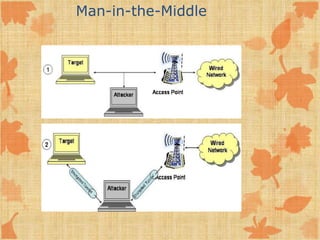
This document discusses security issues with wireless networks and protocols. It describes common wireless standards like 802.11b, g, and a. It then covers security protocols that aimed to improve on WEP like WPA and WPA2, discussing their encryption methods. The document also outlines various threats to wireless security like eavesdropping, unauthorized access, and denial of service attacks. It concludes by listing some common wireless hacking tools.