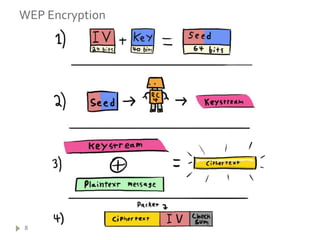
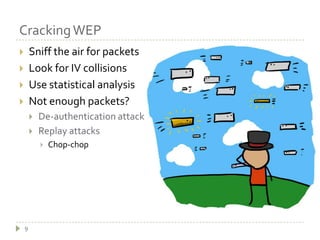
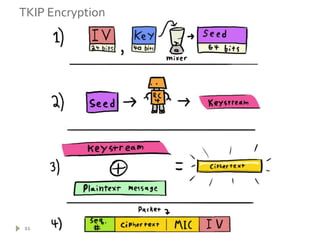
This document summarizes wireless network security and best practices. It discusses how wireless networks are less secure than wired due to packet sniffing and remote access. It describes common wireless attacks like man-in-the-middle and denial of service. WEP encryption is shown to be flawed and easily cracked. WPA was introduced as an improvement over WEP but still has some vulnerabilities. The document recommends using strong encryption like AES, along with other security measures such as MAC filtering, static IPs, network separation, and policy to help secure a wireless network.



![Attacker Incentive6Free internet![Industrial] espionageGeneral maliceFun and profit](https://image.slidesharecdn.com/wirelessnetworksecurity-091223225256-phpapp01/85/Wireless-Network-Security-6-320.jpg)