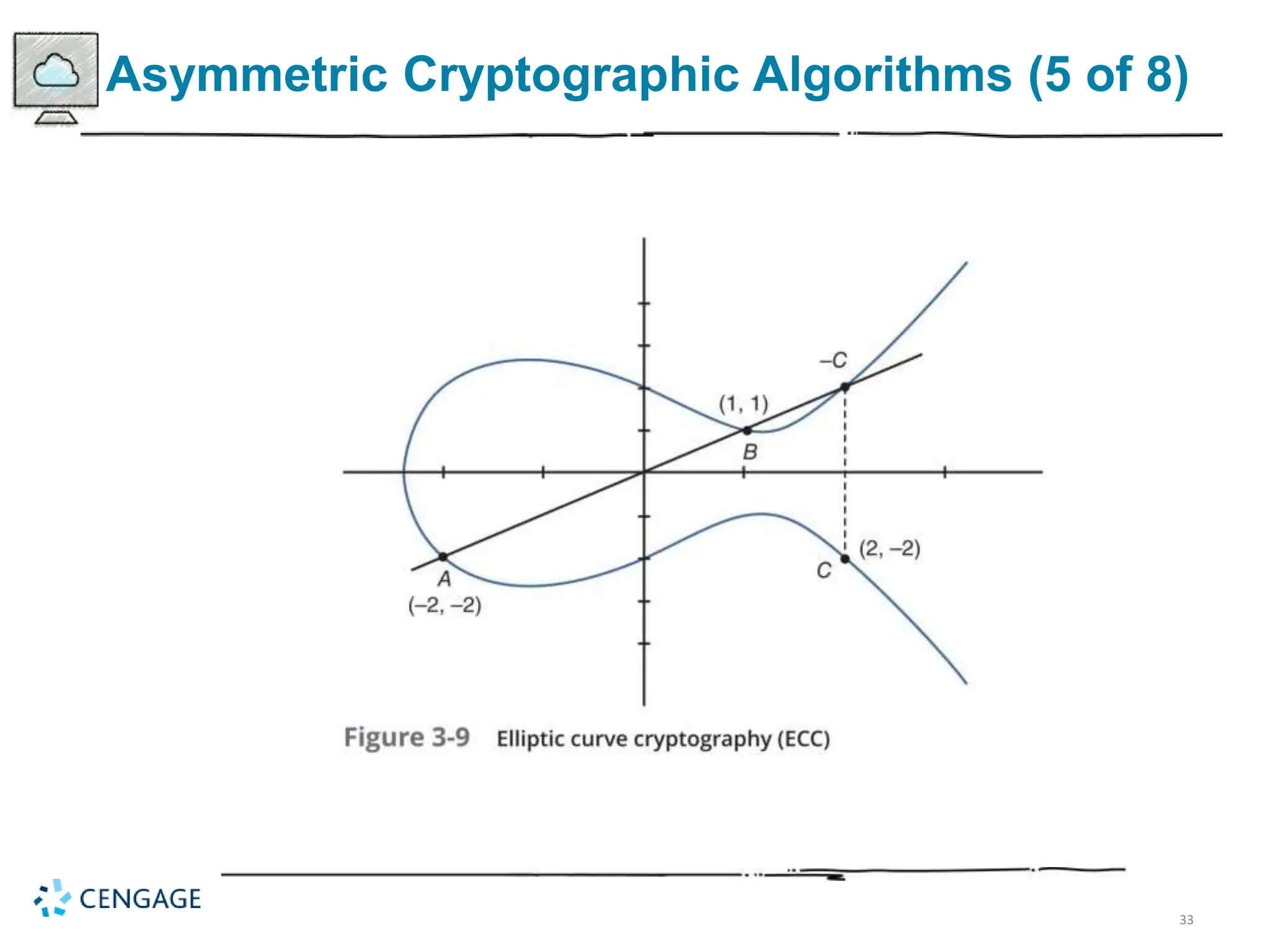
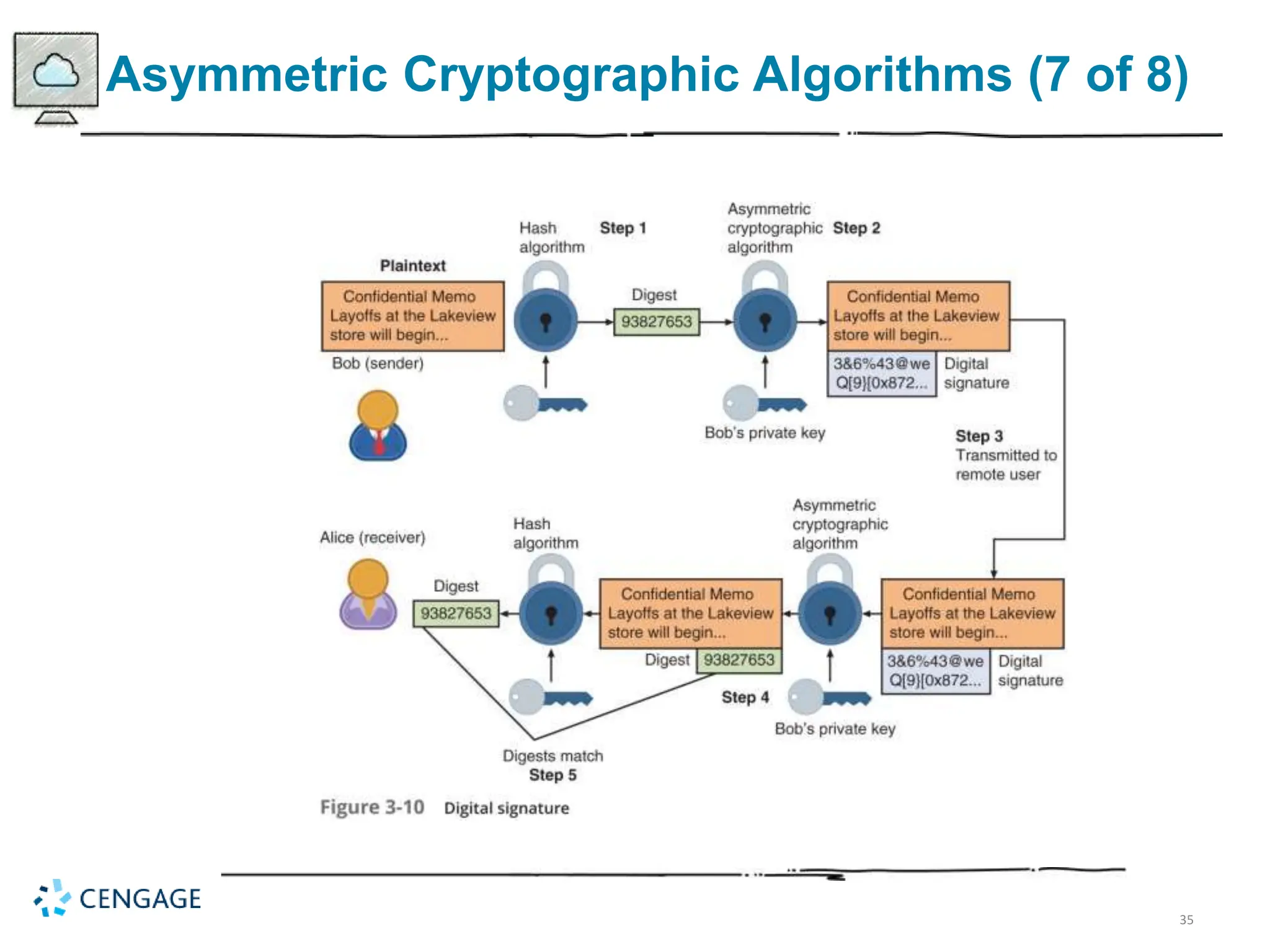
The document provides a comprehensive overview of cryptography, defining key concepts and methods including hash, symmetric, and asymmetric algorithms. It discusses the importance of cryptography for security, emphasizing its roles in confidentiality, integrity, authentication, and more, as well as its application in protecting data in various states. Additionally, it highlights the constraints and various types of cryptographic attacks that exploit weaknesses in these systems.