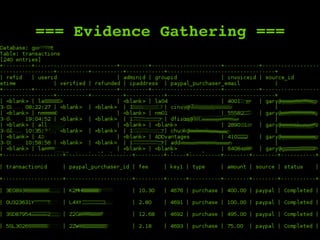
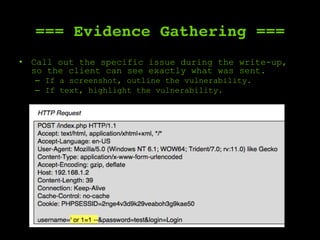
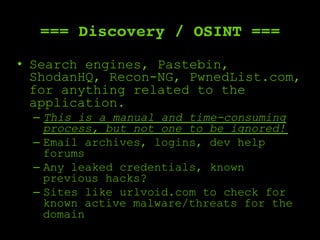
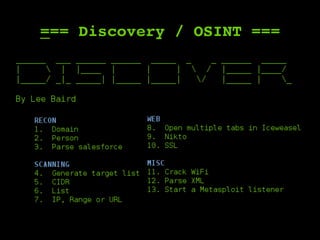
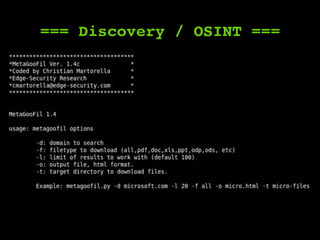
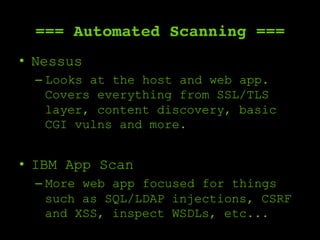
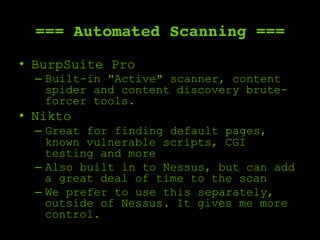
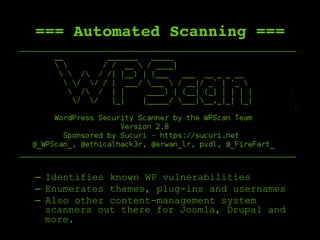
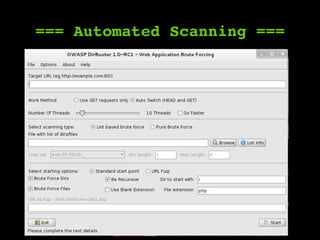
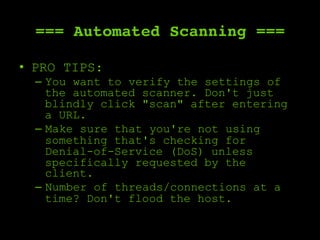
The document outlines a comprehensive framework for conducting security assessments on web applications, emphasizing the importance of evidence gathering, automated scanning, and manual testing. Key recommendations include using tools like KeepNote, Nessus, and Burp Suite, and maintaining a structured methodology to ensure thoroughness. It stresses the need for practical experience and learning to effectively identify and exploit vulnerabilities.