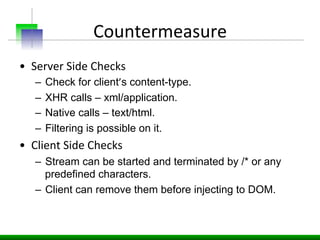
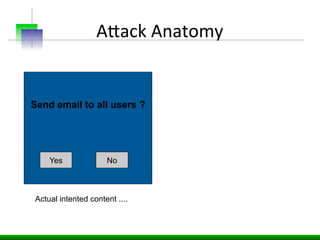
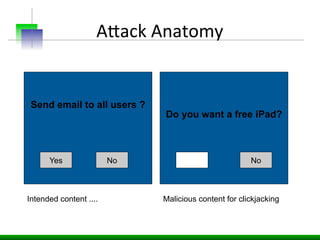
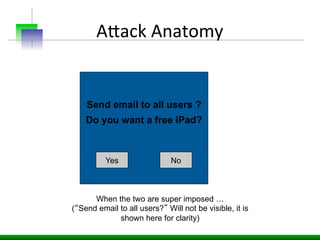
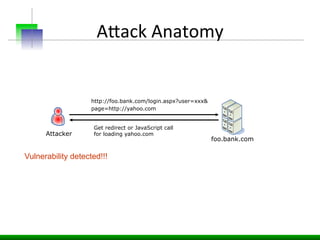
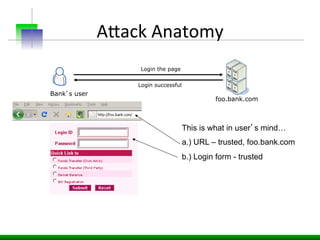
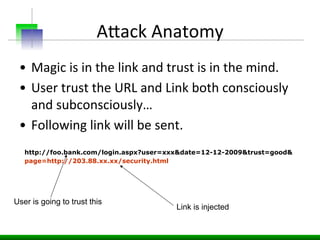
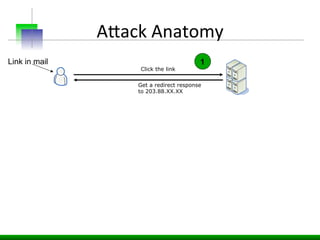
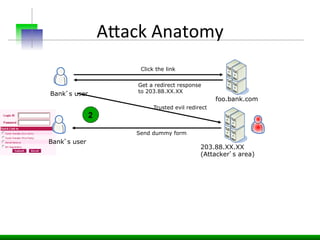
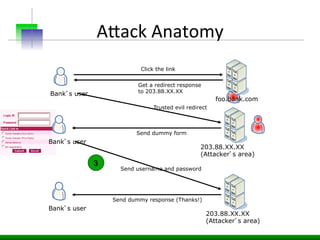
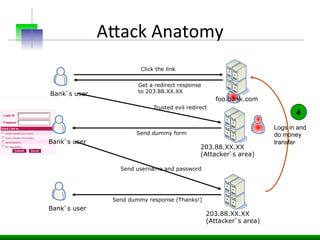
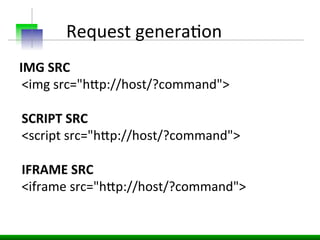
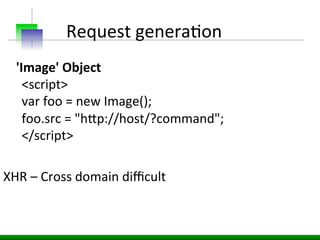
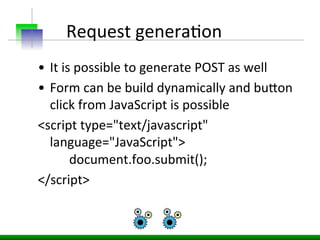
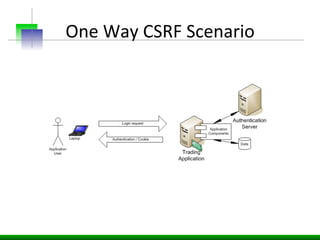
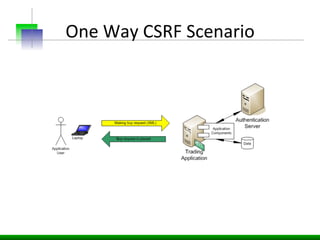
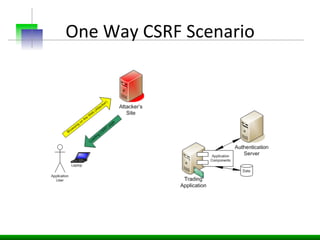
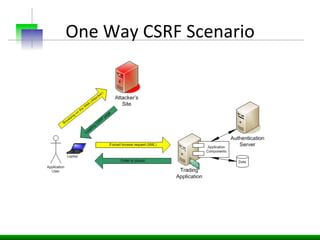
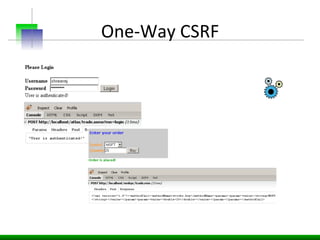
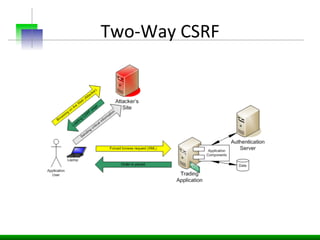
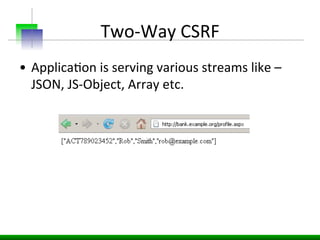
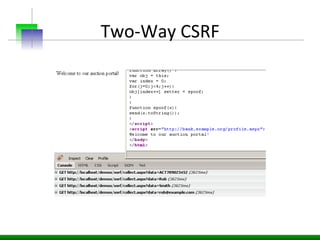
This document discusses various web application security vulnerabilities including Cross Site Request Forgery (CSRF), clickjacking, and open redirects. CSRF involves forcing unauthorized requests to a web application to perform actions on the user's behalf. Clickjacking involves tricking a user into clicking something different than what they see. Open redirects can allow attackers to redirect users to malicious sites.





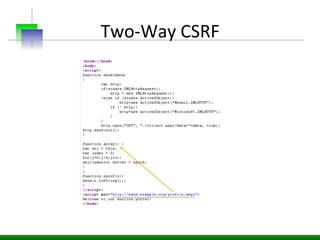
![Two-‐Way
CSRF
• AOacker
page
can
make
cross
domain
request
using
SCRIPT
(firefox)
• Following
code
can
overload
the
array
stream.
funcEon
Array()
{
var
obj
=
this;
var
index
=
0;
for(j=0;j<4;j++){
obj[index++]
seOer
=
spoof;
}
}
funcEon
spoof(x){
send(x.toString());
}](https://image.slidesharecdn.com/csrf-151026090013-lva1-app6891/85/CSRF-ClickJacking-Open-Redirect-18-320.jpg)