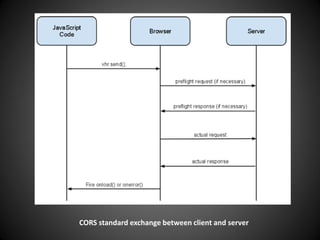
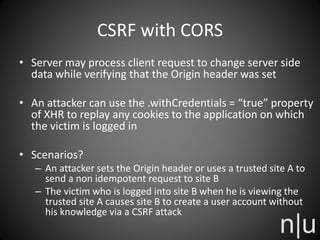
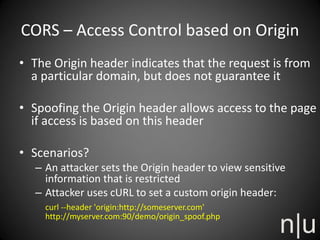
Riyaz Walikar discusses the Same Origin Policy (SOP) and Cross Origin Resource Sharing (CORS). SOP restricts how scripts from one origin can interact with resources from other origins for security. CORS allows relaxing SOP for legitimate cross-origin requests by using special HTTP headers. However, CORS implementations must be careful to avoid security issues like universal permissive policies, misplaced trust, CORS-based CSRF attacks, and caching or origin spoofing vulnerabilities.