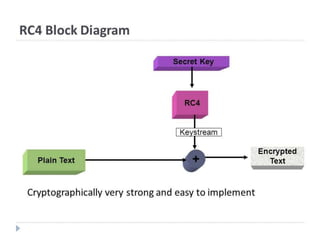
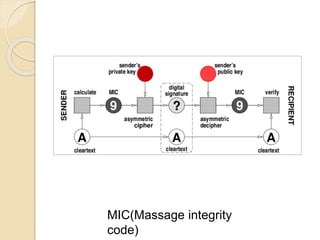
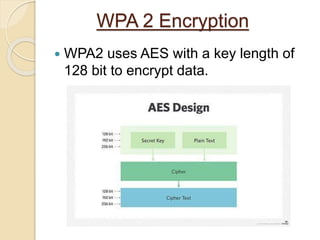
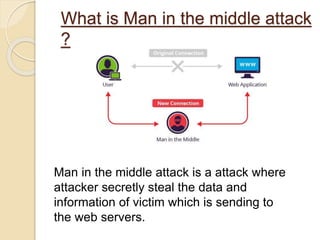
WPA3 (Wi-Fi Protected Access 3) is the next generation of Wi-Fi security, designed to enhance protection over WPA2 by introducing features like stronger encryption and better defense against attacks such as KRACK and man-in-the-middle. WPA2, adopted in 2004, provided data protection but had vulnerabilities that WPA3 addresses, including improved password protection and simplifying Wi-Fi connection processes. The document outlines the evolution of wireless security protocols and discusses the limitations of previous systems while highlighting the advantages of adopting WPA3.