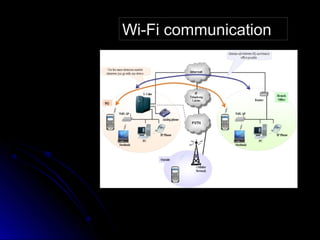
Wi-Fi technology uses radio waves to transmit and receive data wirelessly. It uses standards such as 802.11b, 802.11a, and 802.11g. A Wi-Fi network consists of access points that broadcast a wireless signal to connect devices like computers, phones and tablets. Security measures for Wi-Fi include encrypting data transmission and authenticating users and servers to prevent eavesdropping, spoofing and denial of service attacks. Common configurations and applications of Wi-Fi include home and office networks, as well as use by travelers.