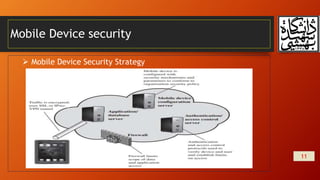
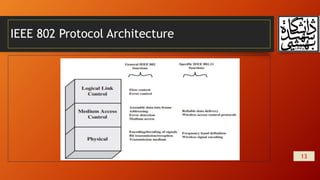
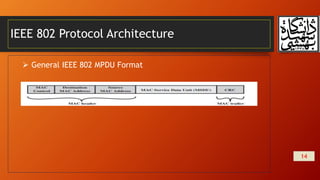
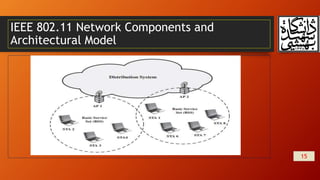
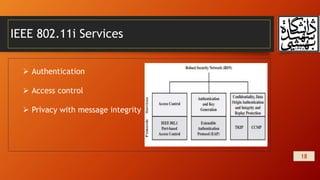
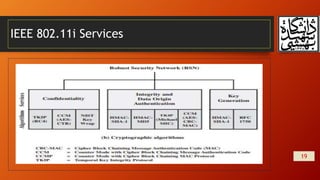
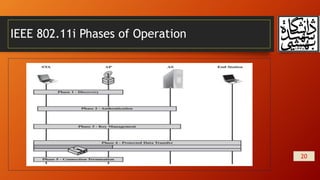
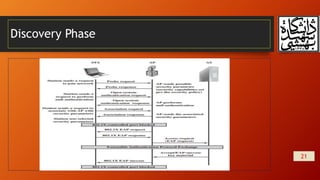
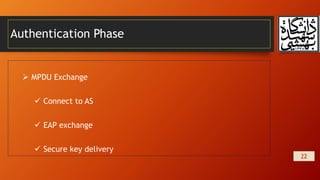
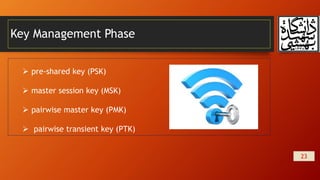
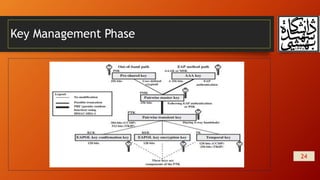
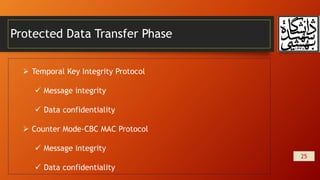
This document summarizes wireless network security and mobile device security. It discusses wireless network threats such as identity theft, man-in-the-middle attacks, and denial of service attacks. It also discusses IEEE 802.11 wireless LAN security standards including WEP, WPA, and RSN. Mobile device security threats include lack of physical security controls, use of untrusted networks and applications. The document outlines security strategies for wireless transmissions, access points, and networks. It also describes the phases of IEEE 802.11i including discovery, authentication, key management, and protected data transfer.