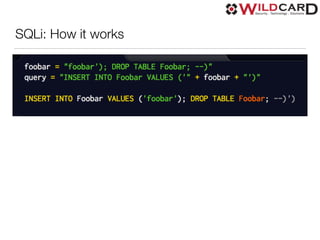
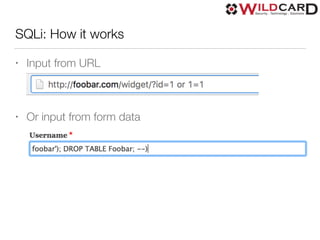
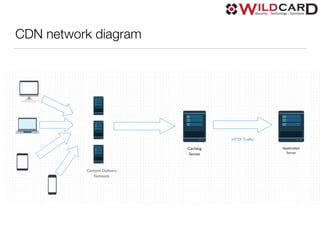
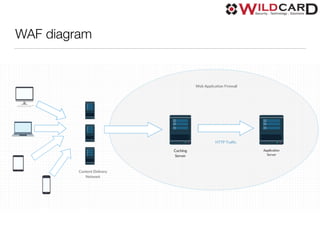
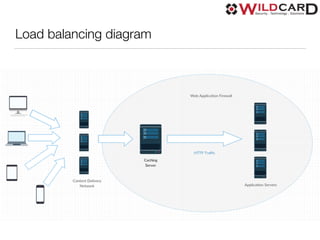
The document is a presentation on common web security issues and vulnerabilities, highlighting the importance of security for website owners and developers. It details the top five security risks, including SQL injection, Denial of Service, Cross-Site Scripting, Cross-Site Request Forgery, and access control, along with prevention solutions for each. Additionally, the document discusses caching, load balancing, database selection, performance, monitoring, and the role of add-ons in maintaining web security.