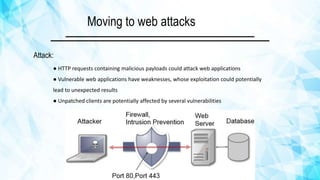
Web security focuses on protecting internet-based applications and browsers from various online threats, including vulnerabilities in web applications and security breaches targeting users. Common attack methods involve exploiting flaws like SQL injection, cross-site scripting, and session hijacking to compromise sensitive data or impersonate users. Effective security relies on multiple layers of defense both on the client and server sides to mitigate these risks.