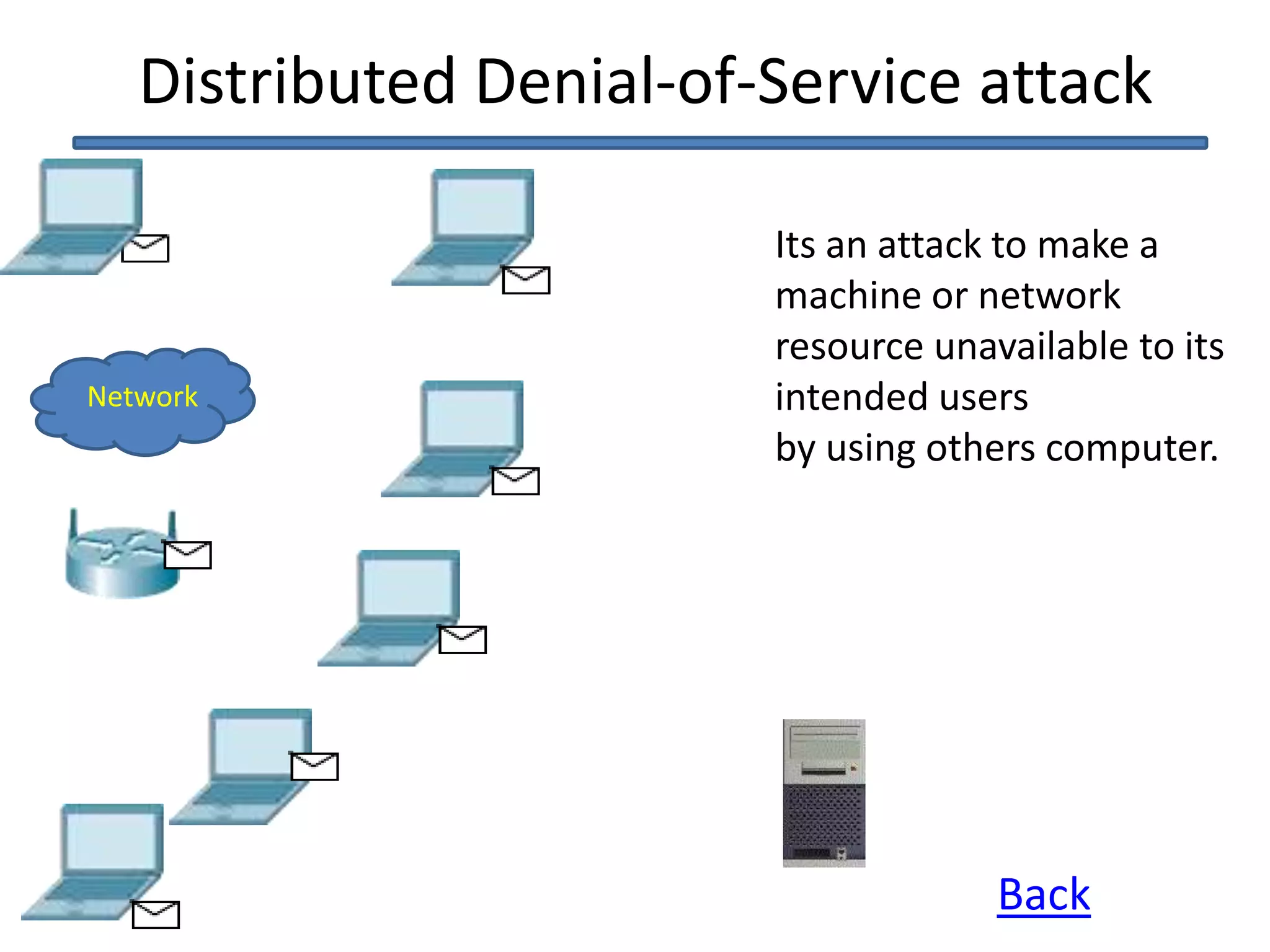
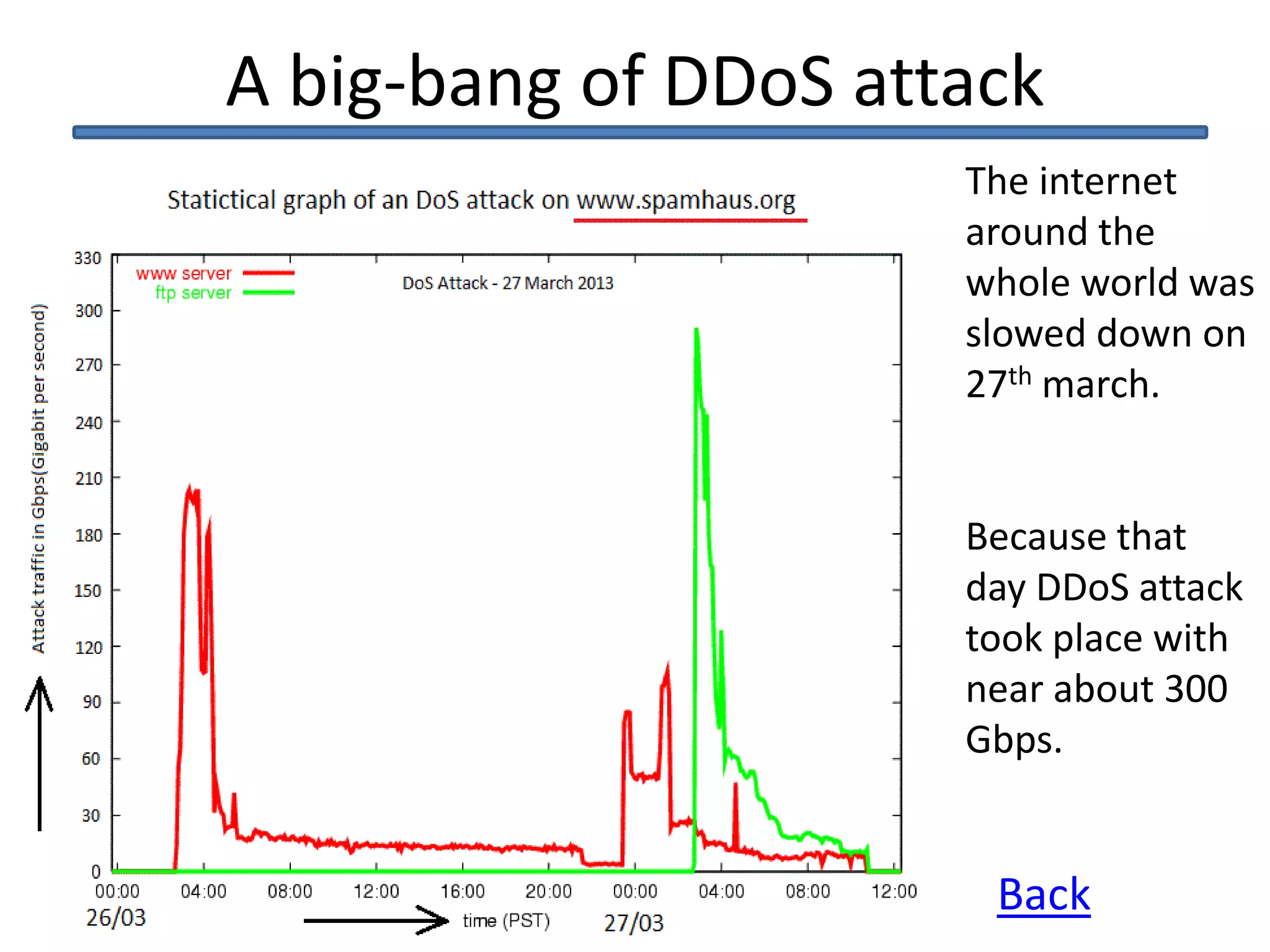
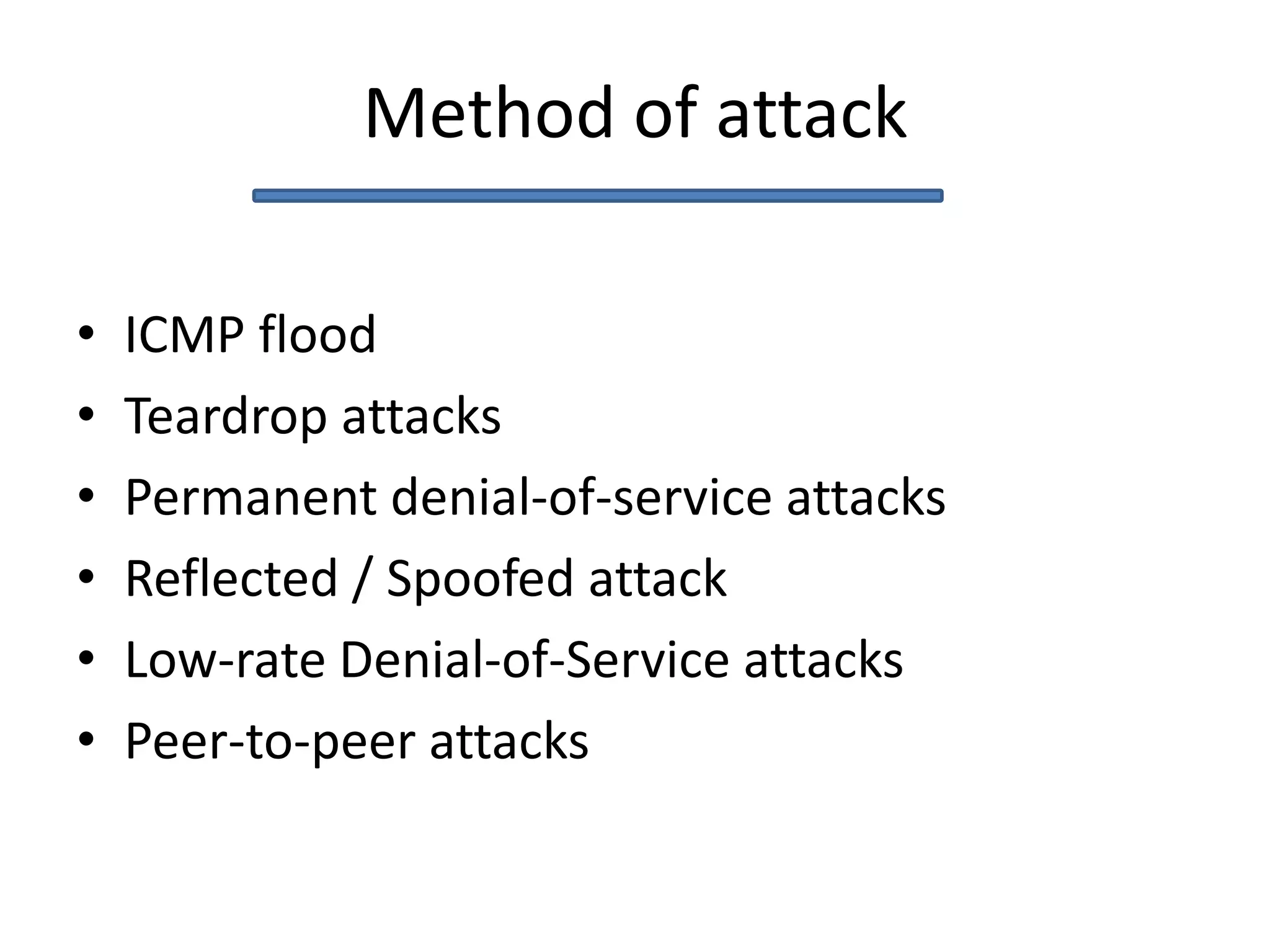
