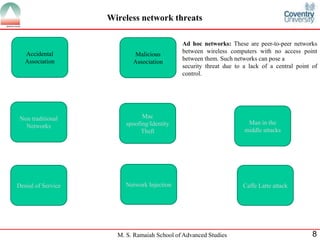
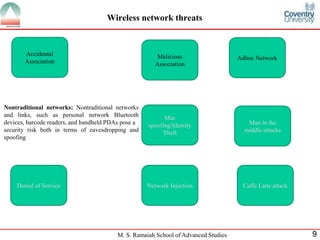
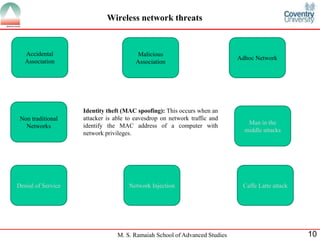
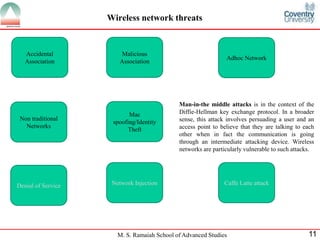
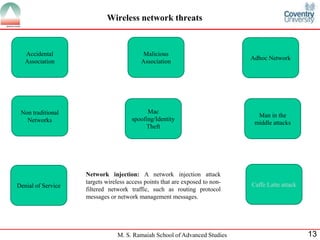
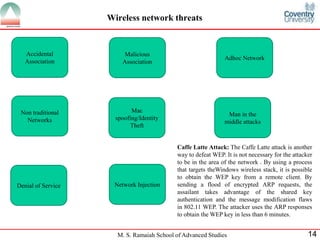
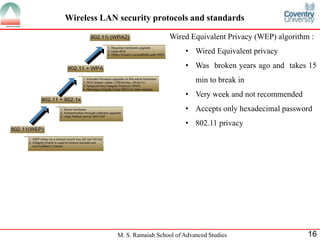
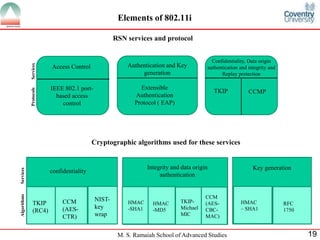
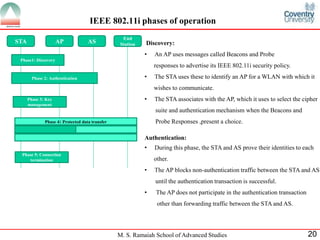
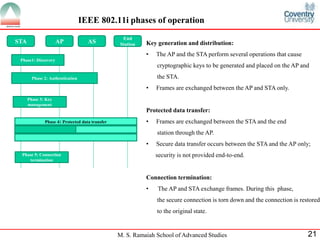
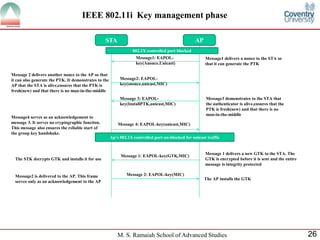
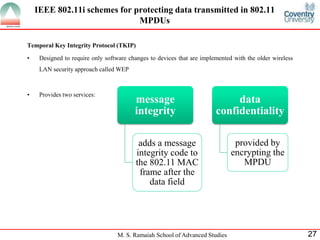
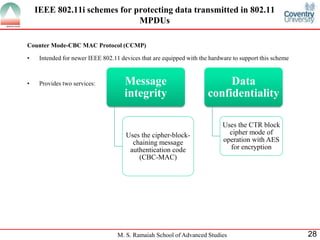
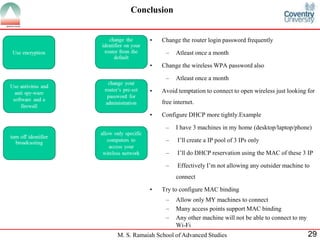
The document presents a detailed overview of wireless networking security, outlining various security threats and the importance of implementing effective wireless security policies. It discusses protocols such as WPA2 (802.11i), focusing on authentication, access control, and data protection mechanisms against attacks like man-in-the-middle and denial of service. The conclusion emphasizes the necessity of routinely updating passwords and configuring network settings to enhance security.





![M. S. Ramaiah School of Advanced Studies 30
References
[FRAN07] Frankel,S.;Eydt,B.;Owens,L.;And Scarfone,K. “Establishing wireless robust security networks: A guide
to 802.11i”. NIST special publication Sp 800-97, February 2007.
[Edney04] Edney, J.; Arbaugh,W.; “Real 802.11 Security: WiFi Protected Access and 802.11i”. Addison-Wesley,
2004.
[WPA2015] “Wi-fi Protected Access”[Online] Available from: http://en.wikipedia.org/wiki/Wi-
Fi_Protected_Access (Accessed: 1 January 2015)
[WSA2015]“Wireless Security Access”[Online] Available from: http://en.wikipedia.org/wiki/Wireless_security
(Accessed: 25 December 2015)](https://image.slidesharecdn.com/cjb0412001-advancedwirelesssystem-spc2520-presentation-150104012455-conversion-gate02/85/Wireless-Networking-Security-30-320.jpg)