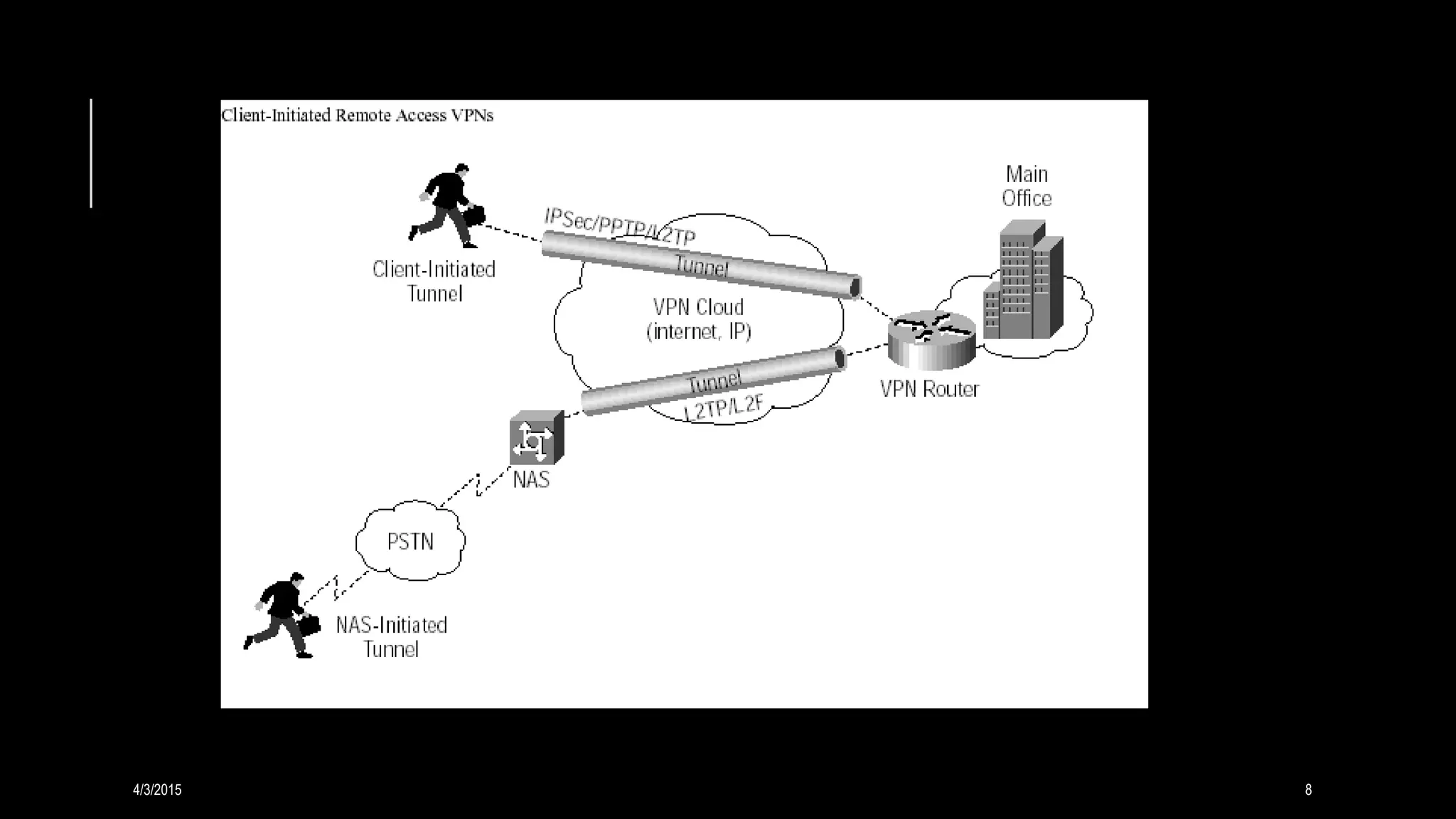
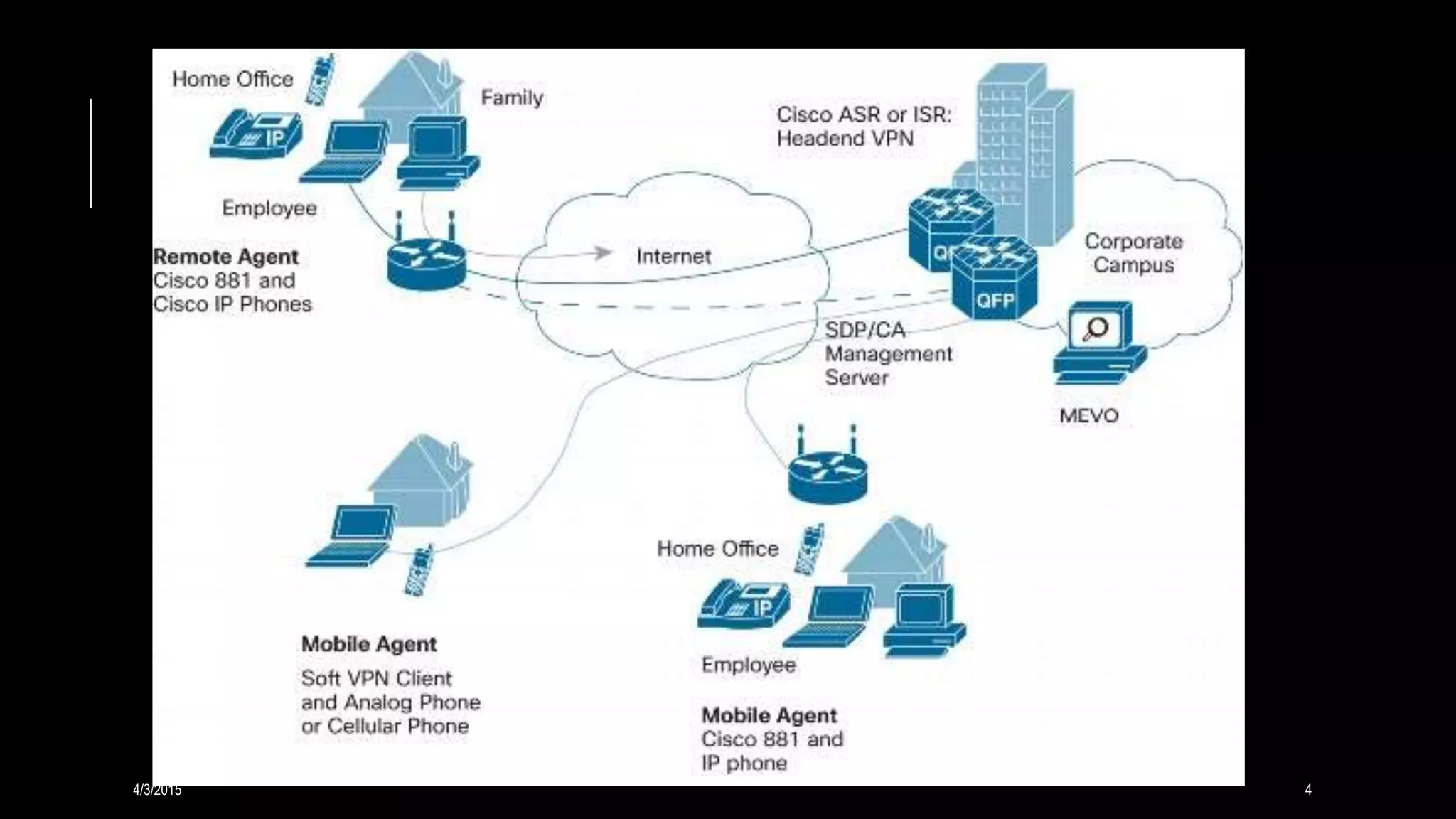
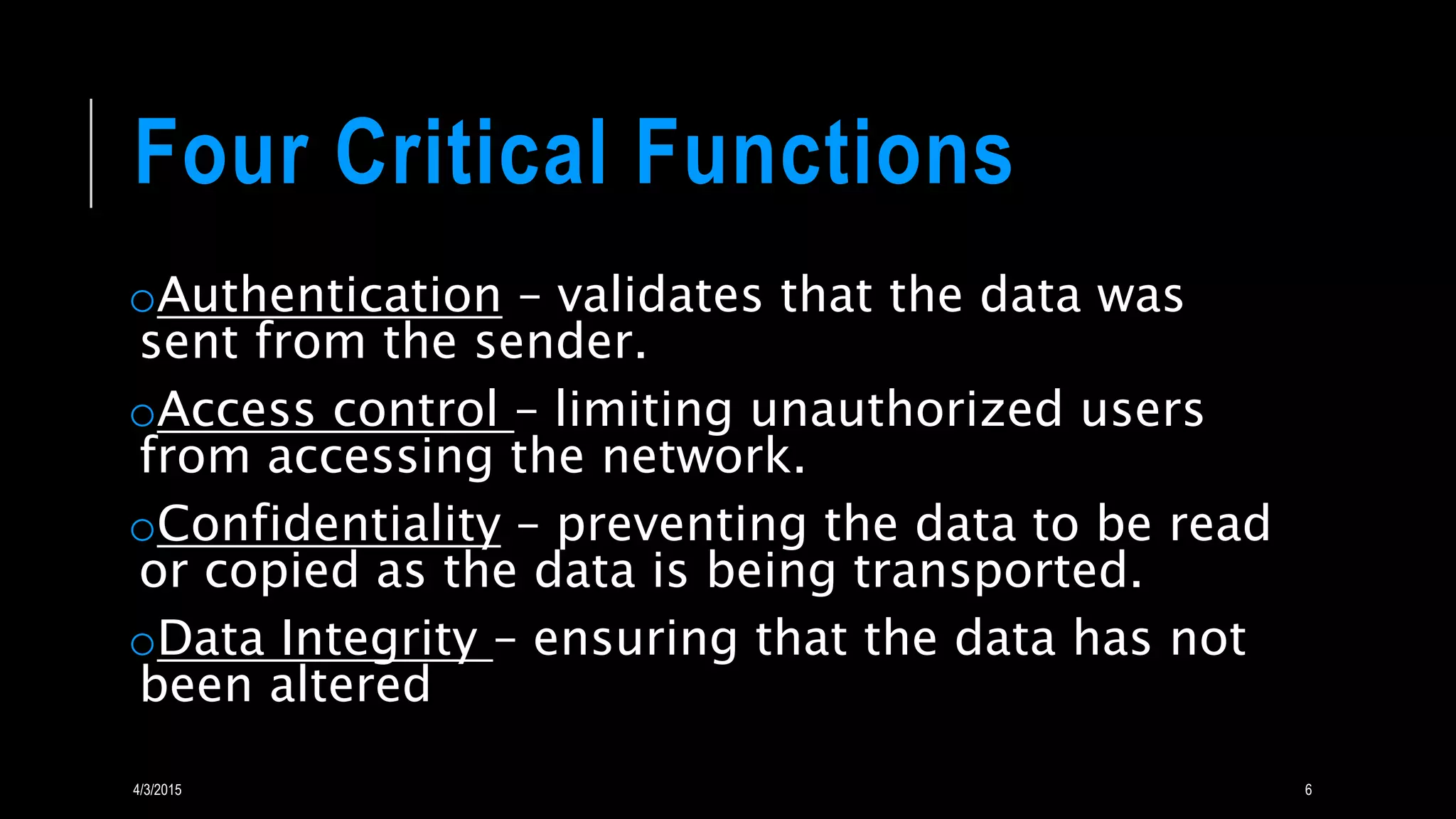
A VPN creates a secure connection over a public network like the Internet by tunneling link layer protocols. It allows remote users to access private networks. VPNs provide security by using an encrypted connection with another IP address and separating IP traffic. Key functions include authentication, access control, confidentiality, and ensuring data integrity. Common protocols are PPTP, L2TP, IPsec, and SSL/TLS.




![Tunneling
A virtual point-to-point connection made through a
public network. It transports encapsulated datagrams.
Encrypted Inner Datagram
Datagram Header Outer Datagram Data
Area
Original Datagram
Data Encapsulation [From Comer]
4/3/2015 7](https://image.slidesharecdn.com/vpn-150403164003-conversion-gate01/75/Virtual-Private-Network-VPN-7-2048.jpg)