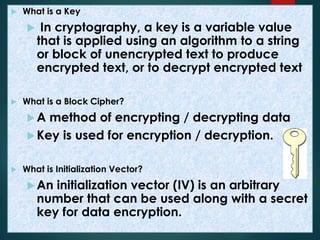
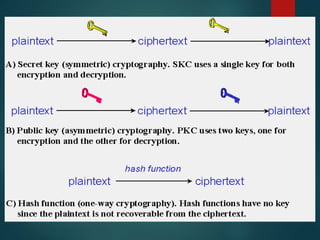
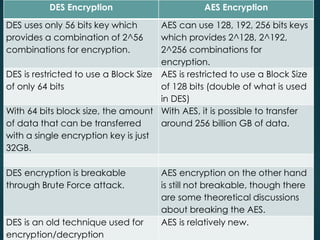
This document provides an overview of cryptography. It discusses that cryptography is the practice of secure communication in the presence of others. The purpose of cryptography is to defend against hackers and industrial espionage while securing e-commerce, bank accounts, intellectual property, and avoiding liability. Cryptography provides authentication, privacy, integrity, and non-repudiation. Encryption converts plain text to cipher text using a key while decryption converts cipher text to plain text. Common cryptographic algorithms are secret key cryptography, public key cryptography, and hash functions. Secret key cryptography uses a private key for encryption while public key cryptography uses a public key exchanged over an insecure channel. Hash functions produce a checksum of data. AES encryption is now commonly used and