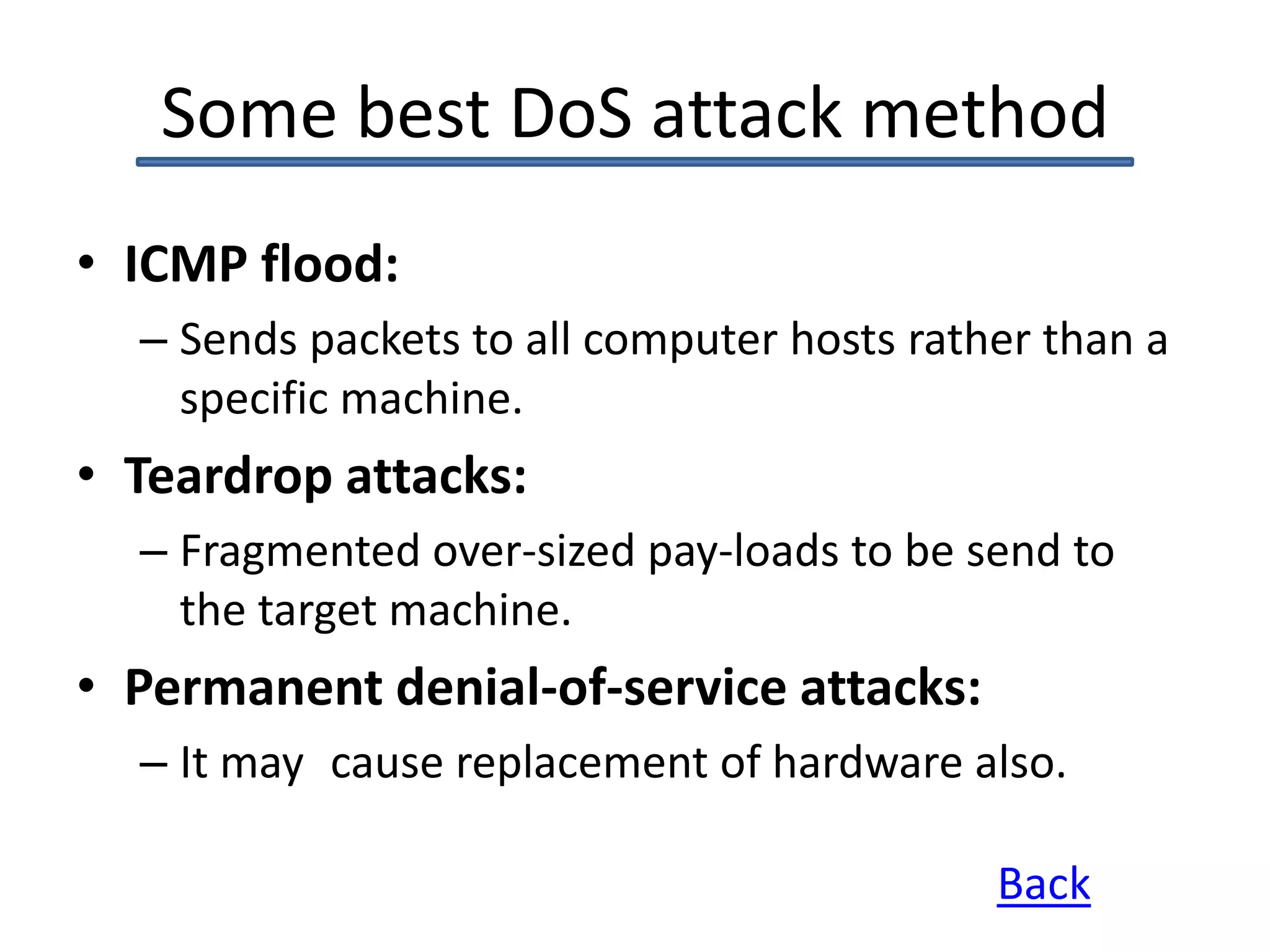
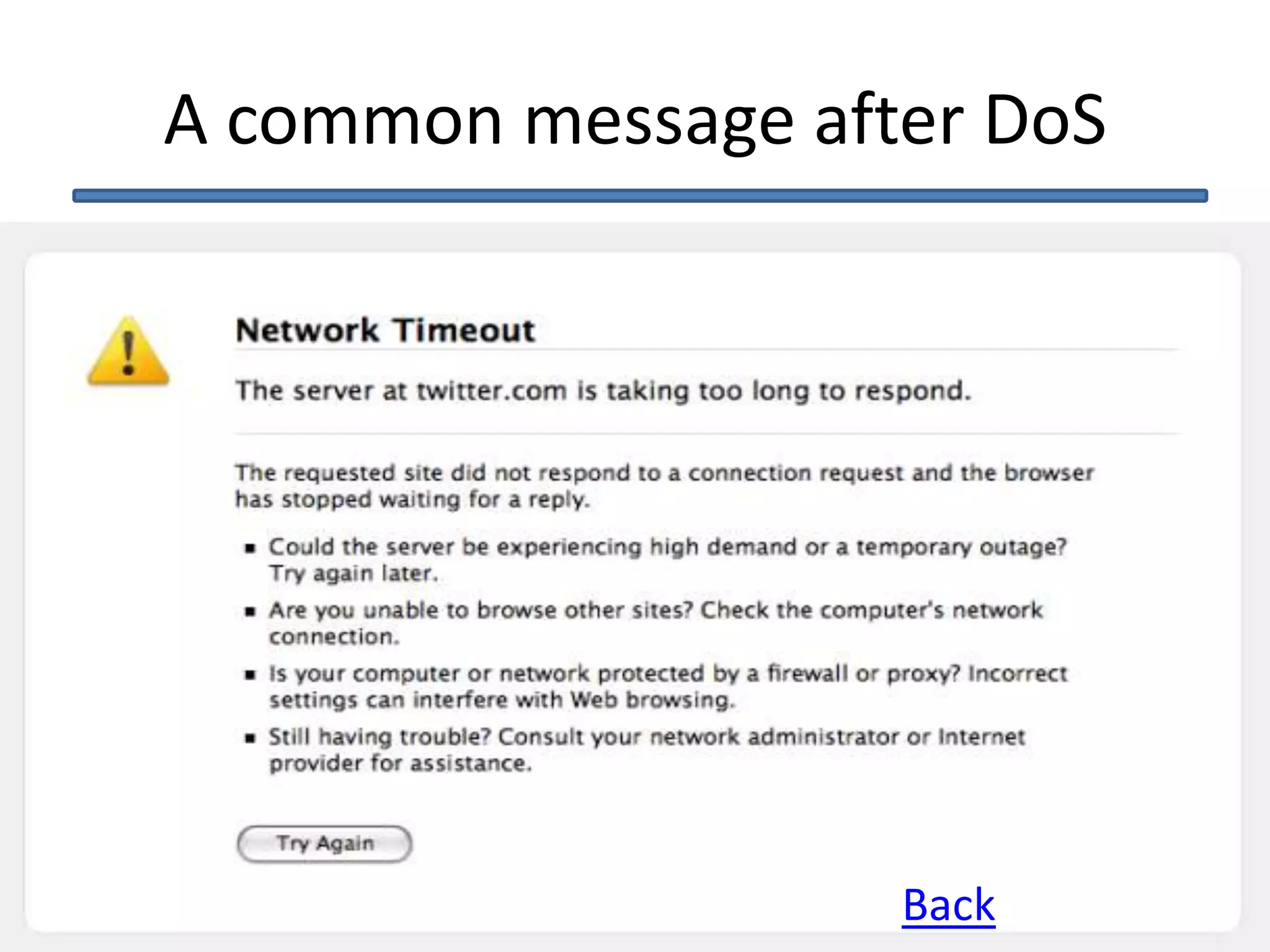
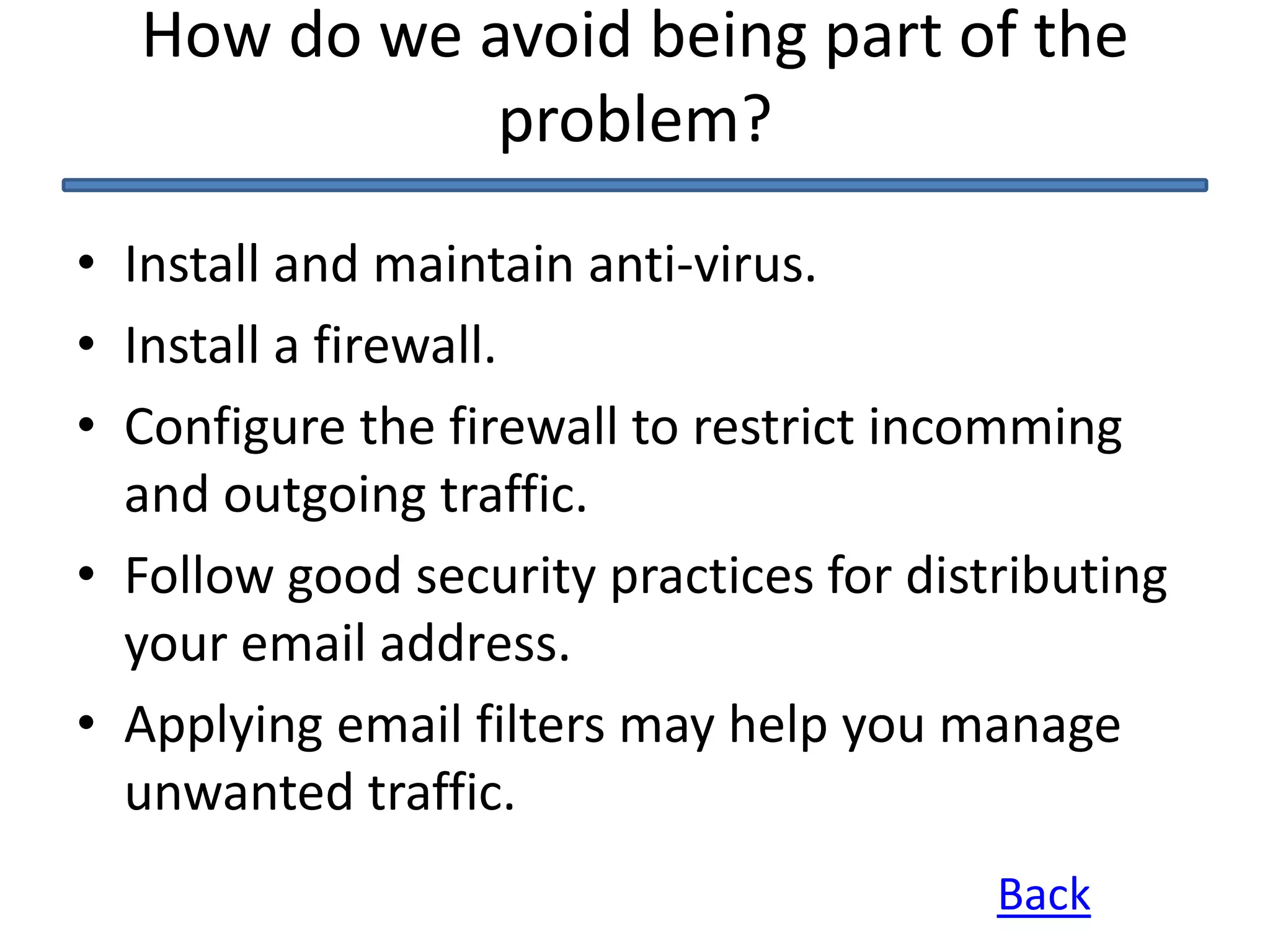
This document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines DoS as making a machine or network unavailable to its intended users. DDoS uses other computers to launch the attack. Methods of attack mentioned include ICMP floods, teardrop attacks, and reflected/spoofed attacks. Signs of an attack include slow network performance. The document provides tips for system administrators and users, such as contacting providers and following security best practices, to mitigate attacks.